- 1Department of Mechanical Engineering and Mechanics, Lehigh University, Bethlehem, PA, United States
- 2Department of Electrical and Computer Engineering, Lehigh University, Bethlehem, PA, United States
Resonance is a well-known phenomenon that happens in systems with second order dynamics. In this paper, we address the fundamental question of making a network robust to signal being periodically pumped into it at or near a resonant frequency by an adversarial agent with the aim of saturating the network with the signal. Toward this goal, we develop the notion of network vulnerability, which is measured by the expected resonance amplitude on the network under a stochastically modeled adversarial attack. Assuming a second order dynamics model based on the network graph Laplacian and a known stochastic model for the adversarial attack, we propose two methods for minimizing the network vulnerability–one through direct optimization of the spectrum of the network graph, and another through optimization of an auxiliary network graph attached to the main network. We provide theoretical foundations for these methods as well as extensive numerical results analyzing the effectiveness of both methods in reducing the network vulnerability.
1 Introduction
In this paper we consider the phenomenon of runaway amplification of signal in a network due to resonance, which has implications on security of the network. This is possible if an adversarial agent pumps signal into one or more vertices of the network in a periodic manner at a frequency that matches or is very close to one of the natural frequencies of the network. This phenomenon is observed in networks with a second order signal dynamics.
While second order dynamics over networks has been studied in the past van der Schaft and Maschke (2013), Chow and Kokotovic (1985), Romeres et al. (2013), Cheng et al. (2017), especially in context of power grids (since power transmission using alternating currents are described naturally using second-order dynamics), existing literature does not focus on controlling network parameters and topology for the purpose of mitigation of resonance.
The contributions of this paper are as follows.
• We develop a second-order dynamics model (represented by a system of second order differential equations) for signal transmission over a network under external forcing (source of the adversarial signal), that is consistent with the network topology (Section 3).
• We develop the notion of network vulnerability, measured by the expected resonance amplitude under stochastically modeled adversarial forcing (Section 3).
• We propose two methods, namely, Network Graph Optimization and Auxiliary Graph Optimization, for optimizing the network graph’s edge weights (representing the connection strength between two network nodes) to reduce expected resonance under the following conditions respectively: (i) the main network can be altered by modifying its edge weights, (ii) edge weights of the main network cannot be modified directly, but an auxiliary network can be attached to it. We develop theoretical foundationd for the respective optimization problems that can be solved via centralized solvers (Sections 4 and 5).
• We analyze the performance of both methods through extenive numerical experiments and numerical analysis of the effect of the hyper-parameters involved in the problems (Section 6).
2 Related work
The Laplacian dynamics on a graph,
While first-order signal dynamics is most well-studied in context of networks (Mirzaev and Gunawardena, 2013; Olfati-Saber and Murray, 2004; Ren et al., 2005), higher-order dynamics has also been studied. A second-order dynamics over a network is relevant, for example, in context of distributed power grids, electrical circuits and consensus in such networks (Romeres et al., 2013; Dorfler et al., 2018; Nagpal et al., 2023), where the dynamics of alternating electrical current and voltage are naturally second order. The motion dynamics of mobile agents (e.g., robots) is often governed by Newtonian dynamics, which gives rise to second-order dynamics over a network of such agents Olfati-Saber (2006). Second order dynamics can also be used to model transmission of information on social networks where the transmissibility of a signal depends both on its amount (how widespread it is) and its rate of change (how “viral” it is). The properties of second-order dynamics over networks have been well-studied in the literature (see van der Schaft and Maschke (2013); Chow and Kokotovic (1985) for example,), and model reduction in the context of such dynamics has been investigated (Romeres et al., 2013; Cheng et al., 2017). However, existing literature does not focus on active control of network parameters and topology for the purpose of prevention of resonance.
