- University of Salford, Salford, United Kingdom
The mechanisms and evolving standards collectively known as self-sovereign identity (SSI) offer the prospect of a decentralized Internet by providing a central pillar for a human-centered data ecosystem (HCDE). Once established this technology promises to afford participants the same agency in the digital realm as individuals experience in the real world. Investigation suggests that the domain is now sufficiently mature to realize practically the principles of SSI, but in order to achieve sustainable adoption, significant design focused work needs to be undertaken at the interface layer. This paper presents recent practice-led research designed to project current SSI prototypes to scale through conceptual modeling, preliminary user interface, and critical analysis. This research introduces the term sovereign boundary mechanism (SBM), a standardized collection of SSI interactions, which can be described as a metaphorical ring of sovereignty between the participant and the wider network. Within this model, participants control identity, relationships, and data streams and access control. This research identifies the domains of interaction and the minimum required objects for a full-scale SSI engagement through an SBM. It defines the component parts and functionality of a wider HCDE which require further consideration, and it identifies emergent concepts for which a participant may lack mental model and understanding. The research considers human computer interaction (HCI) theory across internalized, external, and distributed cognition, arguing that the current trajectory of SSI requires significant internalized representations, prior knowledge, and participant responsibility. This research argues that these elements are problematic and pose a significant barrier to sustainable adoption. In conclusion, this research suggests that the decentralized community needs to recognize the obstacle potentially posed at the interface layer and engage in collective standardization, strategy, and design thinking to increase the probability of sustainable adoption.
Introduction
The management of digital identities and personal data represents a formidable challenge for the 21st century; issues of privacy, inference profiling, surveillance capitalism, GAFA monopoly, democratic interference, and the lost opportunities of big data are significant. Many envisage a decentralized alternative to the centralized network, one that places the human at the center of data streams, facilitating transparency, agency, and negotiated access to personal data. Self-sovereign identity is a collection of concepts and standards that promises to emancipate the everyday user from the asymmetrical relationships observed across today’s Internet. By establishing and controlling persistent digital identities and exchanging digital credentials, relationships and trust networks can be established. The decentralized nature of the technology and the subsequent requirement for the individual to manage and protect what is a complex decentralized key management system pose several interactive design challenges. This paradigm shift introduces unfamiliar concepts and raises issues of missing metaphor and mental model. If SSI is to become accessible and sustainable, we must investigate and understand SSI applications and case studies and interactions and identify the foundation design patterns needed to manage and transact personal data through digital identity.
This paper presents what is part one of a two-part publication of outcomes from doctoral research conducted between 2017 and 2020. The research poses a primary question: can a sustainable technology be established to allow for individual agency within a decentralized Internet? Two additional questions were then derived. The first considered usability at the interface layer and asks: can an interface layer for a decentralized Internet be designed to allow for accessible interaction? And the second considered value proposition and adoption and asks: how might a decentralized Internet provide value, emerge, and be adopted? As this work progressed, it became evident that the trajectory toward a decentralized Internet would require the development of a human-centered data ecosystem (HCDE): a central pillar of which could be provided by the emergent domain of self-sovereign identity (SSI). This paper presents the academic framework, method, findings, and recommendations relating to the investigation of usability and accessibility at the interface layer for SSI. A second paper presenting the findings relating to value proposition and adoption can also be found within this journal.
Pre-Assumptions
It is not the intention of this research to advocate privacy concern or lobby for the adoption of sovereign identity decentralized technologies. The aim of this research is to consider and reflect the current proposals for SSI interactions and to extend current prototypes to scale in the context of the defined principles, required mechanisms, and evolving standards. The objective has been to enter the problem space as a designer, extend its current position, and then reflect on the outcome. That said, there are a number of accepted arguments on which this work is constructed. It is accepted that the broad concept of network centralization means giving up control of our personal information and identity (Moglen, 2013; Van Kleek and O’Hara, 2014) that the advent of the centralized model poses a significant threat to our collective and individual privacy (Solove, 2008) and that personal data are now exploited by capital in order to leverage influence over our daily lives (Schneier, 2015; Zuboff, 2015). It is accepted that there is a decentralized alternative to the centralized model which will offer a participant greater agency over elements of their personal data (Haddadi, 2015; Hornung et al., 2015; Mortier, 2014) that identity can be established through the ownership and control of personal data (IIW, 2019) and that an identity layer is integral to a sovereign engagement with the wider network and evolving Internet (Cameron, 2005; Allen, 2016; Tobin and Reed, 2016). There is an awareness of what could be considered to be a moderate bias, and every conscious effort has been made to prevent it from influencing the design of this research, the methods of data gathering, and the analysis and interpretation of results.
Theoretical Framework
When exploring the interface layer for SSI, this research considers the wider academic context. The domain of human data interaction (HDI) (Mortier, 2014; Haddadi, 2015) recognizes the pervasiveness of computing in our data driven society. The theory argues that human computer interaction (HCI) has traditionally focused on interactions between humans and computers as artifacts. However, with the rapid evolution of human’s interacting predominantly with data, a different academic perspective is required. Moritier (2014) defines HDI as “placing the human at the center of the flows of data, providing mechanisms for citizens to interact with these systems and data explicitly” (p. 1). The concepts of HDI illustrate the opaque mechanisms used to process personal data and the hidden inferences and subsequent feedback loops. This theory argues that a user requires legibility to understand the ambient ways in which data are processed and utilized, that agency is required to control, manage, and permit access to personal data, and that users require a means to negotiate the terms under which their data can be used. The concept of SSI provides the mechanisms required fulfilling the principles laid down by HDI and as such HDI can act as a suitable overarching academic domain.
