- Department of Water Resources and Environmental Engineering, School of Civil Engineering, National Technical University of Athens, Athens, Greece
1 Introduction
The technological foundation of each civilization determines its living conditions and prosperity (Sargentis, 2022; Sargentis et al., 2021a; Koutsoyiannis and Sargentis, 2021). Access to discussed resources should not be viewed as solely an individual concern, since abundance is significantly shaped by economies of scale and collective practices. At the same time, they are fundamentally linked to the political practices that must be followed. Wittfogel noted that hydraulic works requiring collective effort have underpinned social structures depending on elite oversight mainly due to their complexity (Wittfogel, 1981) which refers to the behaviour of a system or model characterized by a large number of interconnected components, nonlinear interactions, and emergent properties that cannot be fully understood by analysing individual parts in isolation (Lorenz, 1963).
However, there is always a turning point in economies of scale where, past a certain threshold, the rising managerial costs increases the unit cost (Coase, 1937; Koutsoyiannis, 1979). Projecting this principle onto social dynamics, we note that, there is an optimal point at which society gains the most from cooperative behaviour (Dunbar, 1992), yet it becomes inefficient when social structures expand to such an extent that the cost of their coordination outweighs the provided benefits (Williamson, 1973; North, 1990).
The challenges of balancing cooperative benefits with coordination costs in achieving economies of scale by state regulations have been addressed through socio-political theories emphasizing the state’s role. Adam Smith recognized that cooperative market interactions, facilitated by minimal state intervention, could create economies of scale through specialization and trade, with the state ensuring basic legal frameworks (Smith et al., 1776; Phillipson, 2010). Karl Marx argued that cooperative labor under capitalism, while initially fostering economies of scale, required state-led collectivization to equitably distribute benefits and overcome exploitative capital accumulation (Marx, 1867; Marx, 1875). John Maynard Keynes emphasized state-driven cooperation, advocating for public investment and demand management to stabilize markets and sustain economies of scale during economic downturns (Keynes, 1936). Neoliberalism, led by figures like Friedrich Hayek and Milton Friedman, critiqued state overreach, promoting cooperative market mechanisms with minimal state involvement to maximize economies of scale through competition and innovation (Hayek, 1960; Friedman, 1960).
These perspectives shaped societal systems, with capitalism and communism as the most prominent rivals (Hobsbawm, 1994). It is interesting to note that both the Soviet Union (communism) and the United States (capitalism) landed humans on the moon in late 1960s, demonstrating that each system, could equally effectively achieve the monumental milestone of that era (Siddiqi, 2010; Logsdon and John, 2010).
The same principle applies to technological applications—there is a limit beyond which the evolution of complexity ceases to be beneficial. For instance, the embedded complexity in various consumer goods, such as cars, creates vulnerabilities that render these vehicles prematurely obsolete (Cummings, 1984; Arthur, 2010). While in earlier times this was often regarded as a disadvantage, today it appears that the temporariness of an object, which creates the need for its replacement within a short period, promotes the desired outcome: the consumption of new products to replace it (Schumpeter, 2013). This could imply that the durability of things is almost undesirable (Slade, 2007).
Within the framework of globalization, this may not have been a flaw, as global trade was encouraged to enable easy replacement and consumption, affecting every aspect of modern life (Sargentis and Koutsoyiannis, 2023; Stiglitz, 2017). However, it presupposes a complex, interconnected economic system that is fragile in the face of various regulatory attempts (Lester, 2011). For example, maritime transport (Figure 1) underpins the global economy, facilitating approximately 80% of international trade by volume (left pie chart in the bottom of Figure 1) and around 70% by value (right pie chart in the bottom of Figure 1), underscoring its critical role in the global movement of goods (Figure 1) (United Nations Trade and Development, 2024).
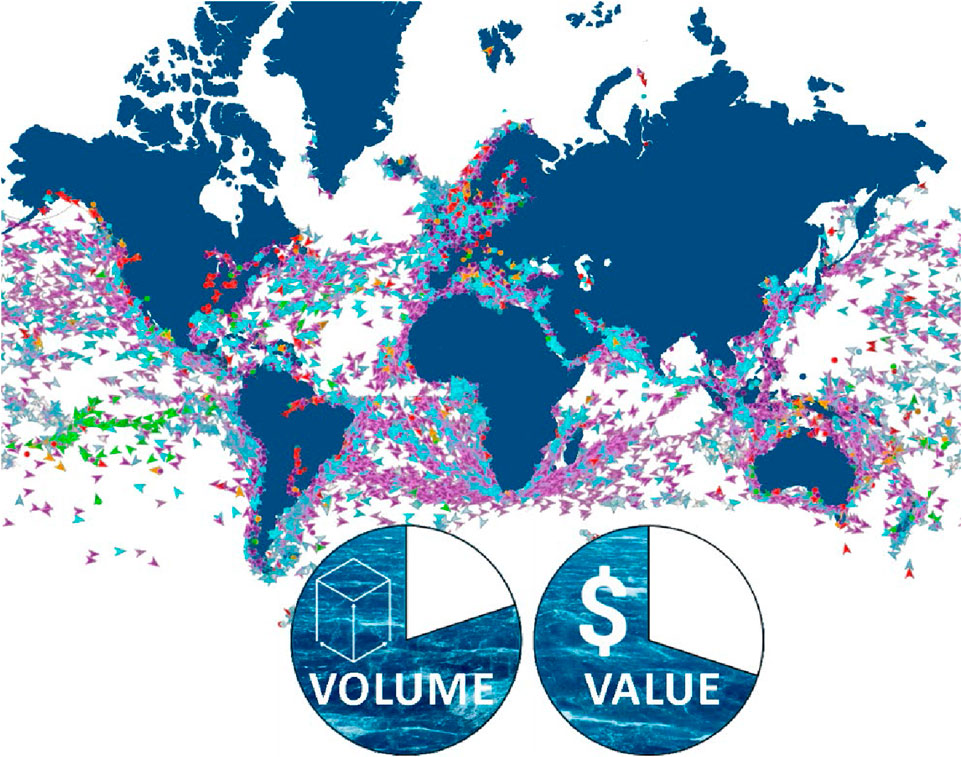
Figure 1. Global maritime traffic as a reflection of trade complexity — positions of cargo ships worldwide which carries ∼80% of international trade by volume (left pie chart) and ∼70% by value (right pie chart) on 10 April 2025. Data were adopted graphically via MarineTraffic (2025).
Systemic vulnerabilities are weaknesses within a system that arise from its structure, interconnections, or dependencies, making it susceptible to cascading failures or disruptions when stressed (Beck, 1992). These vulnerabilities are often hidden and emerge under specific conditions as in electronic-based solutions. Electronics-based solutions (Taleb, 2012) present systemic vulnerabilities beyond the regulatory risks evident in the 2022 Russian sanctions (Sargentis et al., 2022a) or the recent U.S. trade conflicts (April 2025) (The Washington Post, 2025). Unlike simpler mechanical systems, these technologies are inherently susceptible to disruptions in sensitive supply chains, cyberattacks, and electromagnetic pulses—creating layers of systemic vulnerability often overlooked in technological adoption decisions (Cummings, 1984; Kopp and Brauch, 2003).
Systemic vulnerabilities in complex system appears highly unstable—especially when considering isolated technical incidents, such as two small fires at Heathrow Airport which disrupted global air travel. In addition, the rapidly interconnected world, which must manage emerging complexity with tools that have not yet reached full maturity, becomes vulnerable to malicious actions such as the Mt. Gox Hack (2014).
Resilience is the capacity of a system to absorb disturbances, adapt to changes, and maintain its core functions and structure in the face of stress or shocks (Allen et al., 2014). As it is a desired goal, a question arises as to whether and how societies can thrive without the emerging complexity that has been imposed through technological solutions as well as the communication and cooperative policies that sustain global trade.
Ensuring social thriving is critical, an optimization is required—one that is simple, resilient, self-sufficient, and capable of supporting at least the foundation of societal prosperity—through available adaptations (Sargentis et al., 2024a), (Sargentis and Kougkia, 2024).
Section 2 analyzes the methodology used to approach the vulnerabilities inherent in complex systems, focusing on their susceptibility to disruptions. Section 3 delves into examples of governmental failures and technical failures, using the evolution of technology of vehicles and digital infrastructure as case studies to illustrate fragility in advanced technologies. Section 4 emerges the role of critical aspects of modern civilization: digital infrastructures and satellites. Section 5 explores future technological paradigms, weighing the promises and perils of automation, digital currencies, and interconnected systems arguing that progress is neither linear nor guaranteed. The discussion in Section 6 synthesizes these insights, proposing strategies for resilience at governance and technological levels. Finally, Section 7 concludes with recommendations for proactive design and planning to ensure robust systems, emphasizing the urgency of action during periods of stability.
2 Methodology
This study adopts a multidisciplinary approach to analyze the interplay between technological complexity, systemic vulnerabilities, and resilience in modern civilizations, with a focus on resource management perspectives. The methodology comprises three key components.
