Education Exchange Storage Protocol: Transformation Into Decentralized Learning Platform
- 1Ministry of Education Key Laboratory of Molecular and Cellular Biology, Master of Information Technology, University of Raharja, Tangerang, Indonesia
- 2School of Computing, Faculty of Engineering, University of Technology Malaysia, Johor, Malaysia
- 3Computer Science and Technology, Albaha University, Al Bahah, Saudi Arabia
- 4Master of Information System, University of Raharja, Tangerang, Indonesia
- 5Information Technology, University of Raharja, Tangerang, Indonesia
- 6Information System, University of Raharja, Tangerang, Indonesia
The current micro-teaching process is readily online, and it is functional anywhere and anytime ubiquitously. All or most teaching and learning activities are accessible in centralized storage. However, centralized storage has inherent problems, such as a single point of failure with many possible data breaches, much duplication of data stored repeatedly in one location, and the lack of trust in third parties for data stored in centralized storage. Further issues include the high cost and low performance of the online systems that hinder the quality of the education process. In this paper, we propose a new framework Education Exchange Storage Protocol (EESP). EESP aims to improve the efficiency of the decentralized storage ecosystem in micro-teaching, coupled with blockchain technology acting as a control layer. Blockchain empowers the decentralized system by bringing together the most incompatible unstructured entities and integrate them. The decentralized storage system is armed with a blockchain smart contract that acts as a control layer, featuring impregnable security, immutability, trace-ability, and transparency. The EESP framework aims to elevate teaching and learning through blockchain decentralized storage systems in a transformational way, including but not limited to things like micro-credential, massive open online courses, and gamification, all in a single immersive learning platform. Finally, we tested and evaluated this framework using the truffle simulator, and the results demonstrate that the EESP model significantly improves performance.
1 Introduction
The entire education sector landscape has shifted because of the Covid-19 pandemic outbreak. Schools and colleges remain closed indefinitely; fear of losing hope for the future resonates worldwide (Watermeyer et al., 2021). The children from kindergarten to K12 and colleges stay at home and are constrained to study exclusively online. This negative impact affecting life and lifestyle is preeminent (Wang et al., 2018a), like never before in centuries. Families around the world are especially concerned about the education of their children. There is an urgent and immediate need to save our children’s future, and this situation calls for unity and humanity (Palacios et al., 2019).
As a consequence of the pandemic (McElroy et al., 2020), technology undoubtedly remains the only vital turning point that can usher a fundamental structural shift in education (Vimal and Srivatsa, 2019). The change is paramount; it not only alleviates the impact of the pandemic it also accelerates learning. The digital transformation is unprecedented in improving productivity by increasing student engagement and motivation. Various new models of connections in an integral teaching and learning platform are overwhelmingly introduced by developers (Rich et al., 2021), linking teachers and students to invaluable professional resources and experiences that entirely improve personalized learning like never before. Flexibility in learning, in terms of preferred day and time, or personal favorite places to engage in teaching and learning (Yates et al., 2021), the people in this era of civilization have the incredible opportunity to enjoy the unprecedented ubiquitous learning experience.
Although many attempts to offer the best education platform worldwide, people still demand something unique that fits everybody’s education needs. Too many education platforms are readily available to the public (Kwon et al., 2020), and which one will tailor best to our needs remains questionable. Unclustered learners are making trial and error, wasted time and resources spent fruitlessly testing unproductive learning platforms. How wonderful if time and resources could be on productive learning rather than navigating aimlessly on identifying suitable learning platforms.
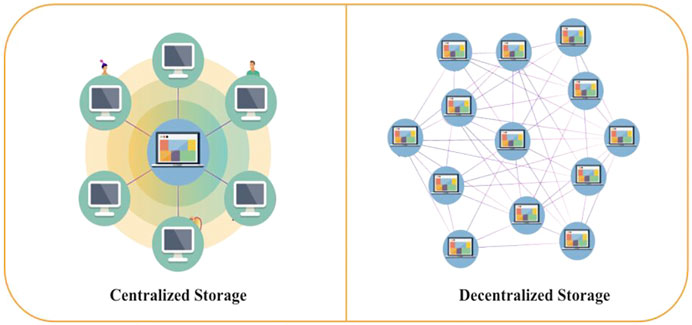
So many technologies combine and converge to form the learning platform, this research aims to focus on the storage for micro-teaching (Poitras et al., 2021). For micro-teaching to be effective, much data needs to be readily available to teachers and learners. And up to the current technology in time, the most necessity of storage for micro-teaching remains in a centralized database (Chiu, 2021). These configurations are largely prone to a data breach on confidential and sensitive data. As shown in Figure 1, another problem in the centralized system is congestion, which has a single natural point of failure. If this point of failure is misused, it can easily lead to data loss or leakage. Consequently, higher education typically implements security policies that restrict access to sharing of records in micro-teaching to protect personal information (Yuan, 2020; Erdemir and Yeşilçınar, 2021). Even if the centralized storage system is reserved for data availability, the centralized storage service provider may still experience Force Majeure factors (such as political censorship) that prevent users from accessing their data (Wang et al., 2018b).
In addition, it is a common practice that users often store the same micro-teaching data repeatedly in one location (Ledger and Fischetti, 2020). The attempt causes inconsistent data redundancy and consumes unnecessarily large data storage space, leading to the increased overhead cost of centralized cloud storage services. At present, decentralized storage already costs a lot cheaper than popular centralized storage (Munson and Hu, 2010). Not only that, the data stored on third parties may be corrupted or altered, thus causing the whole system to be compromised (Xu et al., 2020). Centralized multi-tenant data architectures directly risk that user’s proprietary data is vulnerable to unauthorized higher education competitors or malicious attackers. Cloud service providers could sometimes be dishonest, enticed, or swayed by some personal interest (Pu et al., 2020; Lang et al., 2018). Due to efficiency demand, they could discard unused or infrequently accessed data to save storage space while claiming it is still adequately maintained in the cloud. As a result, higher education must ensure that their micro-teaching data is appropriately accessible in the cloud by making multiple timely backups. Moreover, data leak cases like Facebook-Cambridge Analytica have resulted in a substantial shift from centralized to decentralized data storage systems at the time (Fahey and Hino, 2020).
Underpinning this research is from the above point of view; the future of education requires a decentralized storage approach. The challenge remains on the control and accessibility of the asset: to deliver the packages with great security control; to ensure self-sovereignty of the assets; to provide provenance and trace-ability of the assets; to prevent any tampering of data by making it immutable; to ensure the transaction of data without inter-mediation (Cai, 2018). For this, we propose a new framework, EESP, to efficiently achieve decentralized storage in micro-teaching by combining with blockchain technologies as a control layer. No more worrying about a single point of failure, data compromised, or data inaccessible issues. There will be no more data in repeated fashion and also eliminating third parties.
The remainder of this paper is organized as follows. Part II includes related work describing micro-teaching, blockchain education, decentralized storage, peer-to-peer, and content-addressable storage. The schematic of the system is described in detail in Part III, starting with an illustration of centralized storage issues, and follows with the EESP proposed framework. The framework is further elaborated into smart contract design and algorithm. Subsequently, Part IV presents a case study to prove the working scheme. Finally, we wrap up the research by summarizing the conclusions and the research implications. Future challenges suggest the direction of future research that will naturally be conducted by the authors of this paper or other authors interested in this research domain.
2 Related Work
To fundamentally understand the flow of the research, this section discusses several knowledge and technologies relevant to our work, such as Micro-teaching, Blockchain Education, Decentralized Storage, Peer, and Content Addressable Storage.