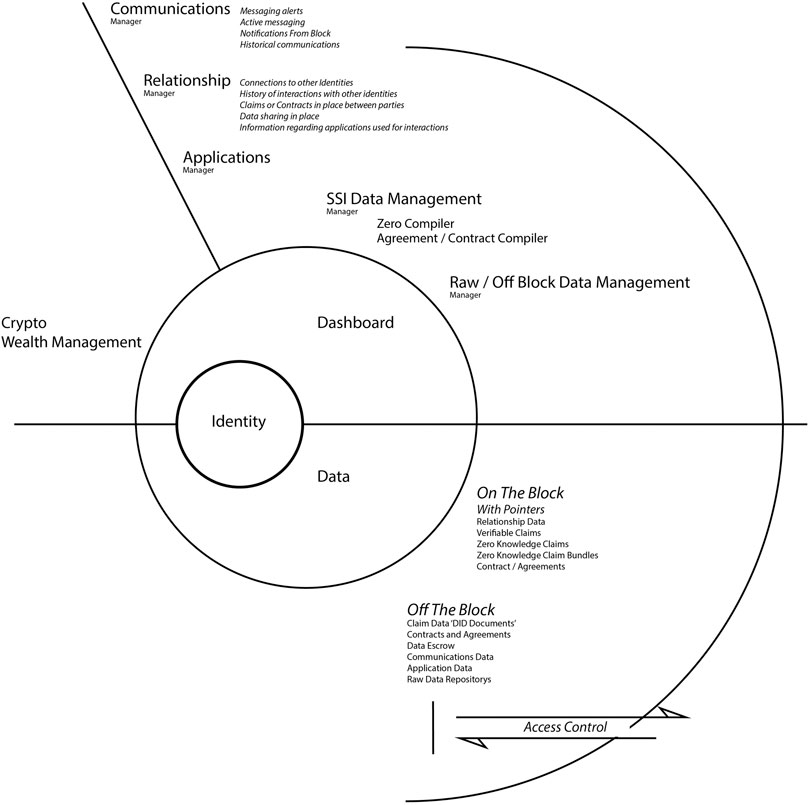
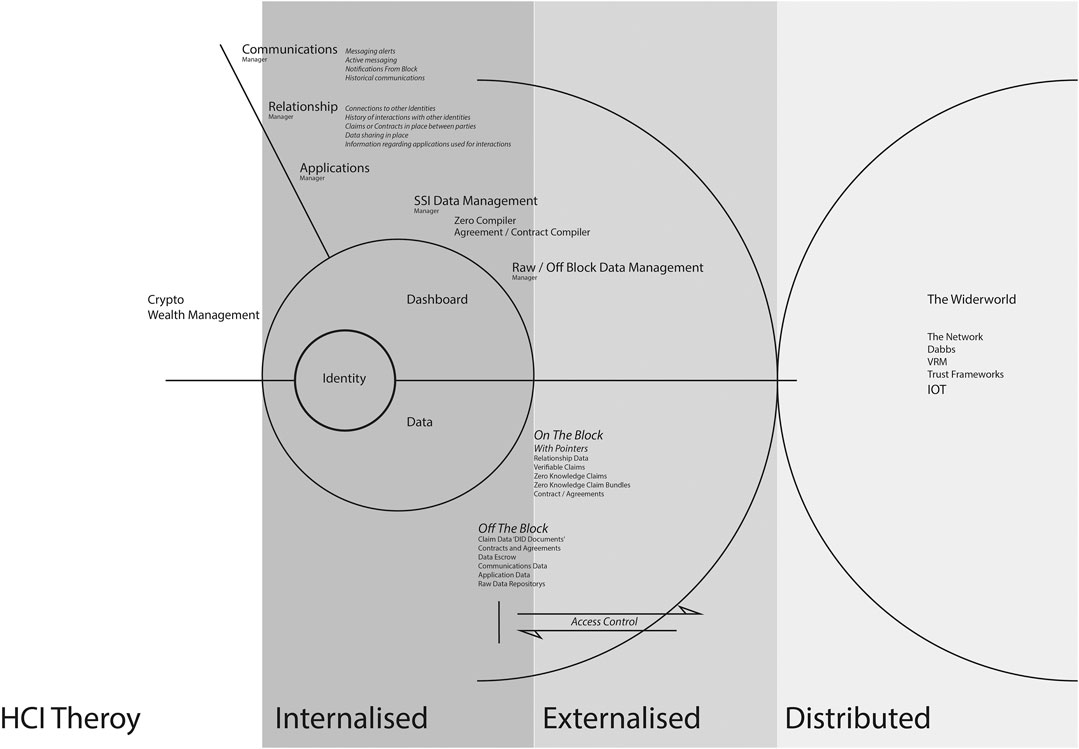
As the interface layer for SSI interactions is investigated, it becomes evident that the paradigms of cognitive theory found within human computer interaction (HCI) are highly relevant (Harrison et al., 2007; Rogers, 2012). The current trajectory within SSI suggests that participants will manage their affairs independently through a digital wallet, engaging what is coined within this research as a sovereign boundary mechanism (SBM). These are the core interactions enabled through SSI, found at the center of a wider human-centered data ecosystem. An SBM represents a standardized set of concepts, tools, and user representations that allows for an interaction with a decentralized Internet, through a HCDE with SSI at its core.
Figure 1 illustrates the component parts of a sovereign boundary mechanism. The inner core consists of identity, access to core functionality, and personal data. The second shell consists of the accessible applications and mechanisms required to manage personal identity, credentials, data, and contracts, together with the management of data storage and access control. The outer ring depicts the sovereign boundary between the participant and the wider network.
The SBM model represents a standardized collection of interactions that the participant independently controls. This is a strict task-based engagement that arguably presents new distinct ideas and original concepts. The notion of sovereignty at the core of this model equates to individualism and given the gravitas of the personal data being transacted, the assumption can be made that a strong internalized understanding of the domain will be required to engage initially and sustain participants. This research recognizes the value of the classical HCI theory of internalized cognition (Craik, 1943; Norman, 1986; Kirsh, 1997; Johnson-Laird, 2001), considering participant mental model, internalized understanding, and processing of information at both the interface layer and within the wider data ecosystem. There are long standing arguments that challenge the validity and value of specifically internalized cognitive psychology in HCI to inform the design of computer systems and interface (Carroll, 1991; Landuer, 1991). This research suggests that internalized HCI cognitive theory is still an important consideration, not in the pursuit of an overarching set of design rules for the development of general interactive experiences, but as a framework to map and design the required internalized understanding and core functionality of a specific and standardized domain. This position is supported by Payne (2003) who argues that internalized cognitive processes and mental model are valid when considered in a specific context.
As an SBM engagement progresses outwards toward transactions with the wider network, the required internalized cognitive understanding and processing of the core concepts migrate into the functional management of identity, relationships, credentials, and data across a spectrum of scenarios. When considering the design of the tools and mechanisms to facilitate this, the theories of externalized cognition are important. The notion of external cognition centers around the argument that “when individuals are solving problems, human beings use both internal representations stored in their brains and external representations, recorded on a paper, on a blackboard, or on some other medium” (Larkin and Simon, 1987, p. 66). Scaife and Rogers (1996) describe computational offloading, the way in which external representations change the amount of cognitive effort needed to carry out a task. They go on to describe graphical constraining, arguing that external representations can be designed in such a way as to limit the possible inferences that can be made in completing a task, reducing the load on internal memory allowing more space to plan the next move. There is the notion of re-representation, a consideration of how different external representations with the same abstract structure make the solving of problems easier or more difficult. They argue for the theory of cognitive tracing that an external representation should be interactive and that a user should be able to mark and annotate to aid understanding and to build external memory (Scaife and Rogers, 1996). O’Malley and Draper (1992) offer interesting arguments through which to consider the interplay between internalized and externalized representations when interacting with systems. They suggest that the internalized representation is not only knowledge of a systems function but also knowledge of where to look and how to find further information through the externalized representations.
It is the interplay between internalized and externalized cognition that needs to be understood and managed in the development of an interface layer for SSI, in what is arguably a significant paradigm shift in network engagement that by its very nature requires a degree of internalization. It is the balancing of these cognitive processes within the context of adoption theory (Rogers, 1962) and the technology life cycle (Moore, 1991) that will determine the probability of achieving accessible, sustainable technologies and tools for SSI within a wider human-centered data ecosystem.
When contemplating the cognitive HCI theory relative to SSI and a sovereign boundary mechanism, it is important to consider the interactions within the wider ecosystem. A human-centered data ecosystem has the potential to comprise a spectrum of participants, both human and machine, in a number of environments both virtual and physical. Users may engage with applications in emergent ways, as individuals or as a collective. This spectrum of activity and interaction involves interpretation and utilization of mechanisms relative to context, so the theories of situated action need to be considered within the equation (Suchman, 1987). As interaction across the wider network will include group and collaborative coordination, the theory of distributed cognition also needs to be considered (Hutchins, 2000).
This research argues that an accessible model of interaction for an SSI driven HCDE will contain internalized, externalized, and distributed cognitive processes and that understanding, mapping, and optimizing the relationships between these elements are critical for a sustainable, functional interface layer. This utilization of a range of cognitive theories across a border interaction utilizes what Harrison et al. (2007) describes as a phenomenological matrix, a collection of HCI theory applied pragmatically where and when it is required.