2.1 Historical and comparative analysis
Historical case studies, such as the collapse of the Roman Empire, Soviet Union and the Qing Dynasty (China) are examined to identify patterns of overextended infrastructure and administrative complexity leading to systemic failure. These are compared with contemporary examples (e.g., megacity resource management, global trade disruptions) to draw parallels and highlight recurring vulnerabilities.
2.2 Data-Driven visualization
Quantitative data from global datasets (e.g., World Bank, Marine Traffic—cargo ship positions, Flightradar—air traffic, TeleGeography—submarine cable) are analyzed to illustrate the scale and fragility of interconnected systems. Visualizations are generated to map trade complexity, economic impacts, and cascading failures.
2.3 Qualitative risk assessment
Technical and governance failures are evaluated through qualitative frameworks, focusing on vulnerabilities in digital systems (e.g., ECUs in vehicles, cyber-hacks, CBDCs and resource distribution). Scenarios such as EMP attacks and trade wars are explored to assess cascading risks.
Insights are drawn from real-world incidents, e.g., Mt. Gox hack (February 2014) Heathrow fires (March 2025) and the blackout in Iberian Peninsula (April 2025) to propose adaptability strategies and the above examples were used for the revision of the pyramid of human needs.
This mixed-methods approach emphasizes governance and technological perspectives to propose resilience frameworks. Limitations include the speculative nature of future risk scenarios, which however are addressed through transparent sourcing and conservative assumptions.
The methodological steps of the paper, the examined issues and the conclusions are visualized in Figure 2.
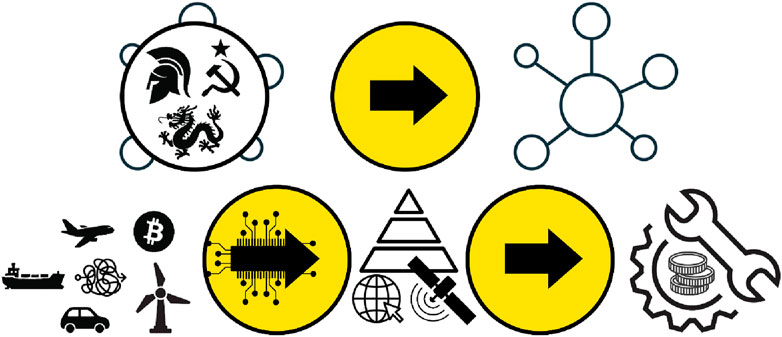
Figure 2. The methodological steps of the paper. On the left side of the image, examples of governmental and technological collapse are presented; in the lower central part of the image, the dependence and revision of the hierarchy of needs based on digital and satellite infrastructure are shown, and on the right side of the image, resilience methods are presented, such as decentralization into smaller clusters, the existence of robust technology, and cash.
3 Vulnerabilities of complexity
The Industrial Revolution and the Electronic Era established sophisticated infrastructures driven by economies of scale, rapid communication, global connectivity, and widespread access to knowledge. Evidently, global poverty rates dropped dramatically over the past century, a triumph humanity owes to these technological breakthroughs (Sargentis et al., 2022b).
Economies of scale and large-scale infrastructure have enabled the clustering of the population in major urban centers (Sargentis et al., 2020a). Megacity aqueducts (Sargentis et al., 2019), supply chains (Sargentis and Koutsoyiannis, 2023), industrial production, refineries, and critical infrastructure facilitate human coexistence (Human Progress, 2025). However, these systems demand complex management, forming a fragile equilibrium that sustains societies. A deliberate or accidental failure in any major infrastructure, especially to the communication system which solves this puzzle, could immediately trigger an existential crisis.
The vulnerability of the contemporary communication system, underpinned by the internet, is exemplified by approximately 1.4 million kilometers of submarine fiber-optic cables linking over 1,200 landing points worldwide (Finn and Yang, 2009). Figure 3 visualizes the comparison of this global infrastructure with the scale and capacity of the mid-19th-century telegraph network, which relied on copper cables to transmit rudimentary Morse code messages (Standage, 1998; Du Boff, 1983; Huurdeman, 2003; Love, 2018). The comparison, spanning roughly 150 years of technological advancement from 1872 to the present, underscores the profound transformation in global connectivity (Carter et al., 2015). While such infrastructures are indispensable for supporting globalization, facilitating the management of complex economic systems, and enabling the distribution of critical resources, their immense scale simultaneously introduces significant vulnerabilities, including susceptibility to cyberattacks and exposure to geopolitical tensions (Headrick, 1991; Brodsky, 2023).
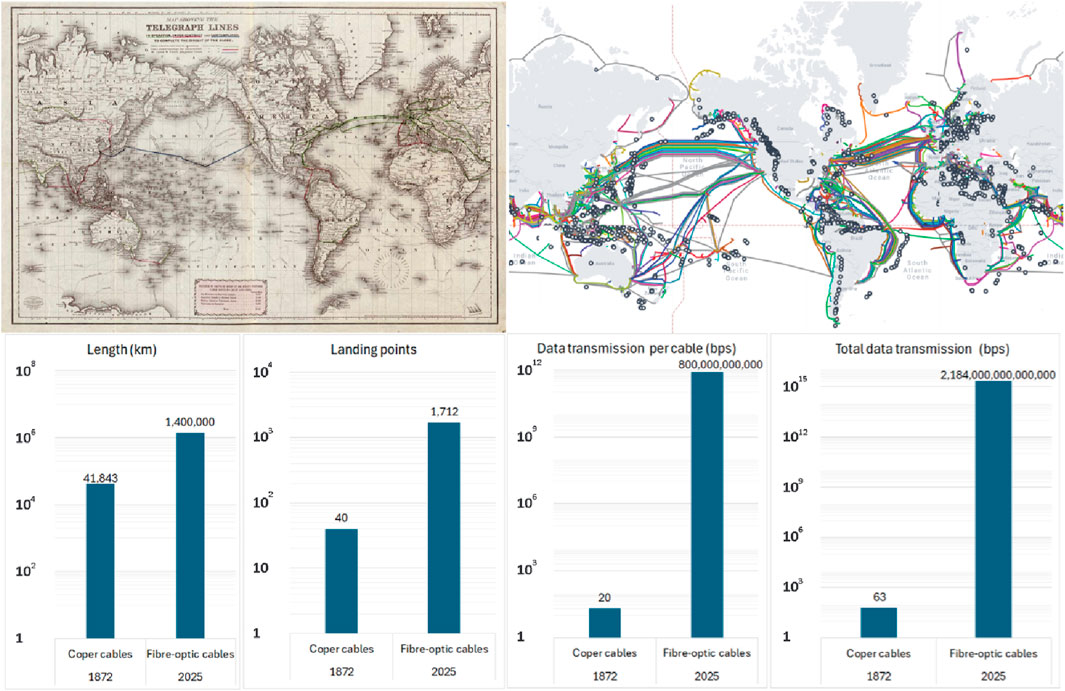
Figure 3. Top left: Telegraph cables (1872) (Lloyd and Co and Norman, 1872); Top right: Fibre-optic submarine cables (2025) (TeleGeography, 2025, licensed under CC BY-SA 4.0); Bottom: Comparison between 1872-2025, length, landing points, data transmission per cable, total data transmission. Τhis comparison does not include data (satellite or terrestrial) transmitted wirelessly in present.
In present, high-frequency trading and interconnected financial networks introduced vulnerabilities that triggered the 2008 global economic crisis, an unexpected outcome hidden by the inherent complexity of the system (Haldane, 2009). Concurrently, advancements in artificial intelligence and cybersecurity heighten concerns about cyber warfare (O’Neil, 2016), underscoring the need for proactive safeguards to prevent societal-threatening consequences.
Today, the discourse on climate change (IPCC, 2021-2023; UNEP, 2024), a narrative that remains under discussion and not fully understood due to its complexity and conflicting viewpoints (Koutsoyiannis, 2025; Iliopoulou and Koutsoyiannis, 2025; Koutsoyiannis and Iliopoulou, 2024; Koutsoyiannis et al., 2023; Vicente-Serrano et al., 2025), has led to policies aimed at reshaping the energy mix through the adoption of renewable energy sources. Even if the narrative of climate change and the associated technologies supporting it are subject to debate (Clintel, 2025), the associated technologies introduce new challenges in their management due to their stochastic nature.
The above vulnerabilities suggest that there is always the possibility that society could become trapped in a death spiral (Schippers et al., 2024) of complexity, from which it would be very difficult to break free.
3.1 Governmental failures
Historically, excessive bureaucratic complexity and endemic corruption have precipitated the collapse of entire societies, as seen in Roman Empire, the Soviet Union and the late Qing Dynasty.
3.1.1 Roman Empire
Tainter argues that the collapse of the Roman Empire illustrates how overextended infrastructure and reliance on complex administrative systems precipitate societal decline (Tainter, 1988). He contends that the empire’s dependence on intricate networks—such as extensive road systems, aqueducts, and a sprawling bureaucracy—demanded substantial resources to sustain. As economic returns diminished, these systems rendered the empire vulnerable to external pressures (e.g., barbarian invasions) and internal weaknesses (e.g., corruption) (Diamond, 2005; Gibbon, 2000). The rigid centralized administrative structure further constrained adaptability, as simplifying governance through decentralization was politically and culturally untenable, accelerating systemic failure.
