The Game Analysis of Information Sharing for Supply Chain Enterprises in the Blockchain
- 1Faculty of Science and Technology, University of Macau, Taipa, China
- 2College of business, Beijing Institute of Technology, Beijing, China
- 3Ruiyou Information Technology (Shanghai) Inc., Shanghai, China
- 4Centre for Efficiency and Performance Engineering University of Huddersfield, Huddersfield, United Kingdom
- 5College of Industrial Automation, Beijing Institute of technology, Beijing, China
The problems of additional inventory costs and inaccurate demand estimation caused by information asymmetry has severely damaged the profits of all participants and restricted the overall development of the supply chain. New technologies and ideas are urgently needed to solve these problems. The blockchain technology is widely accepted as a disruptive technology and a powerful tool to resolve information asymmetry with its advantage in decentralization, transparency, traceability, confidentiality, immutability, etc. The introduction of blockchain into the information system will effectively promote supply chain collaboration by facilitating information sharing among enterprises at various nodes. The paper builds a consortium chain model suitable for supply chain information sharing, uses evolutionary game theory to analyze the strategy changes and influencing factors in the information sharing choices of supply chain participants, and finally verifies the correctness of the results through MATLAB simulation.
1 Introduction
The supply chain is a complex system composed of multiple enterprises that realizes organizational alliance of all links between enterprises based on information flow (Xue et al., 2021). It governs the circulation of products from manufacturers to customers (Leng et al., 2018). The supply chain is not only a multi-organizational network for improving circulation efficiency, but also a business network with value-added at its core, and information flow, logistics flow and capital flow under its framework. With continuous development of the supply chain, a series of problems have occurred during numerous transactions on the part of participants, ranging from high trust costs, tricky transaction disputes, to especially information asymmetry, which has heightened complexity and fragmentation and made demand forecasting increasingly difficult (Yu et al., 2018; Fernández et al., 2019) (Yu et al., 2018; Fernández et al., 2019). The supply chain is also faced with the risk of overcapacity due to low demand realization rate, and excess inventory holdings have generated additional costs, which in turn have seriously damaged the interests of the nodes in the supply chain and restricted its overall development.
The rapid development of information technologies, especially the emergence of blockchain technology (BCT), is considered the fifth subversive innovation after mainframes, personal computers, the Internet, and mobile social networks (Crosby et al., 2016). It boasts the advantages of decentralization, transparency, traceability, confidentiality and immutability, etc. as a powerful tool to solve the problem of information silos (Aste et al., 2017). The application of BCT realizes information and knowledge sharing among business entities (Blockchain white paper, 2019), improves the supply chain partnerships through machine manufacturing trust, reduces costs and enhances efficiency (Queiroz and FossoWamba, 2019). BCT may provide a solution for supply chain information sharing from a technical level, but a series of management models need to be introduced.
Therefore, this paper focuses on the adverse effects of information asymmetry on the supply chain to construct an information sharing game model based on blockchain. Then it analyzes the changes and influencing factors of participants’ information sharing behaviors through dynamic evolutionary games. Trust created by machines for improving supply chain information sharing helps break the shackles of traditional collaborative management models.
The remainder of the paper is arranged as follows. Section 2 presents the literature review in blockchain, SCM, information sharing and evolutionary game theory. Section 3 elaborates upon the information sharing architecture and decentralized operation mode of supply chain based on consortium blockchain. Section 4 establish the game model and analyzes the different kinds of influencing factors on the choice of strategy. Section 5 dynamically analyzes the six influencing factors and verifies the results through MATLAB simulation. Finally, the paper concludes in Section 6.
2 Related Work
2.1 Information Sharing in the Supply Chain
Information sharing refers to data exchange and delivery between different organizations in the transaction or cooperation process (Lee et al., 1997). High-quality information sharing is considered the basis for stable and efficient operation of the supply chain (Zelbst et al., 2010a). The results of qualitative research show that information sharing can reduce the risks caused by information asymmetry, such as alleviating the bullwhip effect, shortening the order lead time, reducing costs, and improving operating efficiency (Jeong and Hong, 2019; Devika et al., 2016) (Devika et al., 2016; Jeong and Hong, 2019). At the same time, some studies have proved through quantitative analysis that selecting information sharing strategies among members is beneficial to saving costs and increasing overall profits (Yu et al., 2001). By comparing the changes in expected value of revenues before and after sharing demand and cost information, it is concluded that the total revenues of the supply chain has increased after information is shared (Yang et al., 2009).
Based on the research on influencing factors of information sharing, empirical analysis shows that the sharing behavior is affected by factors such as input costs, information leakage, changes in the external environment, and current information technology levels (Akbulut, 2002). The additional profit distribution also has a certain impact on the choice of information sharing behavior for enterprises (Srivastava, 2017). Some studies have concluded that the trust between participating companies is obviously positively correlated with information sharing (Huang and Iravani, 2005). Additionally, some other researches have collected data from 155 production and service departments to analyze the extent to which levels of RFID technology used by enterprises affect information sharing behavior. The results show that companies with high-level RFID technology are more willing to share information (Zelbst et al., 2010b).
2.2 Application of BCT in Supply Chain
The first well-known case of harnessing BCT happened in the field of financial services, namely the use of Bitcoin as a cryptocurrency that is now proliferating. The characteristics of BCT enable Bitcoin to process transactions in a highly secure and efficient manner. In addition, the legend of the Bitcoin success (albeit controversial) led people to evaluate the possibility of applying it to other cases, such as supply chain management. In contrast to its applications in the financial sector, the employment of BCT in supply chain management (SCM) is still in its infancy (Shanley, 2017). The main difference between the use of BCT in finance and in SCM lies in their core values: The core value for the former is information security, whereas that for the latter is system transparency and traceability (Aste et al., 2017). Targeting at the difficulties in SCM, BCT excels with its strong applicability and application value for various links on the supply chain.