It is a common practice to rely on heuristic indicators to develop strategies for controlling network performance. Optimization of the spectrum of the Laplacian matrix in order to affect the connectivity of a network has been studied De Gennaro and Jadbabaie (2006); Sun et al. (2018); Saif et al. (2024). In Zhang et al. (2021), authors aim to limit the transmission of a signal across a network by identifying and reducing the weights of critical edges that connect clusters within the network. Authors consider the spectral radius, algebraic connectivity, effective resistance and other spectral measures to quantify the robustness of graphs, and develop an algorithmic approach to degree-preserving rewiring to optimize robustness in Chan and Akoglu (2016). External attacks that eliminate parts of the network (nodes and edges) are considered in Sheng et al. (2022), where the node degree variance and spectral radius of the graph is minimized and the connectivity is maximized by jointly optimizing graph topology and edge weights. A multi-agent system is considered in Griparic et al. (2022) and a distributed approach based on feedback control is developed to estimate and optimize the connectivity of the communication network between the agents. A similar problem is addressed in Mox et al. (2022), which leverages convolutional neural networks to learn how communication agents should be positioned from an optimization-based solution to the problem. The method is shown to scale to large networks of agents. Readers may refer to Freitas et al. (2023) for a more detailed survey on robustness measures, attack and defense strategies for networks. Although the research in this category is extensive, researchers have relied on spectral measures as heuristic indicators of network performance in general, without explicitly addressing performance of a second-order signal dynamics over the network as we do in this paper.
Graph sparsification methods aim to approximate a given graph with a sparse one Spielman and Srivastava (2008), with the purpose of simplifying analysis or improving computational efficiency Chen et al. (2023); Hashemi et al. (2024). These methods could potentially be leveraged to sever the signal transmission along a network, however, to the best of our knowledge, it is not explored whether such a modification of the network would result in resonance reduction or if the network performance could be maintained afterwards.