Self-Sovereign Identity
The concept of self-sovereign identity solves one of the most challenging problems facing the Internet: the capability to establish, own, and control a persistent verifiable identity. SSI can be defined as the following: “a digital identity that is owned and controlled by an individual, company, or machine that has no reliance on any centralized authority. The identity is persistent and can never be taken from its owner. The identity is part of a wider ecosystem, where relationships can be built, trust can be developed, and identity attributes and data can be exchanged under the complete control of the sovereign identity.” The concept of a wider ecosystem is important, as once a user can control an identity, the concepts of SSI then allow the user to establish independent unique relationships and private communication channels with peers across the network. It allows for the requesting, issuing, and distribution of verifiable credentials. The ecosystem allows for the development of trust networks that are judged appropriate, dependent on a given situation. The realization of SSI is considered to be Web 3.0 and to many is inevitable (Tobin and Reed, 2016). The core principles of SSI can be traced back to the work of Kim Cameron in his Laws of Identity (Cameron, 2005). These principles of digital identity were then evolved further in the context of SSI by Christopher Allen (Allen, 2016). Allen defined a number of principles that need to be satisfied in order for a technology to be considered self-sovereign.
• Existence. Users must have an independent existence.
• Control. Users must control their identities.
• Access. Users must have access to their own data.
• Transparency. Systems and algorithms must be transparent.
• Persistence. Identities must be long-lived.
• Portability. Information and services about identity must be transportable.
• Interoperability. Identities should be as widely usable as possible.
• Consent. Users must agree to the use of their identity.
• Minimalization. Disclosure of claims must be minimized.
• Protection. The rights of users must be protected.
The guiding principles defined by Christopher Allan together with those established by the field of human data interaction (HDI) (Mortier 2014; Haddadi, 2015) have been considered alongside the wider objective of the decentralized movement and evolving technologies and standards to define the high-level functionality and interactions required at the SSI interface layer.
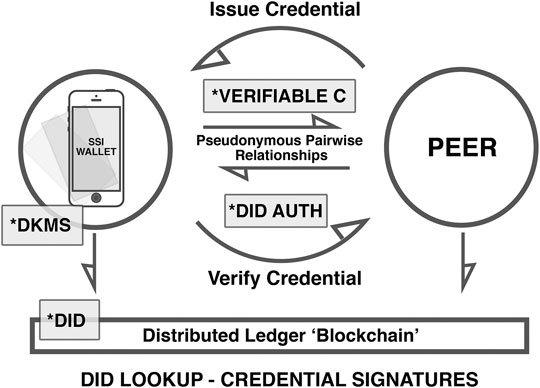
Figure 2 illustrates the component parts of a self-sovereign identity ecosystem, establishing relationships and engagement between two sovereign peers through a pseudonymous pairwise relationship, the exchange and authentication of credentials, the writing and retrieval of digital identifiers, and credential signatures from a dedicated blockchain. When contemplating an interface layer for SSI, it is important to consider it functioning at scale; Figure 2 defines the core mechanics of SSI, but when developing this model within a sovereign boundary mechanism and indeed a wider human-centered data ecosystem, a practical engagement will require additional, peripheral functions and interactions.
The Need to Build a Conceptual Model
Insight into usability issues surrounding personal data protection for the everyday participant can be found in previous research. The paper entitled Why Johnny Can’t Encrypt (Whitten and Tygar, 2005) investigates email encryption software and argues that despite a well-designed interface, a lack of fundamental mental model and understanding prevents Johnny from successfully encrypting his communications. The research suggests that new methods of testing are required when developing interactions that contain novel concepts and ideas. It could be argued that this work draws striking contemporary resemblance to the design space surrounding SSI. Both involving a complex collection of novel interactions, an unfamiliar digital environment, and the transaction of information with a high personal value. When investigating the current decentralized domain, there is a sense that a technically focused development community is overlooking the inevitable user experience and accessibility issues. There is evidence supporting this assumption. In the research conducted by Dunphy and Petitcolas (2018) entitled A First Look at Identity Management Schemes on the Blockchain, the principles of Kim Cameron’s Laws of Identity (Cameron, 2005) are used to evaluate several SSI projects. In conclusion, it is argued that none of the projects currently satisfy Cameron’s 6th law, Human Integration, and in summary state that “there is a noticeable lack of contextual understanding relating to the user experience elements of the schemes we encountered” (Dunphy and Petitcolas, 2018). Developers of SSI applications need to consider the fundamental principles of the diffusion of innovation (Rogers, 1962) which recognizes the requirement for a participant to understand a new product offering, its function, and the value found within its concepts; this needs to be considered in the context of the persuasion of a new user when making a decision to adopt or reject a novel innovation.
This research has concluded that the technical components are now in place to build a functional human-centered data ecosystem with a central component of SSI at its core. Developing an accessible interface layer for such an ecosystem is now a design problem, one which needs to balance the cognitive load required for engagement, with the value proposition decentralized tools and services offer. When we consider the cognitive load, we need to understand the model of interaction, its component parts, and the journey users take to achieve their aims and objectives. We can then begin to map the required user understanding and scaffold for a mental model. The evolving structure can then be interrogated to examine the frictions, while iteratively evolving and improving the design. The first stage in this investigation is to establish a conceptual model (Johnson and Henderson, 2002), the details of which are communicated in the following section.
Methods
The following section describes the methods employed to investigate the interface layer for SSI through practice-led research. This is a component part of a larger mixed methods design (Creswell, 2003) influenced by Design Theory for Mixed Methods in HCI (Turnhout, 2014). Prior to the design of this component, the pertinent literature was considered, and an investigation of historical and contemporary decentralized artifacts was undertaken. Semi-structured interviews with experts from the decentralized field were conducted. Also, interviewed were practitioners from the domain of user experience and user interface design. Figure 3B illustrates how this work sits within a wider research study.

FIGURE 3. (A) Initial User Interface and (B) All component parts of the wider research study. The highlighted section represents the practice-led component described within this paper.
Research Phases
This component of research was undertaken in 4 phases:
Phase One: Defining a Conceptual Model
The current position of SSI comprises of a clear description of principles, defined concepts, developing standards, and preliminary prototypes. The objective of this practice-led component is to extend this current model to a scalable analog interaction and then critically analyze the result. As such, phase one engaged a conceptual modeling method (Johnson and Henderson, 2002) which suggests that practitioners should “begin by designing what to design” (p. 1). The method describes a process which results in a structured text and table-based outcome. The first step is to define the application’s purpose and high-level functionality. Once this is established, the process continues with the definition of the major concepts and vocabulary. The next stage considers the conceptual objects visible to the user through what is termed as an objects and operations analysis. This process investigates the objects users manipulate, their attributes and operations, and the relationships between them. The method then progresses to a task-to-tool mapping exercise. This considers how a participant uses an application to carry out tasks engaging the visible objects, attributes, and operations. Within this practice, the development of a preliminary user interface reflects this stage.
An important understanding within the conceptual modeling process is that it is agile and flexible. As the designer progresses to develop a user interface and evaluation methods are employed (Nielsen, 2005), the conceptual model is continually updated and refined.
Phase Two: Developing a Preliminary User Interface
With a defined conceptual model in place, the method progressed to establish a preliminary user interface in a wireframe format. The purpose of the wireframe is to visualize the defined objects and their relationships, while developing the minimal interface touch points to enable the required interactions. The guiding principle in developing the user interface is simplicity. There are no radical design choices and the process utilizes existing table-based interface design patterns.