3.1.2 Soviet Union
The Soviet Union (1922–1991) developed a highly centralized, bureaucratic system to manage its vast economy and diverse population, but this complexity fostered inefficiencies and corruption. Lengthy administrative processes, coupled with opaque resource allocation, enabled the elites to siphon resources, eroding public trust and economic stability (Fitzpatrick, 1999). By the 1980s, the system’s rigidity stifled innovation and failed to address growing economic stagnation, culminating in the USSR’s dissolution in 1991 (Suny, 2010).
3.1.3 Qing Dynasty
The Qing Dynasty (1644–1912) in China succumbed to bureaucratic bloat and corruption, were intricate governance structures and rampant bribery undermined resource distribution and public welfare, particularly in urban centers. This weakened the dynasty’s ability to respond to internal rebellions and external pressures, leading to its collapse in 1912 (Rowe, 2009).
3.1.4 Systemic vulnerabilities in present megacities
The complexity of managing resources such as Water-Energy and Food nexus (Sargentis and Markantonis, 2024) in present megacities is a critical factor underpinning their sustainability and functionality, rendering them highly vulnerable to disruptions like tariffs and trade wars.
Megacities, characterized by dense populations and intricate infrastructural networks, rely on efficient resource distribution systems that are often strained by global economic policies. For instance, tariffs can increase the cost of imported food in mega-cities which could be considered as food deserts (United Nations, 2018; Sargentis and Ioannidis, 2024; Chatzimpiros et al., 2007). Trade wars further complicate this by disrupting supply chains, as seen in the U.S.-China trade tensions affecting water-intensive agricultural exports (Freund et al., 2020).
The interconnectedness of resource systems amplifies these risks, with energy shortages potentially cascading into water and food crises (Homer-Dixon et al., 2015). Moreover, the governance of these resources in megacities often involves multiple stakeholders, adding layers of complexity that tariffs can destabilize by altering economic incentives (Garfinkel, 2017). Consequently, such economic policies pose perilous threats to megacities’ stability, where resource mismanagement could lead to existential challenges (McDonald et al., 2016).
Our interconnected world relies on the complexity of created synergies (Roser, 2020), as highlighted by the lessons learned from the COVID-19 pandemic. During this period, global trade was agitated, and global growth was halted as it is evident by Gross National Income (GNI) growth and Gross Domestic Product (GDP) growth. Therefore, these synergies promote advancement, but they also made systems vulnerable to unexpected disruptions (Gómez and Verdú, 2017) (Figure 4).
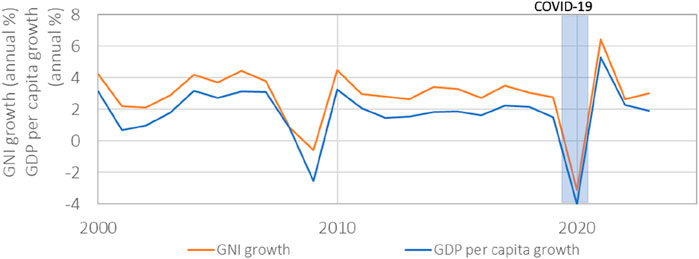
Figure 4. Global GNI growth (annual %) (data from The World Bank, 2025b), and GDP per capita growth (annual %) (data from The World Bank, 2025a).
While complexity in governance is often necessary for managing intricate systems, it can also harbor corruption, as the concealment of resources or procedures from public scrutiny may obscure unethical practices. When governmental systems are perceived as overly complex and subjective, they often fail to deliver timely resolutions, leading to a loss of public trust. This occurs as lengthy procedures for processing standard requests, such as issuing permits or accessing public services, may create opportunities for bribery payments, particularly in countries with high corruption levels (Transparency International, 2024; Reporters without Borders, 2025; Council of Europe, 2025).
3.2 Technical failures
3.2.1 From mechanical resilience to electronic fragility
Modern vehicles have evolved significantly, incorporating advanced features through Electronic Control Units (ECUs) that enhance safety, efficiency, and comfort compared to older, mechanically simpler models. However, this shift introduces a critical vulnerability: failure in an auxiliary electronic system can render these cars inoperable, a stark contrast to the resilience of older vehicles (Charette, 2020). Unlike fashion trends that impose aesthetic changes, automotive technological trends now favor design techniques that address engineering challenges via Electronic Control Units (ECUs), increasing both complexity and fragility. For example, a car in 1970s, lacking electronic systems, reliably performed its core function—transportation—while modern cars, such as those from 2020s, rely heavily on intricate electronics and sophisticated design, making them more effective, comfortable and safer but less durable (Lee and Shin, 2019). Figure 5 shows the clutch pedals of a Jeep Willys (1973) with those of Wrangler (2024). The comparison, spanning roughly 50 years of technological advancement and reveals that the former can be repaired using simple tools if it breaks down, while the latter requires replacement with the specific spare part—something that presupposes the proper functioning of supply chains.
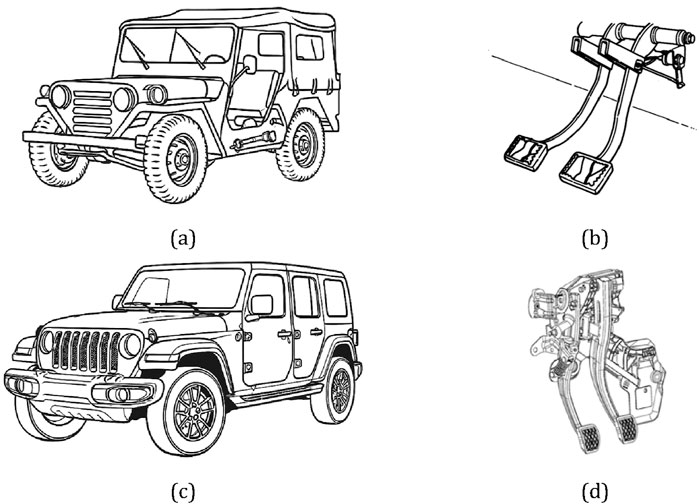
Figure 5. Top: (a) Jeep Willys M151 A2 (1973) (Bringatrailer, 2025); (b) Clutch pedal for Jeep Willys M151 A2 (1973) (Headquarters Department of the Army Washington DC, 1983). Bottom: (c) Jeep Wrangler (2024) (Jeep Wrangler, 2025); (d) Clutch pedal for Jeep Wrangler (2020) (Jeep Wrangler, 2020).
The reliance on electronics escalates maintenance demands and exposes modern cars to supply chain risks, as seen during the COVID-19 pandemic when microchip shortages halted automotive production globally, resulting in an explosive increase in their price (Wright and Haltiwanger, 2022). While these design transformations solve specific issues, they do not proportionally improve operational reliability compared to the robustness of older models, requiring specialized repair facilities that older cars did not (Ward and Smith, 2018). The pandemic underscored this vulnerability, with production delays not limited to electronic goods but extending to vehicles due to their dependence on microchips, highlighting how resource availability can cripple these creative systems (Applied Energy Systems, 2025). Thus, the trade-off between advanced functionality and resilience questions the overall efficacy of these technological advancements.
3.2.2 Efficiency gains and cascading failures in modern infrastructure
While complexity can be managed to optimize infrastructure and technology, a single minor failure can set off a cascade resulting in the collapse of the entire system it supports (Middleton, 2017). For example, the two small fires in critical areas of Heathrow Airport on Thursday, March 20, 2025, (Plucinska et al., 2025) caused a conflict that impacted global air travel (Figure 6), underscoring how complexity drives efficiency but amplifies the risk of cascading failures when key components falter.
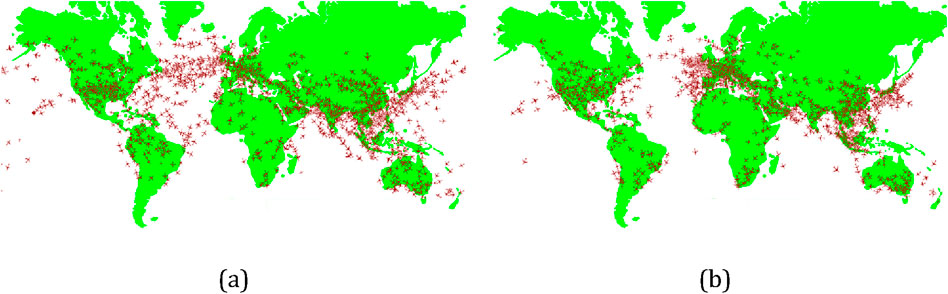
Figure 6. The air traffic on March 21, 2025 (Schneider and Gibson, 2025) compared to the previous normal Friday the same time in; (a) March 14, 2025; (b) March 21, 2025. Data were adopted graphically via Flightradar (2025).