2.1 Micro-Teaching
Micro-teaching is a relatively new invention in teacher education that utilizes a professional development tool in both pre-service and in-service teacher education programs (Orland-Barak and Wang, 2021). Micro-teaching enables teachers to understand teaching and learning processes better and develop teaching abilities, examine their teaching, and examine the teaching of others. From the learners’ perspective, micro-teaching provides transparency and flexibility to learners by providing continuous assessment and prediction towards the learning pathway (Binder et al., 2021; Márquez-Ramos and Mourelle, 2018; Bouilheres et al., 2020). Both teachers and learners benefit from advancing technologies such as the internet of things, artificial intelligence, machine learning, deep learning, and blockchain (Xie et al., 2020). Those technologies converge to provide unparalleled vital services such as involuntary recommendations, advice, and predictions towards teachers’ and learners’ pathways of the education journey. This guidance further ensures collectible assistive information (Spyridonis and Daylamani-Zad, 2021) to uplift education experience and quality to a new level. The underlying foundation is the need for reliable storage, a receptacle where Micro-teaching stores and combines a massive amount of structured and unstructured data (Isaac et al., 2020). Structured data include grades, course material, and assignments. Unstructured data include CCTV captured data, video streaming, and audio files (Subudhi et al., 2019). All reliable data must be readily available for the AI technologies (Coghlan et al., 2021) to learn and adapt to the assigned task (Andriella et al., 2020). The trainee teacher re-teaches the micro-lesson based on the feedback, incorporating the points highlighted by the artificial intelligence dashboard recommendation (Mellit and Kalogirou, 2021).
2.2 Blockchain Education
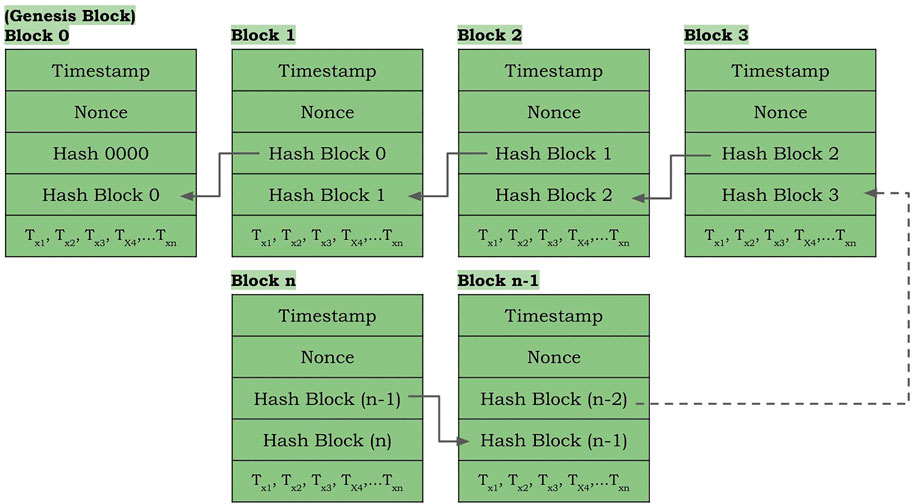
As a decentralized network, Blockchain does not require a central control point or a single storage poin (Rahardja et al., 2020). Blockchain is a decentralized, immutable, and trusted distributed ledger and provides a secure, stable, transparent, audit-able, and effective way to record transactions and interactions of data information (Farahani et al., 2021; Lu, 2018). A typical example of a blockchain is shown in Figure 2.
The process of creating new blocks is known as mining. The first block is called the genesis block (Gramoli, 2020). Since there is no previous block, therefore the previous hash in the genesis block is zero. The new blocks are always appended at the end of the blockchain. Every block consists of at least five main items: timestamp to indicate the exact time when the block was created; nonce to accommodate mining of the block; the previous hash that serves as a connecting chain with the previous block; the hash of the current block; and finally the collection of the transactions in the block (Zhang et al., 2019; Dorri et al., 2019). The main components behind the blockchain architecture include Transactions, Blocks, Cryptography, Smart Contracts, Consensus Algorithms, and P2P network. Storing information on the blockchain ensures the originality of the data and solves the security problem of the central authorization mechanism (Yin et al., 2020). Users cannot change the data stored on the blockchain arbitrarily due to the immutable property of the blockchain. Therefore, it functions as evidence to verify the originality and fluidity of the data. Haiyang Yu et al. proposes an efficient continuous big data integrity checking scheme for blockchain-powered decentralized storage (Yu et al., 2021). Their scheme can check multiple files randomly in each time slot, enabling them to verify the integrity of big data for the entire storage period with a high probability of verification. Sujit et al. are also considering connecting traditional e-health service providers via the BC backbone for seamless patient data exchange with strict access control. This approach allows for off-chain information storage for big data that cannot be part of the main chain.
Blockchain technology is responsible as the engine behind the rise of cryptocurrency. Blockchain is also applied to other financial sectors, the health, IoT, government, and education sectors. Halvdan Haugsbakken et al. discuss the potential value of blockchain technology in higher education and identifies areas where the technology can increase speed, efficiency, and transparency (Haugsbakken and Langseth, 2019). Furthermore, according to (Abbasi et al., 2021), the blockchain concept has demonstrated the potential of current educational opportunities. According to (Alammary et al., 2019), the application of blockchain technology to education is still in its very early stages, and there is plenty of room for discoveries. So, an examination of cutting-edge blockchain research in the field of education should be rigorously carried out. Additionally, according to (Guo et al., 2020), they propose a blockchain-enabled digital rights management system that effectively manages online educational multimedia resources. Their research uncovered an entirely new network architecture for sharing and managing online educational multimedia resources based on a combination of public and private blockchains, as well as three special smart contract schemes for the realization of multimedia digital rights recording, secure storage, and verification without intermediaries (Vacca et al., 2020).
Uni-Chain was designed by Daraghmi et al. (2019) to be compatible with existing EAR databases and provide inter-operable, secure, and efficient access to EAR by universities, students, and third parties while protecting student privacy. According to their findings, universities are responsible for blockchain maintenance, including creation, verification, and addition of new blocks, while allowing students to control access to their EARs securely. Saleh et al. (2020) proposed a blockchain-based model for verification of graduation certificates to improve the verification mechanism by embedding the SHA-256 hash of any data string in the digital signature embedded in the academic certificate to facilitate verification. Other researchers have tried to increase the digital academic record verification system based on blockchain technology that can be very useful in situations where international companies or educational institutions require verification of one’s academic records (Ocheja et al., 2019). Since the digital identifiers given to graduates can be used globally, they can be assigned to anyone anywhere in the world for fast record verification (Lee et al., 2020). With the current general trend in the development and transformation of global education, blockchain technology is expected to emerge as an essential role in developing the “Internet + education” ecology (Qurotul et al., 2020). Research into the educational implications of blockchain is moving rapidly (van Hoek, 2019). Therefore, based on previous studies, there is no existing ideal educational framework design that readily stores and processes all micro-teaching activities quickly and transparently in a decentralized manner.
2.3 Decentralized Storage
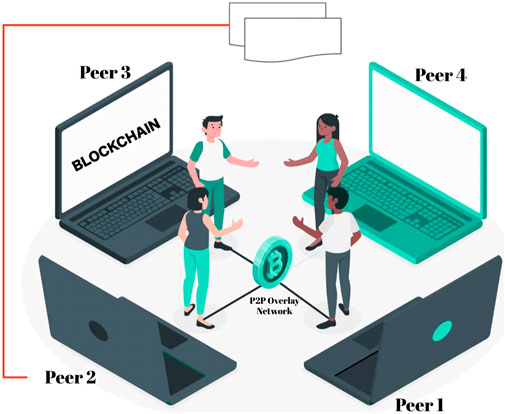
Based on the above discussions, decentralized storage is related to blockchain technology in supporting the storage process of micro-teaching activities in education. As shown in Figure 3, the peer-to-peer nodes in decentralized storage contain stored data readily obtainable whenever needed by many sectors. Such research (Yazdinejad et al., 2020) aims to use blockchain to authenticate new patients decentralized in a distributed hospital network. It is demonstrated, for example, that the proposed architecture for decentralized authentication among distributed connected hospital networks does not require re-authentication. The researchers in Jiang et al. (2020) introduced Searchain, a blockchain-based keyword search system. It enables an oblivious search over an authorized keyword set in the decentralized storage. This mechanism aims to assure private search over authorized keywords with entire retrieval orders. The research (Liu et al., 2020) explores the architecture for transforming centralized degree internship certification and validation into a decentralized ledger of secure databases. BC technology in the DA validation process further encourages employers to engage with universities systematically from the early stages of developing degree apprenticeship standards. This researcher (Ouyang et al., 2021) proposes a combined learning process managed by a blockchain-based decentralized storage consensus mechanism to prevent bias and privacy leakage from central aggregation unity. IntegrityChain, a decentralized storage outsourcing framework providing the feature of data integrity auditing, has been introduced by the authors of (Li et al., 2020). In another effort (Savazzi et al., 2020), researchers proposed a fully decentralized storage (or server-less) learning approach: the proposed FL algorithms leverage the cooperation of devices that perform data operations inside the network by iterating local computations and mutual interactions via consensus-based methods. In particular, Lyu et al. (2020) build a fair and differentially private decentralized storage deep learning framework called FDPDDL, enabling parties to derive more accurate local models reasonably and privately by using their developed two-stage scheme.