Phase Three: Critical Reflection
Once a conceptual model and preliminary user interface had been established, a critical reflection was undertaken by the researcher. This was consciously conducted from the standpoint of the user. A user journey was considered across the full range of functionality at an introductory level. Efforts were made to uncover significant interactive friction, while identifying original concepts, metaphor, and the participant mental model. In addition, the critical reflection identifies elements of a wider human-centered data ecosystem, identifying missing components which may be required for a full spectrum of interaction.
Phase Four: Evaluation Focus Group
Once established the conceptual model and preliminary user interface can be used to communicate the concept of the domain, its components, the required objects, and the scope and scale of the required user interaction. The developed model was subjected to an additional critical analysis, this time through consultation with usability experts and interface designers. The objective of this evaluation was to consider a first cycle of development, investigate the integrity of the fundamental concepts, and provide an unbiased perspective from a practitioner’s standpoint. In order to facilitate this evaluation, a workshop was designed incorporating a focus group. Guidance was taken from Finch and Lewis (2003) in its design and planning. Participants were selected locally, in the Manchester United Kingdom vicinity, for their reputation, experience, and expertise. A website was authored together with Supporting Materials which were then distributed to participants in advance of the workshop. The workshop began with a detailed presentation of the research, the concept of the decentralized Internet, and its principles and objectives. An overview was given of existing technologies, concepts, and standards. A detailed explanation was given regarding the practice-led component of research, including the conceptual model and initial UI. Following the presentation and Q and A, a focus group was conducted based on the following topics of discussion:
• Participant Understanding
• Views on the Complexity of the Interactions
• Mental Model and Metaphor
• Building Accessibility
• The Potential for Automation
Results
The Conceptual Model
The following section presents results for each stage of the conceptual modeling process.
Purpose and High-Level Functionality
The following list defines the purpose and the high-level functionality of a standardized sovereign boundary mechanism, considered in the context of a wider human-centered data ecosystem, the principles of human data interaction and self-sovereign identity, and the evolving technologies and standards.
• Manage digital identities
• Manage connections and relationships
• Establish boundary control
• Facilitate transparency of data usage
• Facilitate secure encrypted channels
• Facilitate credential exchange and management
• Transact data with minimal disclosure
• Support trust networks
• Facilitate portability
• Enable data repository and binding
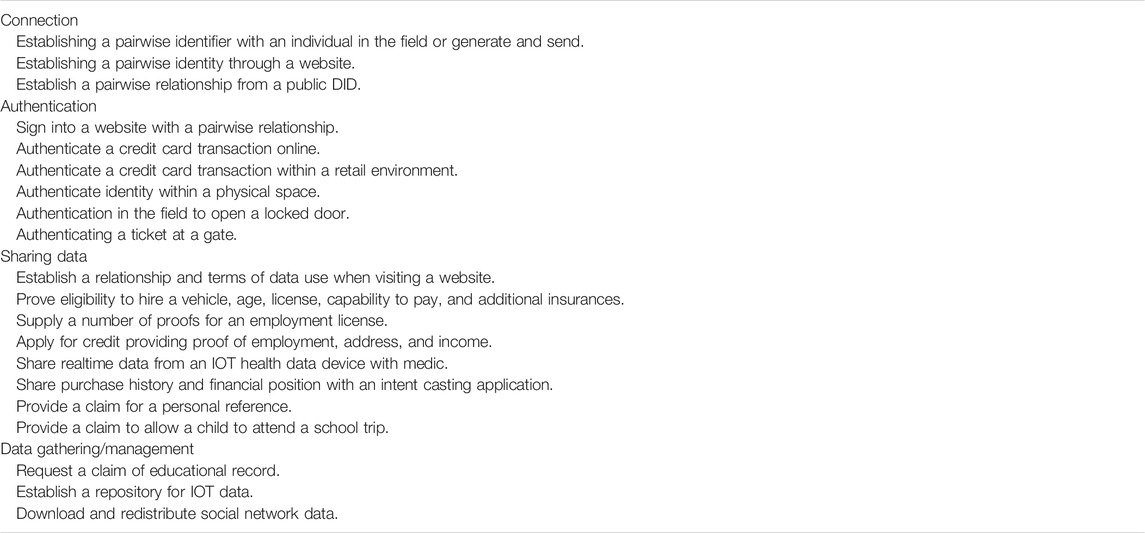
SSI Case Studies and User Scenarios
Table 1 presents an overview of case studies and user scenarios defined as part of the conceptual modeling process. Each has been explored through the development of a user journey and reflects core interactions which might be found in a broader human-centered data ecosystem.
Objects and Operations Analysis
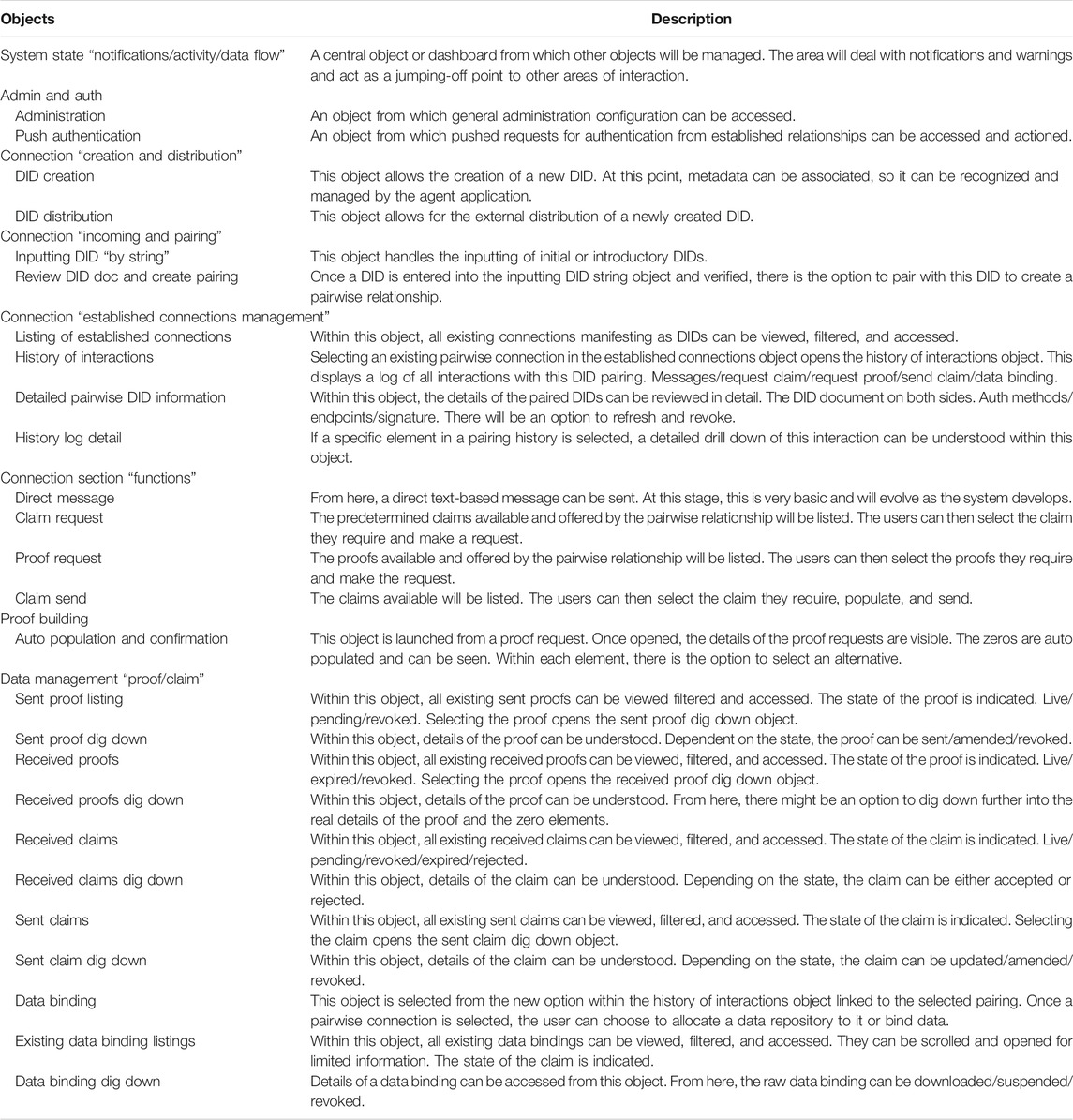
The objects and operations analysis requires the identification of the conceptual objects that a participant can see and manipulate. Once the objects are identified, their attributes are specified and listed alongside their relationships to one another. As the conceptual model develops, outstanding and resolved issues are also listed. Currently, 27 objects have been defined and a brief overview of each is listed in Table 2.