1. Information sharing: Through privacy protection mechanisms such as information encryption and decryption authorization, and zero-knowledge proof, BCT can solve the long-standing contradictions between data privacy and sharing, and eliminate the worries of related parties in data sharing (Michael, 2018; Sara et al., 2019).
2. Guaranteeing data traceability and qualification: BCT is a traceable block-chain data structure constructed in a peer-to-peer network environment (Kim and Laskowski, 2018). BCT featured by distributed data storage, traceability, confidentiality and immutability ensures the authenticity and traceability of data, which has become a fundamental factor for anti-counterfeiting, SCM, supply chain finance and other fields (Lehmacher and McWaters, 2017; Zhou and Qian, 2020).
3. Enhancing mutual trust: Electronic signature plus BCT are another means to ensure data reliability (Lehmacher, 2017). Electronic storage of logistics and trade documents in a credible form solves the problems such as easy loss and tampering of traditional paper documents, thus ensuring the authenticity of data and enhancing mutual trust (Abeyratne and Monfared, 2016; Replicable Typical Experience and Practices, 2020).
4. Improving efficiency: The entire paperless blockchain-based transaction process, combined with the automatic transaction processing with smart contracts, will further enhance automation and convenience of interactions between enterprises, and improve collaboration efficiency (Cui et al., 2015; Apte and Petrovsky, 2016).
Studies have shown that corporate applications pay more attention to security, privacy protection, regulatory compliance and other elements so that the loss of decentralized performance is acceptable to some extent (Cachon and Lariviere, 2005). Therefore, the consortium blockchain with a relatively strong management model has more advantages in terms of efficiency and safety, and can meet the needs of multi-agent collaboration in the industry, which will become the mainstream direction of corporate blockchain applications in the future (Chauhan and Proth, 2005; Hu and Feng, 2017).
2.3 Supply Chain Information Sharing Characteristics Based on Blockchain Technology
1. Because the traditional supply chain has the characteristics of long business chain, large geographical span and high complexity, each node enterprise in the supply chain basically adopts centralized systems such as ERP, EDI or Internet/Intranet information integration system. With the promotion and application of blockchain technology, new features of supply chain information sharing have also emerged, mainly covering several aspects.
2. Data ownership has become clear and special agreements have been made, which to a certain extent motivates companies to try to carry out data sharing. In the past, it was difficult to separate data ownership and use rights, resulting in insufficient incentives for enterprise data sharing. Blockchain time stamps data blocks through a competition mechanism, making data on the chain heterogeneous. The property rights automatically change when data is circulated between different entities through smart contracts. Under the condition of mutual supervision of multiple parties, the consistency of the results of data rights confirmation is ensured.
3. The upstream and downstream enterprises in the supply chain have a certain basis for data sharing, but their development levels are uneven. Under the background of the digital economy, most supply chain enterprises have undergone digital transformation and have certain basic digital facilities. The ability to organize and apply is also not the same, and the value mined from information sharing and the rate of return obtained are also inconsistent.
4. As an intangible asset, information plays an important role in business decision-making, and is its own specific resource and competitive advantage. With the support of blockchain technology, the more private information is shared between the upstream and downstream of the supply chain, the greater the risk of information leakage and cooperation spillover borne by enterprises, and other participants will have opportunistic behaviors such as “free-riding".
2.4 Evolutionary Game Theory
Evolutionary game theory--a mathematical method used to study and predict the evolution of social interactions--considers individuals to be rational and then analyzes individual policy choices and game equilibria (Phelps and Wooldridge, 2013; De et al., 2016). In the evolutionary game, it is important to determine that the concept behind the game equilibrium is the evolutionarily stable strategy (ESS), which is equivalent to the Nash equilibrium but can also be applied to the evolution of individual policies. When a state can be maintained under slight disturbances caused by the dynamic system, it is called a steady state. In addition to the concept of an evolutionarily stable strategy, evolutionary game theory also considers replicator dynamics (RD). According to conclusions derived from the replication dynamic model, the trend of individual strategy selection in the population can be better predicted. The mathematical formula for competitive growth dynamics in RD is a differential equation that simulates the individual participating in the game, so it can better describe the effective rational trend of an individual’s behavior in the population. Some scholars have used the idea of games to conduct research on data sharing.
3 The Information Sharing Architecture Based on Consortium Blockchain
The prerequisites for the supply chain cooperative games include information sharing and interactions between alliances; besides, the agreements reached must be enforced, resulting in a cooperative surplus. These prerequisites happen to meet the features of the BCT and are satisfied by it. Therefore, we use consortium blockchain to provide technical support for supply chain information sharing and coordination.
First, due to the features of long business chains, wide span of regions, and high complexity for the traditional supply chains, each node enterprise on a supply chain basically uses the centralized system such as ERP, EDI or Internet/Intranet Information Integration System which are only limited to the internal management of the company, with no ability to collect or manage the whole data chain generated in the supply chain. Therefore, the information between upstream and downstream members is opaque and lacks interaction, and each node company cannot cope with market fluctuations. The advantages of BCT such as the distributed data storage, traceability, confidentiality and immutability help resolve the bottlenecks of the geographical dispersion of each subject and the difficulty of information exchange, and change the traditional one-way transmission mode to make data collection, verification and storage more reliable, and information delivery and usage more flat, thus bringing higher transparency and visibility to supply chain collaboration. Meanwhile, building a distributed system based on the blockchain maintains a unique and transparent database. Each member of the supply chain can add new data and verify its integrity and validity, access and retrieve all data stored on the blockchain, thereby greatly improving the accuracy of each company’s decision-making in order to better deal with market fluctuations.