Because of its benefits in terms of reliability, availability, and scalability, distributed cloud storage has gotten greater attention, and it presents both possibilities and problems for distributed data storage transactions. Traditional storage transaction systems, which are often centralized, result in high costs, vendor lock-in, and the danger of a single point of failure (Gu et al., 2018).
All of the above introduced decentralized storage applications to various business sectors, but few focus on the area of control required for the data in the micro-teaching domains. The question remains on protecting proprietary intellectual rights on the digital assets in the education sector, especially addressing securities issues in terms of the combination of self-sovereignty, immutability, trace-ability, provenance, and disintermediation.
In this research, we present a decentralized transaction technique for cloud storage based on a smart contract that considers the resource cost for distributed cloud storage to alleviate the drawbacks described above.
2.4 Peer to Peer (P2P)
A peer-to-peer (P2P) (Liu et al., 2019) storage system consists of two roles: data owner and data requester. A data owner holds a set of data objects and intends to share them with a certain subset of nodes: its corresponding data requesters. In a P2P storage system, each node can be both a data owner and data requester of other data owners, simultaneously. There have been many peer-to-peer file-sharing applications all over the world (Li et al., 2018). This incentive considers the security and replication of files or resources during the process of transfer, the authors of suggest to take advantage of a hierarchical data structure of a structured P2P and supports proximity-aware and interest clustered file-sharing systems. In another effort (Hassanzadeh-Nazarabadi et al., 2019), they introduce the Pyramid, which is the first fully decentralized utility-aware and locality-aware replication approach for Skip Graph-based P2P cloud storage systems. Pyramid is locality-aware as it minimizes the average latency between nodes and their closest replica. To improve the P2P file system scheme based on IPFS and Blockchain has been studied by the authors of (Naz et al., 2019), the research is to address the high-throughput problem for individual users in IPFS by introducing the role of content service providers. In another effort, the authors argued that violent extremists are experiencing difficulty maintaining viable, persistent presences on social media platforms. With P2P blockchain-based online platforms, an untenable approach to counter-extremism can co-exist. Surveyed the consensus mechanisms and the agreement protocols designed for distributed systems, such as blockchain platforms and P2P-based systems. They identified that the probabilistic consensus mechanisms tend to sacrifice consistency on CAP theorem, and safety on the FLP impossibility, to achieve consensus.
And in education, as shown in Figure 4 proposed by the authors of (Hashemipour et al., 2021), each peer in the P2P grid represents a participating teacher, and an overlay is formed to represent the neighborhood relationship of participating peers. Also, a peer can join/leave the P2P grid at any time, which characterizes the dynamic nature of P2P grids. To conduct teaching material sharing, a peer installs the tailor-made software, which supports Blog-like operations, such as publication, comment/reply, content organization, etc. In addition, the functions of teaching material search and download are incorporated. In particular, (Ng et al., 2021) proposed a P2P mobile learning model, which shapes the essential interface between the mobile terminals and the web applications. The proposed model is validated via effective trade-off among timely response, individual learning-oriented content management, and multimedia streaming-based peer-to-peer interactivity. They implemented this model using a web-based chat room, achieving a plausible teaching-learning effect. An idea from (Nicholls and Altieri, 2018) is to take advantage of widely-spread and adopted P2P networks for disseminating learning objects, considering them as an ideal means for creating collaborative communities of learners with similar interests. The authors of (Al Ridhawi et al., 2018) introduced a new framework for a more efficient learning environment by using P2P architecture and Semantic Overlay Network. This solution will help inefficient management of LCMS components and improve the performance of LCMS through the RLO. There is even an online reinforcement learning-based approach developed by the authors of (Pouamoun and Kocabaş, 2021) to take advantage of the dynamic run-time characteristics of the P2P IR system represented by information about previous search sessions. Therefore, there is still scarcity in locating in-depth research regarding integration of P2P, blockchain, and decentralized storage to be used in micro-teaching processes.
2.5 Content Addressable Storage
Content addressed storage, also known as CAS, is an object-based system designed for storing and managing fixed content data. It is intended for the safe online storage and retrieval of fixed content, as opposed to location addressed storage, also known as LAS. According to (Ullah et al., 2020), databases increasingly use CAS for storing backup information, and snapshots. The process of content-addressable storage is when requesting a particular resource, there is no need to specify a location, it only needs to determine what to look for. In CAS, we request using their cryptographic hash identifier to retrieve the intended item, where the location of the item itself is completely irrelevant. The hash of each file acts as a unique identifier in the form of digital fingerprint. Retrieving the file simply requires the data requester to broadcast the hash key that belongs to the file. Once requested, the network will ping and attempt using the content identifier CID, to locate the nearest decentralized nodes that contain the desired data. PLEDGE is introduced by the authors of (Makhdoom et al., 2020), an efficient and scalable Security Protocol for protecting fixed-content objects in CAS architectures. Moreover, PLEDGE transparently stores sensitive objects encrypted (partially or totally) in the CAS storage nodes without affecting the CAS storage system operation or performance. It also takes into consideration the processing load, computing power, and memory capabilities of the client devices which may be constrained by limited processing power, memory resources, or network connectivity. Since blockchain systems operate on a peer-to-peer network, the main characteristic of blockchain technology is its natural decentralization (Esmat et al., 2021). So, this research underpin the combination of blockchain technology, decentralized storage, P2P, and content-addressable storage need to conduct in order to create a new trend in the education sector to store all micro-teaching assets.
3 Proposed Scheme
This section will present the issues of centralized storage and the need to conduct the protocol framework of educational exchange storage protocol.
3.1 Centralized Storage Issues
The information contained on the Internet is mostly used in centralized storage, most of us are familiar with it. However, from a technical perspective, it has its own issues. Some of the issues are listed below:
1. The threat of a single point of failure in the education sector is that if one server dies or does not function, the entire system will stop too. The user cannot connect to the server, so the system cannot process requests to provide micro-teaching data. Moreover, if there is no backup, users can immediately lose the micro-teaching data. Hence, it can cause very low data availability issues as well.
2. There is a trade-off between cost and performance. Storing the same data and large micro-teaching files repeatedly on centralized storage causes high redundancy. It will overload the system exponentially and makes it a big disadvantage for higher education.
3. There is no micro-teaching data network access control on third-party storage space, so it can be used as a crime such as hacking, spamming, duplication, and even being sold to irresponsible parties.