Initial UI Development
With an objects and operations analysis defined, a full initial user interface has been developed. A low-resolution image of which can be seen within Figure 3A. This initial user interface is a wireframe utilizing a simple table-based layout. A panel for each of the identified objects has been created, supplemented by a description of the required attributes and functions. To aid in the reading of the wireframe, a colour key has been provided highlighting the identified spheres of interaction; these relate directly to the objects and operations analysis. A PDF version of the wireframe can be found as Supplemental Material of this paper. INITIAL_SSI_UI_DEV_LOCKWOOD__2020.pdf.
Critical Reflection
The conceptual model suggests that a minimum of 27 objects are required for a functional sovereign boundary mechanism. When observing the resulting UI, it is evident that this is complex, and in terms of a cognitive load, it can be debated that it is significant. The user experience requires a clear interpretation and understanding of the system state, within which the interactions are reliant on complex sequences. There is a number of sub-domains within the system and a general understanding of the majority of objects and their relationships would be necessary in order to enable confident engagement. In subsequent phases of development, efforts can be made to reduce complexity, and many of the system processes might be reordered, automated, or streamlined following usability testing. It remains, however, that a human-centered data ecosystem through self-sovereign identity, offering full agency through a sovereign boundary mechanism, presents a collection of original concepts and interactions, which may prove challenging in the context of initial and sustained adoption, interactive friction, and participant mental model.
This research suggests, based on the evidence derived from the conceptual model and subsequent UI, together with the defined principles of HDI and SSI, coupled with the value of personal data, that a sovereign boundary mechanism requires a considerable amount of internalized understanding before meaningful interaction can be achieved. The introduction of such a system introduces considerable friction and is a backwards step in the context of contemporary user interaction design. The notion of sovereignty and independence places a great weight of responsibility on the participant, which potentially results in what is discussed later in this paper as the paradox of the sovereign boundary mechanism.
It is important to separate what can be argued to be a high friction demanding user interface experience and the internalized knowledge and understanding of system and concepts that will be required in order to engage. Critical reflection suggests that the dominant issue in any future development of an analog self-sovereign identity system is not the physical interface design. Many office management tasks, media editing tools, and social networks require engagement with complex UI structures and interactions. This research concludes that in this context, the dominant issue is that of the understanding of concepts and mechanisms. Within a sovereign boundary model of interaction, there are potentially multiple novel concepts that lack precedent, existing mental model or metaphor to allow a participant to build a sufficient internalized understanding.
Below is a non-exhaustive list of potential original concepts which may prove alien to a new participant:
• Identity sovereignty
• Multiple identifiers
• Individual unique relationships with peers
• Peer to peer relationships and equality
• Establishing individual relationships to engage services
• The metaphorical boundary between the participant and the wider network
• The understanding of and the managing of static and dynamic data
• Data binding
• The blockchain as a source of truth
• Verifiable credential and the cascade of validity
• The issuing of credentials
• The concept of proving truths through partial data disclosure
• Finding faith in distributed storage
• Finding faith in one’s self and the responsibility of managing presence
• Understanding the relationships between digital and physical manifestations
Initial critical analysis of the model also raises some interaction challenges and potential incomplete mechanisms. These issues manifest around the edges of the core interaction and include the following:
• Direct messaging: issues concerning machine readable text. How can messages be interpreted, processed, and responded to at scale?
• Claim/credential sending: this would require a repository of standard templates across different categories.
• Claim/credential request: there would need to be a means of transmitting the claims that the connected entity provided.
• Machine readable T&C: there needs to be a means of providing machine readable T&C and potentially contracts. These need to go beyond the notion of Mary Hodders Customer Commons (Hodder, 2019).
• Dynamic data streams: there needs to be a means of understanding the data streams and usage around data binding.
• Progressive trust development: how can the initial building of trust through proofs be streamlined?
• Semantic layer: who defines the semantic layer to link claim elements to zero knowledge proofs?
Focus Group
The focus group included ten prominent individuals from the user experience and interface domain. Five predefined questions were posed to participants following prior communication of SSI technology and the results of the conceptual model and preliminary user interface through a purpose built website. There now follows a summary of the discussion and emergent themes.
From a Participant Perspective, How Understandable Are the Concepts Surrounding Self-Sovereign Identity?
Discussion was centered on the idea that the core concept of relationship building and the proving of something with a verifiable credential was solid, but the peripheral mechanisms may prove problematic. Comments were made regarding the paradigm shift from asymmetric relationships to peer to peer engagement. Concerns were raised that the concept of having individual relationships for every transaction might prove difficult to grasp. First-hand experiences of the development of money sending applications were discussed, highlighting the problems encountered engaging users with one single new concept. It was argued that SSI posed an interesting challenge, as the overall system incorporated multiple new concepts and mechanisms. Arguments were made that these concepts need to be placed into context with clearly understandable use cases and value proposition. Concerns were raised with regard to the abstraction of many of the components of interaction and that in its current form, only the most committed privacy advocate or technology enthusiast would have the drive to fathom the conundrum. The consensus was that the system needed simplification, it needed to be placed in context, and that niches of value needed to be found in order to drive interest and engagement.
What Are Your Views on the Complexity of These Interactions?
The consensus to this question, in the context of the system presented, was that the current manifestation is over complex, that many of these issues can be resolved, but that a considerable reduction in friction needs to be achieved through systematic redesign and usability testing. It was argued that a balance between exposed and hidden interactions needs to be considered if a participant is to be able to initially engage with the system. An interesting debate ensued with regard to how much the user needed to see to comprehend the value, to understand the systems functions, to trust the system, and ultimately to develop and engage a mental model. This was considered to be a key set of variables that would need to be crafted within a further design cycle.
How Do We Build Something That Is Accessible?
The debate continued in the vein of the exposure to the under-laying mechanism, complexity of interaction, and motivation to engage. It was recognized that this would require a fine balance considering initial introduction of the technology through common place usage. The issue of exclusion and the prospect of a large proportion of society not being able to access SSI due to its complexity, initial friction, and the weight of responsibility were discussed in detail. The sentiment being “just because I can, does not mean I would want to,” a conversation continued to discuss on boarding, with ideas being suggested that existing users of large public or corporate systems might be automatically enrolled into an SSI system, only realizing this once additional products and services were offered. This would be seeded by an existing base set of identity credentials. The debate moved to foundation identity credentials and how they could be established and the need for some kind of solid ground that all parties could trust and build upon. There was some interesting conversations regarding trust in one’s own capabilities and the risk this entailed and from a user’s perspective having different, sometimes compromising identities linked to one sovereign system. The consensus was that the interactive friction needed to be reduced, automatic migration to such systems might aid in adoption, and people needed to trust and understand the system, while having confidence in their own competence and capabilities.