Second, the features of the consensus mechanism, encryption algorithm, and immutability based on the blockchain can ensure the security and reliability of data without intermediaries. It is necessary to know that high costs are required to harness the blockchain system. Therefore, it can be used to reduce the intermediate links and transaction costs of each node enterprise, and effectively solve the fraud and unethical problems in the process of supply chain information coordination. At the same time, the smart contract of the supply chain is generated in the form of code, which can realize the automatic verification and execution of contract terms, and improve the operation efficiency of the entire chain.
Finally, the traceability character can help participants track the exact routes of commodities. By viewing goods logistics information in real time, upstream and downstream nodes can more easily manage inventory, and accurately calculate excess inventory and out-of-stock quantities, reducing human errors and inventory costs.
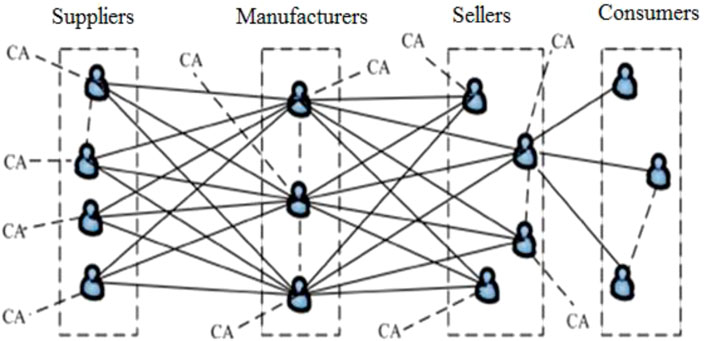
Therefore, for the closely related supply chain business system composed of suppliers, manufacturers, sellers and consumers, this paper proposes a supply chain information system based on the consortium blockchain, and require all participants to join the system only through authorization to avoid the interference from irrelevant users in a bid, and meanwhile to reduce the risk of ill-intentioned users meddling with the supply chain information. Under the supervision mechanism and certain incentives, each node enterprise will be more inclined to provide real information and participate in supervision for its own interests, and strive to maintain the overall efficiency of the supply chain. The overall structure of participant networking is illustrated in Figure 1, where CA stands for certification authority, namely each member company, such as the supplier, manufacturer and seller, which acts as independent certification subject to certify the authenticity and rationality of the information shared in the supply chain.
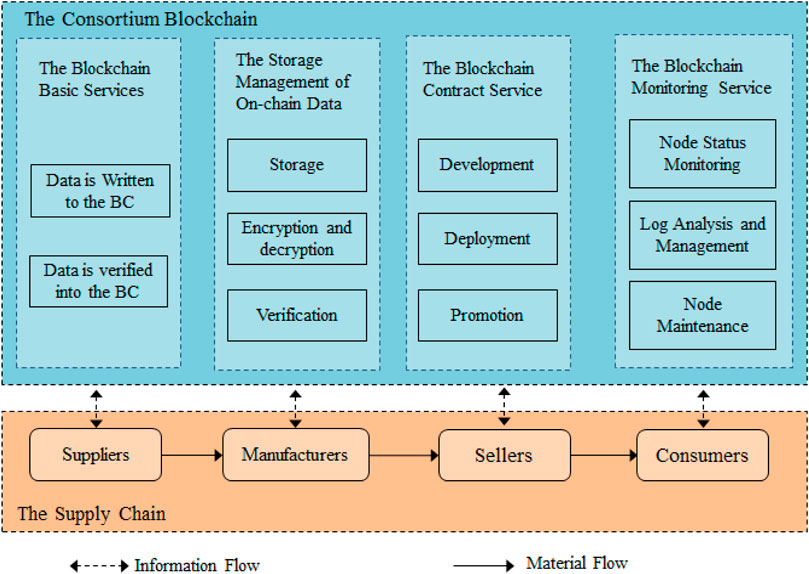
Compared with other participants, the end consumers have greater randomness and instability. Thus, they do not play to role of general certification authorities, but they can access database through authorization. The data generated and shared in the supply chain is no longer stored separately by its own business entities but in a distributed information platform based on the blockchain operating system for all members access. The architecture of the blockchain-based supply chain information sharing system is shown in Figure 2.
In response to the actual business needs of the supply chain, the information exchanged in the system based on the consortium blockchain mainly includes such aspects as inventory, sales, orders, production, and logistics. Through authorized access to on-chain data, the participating nodes make various business decisions in advance, reasonably respond to market demand fluctuations, complete various transaction activities through deployed smart contracts in an automatic and effective manner, and monitor the status of each member in real time, thus promoting the supply chain to improve operational efficiency and profit margins.
4 The Influencing Factors of Information Sharing Based on Evolutionary Game
4.1 Model Analysis
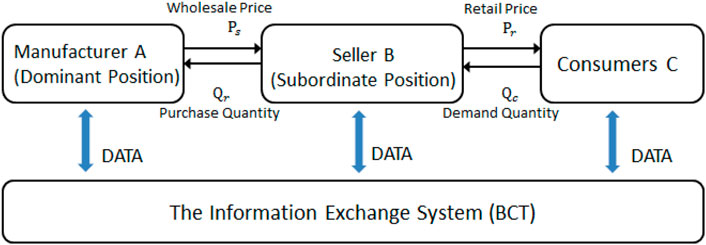
As we know, the choice of information sharing is often affected by companies’ abilities, organizational structure, input costs and other factors, which turns the process into a dynamic selection with game features. Decision-making on information sharing is influenced by four types of factors, including the information technology level of enterprises, quantity and quality of shared information (reflecting trust) among members, risk-taking, and costs (Lehmacher and McWaters, 2017; Sara et al., 2019; Zhou and Qian, 2020). Still based on the three-level structure (see Figure 3), the manufacturer is regarded as Player 1 and the seller as Player 2 to establish the game model and analyze the six kinds of influencing factors as well as their dynamic influence on the choice of strategy.