3.2 Education Exchange Storage Protocol
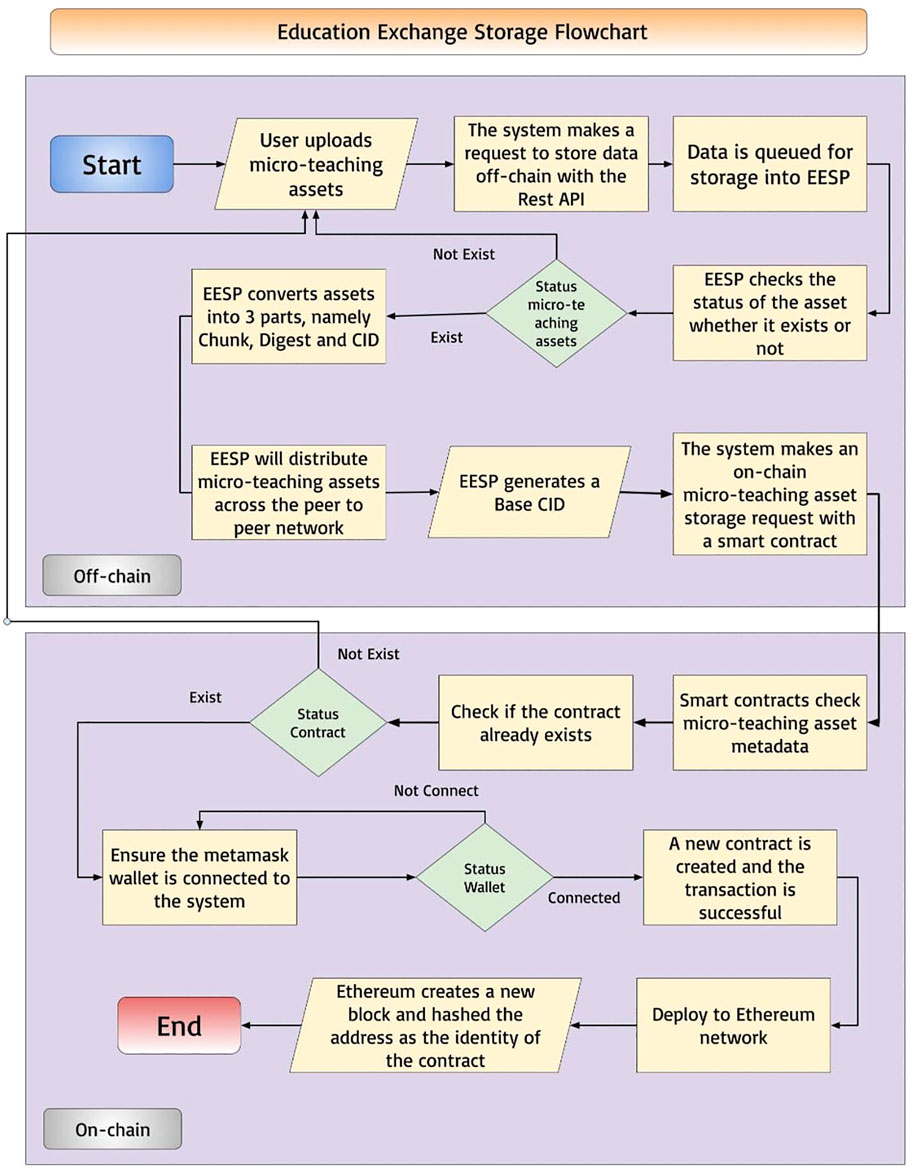
Inspired by the above literature and as far as we know, we are the first to conduct extensive research on combining blockchain and decentralized storage in a P2P environment. This study proposes the Education Exchange Storage Protocol (EESP) which can support the micro-teaching process in higher education and can gain more benefits than data storage and sharing in traditional centralized storage systems. EESP is in the form of protocol because it consists of rules and sequences to make decentralized storage platform functional. Additionally, we use a framework (Figures 5–7) to explain the flow of the protocol in a simple and understandable. EESP is P2P among the academic community in higher education.
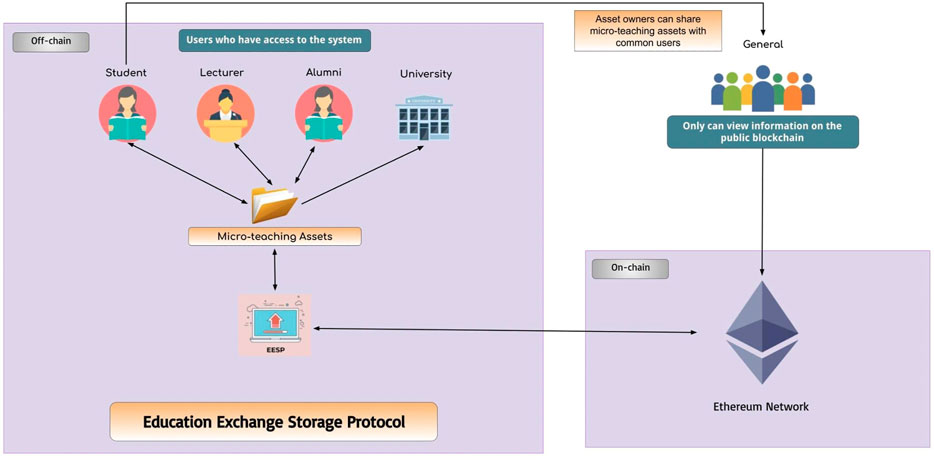
As can be seen from Table 1 and Figure 5, there is an EESP flowchart for micro-teaching in the field of education to make it easier to understand the algorithm design. Starting from users, namely students, lecturers, universities or management, alumni, and the general public. Registered users such as students and lecturers have the right to upload micro-teaching assets. The micro-teaching asset upload process occurs at the off-chain layer, when the user uploads the system will make a request to the server to save the user’s assets to the off-chain with Rest API, of course, in this process a queue occurs. However, this process happens so fast that users will not feel any delays due to queues. Furthermore, EESP will first check the micro-teaching assets received, to find out in advance that these assets have never been stored on the EESP network. If the same micro-teaching asset already exists on the blockchain network then the request made will be rejected. When the micro-teaching asset has been confirmed not to be stored in the EESP, the process will continue. EESP will automatically convert assets to Chunk, Digest, and Content Identification (CID). After the CID is successfully created the asset will be distributed on the EESP P2P network to generate a Base CID as the identity of the asset. The process is continued by the server that makes a request to store data at the on-chain layer. Before the micro-teaching asset is received, the smart contract will check the micro-teaching asset through its metadata. Then, it performs checks to ensure that a contract with the micro-teaching asset has never been created on a public blockchain network. If the contract already exists, then the request will be rejected and the process cannot continue with the same micro-teaching asset due to the nature of the blockchain which rejects duplication. After the inspection is complete and declared accepted, the system will ensure that the user’s wallet is connected to the system. After all the requirements have been met, a new contract will be created and stored in the blockchain network. A new block will be created that stores information about the contract made, the hash of the block will become the identity of the micro-teaching asset in the blockchain public network.
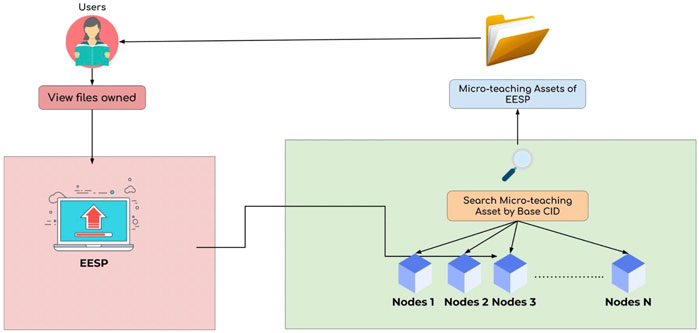
As can be seen from Figure 6 when the user wants to view the assets from the micro-teaching that have been stored in EESP, the user needs the CID generated by EESP, this CID is stored on the Blockchain Data Storage platform on each asset owner account. EESP will leverage when there is a request to view assets. Verify using the Base CID, and this search will be performed on all connected nodes on the EESP network. when the asset, then the user can see it as a complete undivided asset found.
User access control within the blockchain public network is so limited that general users can only view the information of the contracts made, but general users cannot view the assets of the EESP users as can be seen in Figure 7. General users need permission from the owner of the asset and are required to have access to the EESP system in order to view the asset.
3.2.1 Smart Contract Design
Smart contracts have three distinguishing characteristics: autonomy, decentralization, and self-sufficiency. According to autonomy, smart contract creators are no longer needed once the contracts are deployed on the blockchain.
The schematic of the smart contract is depicted in Figure 8. Each contract will be allocated a unique 20-byte address. The contract code cannot be changed once it is applied to the blockchain. Users can only submit transactions to the contract address to execute them. Each consensus node (also known as a miner) on the network will then perform these transactions to reach a consensus on its performance. The contribution of this research is to automate the issuance of degree certificates on the blockchain upon completion of the degree using smart contracts. Results are to address unmanaged risk, bureaucracy, human intervention, and fraud. In this study.

FIGURE 8. Smart contract system? (Delmolino et al., 2016).