3.2.3 Digital reflections: the vulnerability of online social and financial systems
The digital world is becoming a reflection of our personalities, with social media and online platforms shaping how we connect and interact. As we rely more on these systems, they grow more complex, mirroring the intricate social structures of real life. Social Networking Services (SNS), such as Facebook, Linkedin and X, have become integral to modern communication, but their complexity—driven by vast user networks and algorithmic content curation—creates significant vulnerabilities. Data breaches, such as the 2018 Cambridge Analytica scandal, exposed personal data more than 50 million users, influencing political processes and eroding trust (Cadwalladr and Graham-Harrison, 2018). This complexity, however, can lead to significant vulnerabilities, such as hacking cryptocurrencies or social networks, which threaten our digital existence or our digital finance.
Cybersecurity technologies are vital for safeguarding today’s interconnected systems, but their increasing complexity can create critical vulnerabilities if not properly implemented. The 2020 SolarWinds cyberattack, which compromised numerous government and corporate networks through a supply chain vulnerability, revealed how even sophisticated systems can be exploited (America’s Cyber Defence Agency, 2025). Similarly, the success of Central Bank Digital Currencies (CBDCs) depends on robust cybersecurity frameworks to prevent breaches that could destabilize entire economies (Di Iorio et al., 2024). As digital infrastructures become more integrated into essential services—such as financial networks and power grids—the risk of systemic disruption grows. A systematic review of cyber risk found that cybercrime cost nearly USD 1 trillion in 2020, emphasizing the magnitude of the economic threat and its implications for global financial stability (Aamir et al., 2021).
Emerging technologies like blockchain, which underpins cryptocurrencies such as Bitcoin, further increase systemic complexity due to their decentralized architecture and reliance on cryptographic protocols. While blockchain is engineered for data integrity, it remains susceptible to sophisticated exploits. The World Economic Forum’s 2022 report on digital dependencies underscores how such complexity can magnify cybersecurity risks, particularly when digital systems are deeply embedded in critical infrastructure (World Economic Forum, 2022). This deepening reliance on digital ecosystems means that any failure or breach can have far-reaching consequences for society and the economy (Dupont et al., 2023; Admass et al., 2024; Safi et al., 2023).
A breach in one part of a cryptocurrency exchange can affect many users, as seen in the 2014 Mt. Gox hack, where 850,000 Bitcoins were stolen (Guinness World Records, 2025) impacting thousands of investors. (BTC to US$, 2025). In that period the cost of Mt. Gox hack was about 550 million US$ but with the present Bitcoin price, Mt. Gox hack would cost about 80 billion US$ (Figure 7). Additionally, 51% attacks, where a single entity gains control of the majority of a network’s computing power, can compromise smaller blockchains, as seen in the 2018 Bitcoin Gold attack (Ramos et al., 2021). This illustrates that as our dependence on intangible, interconnected digital systems grows, so too does our vulnerability to large-scale cyber threats.
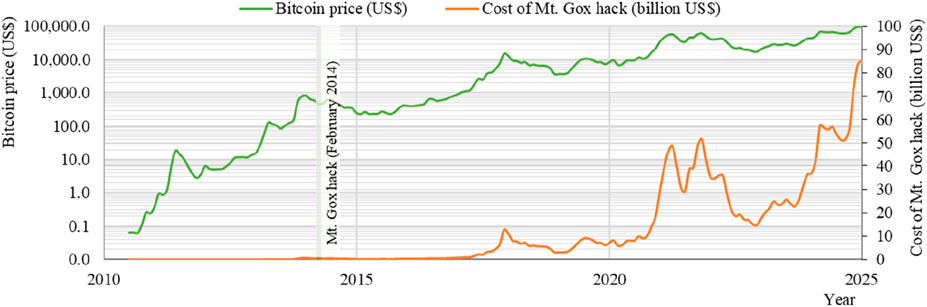
Figure 7. The evolution of Bitcoin’s price in left yy’ axis and the impact of Mt Gox hack in billion US$ in right yy’ axis.
With increasing dependence on digital systems for communication, finance, and identity, these vulnerabilities evolve into existential threats. To further illustrate this point we highlight a hack incident like the 2012 LinkedIn data breach, which affected 6.5 million passwords, exposing personal data, and leading to identity theft (Chin, 2025).
3.2.4 Vulnerabilities in energy transition
The required complexity, which should remain manageable in the energy transition, became strikingly evident during the blackout in the Iberian Peninsula on April 28, 2025 (CIMSS Satellite Blog, 2025). The incident underscored the intricate nature of modern grid management, as the system’s complexity was so profound that even the grid operator, Red Eléctrica de España, could not identify the cause of the outage (Reuters, 2025b). Remarkably, even days after the event, the precise reasons remained unclear (The Guardian, 2020; Reuters, 2025c), with initial hypotheses ranging from a “rare atmospheric phenomenon” causing oscillations in high-voltage lines to potential non-compliance with curtailment orders by renewable energy producers, exacerbating grid instability (Reuters, 2025a; The Guardian, 2025). As the second hypothesis seams more rational, initial estimates indicate that EU power grid needs trillion-dollar upgrade to avert Spain-style blackouts (Chestney, 2025).
This opacity highlights a critical challenge in the energy transition: the integration of high renewable energy penetration (Johnston and Hancock, 2025; The Guardian, 2025; Reed and Gross, 2025), particularly from variable sources like solar and wind, introduces low-inertia states that can amplify grid vulnerabilities, as seen in the rapid frequency destabilization and subsequent voltage collapse during the blackout.
This event does not solely highlight the need for better digital monitoring, as claimed, because it is akin to fixing one mistake with a larger one. It signifies the need for a redefinition of the technological approach and its reassessment, to prevent cascading failures, ensuring that complexity does not compromise reliability.
These examples highlight systemic issues stemming from complexity in various forms, revealing the fragility of systems exposed to systemic risks. Humanity’s dependence on automation, the simulation of personality or creativity in virtual realities and the dependence in immature technologies as renewable energy (Sargentis et al., 2025a), could result in cascading failures and the loss of control (Carr, 2014).
4 The achilles’ heel of civilization
A depiction of civilization’s collapse following a limited Electromagnetic Pulse (EMP) attack is provided by Paul Craig Roberts (Roberts, 2025), who outlines how three high-altitude nuclear detonations over the United States could devastate power grids and critical national infrastructure. According to the analysis, pulses would instantly damage electronic devices, crippling hospitals, water supply systems, telecommunications, and transportation networks. This reliance on interconnected electrical systems amplifies vulnerability, as even a minor disruption could trigger cascading failures across urban centers.
Uncertainties further arise with the potential implementation of Central Bank Digital Currencies (CBDCs), which, while offering digital efficiency, could become inoperable in such scenarios due to their dependence on electronic infrastructure, thus exacerbating economic paralysis (Dionysopoulos et al., 2024).
Conversely, decentralized systems like blockchain could provide resilience, ensuring transparency and security in critical operations, i.e., supply chains or emergency response coordination (Tapscott and Tapscott, 2016). Blockchain’s distributed nature might safeguard data integrity even if parts of the network fail, offering a counterbalance to centralized vulnerabilities (Nakamoto, 2008). While these technologies hold potential, their effectiveness hinges on preemptive deployment and robust infrastructure, highlighting the dual-edged nature of innovation in facing existential threats like an EMP-induced collapse.
Assessing each economy’s self-sufficiency in critical resources is essential to secure basic needs, as outlined in Maslow’s hierarchy which traditionally outlines the hierarchy of human needs (Maslow, 1943) (Figures 8, 9a).
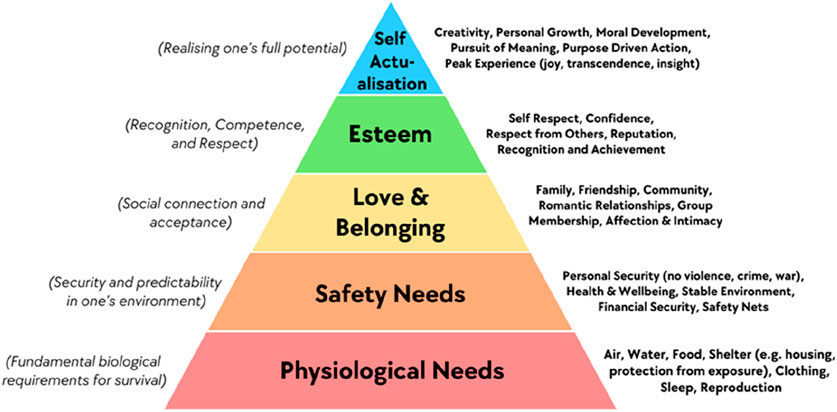
Figure 8. The Maslow’s hierarchy of needs pyramid (The Free Encyclopedia (2025), licensed under CC BY-SA 4.0.).