First, the long-term cooperative relationship between the manufacturer and the seller is examined. When there is no data exchanging between nodes in the supply chain, each member is in a state of information asymmetry, and sharing or non-sharing is optional. The probability for Player 1 to choose the sharing strategy is
Second, according to the quantitative analysis results in the previous chapter, when both players choose the sharing strategy, it can produce the “1 + 1>2” synergy effect, which increases the benefits of players. Therefore,
For better describing the game, we define the axioms and assumptions as follows.
Axiom 1. When both players of the game choose the sharing strategy, in addition to increasing the direct benefits of the entire supply chain, they will also obtain certain indirect benefits (similar to incentives), including a good corporate image and reputation, increased opportunities for cooperation with other companies, etc. (Akbulut, 2002; Yang et al., 2009; Srivastava, 2017). Therefore,
Axiom 2. The trust between members of the supply chain is the prerequisite for information sharing. When the trust becomes stronger, the amount of information shared will be greater and the quality also better (Yu et al., 2001; Yang et al., 2009).
Assumption 1. In the game, the internal factors such as operating conditions, employee literacy, managerial expertise and organizational structure of each enterprise are different. Therefore, the ability to collect and use information is also different. The coefficient
Assumption 2. While information sharing brings additional benefits to enterprises, it also calls into demand certain costs.
Assumption 3. When companies share their own private information, various potential risks will arise, such as business information leakage, moral hazards, etc., which will in turn affect their revenues (Jeong and Hong, 2019).
4.2 Static Analysis of Evolutionary Stability Strategies
In this game model, manufacturers and sellers are independent players. Replicated dynamic equations are formulated to obtain their respective optional evolutionary stability strategies.
Proposition 1. The replicated dynamic equation for the manufacturer to choose the sharing strategy is as follows:
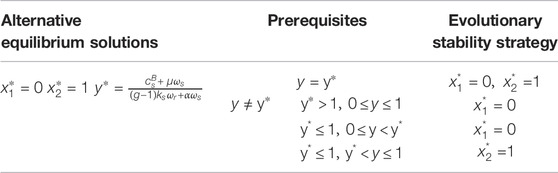
The following three equilibrium solutions can be obtained by setting Fx to zero:
Proof of Proposition 1
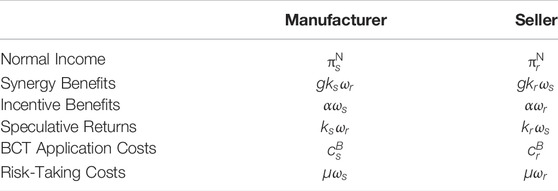
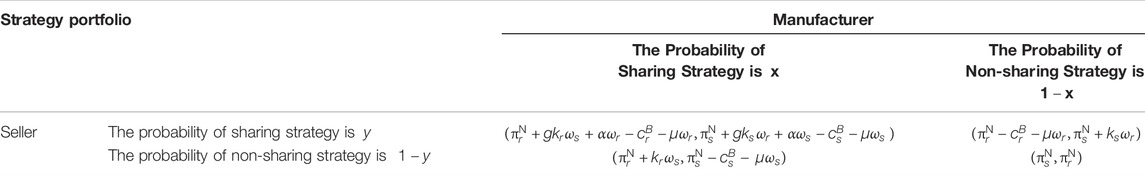
According to the pay-off matrix (see Tables 2,3), it is calculated that the expected benefits of sharing strategy adopted by the manufacturer is:
The expected benefits of non-sharing strategy is as follows:
Second, the average expected benefits adopted by the manufacturer is as follows:
Next, the replicated dynamic equation for the manufacturer to choose the sharing strategy is as follows:
Finally, substitute Eq. 2, Eq. 3, and Eq. 4 into Eq. 5 to get the final replicated dynamic equation.
Proposition 2. The replicated dynamic equation for the seller to choose the sharing strategy is as follows:
The following three equilibrium solutions can be obtained by setting Fy to zero.The detailed argumentation is omitted, as it is similar to that of Proposition 1.Based on the stability axioms of differential equations, it is concluded that when such conditions are satisfied as the first derivative
Finally, the corresponding dynamic evolutionary stability strategies can be found, which is shown in Table 4 and Table 5.