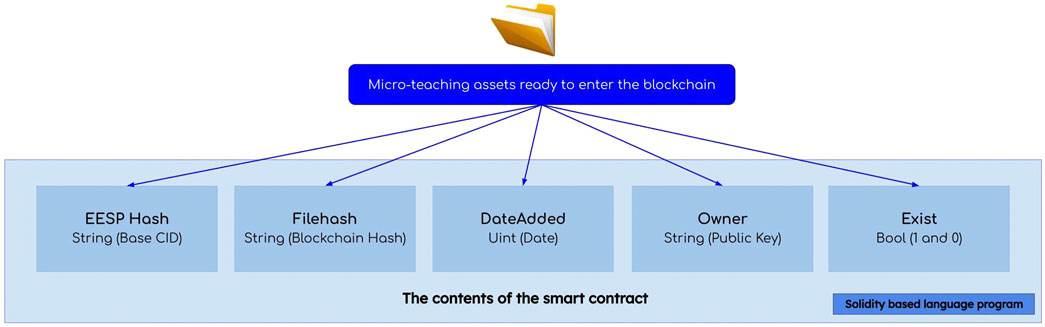
From present Figure 9, user assets that are ready to be stored on the blockchain will get the help of smart contracts to eliminate third parties from contracting asset storage transactions so that asset security is guaranteed. There is the structure of the smart contract used, written using the solidity language that was specifically created to create smart contracts on various blockchain platforms. After the user’s asset is received, the smart contract will check the metadata of the asset, the smart contract will create a new contract that contains five main elements, namely EESP Hash, File Hash, Date Added, Owner and Exist.
3.2.2 Algorithm Design
In this section the logic and algorithms of EESP are explained in detail. This research focuses on using the Solidity programming language to create Smart Contract designs. There are special variables and functions for processing assets integrated on a decentralized network. We mainly use the following special variables:eespHash: the hash generated after the asset is successfully stored into the EESP distributed network, the hash is used as the identity of an asset that stores information about the stored asset or is known as CID (Content Identifier) and can be used to access the stored data.fileHash: this hash is generated automatically after the eespHash CID is stored in the Blockchain network, the benefit of this fileHash can provide a guarantee of the validity of the content stored in the EESP network.dateAdded: is information about the time when the asset storage process was carried out by the user. Owner: Is the owner of the data that carries out the process of storing assets into the EESP and Blockchain, and has full control over the data stored. Exist: Used to ensure that there is no duplicate content either on the EESP or on the Blockchain network.
Algorithm 1 Store File to Blockchain
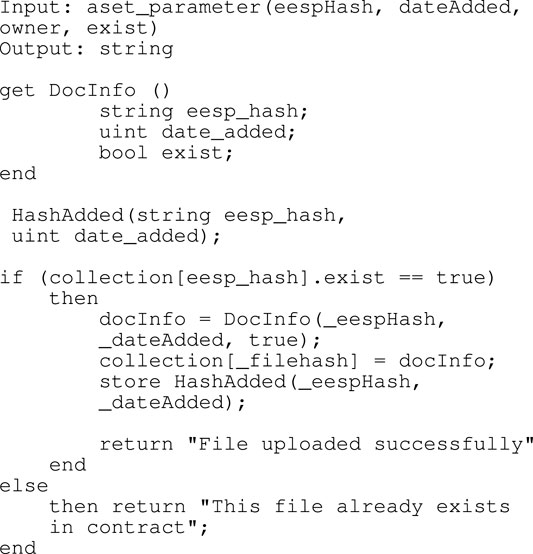
Get DocInfo() is a function to get the data that the asset owner wants to store, in this case the smart contract will check some metadata, namely eespHash, dateAdded and exist.HashAdded function is used to store multiple asset parameters derived from user assets as an array.Collection [eesphash] function is useful to ensure that the asset to be stored is not duplicated, if it is found that the asset already exists then the storage fails.store HashAdded after going through the inspection process and it is stated that the assets are not duplicated, the smart contract will be executed and a new transaction will be created on the Blockchain, in which it stores the information obtained from HashAdded.
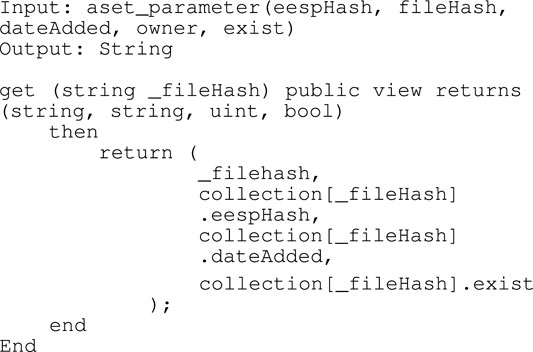
Algorithm 2 View from Blockchain
get(string_hash) This function is used to access assets stored in Blockchain decentralized networks. In order to obtain access rights to the targeted asset, a hash generated after the data storage process into the Blockchain is required. The result of this function will display a string of data that comes from the asset metadata, namely fileHash, eespHash, dateAdded and availability status.
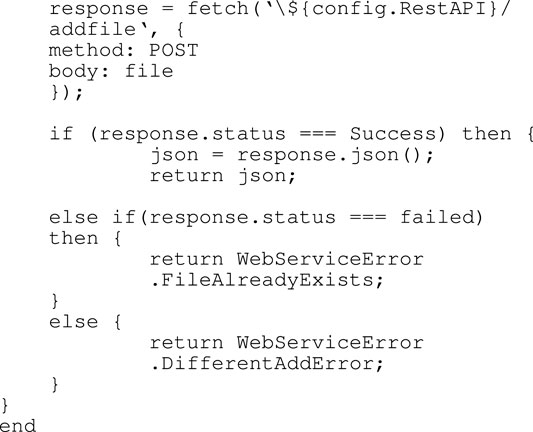
Algorithm 3 EESP Store File
store addFile(file) This function is used to store assets into an EESP distributed network, the process starts from sending an asset storage request by using the Rest API POST method. Response.status is used to notify the owner of the status of the asset that you want to keep, if the process fails because the asset is duplicated it will display an error message.
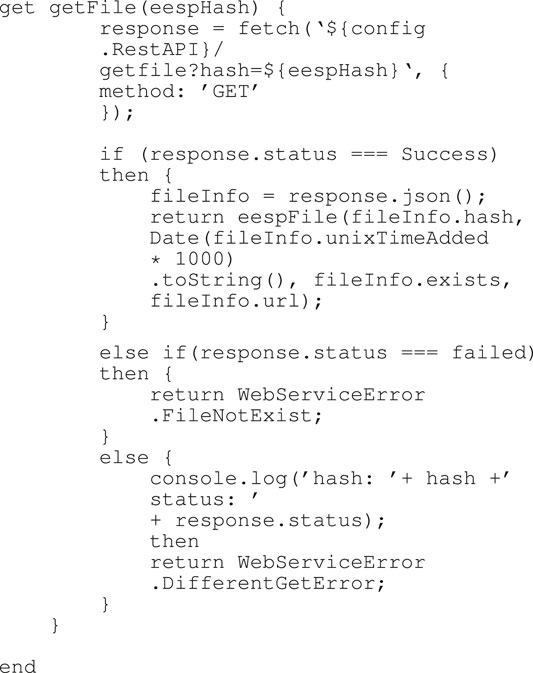
Algorithm 4 EESP Get File
get getFile() This function is useful for accessing assets stored in the EESP network, by making use of the Rest API GET method based on the received eespHash.Response.status function is used to notify asset owners about the current status of wanting to access their stored assets. If the status is successful then information about the asset will be displayed, while the failed status will display an error message such as the asset is not available until another error message.
4 EESP Analysis
This paper, in particular, highlights the novelty in synthesizing blockchain technology, a content-addressable storage mechanism, and blockchain smart-contract technology to create an EESP decentralized storage system for higher education. We gain significant benefits compared to the traditional centralized storage systems for data storage and accessibility in the education domain. In this chapter, we will discuss the experiments and the results. Then, this chapter concludes on the EESP framework’s contributions in terms of security and privacy.
To run the experiments, we use GitHub and set up the truffle simulators, which consist of four main engines: Solidity Framework, Ganache, Dapp’s frontend libraries, and truffle simulator. The comprehensive solidity code is in this paper Supplementary Appendix SA. To facilitate researchers to conduct further investigations and replicate the work, we include the GitHub release.