Could You Share Your Thoughts on Mental Model and Metaphor?
The general consensus was that in its current form, the system would be difficult to comprehend and understand. There are potentially multiple original concepts all of which need to be considered and simplified relative to a holistic user experience. It was argued that a system of this kind needed to be standardized in terms of general concepts, language, and interaction, so the experience was consistent across contexts. There was agreement that the lack of understanding of the system might exclude certain types of individuals and that participants would need assistance from a trusted party to adopt. Comparison was made with crypto currency with it being argued that for many, this is not a technology that can be adopted independently. Comment was made that the next steps should include a systematic testing strategy in order to understand, simplify, and reduce friction and that a scaffold of the required mental model in terms of the concepts, interactions, and wider ecosystem should be mapped.
Can Any of This Be Automated?
The general consensus that emerged is that automation could solve many of the complexities and frictions identified that individuals are becoming accustomed to AI and that AI can work for the individual in a sovereign way. It was suggested that many interactions in the system are mundane and that repetitive actions could be driven by an overarching user policy. Discussion centered around two areas: firstly, the means for an individual to inspect the automated component and gain trust that it was acting in their interests, and secondly that we should not replace one kind of blackbox solution with another. There still needed to be visibility of the underlying processes and functions, so the participant can understand what was happening, in order to comprehend the value propositions and advantage.
Discussion
The following sections cover the pertinent topics emerging from this research relative to the development of an interface layer for SSI, in the context of both a sovereign boundary mechanism and wider human-centered data ecosystem.
The Sovereign Boundary Mechanism
The development of a conceptual model in-line with the principles of the decentralized domain, following the trajectory of technologies and standards, realizes a system that allows participants to manage their data, information, communications and affairs independently through a digital wallet and agent. The concept of sovereignty in this context translates to individualism, and this in turn, given the complexity of the required interaction, poses several issues. Within this research, this independent domain of interaction has been titled a sovereign boundary mechanism. This means there is a clear boundary between the sovereign domain and the wider network. Within this domain participants manage identity, relationships, credentials, personal data, and access control, this is a strict task-based interaction, one which incorporates new distinct ideas and concepts. Given the gravitas and value of the personal data being transacted, this research suggests that a strong internalized understanding of the domain will initially be required to engage users. This requirement for internalized knowledge relates to the traditional notion of internalized cognition and mental model (Craik, 1943; Norman, 1986; Payne, 2003). Creating a situation where a participant is required to engage in significant internalized cognitive processes is counterintuitive to the evolution of HCI theory and accepted design thinking, where externalized cognition and computational offloading are considered best practice (Scaife and Rogers, 1996; Hutchins, 2000; Payne, 2003).
The required degree of internalized understanding and cognition in the context of adoption and the diffusion of innovation (Rogers, 1962) is arguably a primary consideration for the decentralized community. This research has clearly highlighted the complexity of a sovereign boundary mechanism, and further research and design practice needs to be undertaken to explore how complexity, friction, and internalized cognitive processes can be significantly reduced.
The Paradox of a Sovereign Boundary Mechanism
The objective of decentralization is to emancipate the participant from the centralized Internet. In doing so, the negative consequences are mitigated, and the missed opportunities presented by a decentralized alternative can be realized. However, this research suggests that the current trajectory may inadvertently replace one set of constraints with another. The complex landscape, isolation, internalized cognitive load, responsibility of managing one’s own data, and generation of friction not found in centralized counterparts may replace one form of incarceration with another. It can be argued that these issues can be addressed and overcome, but the notion of the proverbial, out of the frying pan and into the fire, needs to be considered as future tools are conceived and developed.
The notion of a genuine decentralized Internet is predicated on the principle that the owner of the data should have control over it. The individual should have command over multiple immutable persistent identifiers, and they should have agency to decide who to share a relationship with and who on the network can observe their activities and transactions. The participant should have the capability to manage and redistribute their credentials or data to whom they see fit under their own terms and conditions (Mortier, 2014; Allen, 2016). This research has demonstrated what has been termed as a sovereign boundary mechanism, representing a participant who sits within a metaphorical boundary, defining identity, controlling relationships, and managing data streams. This is achievable through an analog model that potentially liberates the participant from the centralized Internet. Paradoxically, this model comes with a number of caveats which pose significant problems. This research has raised the issues of complexity, internalized cognition, mental model, friction, risk, responsibility, trust, and exclusion. By recognizing and considering these challenges through design thinking, coupled with an investigation of value proposition, the probability of mainstream SSI adoption can be significantly improved.
Back Peddling on Friction
A topic discussed within expert interviews and exposed through the practice-led component is that of increased interactive friction. This research suggests that the existing SSI analog model extended within this research exhibits a higher level of friction across interactions than that found within centralized counterparts. This relates to the required cognitive engagement, the understanding of original concepts, vague mental model and metaphor, and the shouldering of more personal responsibility. This research does not offer a metric on this assumption, but through developing and analyzing a sovereign boundary mechanism, the array of conceptual components for interaction and the collective required objects, and subsequent multilayered user interface, the friction level would appear to be substantial. If decentralized technologies are to find adoption, friction needs to be reduced not increased. Placing a number on this increased friction, potentially found in differing forms of decentralized interactions, is outside the scope of this research. However, this is a topic that warrants further investigation and should be prioritized within any continued endeavor.
A Missing Mental Model
When considering the underlying assumptions driving this research, the paper, Why Johnny Can’t Encrypt, is cited (Whitten and Tygar, 1999). The assumption is stated that the circumstances described within Whitten’s work may emerge when considering decentralized endeavors. Within the cited research, it is argued that different methods of user evaluation are required when considering software, where a user lacks the understanding of the underlying concepts and mechanisms. In essence, the user lacks the mental model of the domain. The paper is concerned with sending emails with encryption software and argues that even with a well-designed interface, users struggle to complete what is a relatively simple task. A sovereign boundary mechanism represents a system which is arguably considerably more challenging. This research has demonstrated a user domain that is significantly complex. There are multiple concepts, processes, and interactions, which when taken individually, potentially lack the mental model for meaningful engagement. However, when these elements are combined as a whole, this research suggests that without considerable guidance, the objective of sovereign agency and utilization of personal data through a mechanism of this kind are impractical. It is accepted that the developed user interface within the conceptual model is preliminary and that further cycles of refinement will reduce complexity and potentially improve the mapping of interactions. However, refinement of the UI will not be enough and it has to be recognized that a full sovereign boundary mechanism, in this guize, presents considerable barriers with respect to forming an operational mental model for the participant.
Internalized Cognition
Leading on from the discussion regarding the complexity and potential missing mental models, even with sufficient understanding of the system domain, the degree to which a participant may rely on internalized cognition in order to engage is of concern.
This research identifies that the required internalized understanding for both the interaction and many of the broader concepts is significant. It can be argued that the cognitive load for initial engagement poses an issue for adoption. The very concept of sovereignty, and the metaphor of a secure boundary, suggests a degree of user isolation and internalization. The value and differing types of the personal data, the weight of being solely responsible, and the complex processes through which data must traverse to engage in meaningful transactions amounts to a sizeable load of internalized understanding and knowledge. If a mental model for this domain can be established, it can be argued that engagement will still require a considerable degree of internalized cognition. Within the expert interviews, comparison was made with crypto currencies and the difficulty individuals have in understanding and engaging with an ecosystem when asset value and responsibility fall into the equation. It can be argued that a sovereign boundary mechanism is considerably more complex. Within the product design process, the degree of internalized cognition needs to be accepted and measured. From there, every effort needs to be made to reduce the internalized understanding and decision making required. As discussed in the back pedaling on friction section, the increased friction posed by decentralized systems is a primary issue, and it is the internalized processes that are arguably responsible.