4.3 Dynamic Analysis of Evolution
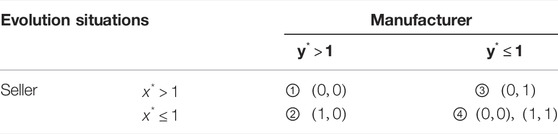
The information sharing between upstream and downstream enterprises along a supply chain is a dynamic evolutionary process, and is subject to the joint actions of the participants. Such joint actions form the combinations of evolutionary stability strategy, which are listed in Table 6 we make dynamic analysis on the evolution process:
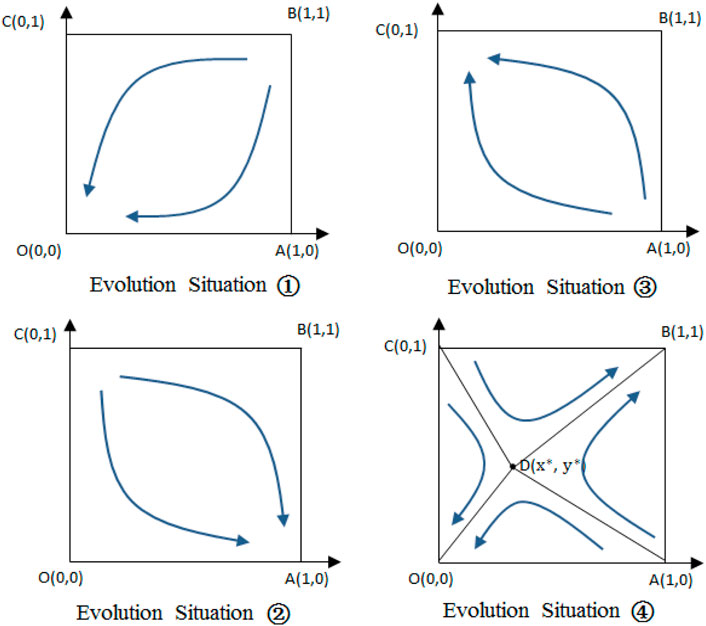
4.4 Evolution Situation 1
When the conditions
4.5 Evolution Situation 2&3
When the condition
In the beginning, the manufacturer or seller unilaterally adopts information sharing strategies and can obtain larger additional benefits. However, as the games are repeated, the input costs and risk-taking will gradually increase, and eventually both parties will become unwilling to share information. Therefore, in both cases, the final strategies for them are non-sharing, namely, the final stable point is (0, 0).
4.6 Evolution Situation 4
When the condition
The broken line ADC is the dividing line between two evolutionary stable points (0, 0) and (1, 1). The figure shows that in the OADC region, the evolution process converges to
The dynamic evolution diagrams of four Situations are shown in Figure 4.
5 Dynamic Analysis of Influencing Factors and Numerical Experiments
The evolutionary game analysis of the manufacturer and the seller shows that whether a player chooses to share information is closely related to the critical point
From the formula composition of the critical point , it is known that the value of the critical point is mainly affected by the six parameter values of each node enterprise on the supply chain, including technology application costs, risk-taking coefficient, incentive coefficient, synergy coefficient, the ability to absorb and utilize information, and the size of shared information flows. We use MATLAB to simulate and verify the evolution process of the game model’s replicated dynamic equations, and discuss the influence of various factors on the results of the information sharing strategy choice.