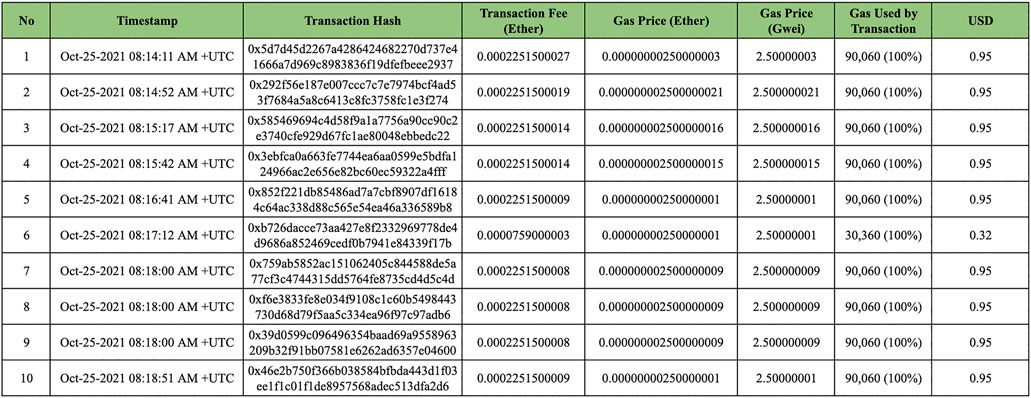
We ran 750 simulations for 25 days, and we found astounding discoveries that this framework applies to decentralized education space. Further rigorous experiments integrating other aspects of education functions still need to be conducted to prove our claims, which is beyond the scope of this paper. Indeed, this work contributes to laying the foundation for further leaps and bounces of advancement in decentralized education space. Supplementary Appendix SB provides a few samples of results, including gas usage and gwei consumptions. In Figure 10 we further assimilate those results into tables to provide a more vivid visual representation.
Based on the experiments and results, we would like to paint the landscape of our discoveries comparing traditional education with the newly proposed decentralized education. It is essential to understand that our focus is on the storage domain. We have highlighted this argument in Section 1 of this paper that finding the perfect storage solution is crucial and pivotal for further development and advancement of the technology.
Avoid Single Point of Failure:
Unlike traditional centralized storage, our EESP decentralized storage system adopted for higher education can solve the problem of a single point of failure in our solution. With P2P, data owners have the ability to distribute and share files securely because micro-teaching data is hashed. When users need micro-teaching data, P2P networks will quickly provide it. Furthermore, the EESP framework has incentives for users who can provide nodes for those who need it. If users do not want to enable their nodes, they can still store and share files on the EESP network.
Avoid High Redundancy
Micro-teaching data reliability and availability are ensured by runs on a peer-to-peer basis, uses DHT routing technology, with higher data throughput, and low redundancy.
Avoid Third Parties
In centralized storage schemes, we need to rely on service providers to perform search operations honestly and provide appropriate results. However, the service provider may return incorrect results or return no results to save resources, etc., so that the user pays for the service but cannot enjoy the service. In our solution, the EESP framework ensures fairness of the search process through content-addressable storage and smart contracts. The process of storing content-addressable is that when requesting a specific resource that has been hashed, it doesn’t need to specify a location, it just needs to specify what to look for. Smart contracts can perform search operations honestly and according to predetermined logic, and the reliability and availability of data can be guaranteed. So that data owners can control their own data.
The contributions of the research are as follows, we were able to create the EESP framework and combine a decentralized storage network for micro-teaching with blockchain and smart contract as a control layer. Users in the civitas community can act as a storage provider or consumer or both. Blockchain smart contract governs between users, rewarding providers and charging consumers. The EESP framework is sustainable because users are incentivized to contribute. It can be stated that as long as the blockchain network and the EESP framework are secure, so is the proposed framework.
5 Conclusion and Future Work
This research suggests that we should migrate from classical centralized storage into innovative decentralized schemes in the education sector. To achieve this purpose, we introduce a novel EESP framework coupled with a blockchain smart contract that contributes to making significant changes and improvements compared to the current system. The findings of the EESP framework can be applied for the benefits of humanity in this digital era, users in education can store all micro-teaching data securely, will no longer suffer from a single point of failure, high redundancy issues, and no more third party can intervene with and benefit from the network of our framework. We synthesize a blockchain smart contract, assimilating it into the EESP framework so that each hash information micro-teaching can be saved to the node’s blockchain. Our future work is to assemble more educational functions and applications into the EESP framework and then do more rigorous simulations and more in-depth customization optimization for content-related services in micro-teaching education.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Ethics Statement
Written informed consent was obtained from the individual(s) for the publication of any potentially identifiable images or data included in this article.
Author Contributions
UR, MN, RB, QA, MH, and FO contributed to the activities. QA, MH, and FO manage the database of activities. UR, MN, and RB wrote the first draft of the manuscript. All authors contributed to manuscript revision, reading, and approval of submitted versions.
Funding
And this research has been funded by a World Class Professor (WCP) Indonesia grant based on Decree Number 2817/E4.1/KK.04.05/2021.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Acknowledgments
The author would like to thank the Ministry of Education and Culture, LPDP Indonesia, University of Raharja for their financial support and for providing a place to support this research through research system analysis.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/feduc.2021.782969/full#supplementary-material
References
Abbasi, G. A., Tiew, L. Y., Tang, J., Goh, Y. N., and Thurasamy, R. (2021). The Adoption of Cryptocurrency as a Disruptive Force: Deep Learning-Based Dual Stage Structural Equation Modelling and Artificial Neural Network Analysis. Plos one 16, e0247582. doi:10.1371/journal.pone.0247582
Al Ridhawi, I., Aloqaily, M., Kantarci, B., Jararweh, Y., and Mouftah, H. T. (2018). A Continuous Diversified Vehicular Cloud Service Availability Framework for Smart Cities. Computer Networks 145, 207–218. doi:10.1016/j.comnet.2018.08.023
Alammary, A., Alhazmi, S., Almasri, M., and Gillani, S. (2019). Blockchain-based Applications in Education: A Systematic Review. Appl. Sci. 9, 2400. doi:10.3390/app9122400
Andriella, A., Torras, C., and Alenyà, G. (2020). Cognitive System Framework for Brain-Training Exercise Based on Human-Robot Interaction. Cogn. Comput. 12, 793–810. doi:10.1007/s12559-019-09696-2
Binder, M., Pfisterer, F., Lang, M., Schneider, L., Kotthoff, L., and Bischl, B. (2021). mlr3pipelines-flexible Machine Learning Pipelines in R. J. Machine Learn. Res. 22, 1–7.
Bouilheres, F., Le, L. T. V. H., McDonald, S., Nkhoma, C., and Jandug-Montera, L. (2020). Defining Student Learning Experience through Blended Learning. Educ. Inf. Technol. 25, 3049–3069. doi:10.1007/s10639-020-10100-y
Cai, C. W. (2018). Disruption of Financial Intermediation by Fintech: a Review on Crowdfunding and Blockchain. Account. Finance 58, 965–992. doi:10.1111/acfi.12405
Chiu, M.-S. (2021). Making Open Educational Resource Videos on Sustainable Development: Students' Attitudes, Rationales, and Approaches. Res. Sci. Technol. Edu., 1–25. doi:10.1080/02635143.2021.1966406
Coghlan, S., Miller, T., and Paterson, J. (2021). Good proctor or “Big Brother”? Ethics of Online Exam Supervision Technologies. Philosophy & Technology 1355, 1–26. doi:10.1007/s13347-021-00476-1
Daraghmi, E.-Y., Daraghmi, Y.-A., and Yuan, S.-M. (2019). Unichain: a Design of Blockchain-Based System for Electronic Academic Records Access and Permissions Management. Appl. Sci. 9, 4966. doi:10.3390/app9224966
Delmolino, K., Arnett, M., Kosba, A., Miller, A., and Shi, E. (2016). Step by step towards creating a safe smart contract: Lessons and insights from a cryptocurrency lab. International conference on financial cryptography and data security, Springer, 79–94.