A Spectrum of Human Computer Interaction Theory
This research concludes that a human-centered data ecosystem through a sovereign boundary mechanism requires the consideration of a spectrum of HCI theory and paradigms (Rogers, 2012) and that any further innovation needs to recognize this in its deliberation. The graphic in Figure 4 suggests the applicable theory across a model of a human-centered data ecosystem.
Internalized cognition and domain specific mental model (Payne, 2003) is relevant to the core of a sovereign boundary mechanism. Externalized cognition (Scaife and Rogers, 1996) is relevant between the core and the boundary. The notion of distributed cognition (Hutchins, 2000) (Payne, 2003) and situated action (Suchman, 1987) is applicable as engagement and transaction occur outside of the user boundary across the wider network. In addition, interactions and decision making within the wider ecosystem will be reliant on community-based templates and the development of trust networks, so societal and cooperative theories of HCI are also relevant (Schmidt, 2011). What is clear is that SSI falls into a number of HCI paradigms, and in identifying them, the application of Harrison’s phenomenological matrix, where theories are considered and selected were deemed appropriate, would seem to be of relevance (Harrison et al., 2007).
This research suggests that the SSI community needs to recognize the importance of HCI cognitive theory and systematically address both issues of direct usability and the interaction and internalized understanding of concepts. This research argues that Payne’s theory (Payne, 2003) of specific mental models for domains should be followed to map the required user understanding in detail. Any direct interaction should consider how the interface layer can push as much cognition as possible into the externalized realm. Finally, interaction and transactions need to be fully understood outside the sovereign boundary mechanism so that distributed cognitive relationships and situated actions can be defined. Above all, the consistency and cooperation across all stake holders are considered critical.
Types of activity recognized through this research, which may be reliant on distributed cognition and the consideration of situated action are as follows:
1. Validation/reputation/trust of individual actors
2. Collective decision making
3. Collective production activity
4. Collective data sharing
5. The construction of larger cognitive artifacts and systems
A final notable HCI theory and ethical movement is that of human values, which argues that digital technology should strive to consider human values within its development process and ultimate application (Harper et al., 2008). The theory introduces the notion of empathy into the design process, as a point of reflection to consider the human values within any technology development.
Can AI or Collective Intelligence Reduce the Cognitive Load?
This topic of discussion derives from both consultation with experts and the critical reflection of the conceptual model. More conversation centers around the intelligent agent or personalized artificial intelligence, taking control of much of the mundane decision making and ongoing administration, involved in this type of decentralized system. This might be based on broad sweep criteria defined by a participant or derived through machine learning based on the participant’s history. This concept has the potential to drastically reduce the cognitive load required, drawing the participant’s attention only to critical and important decisions. The concept of AI supporting decentralized engagement is attractive but can also be seen as a misguided panacea. There are issues of trust, understanding, and value, which need to be considered as trade-offs against automation. If an objective of decentralization is transparency, to hide critical decision making within a blackbox may be contradictory. How can the participant trust the AI? Who defines the AI? And more importantly, how much of the inner workings of the system does the user need to see and understand, in order to both have faith and see value in the engagement? This is a significant topic for further research and debate.
Another solution to cognitive load reduction and decision making may be the establishing of group or tribe, a trust network that collectively makes decisions through shared values, for instance an environmental collective that marshals relationships and transactions through ethical reputations. This is part of the trust framework conversation, related to the theories of distributed cognition (Hutchens, 2000) and the emerging of technology in context (Suchman, 1987). This again offers a rich seem for future research.
An aside to the notion of collective decision making is that of democracy, political representation, and vote casting. An interesting discussion might be found around the concept of decentralized systems acting as a voting mechanism. The logic being if knowledge is power then sharing your data and subsequent inferred collective information may offer a new and dynamic means of democratic process.
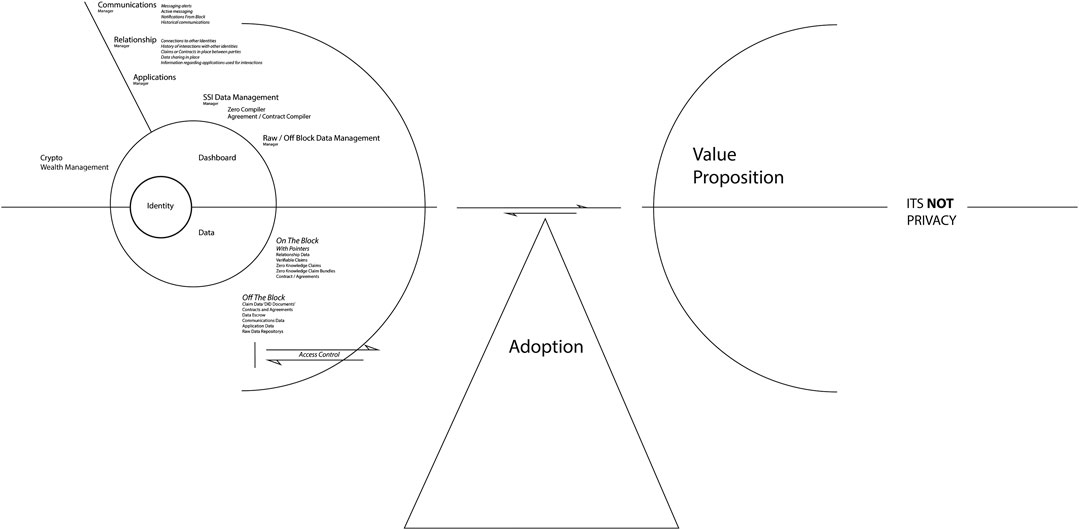
Balancing the Cognitive Load Against the Value Proposition
The practice-based component of this research has demonstrated that there is considerable cognitive load, complexity, and participant responsibility that potentially manifests within an active human-centered data ecosystem. This friction might be mitigated through careful design considerations, but it can still be argued that even then the required engagement demands more effort on behalf of the participant than that currently found within existing centralized services. To this end, in line with many of the decentralized arguments around the communication of privacy, control, missed opportunity, and value proposition, any development of an interface layer needs to be balanced against the value that interaction serves to the user. Where this balance lies and how it manifests is a central conundrum in the delivery of a sustainable decentralized Internet and stands as a source of considerable further research. Figure 5 Illustrates the balancing of Cogitative Load again the Value Proposition
A Starting Point for a Full Interface Layer Mapping
This research has argued for a standardized set of user interactions to facilitate engagement with a user-centered data ecosystem utilizing SSI at its core. The objective of this work has been to develop an initial conceptual model and preliminary user interface. Critical reflection has suggested that there are significant issues regarding internalized cognition, mental model, and metaphor. There are considerable opportunities for further practice-based research as this initial representation evolves through subsequent cycles. The preliminary conceptual model requires further testing, prototyping, and development. The mechanisms of the wider ecosystem need to be explored and metrics need to be drawn against a spectrum of models for a sliding scale of user engagement. There is a need to refine a detailed optimized mapping of this challenging user experience, as this work has taken only the first tentative steps toward that objective. This research has not resolved the challenge of establishing an accessible interface layer for self-sovereign identity, instead it acts as a contribution to knowledge and a jumping-off point for further research and development for what is a very important academic and practical domain.