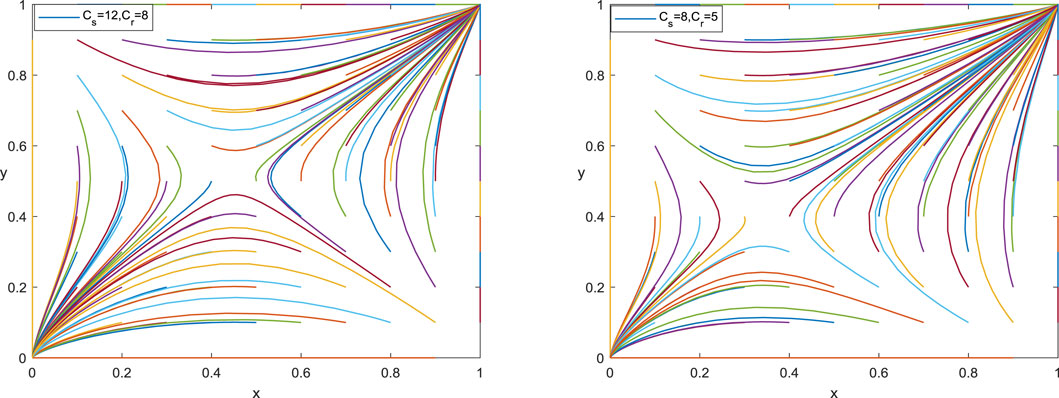
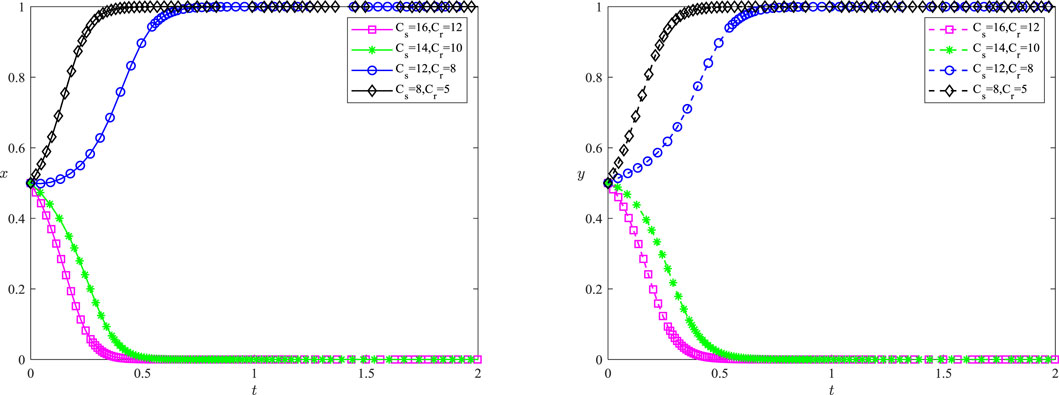
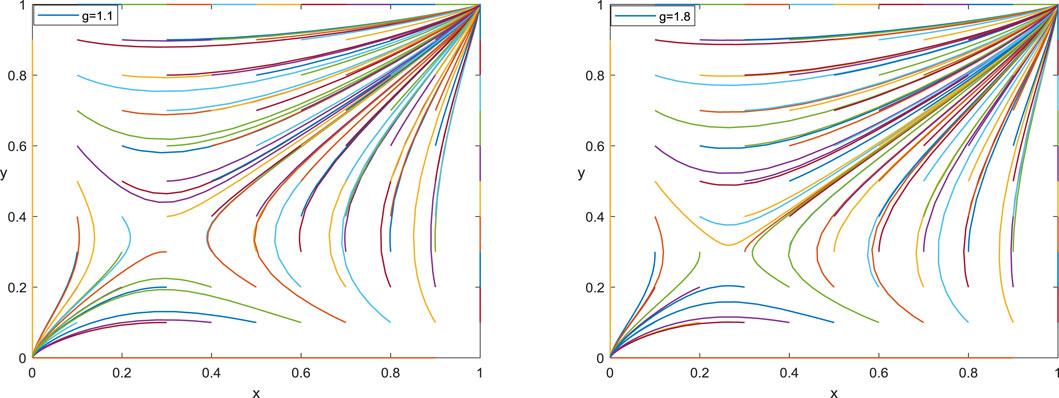
5.1 Technology Application Costs (C)
When the technical application costs of information sharing are reduced, the values of
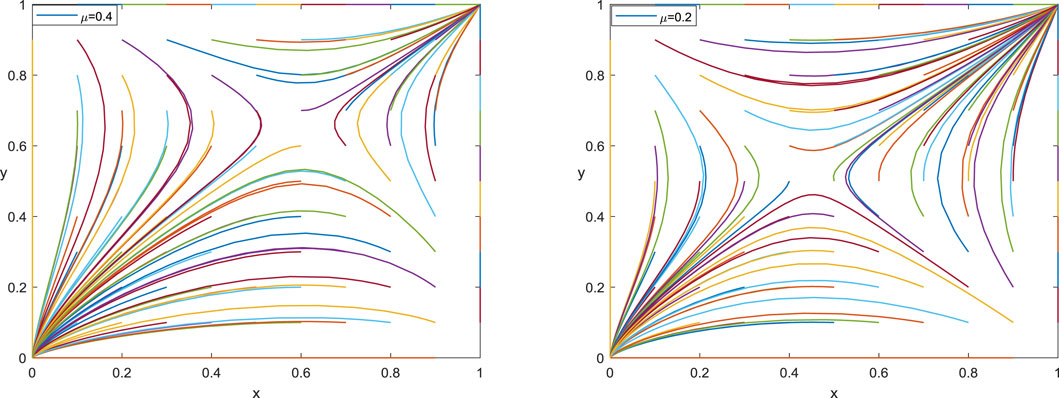
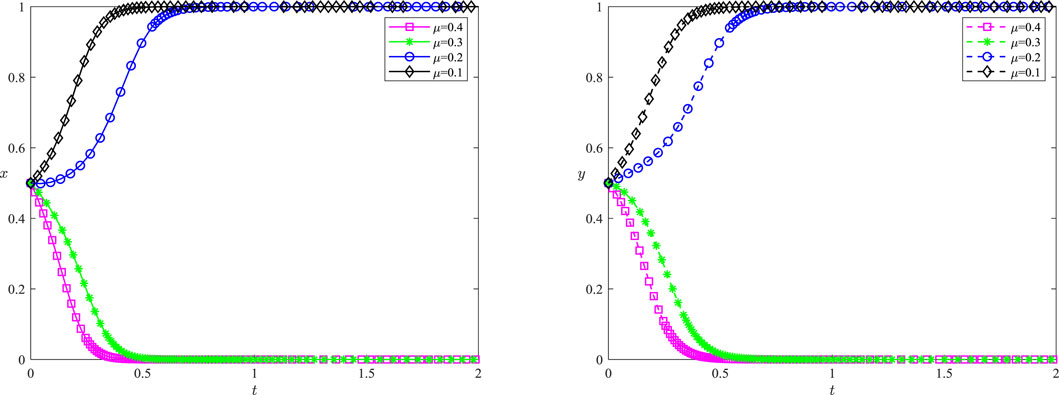
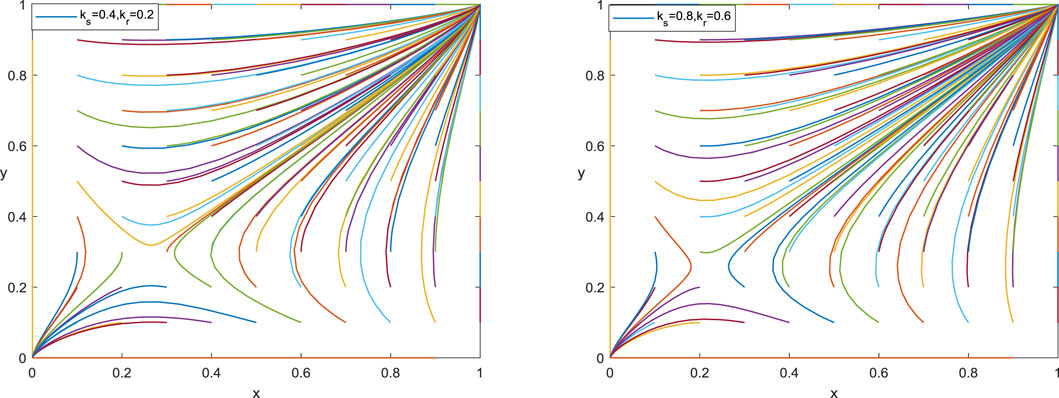
5.2 Risk-Taking Coefficient (μ)
When the risk-taking coefficient μ decreases, the critical point
5.3 Incentive Coefficient (
As the incentive coefficient
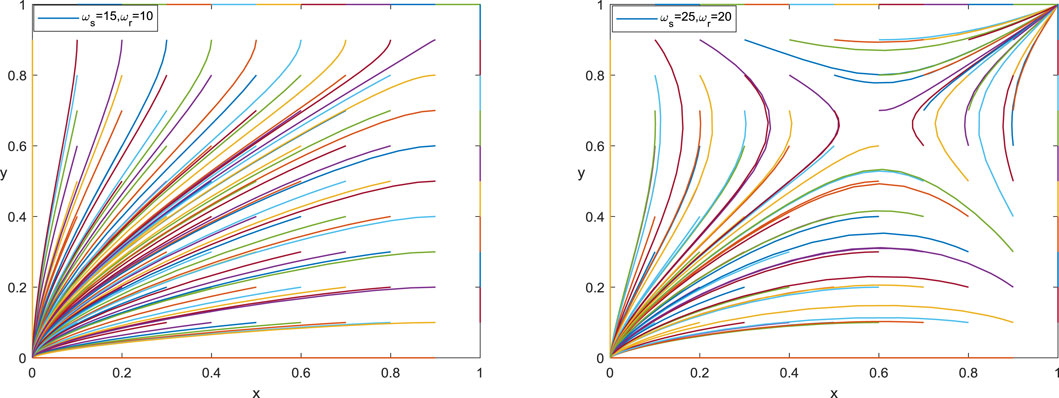
5.4 Synergy Coefficient (
When the synergy benefits
5.5 The Ability to Absorb and Utilize Information (
The ability of enterprises to absorb and utilize information determines the benefits they obtain through data exchange and affects their willingness to choose information sharing strategies. Figure 11 shows that when their ability to absorb and utilize information is better, the value of parameter
5.6 The Size of Shared Information Flows (
When the size of shared information flows
6 Conclusion
With the rapid development of information technologies in the Internet era, market competition has evolved into competition among supply chains. In order to improve the responsiveness of supply chains to market demand, reduce costs, and enhance efficiency, it is necessary to realize information sharing among the nodes on the supply chain. . To achieve the above objective, we use evolutionary game theory to studies the change of supply chain members’ choice of information sharing, analyzes the strategy shifts between participating companies by using replicated dynamic equations and phase diagrams, and discusses specific effects of six influencing factors on information sharing. In future, we plan to implement a complete platform for information exchange on the supply chain based on the emerging blockchain technology.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author Contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Conflict of Interest