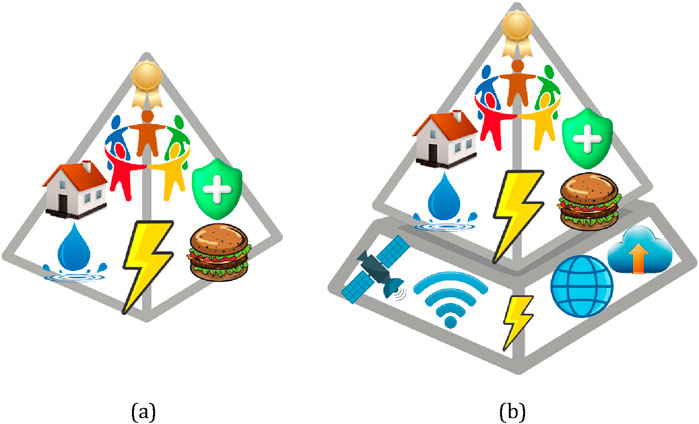
Figure 9. An abstract visualization of the Maslow’s Hierarchy of Needs Pyramid (Maslow, 1943): (a) Original view: At the base are physiological needs (water, energy and food nexus), followed by safety, then the need for belonging, and at the top, esteem and self-actualization; (b) Modern Update of the Pyramid: The new base of the pyramid includes functional energy for the internet and satellite infrastructures which form the new foundation of the pyramid as there are necessary to manage the complexity to provide all the above (water, food, security, belonging, economy), reflecting the dependencies of the civilization in digital infrastructures.
In the current context, Maslow’s hierarchy (Maslow, 1943), appears to require a reassessment to reflect modern societies’ critical dependence on digital technology (Madhusudan Rao and David, 2022) and below the base of the pyramid, which covers survival needs such as water, energy and food, we could add a new, foundational level: digital connectivity. This level encompasses internet and satellite infrastructures (with their functional energy) which have become prerequisites for accessing information, communication, and the management of complexity as supply chains, energy grid, water infrastructures, economy and other essential services (Figure 9b).
Söderbaum assumes that modern societies, overly reliant on electronics, could collapse to pre-industrial levels in a crisis like an electromagnetic pulse, lacking fallback technologies or infrastructure (Söderbaum, 2016). Sargentis and Kougia [38] note that, in present, everything depends on digital infrastructures, the technologies of the 1970s no longer exist (Sargentis et al., 2025b), and even working animals are absent in developed societies (Sargentis et al., 2024b). Therefore, modern societies cannot sustain even their basic functions, as digital infrastructure is integrated into every aspect of daily life. In a crisis scenario, the collapse of this digital layer could paralyze societies, making even the fulfillment of basic needs extremely challenging, thus amplifying the regression to primitive, hunter-gatherer era.
5 Future technological paradigms
The pursuit of automation, the registration of electronic identities and biometric data, and the control of money through digital currencies have sparked significant debate, as they promise efficiency but also raise concerns about privacy and stability (Koutsoyiannis et al., 2024). These initiatives rely on a hyper-connected world with immense computational power and robust digital security to prevent data theft or leaks, yet such security is far from guaranteed (Schneier, 2015).
When governance depends on digital records, stability is not assured, as vulnerabilities in interconnected systems can lead to catastrophic failures, such as data breaches or system collapses [110] (e.g., the reliance on digital currencies like CBDCs could expose economies to cyber risks, where a single breach might disrupt entire financial systems, highlighting the fragility of these technological advancements).
It is historically documented that progress is not linear, and the complexity of modern systems may precipitate regression, as seen in the Minoan civilization around 1500 BCE, which boasted advanced sanitation systems, a technology that was lost for nearly 2,500 years after Minoan’s collapse (Angelakis, 2017; Angelakis et al., 2003).
This historical precedent suggests that the future envisioned for 2050, filled with technological marvels, is not guaranteed; a connected world could just as easily unravel due to over-reliance on fragile digital infrastructure (Homer-Dixon, 2006). The risk of regression looms large if cybersecurity and systemic resilience are not prioritized, potentially leading to a scenario where the remarkable comforts of the modern era could be lost to the annals of history.
6 Discussion: adaptability & resilience
6.1 At the governance level
Even if each one of the collapses which were presented in section 3 (Roman, Soviet Union, Qing Dynasty) had unique factors, the recurring pattern of the central authority’s efforts to consolidate power through increasingly inefficient bureaucratic complexity, rising corruption, and external pressures, ultimately strained their systems. This tension often sparked unrest and systemic collapse, as these structures failed to ensure sustained prosperity, prompting demands for the formation of a new social structure.
Corruption embedded in complex governance systems represents a critical challenge (Xi, 2015). When left unchecked, this corruption can trigger revolutionary forces that threaten social stability. The situation becomes particularly unstable when revolutionary movements lack coherent political direction or alternative governance models that could effectively address these systemic problems.
Several great empires, including the Roman, Byzantine and Ottoman demonstrated remarkable resilience by governing decentralized systems of semi-autonomous community clusters. The Romans (∼500 years) divided their vast territory into provinces with local governors managing taxation and justice, while allowing cities significant self-governance (Garnsey and Saller, 1987). The Byzantines (∼1,125 years) implemented the theme system, granting military and administrative autonomy to regional units under strategic leaders (Treadgold, 1997; Haldon, 1997). Likewise, the Ottoman Empire (∼623 years) organized small religious and ethnic communities, granting them autonomy to self-govern education, law, and religious practices, provided they met imperial tax and loyalty obligations (Barkey, 2008). This balance of central authority and local autonomy fostered stability across these empires.
6.2 At the technological level
Technological resilience requires a vision that prioritizes durability over convenience. While the history of technology has provided robust tools, modern consumerism often favors fragile, comfort-driven designs. Yet, what doesn’t exist can’t break—e.g., if cars don’t have electric windows, the electric mechanisms can’t fail.
The Willys, though less fast, safe, or comfortable, reliably served its purpose. Simple, durable technologies—vehicles, farm equipment, generators, water pumps—can be produced affordably to enhance societal resilience with collective awareness and related investments. These technologies could be promoted in the market as developmental technological solutions for developing countries and as safeguards solutions for developed ones, while establishing a new brand market focused on simplicity, resilience and affordability.
Excessive dependence on digital systems and currencies heightens the risk of systemic failure if they collapse (cybersecurity, EMP e.tc.). Acemoglu and Robinson argue that resilient societies balance institutional strength with tangible resources, such as cash, to avoid anarchy during crises (Acemoglu and Robinson, 2012). Therefore, preserving real-world social and economic structures is critical and analyzing trade balances to secure a basic quality of life with self-sufficient, even without prosperity it is an important issue, particularly for maintaining social cohesion and an optimistic outlook in society (Baldwin and Lopez-Gonzalez, 2015).
7 Conclusion
It is observed in nature, infrastructure, and societies that clustering (which needs the creation and management of complexity) fosters growth through economies of scale optimizing the use of resources (Sargentis et al., 2020a; Sargentis et al., 2024c) but reduces resilience. Conversely, declustering enhances resilience as a defensive strategy (Sargentis et al., 2022c) but slows growth. Societies that adapt their socio-technological model to circumstances, embracing flexible structures, ensure stability, resilience, optimism, and dominance.
The vulnerabilities embedded in intricate systems, whether governmental corruption, economic interdependence, or fragile technological designs, threaten societal stability, as evidenced by historical collapses and contemporary crises.
Megacities rely on intricate infrastructure—aqueducts, supply chains, and industrial systems—forming a fragile equilibrium where failures, like water-energy and food supply disruptions can trigger existential crises. Decentralized systems, such as localized water-energy and food management (Sargentis et al., 2024a; Sargentis et al., 2020b; Sargentis et al., 2021b) or regional manufacturing, can enhance resilience by reducing dependency on interconnected world.
The resilience of governmental and technological systems hinges on deliberate design, optimally implemented during periods of stability and prosperity. What is achievable today—whether an innovative concept or a practical tool—may become unattainable following a systemic collapse, underscoring the urgency for proactive planning (Markantonis et al., 2023). It is essential for societies to engage in critical self-reflection to construct robust governance frameworks and technological infrastructures, a necessity that spans both domains (Sargentis et al., 2022d).
By adopting resilience frameworks and adaptive governance, humanity can steer technological growth towards sustainable thriving rather than disintegration. The path forward lies in striking a balance—tempering complexity with oversight, pairing innovation with regulation, and aligning progress with accountability. Only through such equilibrium can societies navigate the challenges of an increasingly interconnected and technology-dependent world, ensuring that advancements bolster resilience rather than precipitate collapse.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
G-FS: Conceptualization, Data curation, Formal Analysis, Funding acquisition, Investigation, Methodology, Project administration, Resources, Software, Supervision, Validation, Visualization, Writing – original draft, Writing – review and editing.
Funding
The author(s) declare that no financial support was received for the research and/or publication of this article.
Acknowledgments
This paper is dedicated to the Willys M151A1 (1963), driven by the author from 2000 to 2007, which provided unforgettable driving experiences and is fondly remembered with nostalgia. Figure 5 top, was created by Chatgpt using the original from the related references. AI tools as Grok and Chatgpt have been used to optimize the translation from the original text. The author would like to thank the editor, the reviewers and Dr. Ioannis Benekos for their creative comments.