Conclusion
This research concludes that the core technological infrastructure is now in existence to facilitate a genuine sovereign identity layer for the Internet, one which satisfies the principles of both human data interaction and self-sovereign identity. Investigation suggests that a dominant trajectory for a human-centered data ecosystem with the advent of a functional identity layer is progressing toward a sovereign boundary mechanism with self-sovereign identity at its core. By projecting forward the current trends through a conceptual modeling exercise, this research has demonstrated a potential interaction model that is complex and high in friction, requiring significant internalized cognitive processes and knowledge. Though the core technological infrastructure is in place, the development of a preliminary user interface suggests a number of mechanisms and interactions which still need to be developed to facilitate a full human-centered data ecosystem. This research concludes that in the development of an interface layer for SSI, a spectrum of HCI cognitive theory needs to be considered and any next steps should attempt to map the interplay between internalized, externalized, and distributed cognition. This research suggests that the SSI community needs to recognize the obstacle potentially posed at the interface layer and engage in collective standardization, strategy, and design thinking to increase the probability of the sustainable adoption of this revolutionary technology.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the author, without undue reservation
Author Contributions
The author confirms being the sole contributor of this work and has approved it for publication.
Conflict of Interest
The author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fbloc.2020.609101/full#supplementary-material.
References
Allen, C. (2016). The path to self-sovereign identity. Available at: http://www. lifewithalacrity.com/2016/04/the-path-to-self-soverereign-identity.html (Accessed January 1, 2020).
Cameron, K. (2005). The laws of identity. Available at: https://www.identityblog.com/stories/2005/05/13/TheLawsOfIdentity.pdf (Accessed January 1, 2020)
Carroll, J. M. (1991). Designing interaction: psychology at the human computer interface. Cambridge, United Kingdom: Cambridge University Press.
Craik, K. J. W. (1943). The nature of explanation. Cambridge, United Kingdom: Macmillan University Press.
Creswell, J. W. (2003). Research design: qualitative, Quantitative and mixed methods approaches. 2nd Edn. London, United Kingdom: SAGE Publications Ltd.
Dunphy, P., and Petitcolas, F. (2018). A first look at identity management schemes on the blockchain. IEEE Security and Privacy 16 (4), 20–29. doi:10.1109/MSP.2018.3111247
Finch, H., and Lewis, J. (2003). Focus groups, qualitative research practice. London, United Kingdom: SAGE Publications Ltd.
Haddadi, H. (2015). Personal data: thinking inside the box. Aar. Hu. Cen. Comp. 1, 1. doi:10.7146/aahcc.v1i1.21312
Harper, R., Rodden, T., Rogers, Y., and Sellen, A. (2008). Being human: human-computer interaction in the year 2020. Cambridge, United Kingdom: Microsoft Research.
Harrison, S., Tatar, D., and Sengers, P. (2007). “The three paradigms of HCI,” in Alt. Chi. Session at the SIGCHI conference on human factors in computing systems, San Jose, CL, January 2007 [abstract].
Hodder, M. (2019). Customer Commons. Available at: http://www. http://customercommons.org/author/mary-hodder/ (Accessed October 13, 2019).
Hornung, H., Pereira, R., and Baranauskas, M. C. C. (2015). Challenges for human-data interaction—a semiotic perspective. Hum.-Comp. Inter.: Design and Eval. 1, 37–48. doi:10.1007/978-3-319-20901-2_4
Hutchins, E. (2000). Distributed cognition: toward a new foundation for human-computer interaction research. ACM Trans. Com.-Hum. Inter. 7 (2), 174–196. doi:10.1145/353485.353487
IIW (2019). Internet identity workshop. Available at: https://internetidentityworkshop.com/ (Accessed April 7, 2019).
Johnson, J., and Henderson, A. (2002). Conceptual models: begin by designing what to design. Interactions 9 (1), 25–32. doi:10.1145/503355.503366
Johnson-Laird, P. N. (2001). Mental models and deduction. Trends Cognit. Sci. 5 (10), 434–442. doi:10.1016/s1364-6613(00)01751-4
Kirsh, D. (1997). Interactivity and multimedia interfaces. Instr. Sci. 25, 79–96. doi:10.1023/A:1002915430871
Landuer, T. K. (1991). “Let’s get real designing interaction,” in Psychology at the human computer interface (Cambridge, United Kingdom: Cambridge University Press).
Larkin, J., and Simon, H. (1987). Why a diagram is (sometimes) worth ten thousand words. Cognit. Sci. 11, 65–99. doi:10.1016/S0364-0213(87)80026-5
Moglen, E. (2013). The tangled web we have woven. Commun. ACM 56 (2), 20–22. doi:10.1145/2408776.2408784
Mortier, R. (2014). Human-data interaction: the human face of the data-driven society. Available at SSRN: https://ssrn.com/abstract=2508051 (Accessed September 10, 2018).
Norman, D. (1986). “Cognitive engineering,” in User centred system, Editors S. Draper, and D. Norman (Hillsdale, NJ: Lawrence Erlbaum Association).
O’Malley, C., and Draper, S. (1992). “Are mental models really in the mind? representation and interaction,” in Models in the mind: perspectives, theory and application, Editors Y. Rogers, A. Rutherford, and P. Bibby (London, United Kingdom: Academic Press), 73–91.
Payne, S. (2003). “Users mental models: the very ideas,” in HCI models, theories, and frameworks: toward a multidisciplinary science (Burlington, MA: Morgan Kaufmann).
Rogers, Y. (2012). HCI theory, classical, modern, and contemporary. San Rafael, CA: Morgan & Claypool Publishers.
Scaife, M., and Rogers, Y. (1996). External cognition: how do graphical representations work? Int. J. Hum. Comput. Stud. 45 (2), 185–221. doi:10.1006/ijhc.1996.0048
Schmidt, K. (2011). Cooperative Work and coordinative practices: Contributions to the conceptual Foundations of computer-supported cooperative work (CSCW). Heidelberg, Germany: Springer. doi:10.1007/978-1-84800-068-1
Tobin, A., and Reed, D. (2016). The inevitable rise of self-sovereign identity Sovrin Foundation. Available at: https://sovrin.org/wp-content/uploads/2018/03/The-Inevitable-Rise-of-Self-Sovereign-Identity.pdf (Accessed April 20, 2020).
Turnhout, K. (2014). Design patterns for mixed-method research in HCI. Nijmegen, Netherlands: HAN University of Applied Science.
Van Kleek, M., and O’Hara, K. (2014). “The Future of Social is personal: the Potential of the personal data store,” in Social collective intelligence: combining the powers of humans and machines to build a smarter society. Heidelberg, Germany: SpringerAvailable at: http://eprints.soton.ac.uk/363518/1/pds.pdf (Accessed September 28, 2017), 125–158.
Whitten, A., and Tygar, J. (1999). Why Johnny can’t encrypt: a usability evaluation of pgp 5.0,” in Proceedings of the 8th USENIX Security Symposium, Washington, DC, December 8, 1999.
Keywords: self-sovereign identity, human data interaction, human-centered data ecosystem, sovereign boundary mechanism, decentralized internet, interface layer, usability
Citation: Lockwood M (2021) An Accessible Interface Layer for Self-Sovereign Identity. Front. Blockchain 3:609101. doi: 10.3389/fbloc.2020.609101
Received: 22 September 2020; Accepted: 24 December 2020;
Published: 02 March 2021.
Edited by:
Kaliya Young, Merritt College, United StatesCopyright © 2021 Lockwood. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Mick Lockwood, bS5nLmxvY2t3b29kQHNhbGZvcmQuYWMudWs=
 Mick Lockwood
Mick Lockwood