Authors ZZ and ZY were employed by Ruiyou Information Technology (Shanghai) Inc.
The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Abeyratne, S. A., and Monfared, R. P. (2016). Blockchain Ready Manufacturing Supply Chain Using Distributed Ledger [J]. Int. J. Res. Eng. Technology 5 (9), 1–10. doi:10.15623/ijret.2016.0509001
Akbulut, A. Y. (2002). An Investigation of the Factors that Influence Electronic Information Sharing between State and Local Agencies [C]. Dallas: Eighth Americas Conference on Information Systems, 2454–2460.
Apte, S., and Petrovsky, N. (2016). Will Blockchain Technology Revolutionize Excipient Supply Chain Management [J]. J. Excipients Food Chemicals 7 (3), 76–78.
Aste, T., Tasca, P., and Di Matteo, T. (2017). Blockchain Technologies: The Foreseeable Impact on Society and Industry. Computer 50 (9), 18–28. doi:10.1109/mc.2017.3571064
Blockchain white paper (2019). Blockchain white Paper. [EB/OL].[2019-11-08]. Available at: http://www.caict.ac.cn/kxyj/qwfb/bps/201911/t20191108_269109.htm.
Cachon, G. P., and Lariviere, M. A. (2005). Supply Chain Coordination with Revenue-Sharing Contracts: Strengths and Limitations. Management Sci. 51 (1), 30–44. doi:10.1287/mnsc.1040.0215
Chauhan, S. S., and Proth, J.-M. (2005). Analysis of a Supply Chain Partnership with Revenue Sharing. Int. J. Prod. Econ. 97 (1), 44–51. doi:10.1016/j.ijpe.2004.05.006
Crosby, M., Pattanayak, P., Verma, S., and Kalyanaraman, V. (2016). Blockchain Technology: beyond Bitcoin [J]. Appl. Innovation 2 (6-10), 71.
Cui, R., Allon, G., Bassamboo, A., and Van Mieghem, J. A. (2015). Information Sharing in Supply Chains: An Empirical and Theoretical Valuation. Management Sci. 61 (11), 2803–2824. doi:10.1287/mnsc.2014.2132
De, S., Nau, D. S., and Gelfand, M. (2016). Using Game Theory to Study the Evolution of Cultural Norms. CoRR. Available at: https://arxiv.org/pdf/1606.02570.pdf.