Conflict of interest
The author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Correction note
This article has been corrected with minor changes. These changes do not impact the scientific content of the article.
Generative AI statement
The author(s) declare that Generative AI was used in the creation of this manuscript. Grok for helping the translation of the manuscript and ChatGPT for the creation of Figure 5 (the scheches Jeep Willys M151 A2 (1973) and Jeep Wrangler (2024)).
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Aamir, M., Rizvi, S. S. H., Hashmani, M. A., Zubair, M., and Usman, J. A. (2021). Machine learning classification of port scanning and DDoS attacks: a comparative analysis. Mehran Univ. Res. J. Eng. Technol. 40 (1), 215–229. doi:10.22581/muet1982.2101.19
Acemoglu, D., and Robinson, J. A. (2012). Why nations fail: the origins of power, prosperity, and poverty. Crown Business.
Admass, W. S., Munaye, Y. Y., and Diro, A. A. (2024). Cyber security: state of the art, challenges and future directions. Cyber Secur. Appl. 2, 100031–109184. doi:10.1016/j.csa.2023.100031
Allen, C. R., Angeler, D. G., Garmestani, A. S., Gunderson, L. H., and Holling, C. S. (2014). Panarchy: theory and application. Ecosystems 17, 578–589. doi:10.1007/s10021-013-9744-2
America’s Cyber Defence Agency (2025). Advanced persistent threat compromise of government agencies, critical infrastructure, and private sector organizations. Available online at: https://www.cisa.gov/news-events/cybersecurity-advisories/aa20-352a.
Angelakis, A. N. (2017). Hydro-technologies in the minoan era. Water Supply 17 (4), 1106–1120. doi:10.2166/ws.2017.006
Angelakis, A. N., and Koutsoyiannis, D. (2003). “Urban water resources management in ancient Greek times,” in The encycl. Of water sci., markel dekker inc. Editors B. A. Stewart, and T. Howell (New York, N.Y., USA), 999–1007.
Applied Energy Systems (2025). Navigating complexities: the semiconductor shortage’s effect on the auto industry. Available online at: https://www.appliedenergysystems.com/semiconductor-shortages-effect-on-auto-industry/.
Baldwin, R., and Lopez-Gonzalez, J. (2015). Supply-chain trade: a portrait of global patterns and several testable hypotheses. World Econ. 38 (11), 1682–1721. doi:10.1111/twec.12189
Barkey, K. (2008). Empire of difference: the Ottomans in comparative perspective. Cambridge University Press.
Bringatrailer (2025). 1974 AM general M151A2. Available online at: https://bringatrailer.com/listing/1974-american-general-m151a2/.
Brodsky, P. (2023). Total international internet bandwidth now stands at 1,217 tbps. Available online at: https://blog.telegeography.com/total-international-bandwidth-now-stands-at-1217-tbps.
BTC to US$ (2025). BTC to US$. Available online at: https://www.google.com/finance/quote/BTC-USD.
Cadwalladr, C., and Graham-Harrison, E. (2018). Revealed: 50 million Facebook profiles harvested for Cambridge analytica in major data breach, 17.3. The Guardian. Available online at: https://www.theguardian.com/news/2018/mar/17/cambridge-analytica-facebook-influence-us-election.
Carter, L., and Douglas, R. B. (2015). “Subsea telecommunications,”In the routledge handbook of ocean resources and management. Editors H. D. Smith, J. Luis Suárez de Vivero, and T. S. Agardy (Routlege). doi:10.4324/9780203115398
Charette, R. N. (2020). The electric vehicle revolution: challenges in automotive electronics. IEEE Spectr. 57 (10), 34–39. doi:10.1109/MSPEC.2020.9214567
Chatzimpiros, P., Lagos, G., and Sargentis, G.-F. (2007). “Man and city. Myth and vision,” in Proceedings of the 10th international conference on environmental science and technology, kos island, Greece, 5–7 September 2007. Department of environmental studies (University of the Aegean). doi:10.5281/zenodo.3767046
Chestney, N. (2025). EU power grid needs trillion-dollar upgrade to avert Spain-style blackouts. Reuters. Available online at: https://www.reuters.com/sustainability/climate-energy/eu-power-grid-needs-trillion-dollar-upgrade-avert-spain-style-blackouts-2025-05-05/.
Chin, K. (2025). The impact of social media on cybersecurity. UpGuard. 2 Jan 2025. Available online at: https://www.upguard.com/blog/the-impact-of-social-media-on-cybersecurity.
CIMSS Satellite Blog (2025). Power outage on the Iberian peninsula in the day night band. Available online at: https://cimss.ssec.wisc.edu/satellite-blog/archives/64451.
Clintel (2025). There is no climate emergency. Available online at: https://clintel.org/world-climate-declaration/.
Coase, R. H. (1937). The nature of the firm. Economica 4 (16), 386–405. doi:10.1111/j.1468-0335.1937.tb00002.x
Council of Europe (2025). Greece: criminal justice system inadequate to counter corruption. Available online at: https://www.coe.int/en/web/portal/-/greece-despite-some-improvements-more-work-needed-to-restore-ability-of-criminal-justice-system-to-counter-corruption.
Cummings, L. L. (1984). Normal accidents: living with high-risk technologies. Pinceton University Press. Available online at: https://books.google.gr/books?hl=en&lr=&id=g66J6Vzq6EYC&oi=fnd&pg=PR5&dq=Normal+Accidents:+Living+with+High-Risk+Technologies.
Di Iorio, A., Kosse, A., and Mattei, I. (2024). Embracing diversity, advancing together – results of the 2023 BIS survey on central bank digital currencies and crypto. BIS. Monetary and Economic Department. Available online at: https://www.bis.org/publ/bppdf/bispap147.pdf.
Dionysopoulos, L., Marra, M., and Urquhart, A. (2024). Central bank digital currencies: a critical review. Int. Rev. Financial Analysis 91, 103031. ISSN 1057-5219. doi:10.1016/j.irfa.2023.103031
Du Boff, R. B. (1983). The telegraph and the structure of markets in the United States, 1845-1890. Res. Econ. Hist. 8, 253–277.
Dunbar, R. I. M. (1992). Neocortex size as a constraint on group size in Primates. J. Hum. Evol. 22 (6), 469–493. doi:10.1016/0047-2484(92)90081-j
Dupont, B., Shearing, C., Bernier, M., and Leukfeldt, R. (2023). The tensions of cyber-resilience: from sensemaking to practice. Comput. and Secur. 132, 103372. 0167-4048. doi:10.1016/j.cose.2023.103372
Finn, B., and Yang, D. (2009). Communications under the seas: the evolving cable network and its implications. Cambridge, MA: The MIT Press. doi:10.7551/mitpress/9780262012867.001.0001
Fitzpatrick, S. (1999). Everyday stalinism: ordinary life in extraordinary times: soviet Russia in the 1930s. Oxford University Press.
Flightradar (2025). Flightradar. Available online at: https://www.flightradar24.com/.
Freund, C., Maliszewska, M., Mattoo, A., and Ruta, M. (2020). When elephants make peace: the impact of the China-US trade agreement on developing countries. World Bank policy Res. Work. Pap. (9173). Available online at: https://documents1.worldbank.org/curated/en/925591583252308139/pdf/When-Elephants-Make-Peace-The-Impact-of-the-China-U-S-Trade-Agreement-on-Developing-Countries.pdf.
Friedman, M. A. (1960). Program for monetary stability. New York, NY, USA: Fordham University Press.
Garfinkel, C. I. (2017). The governance of urban sustainability transitions in the global south. Environ. Res. Lett. 12 (3), 031001. doi:10.1088/1748-9326/aa60a4
Garnsey, P., and Saller, R. P. (1987). The roman empire: economy, society and culture. University of California Press.
Gómez, J. M., and Verdú, M. (2017). Network theory May explain the vulnerability of medieval human settlements to the black death pandemic. Sci. Rep. 7, 43467. doi:10.1038/srep43467
Guinness World Records (2025). Largest cryptocurrency hack. Available online at: https://www.guinnessworldrecords.com/world-records/696467-largest-cryptocurrency-hack.
Haldane, A. G. (2009). “Rethinking the financial network,” in Speech delivered at the financial student association. Amsterdam: Bank of England. Available online at: https://www.bankofengland.co.uk/speech/2009/rethinking-the-financial-network.
Haldon, J. F. (1997). Byzantium in the seventh century: the transformation of a culture. Cambridge University Press.
Headquarters Department of the Army Washington DC (1983). Organization maintenance manual for M151A2. Available online at: https://www.jeepolog.com/UserFiles/downloads/m151/TM_9-2320-218-20-1-1.pdf.
Headrick, D. R. (1991). The invisible weapon: telecommunications and international politics, 1851-1945. Oxford University Press.
Homer-Dixon, T., Walker, B., Biggs, R., Crépin, A. S., Folke, C., Lambin, E. F., et al. (2015). Synchronous failure: the emerging causal architecture of global crisis. Ecol. Soc. 20 (3), 6. doi:10.5751/ES-07681-200306
Homer-Dixon, T. F. (2006). The upside of Down: Catastrophe, creativity, and the renewal of civilization. Island Press.