Dorri, A., Kanhere, S. S., Jurdak, R., and Gauravaram, P. (2019). Lsb: A Lightweight Scalable Blockchain for Iot Security and Anonymity. J. Parallel Distributed Comput. 134, 180–197. doi:10.1016/j.jpdc.2019.08.005
Erdemir, N., and Yeşilçınar, S. (2021). Reflective Practices in Micro Teaching from the Perspective of Preservice Teachers: Teacher Feedback, Peer Feedback and Self-Reflection. Reflective Pract., 1–15. doi:10.1080/14623943.2021.1968818
Esmat, A., de Vos, M., Ghiassi-Farrokhfal, Y., Palensky, P., and Epema, D. (2021). A Novel Decentralized Platform for Peer-To-Peer Energy Trading Market with Blockchain Technology. Appl. Energ. 282, 116123. doi:10.1016/j.apenergy.2020.116123
Fahey, R. A., and Hino, A. (2020). Covid-19, Digital Privacy, and the Social Limits on Data-Focused Public Health Responses. Int. J. Inf. Manage. 55, 102181. doi:10.1016/j.ijinfomgt.2020.102181
Farahani, B., Firouzi, F., and Luecking, M. (2021). The Convergence of Iot and Distributed Ledger Technologies (Dlt): Opportunities, Challenges, and Solutions. J. Netw. Comp. Appl. 177, 102936. doi:10.1016/j.jnca.2020.102936
Gramoli, V. (2020). From Blockchain Consensus Back to Byzantine Consensus. Future Generation Comp. Syst. 107, 760–769. doi:10.1016/j.future.2017.09.023
Gu, Y., Hou, D., Wu, X., Tao, J., and Zhang, Y. (2018). Decentralized Transaction Mechanism Based on Smart Contract in Distributed Data Storage. Information 9, 286. doi:10.3390/info9110286
Guo, J., Li, C., Zhang, G., Sun, Y., and Bie, R. (2020). Blockchain-enabled Digital Rights Management for Multimedia Resources of Online Education. Multimed Tools Appl. 79, 9735–9755. doi:10.1007/s11042-019-08059-1
Hashemipour, N., Crespo del Granado, P., and Aghaei, J. (2021). Dynamic Allocation of Peer-To-Peer Clusters in Virtual Local Electricity Markets: A Marketplace for Ev Flexibility. Energy 236, 121428. doi:10.1016/j.energy.2021.121428
Hassanzadeh-Nazarabadi, Y., Küpçü, A., and Ozkasap, O. (2019). Decentralized Utility-And Locality-Aware Replication for Heterogeneous Dht-Based P2p Cloud Storage Systems. IEEE Trans. Parallel Distributed Syst. 31, 1183–1193.
Haugsbakken, H., and Langseth, I. (2019). The Blockchain challenge for Higher Education Institutions. Eur. J. Edu. 2, 41–46. doi:10.26417/ejed.v2i3.p41-46
Isaac, N. J. B., Jarzyna, M. A., Keil, P., Dambly, L. I., Boersch-Supan, P. H., Browning, E., et al. (2020). Data Integration for Large-Scale Models of Species Distributions. Trends Ecol. Evol. 35, 56–67. doi:10.1016/j.tree.2019.08.006
Jiang, P., Guo, F., Liang, K., Lai, J., and Wen, Q. (2020). Searchain: Blockchain-Based Private Keyword Search in Decentralized Storage. Future Generation Comp. Syst. 107, 781–792. doi:10.1016/j.future.2017.08.036
Kwon, J., Elliott, S., and Velardo, S. (2020). Exploring Perceptions about the Feasibility of Educational Video Resources as a Strategy to Support Parental Involvement in Youth Soccer. Psychol. Sport Exerc. 50, 101730. doi:10.1016/j.psychsport.2020.101730
Lang, M., Wiesche, M., and Krcmar, H. (2018). Criteria for Selecting Cloud Service Providers: a delphi Study of Quality-Of-Service Attributes. Inf. Manag. 55, 746–758. doi:10.1016/j.im.2018.03.004
Ledger, S., and Fischetti, J. (2020). Micro-teaching 2.0: Technology as the Classroom. Australas. J. Educ. Tech. 36, 37–54. doi:10.14742/ajet.4561
Lee, H. A., Kung, H. H., Udayasankaran, J. G., Kijsanayotin, B., B Marcelo, A., Chao, L. R., et al. (2020). An Architecture and Management Platform for Blockchain-Based Personal Health Record Exchange: Development and Usability Study. J. Med. Internet Res. 22, e16748. doi:10.2196/16748
Li, S., Sun, W., and Liu, J. (2018). A Mechanism of Bandwidth Allocation for Peer-To-Peer File-Sharing Networks via Particle Swarm Optimization. Ifs 35, 2269–2280. doi:10.3233/jifs-172276
Li, Y., Yu, Y., Chen, R., Du, X., and Guizani, M. (2020). Integritychain: Provable Data Possession for Decentralized Storage. IEEE J. Select. Areas Commun. 38, 1205–1217. doi:10.1109/jsac.2020.2986664
Liu, Y., He, D., Obaidat, M. S., Kumar, N., Khan, M. K., and Raymond Choo, K.-K. (2020). Blockchain-based Identity Management Systems: A Review. J. Netw. Comput. Appl. 166, 102731. doi:10.1016/j.jnca.2020.102731
Liu, Y., Wu, L., and Li, J. (2019). Peer-to-peer (P2p) Electricity Trading in Distribution Systems of the Future. Electricity J. 32, 2–6. doi:10.1016/j.tej.2019.03.002
Lu, Y. (2018). Blockchain and the Related Issues: A Review of Current Research Topics. J. Manag. Analytics 5, 231–255. doi:10.1080/23270012.2018.1516523
Lyu, L., Li, Y., Nandakumar, K., Yu, J., and Ma, X. (2020). How to Democratise and Protect Ai: Fair and Differentially Private Decentralised Deep Learning. IEEE Trans. Dependable Secure Comput. doi:10.1109/tdsc.2020.3006287
Makhdoom, I., Tofigh, F., Zhou, I., Abolhasan, M., and Lipman, J. (2020).Pledge: An Iot-Oriented Proof-Of-Honesty Based Blockchain Consensus Protocol. In 2020 IEEE 45th Conference on Local Computer Networks. IEEE, 54–64. doi:10.1109/lcn48667.2020.9314794
Márquez-Ramos, L., and Mourelle, E. (2018). On the Relationship between Society and Higher Education: what Path Should We Take? Distance Edu. 39, 19–36. doi:10.1080/01587919.2018.1436401
McElroy, E., Patalay, P., Moltrecht, B., Shevlin, M., Shum, A., Creswell, C., et al. (2020). Demographic and Health Factors Associated with Pandemic Anxiety in the Context of Covid-19. Br. J. Health Psychol. 25, 934–944. doi:10.1111/bjhp.12470
Mellit, A., and Kalogirou, S. (2021). Artificial Intelligence and Internet of Things to Improve Efficacy of Diagnosis and Remote Sensing of Solar Photovoltaic Systems: Challenges, Recommendations and Future Directions. Renew. Sust. Energ. Rev. 143, 110889. doi:10.1016/j.rser.2021.110889
Munson, C. L., and Hu, J. (2010). Incorporating Quantity Discounts and Their Inventory Impacts into the Centralized Purchasing Decision. Eur. J. Oper. Res. 201, 581–592. doi:10.1016/j.ejor.2009.03.043
Naz, M., Al-zahrani, F. A., Khalid, R., Javaid, N., Qamar, A. M., Afzal, M. K., et al. (2019). A Secure Data Sharing Platform Using Blockchain and Interplanetary File System. Sustainability 11, 7054. doi:10.3390/su11247054
Ng, C. H., Koh, N. K., and Ling, H. L. (2021). Incorporating New Literacies in Designing a mobile Learning Application for Secondary/middle School Students. Educ. Inf. Technol. 26, 1485–1504. doi:10.1007/s10639-020-10314-0
Nicholls, C. I., and Altieri, M. A. (2018). Pathways for the Amplification of Agroecology. Agroecology Sust. Food Syst. 42, 1170–1193. doi:10.1080/21683565.2018.1499578
Ocheja, P., Flanagan, B., Ueda, H., and Ogata, H. (2019). Managing Lifelong Learning Records through Blockchain. Res. Pract. Tech. Enhanced Learn. 14, 1–19. doi:10.1186/s41039-019-0097-0
Orland-Barak, L., and Wang, J. (2021). Teacher Mentoring in Service of Preservice Teachers' Learning to Teach: Conceptual Bases, Characteristics, and Challenges for Teacher Education Reform. J. Teach. Edu. 72, 86–99. doi:10.1177/0022487119894230
Ouyang, L., Yuan, Y., Cao, Y., and Wang, F. Y. (2021). A Novel Framework of Collaborative Early Warning for Covid-19 Based on Blockchain and Smart Contracts. Inf. Sci. (N Y) 570, 124–143. doi:10.1016/j.ins.2021.04.021
Palacios, J., Adroher, S., Brodzinsky, D. M., Grotevant, H. D., Johnson, D. E., Juffer, F., et al. (2019). Adoption in the Service of Child protection: An International Interdisciplinary Perspective. Psychol. Public Pol. L. 25, 57–72. doi:10.1037/law0000192
Poitras, E. G., Doleck, T., Huang, L., Dias, L., and Lajoie, S. P. (2021). Time-driven Modeling of Student Self-Regulated Learning in Network-Based Tutors. Interactive Learn. Environments 1–22. doi:10.1080/10494820.2021.1891941
Pouamoun, A. N., and Kocabaş, İ. (2021). Multi-agent-based Hybrid Peer-To-Peer System for Distributed Information Retrieval. J. Inf. Sci., 01655515211010392. doi:10.1177/01655515211010392
Pu, Y., Xiang, T., Hu, C., Alrawais, A., and Yan, H. (2020). An Efficient Blockchain-Based Privacy Preserving Scheme for Vehicular Social Networks. Inf. Sci. 540, 308–324. doi:10.1016/j.ins.2020.05.087
Qurotul, A., Mukti, B., Panca Oktavia, H. P., and Lestari Santoso, N. P. (2020). Lecturer Certification Management Using Blockchain Technology. J. Adv. Res. Dynamical Control. Syst. 12, 624.