Devika, K., Jafarian, A., Hassanzadeh, A., and Khodaverdi, R. (2016). Optimizing of Bullwhip Effect and Net Stock Amplification in Three-Echelon Supply Chains Using Evolutionary Multi-Objective Metaheuristics. Ann. Oper. Res. 242 (2), 457–487. doi:10.1007/s10479-013-1517-y
Fernández, C. P., Trucco, P., and Huaccho, H. L. (2019). Managing Structural and Dynamic Complexity in Supply Chains: Insights from Four Case Studies [J]. Prod. Plann. Control. 30 (8), 611–623. doi:10.1080/09537287.2018.1545952
Hu, B., and Feng, Y. (2017). Optimization and Coordination of Supply Chain with Revenue Sharing Contracts and Service Requirement under Supply and Demand Uncertainty. Int. J. Prod. Econ. 183, 185–193. doi:10.1016/j.ijpe.2016.11.002
Huang, B., and Iravani, S. M. R. (2005). Production Control Policies in Supply Chains with Selective-Information Sharing. Operations Res. 53 (4), 662–674. doi:10.1287/opre.1040.0203
Jeong, K., and Hong, J.-D. (2019). The Impact of Information Sharing on Bullwhip Effect Reduction in a Supply Chain. J. Intell. Manuf 30 (4), 1739–1751. doi:10.1007/s10845-017-1354-y
Kim, H. M., and Laskowski, M. (2018). Toward an Ontology-Driven Blockchain Design for Supply-Chain Provenance. Intell. Sys Acc. Fin Mgmt 25 (1), 18–27. doi:10.1002/isaf.1424
Lee, H. L., Padmanabhan, V., and Whang, S. (1997). Information Distortion in a Supply Chain: The Bullwhip Effect. Management Sci. 43 (4), 546–558. doi:10.1287/mnsc.43.4.546
Lehmacher, W., and McWaters, J. (2017). How Blockchain Can Restore Trust in Trade. [EB/OL].[2018-06-18]. Available at: https://www.weforum.org/agenda/2017/02/blockchain-trade-trusttransparency/.
Lehmacher, W. (2017). Why Blockchain Should Be Global Trade’s Next Port of Call. [EB/OL].[2018-06-10]. Available at: https://www.weforum.org/agenda/2017/05/blockchain-ports-globaltrades/.
Leng, K., Bi, Y., Jing, L., Fu, H.-C., and Van Nieuwenhuyse, I. (2018). Research on Agricultural Supply Chain System with Double Chain Architecture Based on Blockchain Technology. Future Generation Computer Syst. 86, 641–649. doi:10.1016/j.future.2018.04.061
Michael, P. (2018). Reassessing Expectations for Blockchain and Development [J]. Innov. Technol. Governance, Globalization 12 (1), 80–88.
Phelps, S., and Wooldridge, M. (2013). Game Theory and Evolution. IEEE Intell. Syst. 28 (4), 76–81. doi:10.1109/mis.2013.110
Queiroz, M. M., and Fosso Wamba, S. (2019). Blockchain Adoption Challenges in Supply Chain: An Empirical Investigation of the Main Drivers in India and the USA. Int. J. Inf. Management 46, 70–82. doi:10.1016/j.ijinfomgt.2018.11.021
Replicable Typical Experience and Practices (2020). Notice on Promoting the First Batch of Replicable Typical Experience and Practices by Supply Chain Innovation and Application Pilots. [EB/OL].[2020-04-27]. Available at: http://qdtb.mofcom.gov.cn/article/b/202004/20200402959299.shtml.
Sara, S., Mahtab, K., and Joseph, S. (2019). Blockchains and the Supply Chain: Findings from a Broad Study of Practitioners [J]. IEEE Eng. Management Rev. 47 (3), 95–103. doi:10.1109/EMR.2019.2928264
Shanley, A. (2017). Could Block Chain Improve Pharmaceutical Supply Chain Security [J]. Pharm. Technology 41 (3), 34–39.
Srivastava, M. K. (2017). Coordination Mechanisms for Supply Chain: a Review [J]. J. Supply Chain Management Syst. 6 (4), 22–32.
Xue, X., Dou, J., and Shang, Y. (2021). Blockchain-driven Supply Chain Decentralized Operations - Information Sharing Perspective. Bpmj 27 (1), 184–203. doi:10.1108/bpmj-12-2019-0518
Yang, Z., Aydın, G., Babich, V., and Beil, D. R. (2009). Supply Disruptions, Asymmetric Information, and a Backup Production Option. Management Sci. 55 (2), 192–209. doi:10.1287/mnsc.1080.0943
Yu, K., Cadeaux, J., Luo, N., Qian, C., and Chen, Z. (2018). The Role of the Consistency between Objective and Perceived Environmental Uncertainty in Supply Chain Risk Management. Imds 118 (7), 1365–1387. doi:10.1108/imds-09-2017-0410
Yu, Z., Yan, H., and Edwin Cheng, T. C. (2001). Benefits of Information Sharing with Supply Chain Partnerships. Ind. Manag. Data Syst. 101 (3), 114–121. doi:10.1108/02635570110386625
Zelbst, P. J., Green, K. W., Sower, V. E., and Baker, G. (2010). RFID Utilization and Information Sharing: the Impact on Supply Chain Performance. J. Business Ind. Marketing 25 (8), 582–589. doi:10.1108/08858621011088310
Zelbst, P. J., Green, K. W., Sower, V. E., and Baker, G. (2010). RFID Utilization and Information Sharing: the Impact on Supply Chain Performance. The J. Business Ind. Marketing 25 (8), 582–589. doi:10.1108/08858621011088310
Keywords: information sharing, blockchain, game theory, MATLAB simulation, suply chain
Citation: Tang Q, Zhang Z, Yuan Z and Li Z (2022) The Game Analysis of Information Sharing for Supply Chain Enterprises in the Blockchain. Front. Manuf. Technol. 2:880332. doi: 10.3389/fmtec.2022.880332
Received: 21 February 2022; Accepted: 22 March 2022;
Published: 14 June 2022.
Edited by:
Bingqing Shen, Shanghai Jiao Tong University, ChinaCopyright © 2022 Tang, Zhang, Yuan and Li. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Zeng Zhang, Zhangzeng@kuulabu.com
 Qian Tang
Qian Tang Zeng Zhang
Zeng Zhang Zhonglei Yuan
Zhonglei Yuan Zhen Li4,5
Zhen Li4,5