Human Progress (2025). Human progress. Available online at: https://humanprogress.org/.
Iliopoulou, T., and Koutsoyiannis, D. (2025). Have rainfall patterns changed? A global analysis of long-term rainfall records and Re-Analysis data. Herit. Found. Available online at: https://www.heritage.org/environment/report/have-rainfall-patterns-changed-global-analysis-long-term-rainfall-records.
IPCC (2021-2023). Sixth assessment report. Available online at: https://www.ipcc.ch/assessment-report/ar6/.
Jeep Wrangler (2020). Clutch pedals for 2020 jeep wrangler. Available online at: https://store.mopar.ca/v-2020-jeep-wrangler--unlimited-sahara--3-6l-v6-gas/clutch--clutch-pedals.
Jeep Wrangler (2025). Jeep® wrangler. Available online at: https://www.jeep.gr/jeep-wrangler/plug-in.
Johnston, I., and Hancock, A. (2025). Spain and Portugal blackout blamed by critics on solar power dependency. Financial Times. Available online at: https://www.ft.com/content/e6e1fe13-36f7-4fe5-84ba-77717dca68a8.
Keynes, J. M. (1936). The general theory of employment, interest and money. London, UK: Palgrave Macmillan.
Kopp, C. (2003). “The electromagnetic bomb—A weapon of electrical mass destruction,” in Security and environment in the mediterranean. Editor H. G. Brauch (Springer), 645–656.
Koutsoyiannis, D. (2025). When are models useful? Revisiting the quantification of reality checks. Water 17 (2), 264. doi:10.3390/w17020264
Koutsoyiannis, D., and Iliopoulou, T. (2024). Understanding climate: gifts from the nile. 60 pages, SR 301. Washington, DC, USA: The Heritage Foundation.
Koutsoyiannis, D., Iliopoulou, T., Koukouvinos, A., Malamos, N., Mamassis, N., Dimitriadis, P., et al. (2023). In search of climate crisis in Greece using hydrological data: 404 Not Found. Water 15 (9), 1711. doi:10.3390/w15091711
Koutsoyiannis, D., and Sargentis, G.-F. (2021). Entropy and wealth. Entropy 23, 1356. doi:10.3390/e23101356
Koutsoyiannis, D., and Sargentis, G.-F. (2024). “Market empire dead end, reflections without custody,” in memory of Themistocles Xanthopoulos. Editors D. Koutsoyiannis, N. D. Lagaros, and A. G. Boudouvis (Athens: National Technical University of Athens Press – National Technical University of Athens), 99–123.
Lee, K., and Shin, J. (2019). The evolution of automotive technology: from mechanical to electronic dominance. Transp. Res. Part A Policy Pract. 128, 112–130. doi:10.1016/j.tra.2019.07.005
Lester, S. (2011). The globalization paradox: democracy and the future of the world economy by Dani rodrik New York: Norton, 2011. World Trade Rev. 10 (1), 409–417. doi:10.1017/s1474745611000231
Lloyd and Co, H. H., and Norman, B. (1872). Map showing the telegraph lines in operation, under contract, and contemplated, to complete the circuit of the globe. Leventhal Map and Educ. Cent. Available online at: https://collections.leventhalmap.org/search/commonwealth:7h149w260.
Love, J. J. (2018). The electric storm of November 1882. Space weather 16, 37–46. doi:10.1002/2017SW001795
Madhusudan Rao, D. V., and David, A. (2022). Refined model of maslow’s needs theory in internet era. Organ. Hum. Cap. Dev. (ORCADEV) 1 (1), 1–11. Available online at: https://journals.researchsynergypress.com/index.php/orcadev/issue/view/46.
Marine traffic (2025). Marine traffic. Available online at: https://www.marinetraffic.com/.
Markantonis, D., Sargentis, G.-F., Dimitriadis, P., Iliopoulou, T., Siganou, A., Moraiti, K., et al. (2023). Stochastic evaluation of the investment risk by the scale of water infrastructures—case study: the municipality of west mani (greece). World 4, 1–20. doi:10.3390/world4010001
Marx, K. (1867). “Capital. A critique of political economy,” in Das Kapital: kritik der Politischen Oekonomie (Hamburg, Germany: Verlag von Otto Meissner), 1.
Marx, K. (1875). Critique of the gotha programme. Available online at: https://www.marxists.org/archive/marx/works/1875/gotha/ch01.htm.
Maslow, A. H. (1943). A theory of human motivation. Psychol. Rev. 50 (4), 370–396. doi:10.1037/h0054346
McDonald, R. I., Weber, K. F., Padowski, J., Boucher, T., and Shemie, D. (2016). Estimating watershed degradation over the last century and its impact on water-treatment costs for the world’s large cities. Proc. Natl. Acad. Sci. 113 (32), 9117–9122. doi:10.1073/pnas.1605354113
Middleton, G. D. (2017). Understanding collapse. Cambridge: Cambridge University Press. doi:10.1017/9781316584941
Nakamoto, S. (2008). Bitcoin: a peer-to-peer electronic cash system. Available online at: https://bitcoin.org/bitcoin.pdf.
North, D. C. (1990). Institutions, institutional change and economic performance. Cambridge University Press.
O’Neil, C. (2016). Weapons of math destruction: how big data increases inequality and threatens democracy. Crown Publishing Group.
Plucinska, J., Hepher, T., and Muvija, M. (2025). Heathrow shutdown raises concerns over contingency planning. Reuters. Available online at: https://www.reuters.com/business/aerospace-defense/heathrow-shutdown-raises-concerns-over-contingency-planning-2025-03-21/.
Ramos, S., Pianese, F., Leach, T., and Oliveras, E. (2021). A great disturbance in the crypto: understanding cryptocurrency returns under attacks. Blockchain Res. Appl. 2 (3), 100021. doi:10.1016/j.bcra.2021.100021
Reed, S., and Gross, J. (2025). How spain’s success in renewable energy may have left it vulnerable. The New York Times. Available online at: https://web.archive.org/web/20250430045259/https://www.nytimes.com/2025/04/29/business/spain-renewable-energy-power-grid.html.
Reporters without Borders (2025). Reporters without borders. Available online at: https://rsf.org/en/index.
Reuters (2025a). Don’t blame renewables for Spain’s power outage. Available online at: https://www.reuters.com/business/energy/dont-blame-renewables-spains-power-outage-bousso-2025-04-30/.
Reuters (2025b). What caused the power outage in Spain and Portugal? Available online at: https://www.reuters.com/world/europe/what-could-be-behind-iberian-power-outage-2025-04-29/.
Reuters (2025c). Spain, Portugal switch back on, seek answers after biggest ever blackout. Reuters. April, 29. Available online at: https://www.reuters.com/world/europe/spains-power-generation-nearly-back-normal-after-monday-blackout-says-grid-2025-04-29/.
Roberts, P. C. (2025c). An analysis of EMP attack on the U.S. power grids and critical national infrastructure. PaulCraigRoberts.Org. Available online at: https://www.paulcraigroberts.org/2025/03/20/an-analysis-of-emp-attack-on-the-u-s-power-grids-and-critical-national-infrastructure/.
Roser, M. (2020). Breaking out of the Malthusian trap: how pandemics allow Us to understand why our ancestors were stuck in poverty. ourWorldInData.org. Available online at: https://ourworldindata.org/breaking-the-malthusian-trap.
Safitra, M. F., Lubis, M., and Fakhrurroja, H. (2023). Counterattacking cyber threats: a framework for the future of cybersecurity. Sustainability 15, 13369. doi:10.3390/su151813369
Sargentis, G.-F. (2022). “Issues of prosperity: stochastic evaluation of data related to environment, infrastructures, economy and society”. Athens, Greece: National Technical University of Athens. Ph.D. Thesis.