Rahardja, U., Aini, Q., Ngadi, M. A., Hardini, M., and Oganda, F. P. (2020).The Blockchain Manifesto. In 2020 2nd International Conference on Cybernetics and Intelligent System. IEEE, 1–5. doi:10.1109/icoris50180.2020.9320798
Rich, P. J., Mason, S. L., and O'Leary, J. (2021). Measuring the Effect of Continuous Professional Development on Elementary Teachers' Self-Efficacy to Teach Coding and Computational Thinking. Comput. Edu. 168, 104196. doi:10.1016/j.compedu.2021.104196
Saleh, O. S., Ghazali, O., and Rana, M. E. (2020). Studies, Planning and Follow-Up Directorate. Baghdad, Iraq: Ministry of Higher Education and Scientific ResearchSchool.Blockchain Based Framework for Educational Certificates Verification.
Savazzi, S., Nicoli, M., and Rampa, V. (2020). Federated Learning with Cooperating Devices: A Consensus Approach for Massive Iot Networks. IEEE Internet Things J. 7, 4641–4654. doi:10.1109/jiot.2020.2964162
Spyridonis, F., and Daylamani-Zad, D. (2021). A Serious Game to Improve Engagement with Web Accessibility Guidelines. Behav. Inf. Tech. 40, 578–596. doi:10.1080/0144929x.2019.1711453
Subudhi, B. N., Rout, D. K., and Ghosh, A. (2019). Big Data Analytics for Video Surveillance. Multimed Tools Appl. 78, 26129–26162. doi:10.1007/s11042-019-07793-w
Ullah, I., Yang, J.-S., and Chung, J. (2020). Er-tcam: A Soft-Error-Resilient Sram-Based Ternary Content-Addressable Memory for Fpgas. IEEE Trans. VLSI Syst. 28, 1084–1088. doi:10.1109/tvlsi.2020.2968365
Vacca, A., Di Sorbo, A., Visaggio, C. A., and Canfora, G. (2020). A Systematic Literature Review of Blockchain and Smart Contract Development: Techniques, Tools, and Open Challenges. J. Syst. Softw., 110891.
van Hoek, R. (2019). Exploring Blockchain Implementation in the Supply Chain: Learning from Pioneers and Rfid Research. Int. J. Operations Prod. Manag.
Vimal, S., and Srivatsa, S. (2019). A New Cluster P2p File Sharing System Based on Ipfs and Blockchain Technology. J. Ambient Intelligence Humanized Comput., 1–7. doi:10.1007/s12652-019-01453-5
Wang, S., Zhang, Y., and Zhang, Y. (2018a). A Blockchain-Based Framework for Data Sharing with fine-grained Access Control in Decentralized Storage Systems. IEEE Access 6, 38437–38450. doi:10.1109/ACCESS.2018.2851611
Wang, S., Zhang, Y., and Zhang, Y. (2018b). A Blockchain-Based Framework for Data Sharing with fine-grained Access Control in Decentralized Storage Systems. Ieee Access 6, 38437–38450. doi:10.1109/access.2018.2851611
Watermeyer, R., Crick, T., Knight, C., and Goodall, J. (2021). Covid-19 and Digital Disruption in uk Universities: Afflictions and Affordances of Emergency Online Migration. High Educ. 81, 623–641. doi:10.1007/s10734-020-00561-y
Xie, M., Li, H., and Zhao, Y. (2020). Blockchain Financial Investment Based on Deep Learning Network Algorithm. J. Comput. Appl. Math. 372, 112723. doi:10.1016/j.cam.2020.112723
Xu, Y., Zhang, C., Wang, G., Qin, Z., and Zeng, Q. (2020). A Blockchain-Enabled Deduplicatable Data Auditing Mechanism for Network Storage Services. IEEE Trans. Emerging Top. Comput.
Yates, A., Starkey, L., Egerton, B., and Flueggen, F. (2021). High School Students' Experience of Online Learning during Covid-19: the Influence of Technology and Pedagogy. Technol. Pedagogy Edu. 30, 59–73. doi:10.1080/1475939x.2020.1854337
Yazdinejad, A., Srivastava, G., Parizi, R. M., Dehghantanha, A., Choo, K. R., and Aledhari, M. (2020). Decentralized Authentication of Distributed Patients in Hospital Networks Using Blockchain. IEEE J. Biomed. Health Inform. 24, 2146–2156. doi:10.1109/JBHI.2020.2969648
Yin, B., Yin, H., Wu, Y., and Jiang, Z. (2020). Fdc: A Secure Federated Deep Learning Mechanism for Data Collaborations in the Internet of Things. IEEE Internet Things J. 7, 6348–6359. doi:10.1109/jiot.2020.2966778
Yu, H., Hu, Q., Yang, Z., and Liu, H. (2021). Efficient Continuous Big Data Integrity Checking for Decentralized Storage. IEEE Trans. Netw. Sci. Eng. doi:10.1109/tnse.2021.3068261
Yuan, R. (2020). Novice Nontraditional Teacher Educators' Identity (Re)construction in Higher Education: A Hong Kong Perspective. Int. J. Educ. Res. 99, 101508. doi:10.1016/j.ijer.2019.101508
Keywords: blockchain, decentralized storage, education, micro-teaching, EESP
Citation: Rahardja U, Ngadi MA, Budiarto R, Aini Q, Hardini M and Oganda FP (2021) Education Exchange Storage Protocol: Transformation Into Decentralized Learning Platform. Front. Educ. 6:782969. doi: 10.3389/feduc.2021.782969
Received: 25 September 2021; Accepted: 01 November 2021;
Published: 03 December 2021.
Edited by:
Christos Troussas, University of West Attica, GreeceReviewed by:
Sandi Rahmadika, Wonkwang University, South KoreaRaja Kumar Murugesan, Taylor’s University, Malaysia
Copyright © 2021 Rahardja, Ngadi, Budiarto, Aini, Hardini and Oganda. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Untung Rahardja, untung@raharja.info
 Untung Rahardja
Untung Rahardja M. A Ngadi
M. A Ngadi Rahmat Budiarto3
Rahmat Budiarto3  Qurotul Aini
Qurotul Aini Marviola Hardini
Marviola Hardini Fitra Putri Oganda
Fitra Putri Oganda