Sargentis, G.-F., Defteraios, P., Lagaros, N. D., and Mamassis, N. (2022b). Values and costs in history: a case study on estimating the cost of hadrianic aqueduct’s construction. World 3, 260–286. doi:10.3390/world3020014
Sargentis, G.-F., Dimitriadis, P., Ioannidis, R., Iliopoulou, T., Frangedaki, E., and Koutsoyiannis, D. (2020b). Optimal utilization of water resources for local communities in mainland Greece (case study of karyes, Peloponnese). Procedia Manuf. 44, 253–260. doi:10.1016/j.promfg.2020.02.229
Sargentis, G.-F., Iliopoulou, T., Dimitriadis, P., Mamassis, N., and Koutsoyiannis, D. (2021a). Stratification: an entropic view of society’s structure. World 2, 153–174. doi:10.3390/world2020011
Sargentis, G.-F., Iliopoulou, T., Ioannidis, R., Kougkia, M., Benekos, I., Dimitriadis, P., et al. (2025b). Technological advances in flood risk assessment and related operational practices since the 1970s: a case study in the pikrodafni river of Attica. Water 17 (1), 112. doi:10.3390/w17010112
Sargentis, G.-F., Iliopoulou, T., Sigourou, S., Dimitriadis, P., and Koutsoyiannis, D. (2020a). Evolution of clustering quantified by a stochastic method—case studies on natural and human social structures. Sustainability 12, 7972. doi:10.3390/su12197972
Sargentis, G.-F., and Ioannidis, R. (2024). The impacts of altering biodiversity to the water–energy–food nexus: case study north euboea, Greece. Discov. Water 4, 105. doi:10.1007/s43832-024-00165-y
Sargentis, G.-F., Ioannidis, R., Bairaktaris, I., Frangedaki, E., Dimitriadis, P., Iliopoulou, T., et al. (2022c). Wildfires vs. sustainable forest partitioning. Conservation 2, 195–218. doi:10.3390/conservation2010013
Sargentis, G.-F., Ioannidis, R., Dimitriadis, P., Malamos, N., Lyra, O., Kitsou, O., et al. (2024a). “Energy self-sufficiency in rural areas, case study: north euboea, Greece,” in Advances in environmental and engineering research, 2766–6190. doi:10.21926/aeer.2404025
Sargentis, G.-F., Ioannidis, R., Karakatsanis, G., Sigourou, S., Lagaros, N. D., and Koutsoyiannis, D. (2019). The development of the Athens water supply system and inferences for optimizing the scale of water infrastructures. Sustainability 11, 2657. doi:10.3390/su11092657
Sargentis, G.-F., Ioannidis, R., Mamassis, N., Zoukos, V., and Koutsoyiannis, D. (2025a). A review of the energy policy in Greece in the last 50 years and its implications for prosperity. Clean Energy Sustain. 3, 10021. doi:10.70322/ces.2024.10021
Sargentis, G.-F., and Kougkia, M. (2024). Vulnerabilities of water-energy and food nexus in cities of digital era. Insight - Civ. Eng. 7 (1), 608. doi:10.18282/ice.v7i1.608
Sargentis, G.-F., and Koutsoyiannis, D. (2023). The function of money in water–energy–food and land nexus. Land 12, 669. doi:10.3390/land12030669
Sargentis, G.-F., Koutsoyiannis, D., Angelakis, A., Christy, J., and Tsonis, A. A. (2022d). Environmental determinism vs. social dynamics: prehistorical and historical examples. World 3, 357–388. doi:10.3390/world3020020
Sargentis, G.-F., Lagaros, N. D., Cascella, G. L., and Koutsoyiannis, D. (2022a). Threats in water–energy–food–land nexus by the 2022 military and economic conflict. Land 11, 1569. doi:10.3390/land11091569
Sargentis, G.-F., Mamassis, N., Kitsou, O., and Koutsoyiannis, D. (2024b). The role of technology in the water–energy–food nexus. A case study: Kerinthos, north euboea, Greece. Front. Water 6, 1343344. doi:10.3389/frwa.2024.1343344
Sargentis, G.-F., Mamassis, N., and Koutsoyiannis, D. (2024c). The multifaceted importance of mediterranean pine-tree forests to social cohesion. Energy, resin, grazing, and wildfire management in north euboea, Greece. Nat. Resour. Conservation Res. 7 (2), 9962. doi:10.24294/nrcr9962
Sargentis, G.-F., and Markantonis, D. (2024). Water-energy-food nexus and its stochastic dynamics: case study Greece. Discov. Sustain. 5, 511. doi:10.1007/s43621-024-00751-z
Sargentis, G.-F., Siamparina, P., Sakki, G.-K., Efstratiadis, A., Chiotinis, M., and Koutsoyiannis, D. (2021b). Agricultural land or photovoltaic parks? The water–energy–food nexus and land development perspectives in the Thessaly plain, Greece. Sustainability 13, 8935. doi:10.3390/su13168935
Schippers, M. C., Ioannidis, J. P., and Luijks, M. W. (2024). Is society caught up in a death spiral? Modeling societal demise and its reversal. Front. Sociol. 9, 1194597. doi:10.3389/fsoc.2024.1194597
Schneider, K., and Gibson, F. (2025). Chaos in the skies: 'nightmare' heathrow shutdown in numbers. Sky News 21 (3). Available online at: https://news.sky.com/story/chaos-in-the-skies-nightmare-heathrow-shutdown-in-numbers-13333274.
Schneier, B. (2015). Data and goliath: the hidden battles to collect your data and control your world. W.W. Norton and Company.
Söderbaum, P. (2016). Ecological economics: a political economics approach to environment and development. Routledge.
Standage, T. (1998). The victorian internet: the remarkable story of the telegraph and the nineteenth century's online pioneers. Weidenfeld and Nicolson.
Stiglitz, J. E. (2017). Globalization and its discontents revisited: anti-Globalization in the era of trump. WW Norton and Company.
Suny, R. G. (2010). The Soviet experiment: russia, the USSR, and the successor states. Oxford University Press.
Tapscott, D., and Tapscott, A. (2016). Blockchain revolution: how the technology behind bitcoin is changing money, business, and the world. Portfolio/Penguin.
TeleGeography (2025). Submarine cable map. Available online at: https://www.submarinecablemap.com/.
The Free Encyclopedia (2025). Maslow’s hierarchy of needs. Available online at: https://en.wikipedia.org/wiki/Maslow%27s_hierarchy_of_needs.
The Guardian (2020). Blackouts can happen anywhere: how power systems worldwide can collapse. Guard. Available online at: https://www.theguardian.com/business/2025/may/02/blackouts-energy-outage-risks-europe-worldwide-spain-portugal-france
The Guardian (2025). What caused the blackout in Spain and Portugal and did renewable energy play a part? Guard. Available online at: https://www.theguardian.com/environment/2025/apr/29/what-caused-the-blackout-in-spain-and-portugal-and-did-renewable-energy-play-a-part.
The Washington Post (2025). Trump May have just ended globalization as we know it. Available online at: https://www.washingtonpost.com/business/2025/04/04/trump-tariffs-plan-economic-policy-free-trade/.
The World Bank (2025a). GDP per capita growth (annual %). Available online at: https://data.worldbank.org/indicator/NY.GDP.PCAP.KD.ZG.
The World Bank (2025b). GNI growth (annual %). Available online at: https://data.worldbank.org/indicator/NY.GNP.MKTP.KD.ZG.
Transparency International (2024). Global corruption barometer 2024. Available online at: https://www.transparency.org/en/gcb/global/global-corruption-barometer-2024.
UNEP (2024). Emissions gap report 2024. Available online at: https://www.unep.org/emissions-gap-report-2024.
United Nations (2018). World urbanization prospects: the 2018 revision. Department of Economic and Social Affairs. Available online at: https://population.un.org/wup/assets/WUP2018-Report.pdf.
Vicente-Serrano, S. M., Tramblay, Y., Reig, F., González-Hidalgo, J. C., Beguería, S., Brunetti, M., et al. (2025). High temporal variability not trend dominates mediterranean precipitation. Nature 639, 658–666. doi:10.1038/s41586-024-08576-6
Ward, J., and Smith, P. (2018). Automotive repair trends: the shift to specialized maintenance. J. Automot. Technol. 9 (2), 78–92. doi:10.1080/09537325.2018.1454492
Williamson, O. E. (1973). Markets and hierarchies: some elementary considerations. Am. Econ. Rev. 63 (2), 316–325.
Wittfogel, K. (1981). Oriental despotism; a comparative study of total power. New York: Random House.
World Economic Forum (2022). “Global risks report 2022,” in Digital dependencies and cyber vulnerabilities. Available online at: https://www.weforum.org/publications/global-risks-report-2022/in-full/chapter-3-digital-dependencies-and-cyber-vulnerabilities/.
Wright, G., and Haltiwanger, J. (2022). Supply chain disruptions and their economic impact: lessons from the COVID-19 pandemic. J. Econ. Perspect. 36 (2), 123–148. doi:10.1257/jep.36.2.123
Xi, J. (2015). Speech by H.E. Xi Jinping president of the people's Republic of China at the welcoming dinner hosted by local governments and friendly organizations in the United States. Seattle, 22 September 2015. Available online at: https://www.mfa.gov.cn/eng/zy/jj/2015zt/xjpdmgjxgsfwbcxlhgcl70znxlfh/202406/t20240606_11381543.html.
Keywords: complexity, human progress, resilience, technology, governance, systemic vulnerabilities, economic conflicts, self-sufficiency
Citation: Sargentis G-F (2025) Fragility in human progress. A perspective on governance, technology and societal resilience. Front. Complex Syst. 3:1609467. doi: 10.3389/fcpxs.2025.1609467
Received: 10 April 2025; Accepted: 17 July 2025;
Published: 10 September 2025; Corrected: 29 September 2025.
Edited by:
Rosa Maria Benito, Polytechnic University of Madrid, SpainReviewed by:
Joon-Young Moon, Sungkyunkwan University, Republic of KoreaJosé Manuel Galán, University of Burgos, Spain
Copyright © 2025 Sargentis. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: G.-Fivos Sargentis, Zml2b3NAaXRpYS5udHVhLmdy
 G.-Fivos Sargentis
G.-Fivos Sargentis