In this paper we consider a general second-order dynamics over a network with external forcing. We particularly focus on developing methods for mitigating resonance attacks inflicted by an adversarial agent pumping oscillatory signal in a periodic manner at one or more vertices while trying to match a natural frequency of the network. To our knowledge, there has been no prior work on control of resonance in a general graphical network with a focus on increasing robustness of the network to adversarial attacks.
3 Motivation & background
We consider a network (referred to as the main network) represented by a weighted undirected graph
The signal on the
In it is simplest form, such a dynamics can be constructed as a natural extension of the first-order Laplacian dynamics, such that the second derivative of the signal on the
This dynamics can be compactly written as
The Laplacian matrix satisfies the property that its
In this paper we consider a more general form of second-order linear dynamics for signals following second order differential equation Meirovitch (2010):
where,
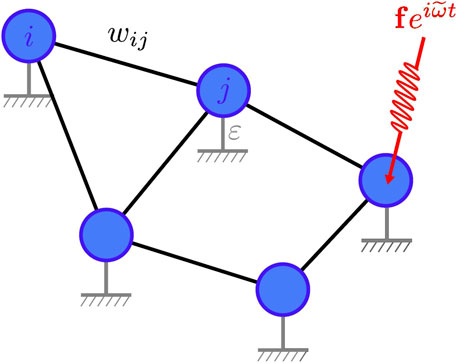
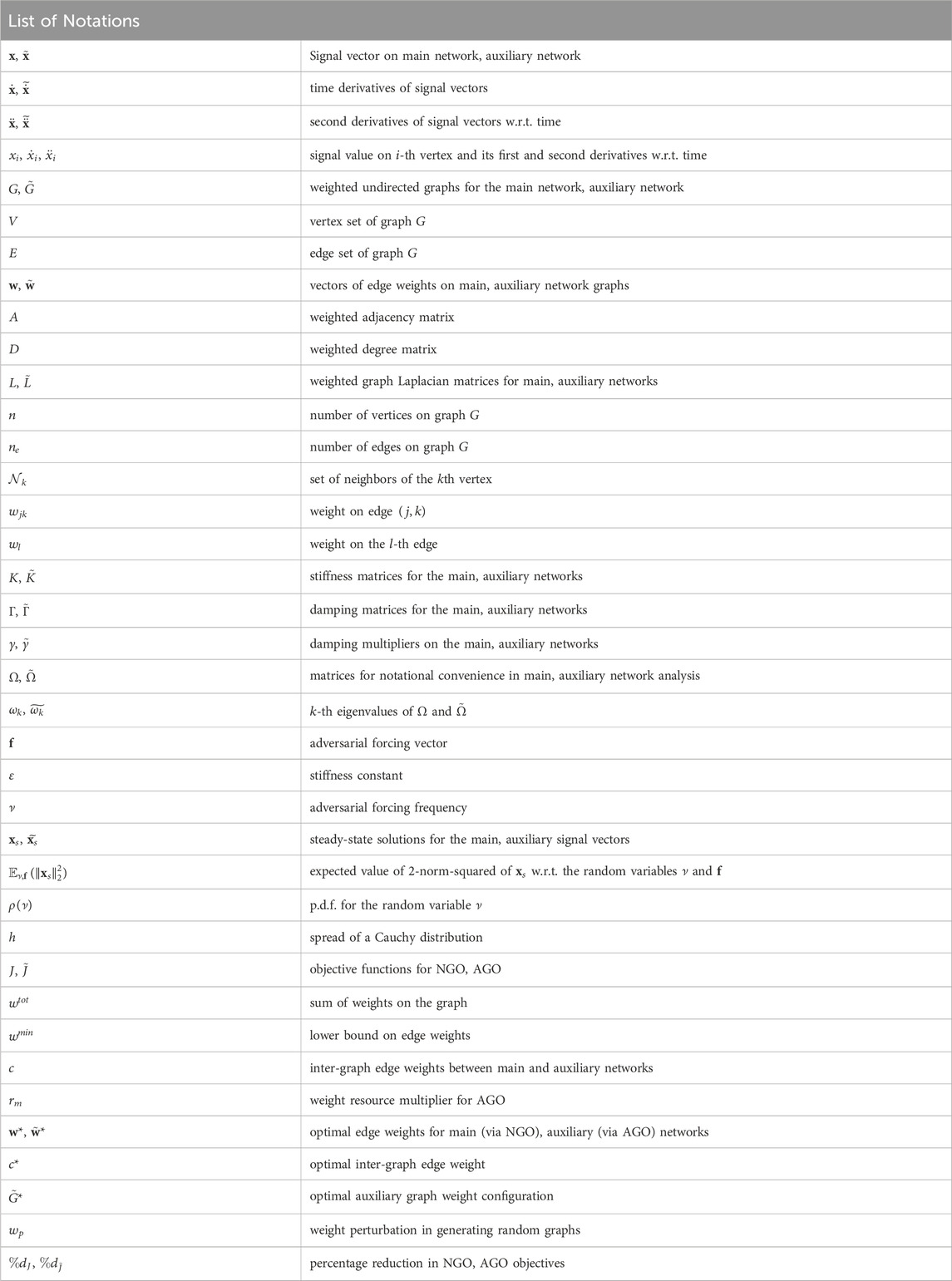
Figure 1. Illustration of a network being attacked by an adversarial agent trying to cause resonance.
The solution to (1), when there is no external forcing (i.e.,
It is a well-known fact that if the forcing frequency
We assume that the adversarial agent tries to match its forcing frequency,
Definition 1. (Network Vulnerability to Adversarial Resonance Attack). We define the network vulnerability to adversarial resonance attack to be the expected value of the squared 2-norm of the steady-state response, denoted as
The main objective of this work is to develop approaches for optimization of the spectrum of the network graph (i.e., the spectrum of the Laplacian matrix, or equivalently, the spectrum of
(1) A direct optimization of the weights on the edges of the network that minimizes
(2) When it is not possible to alter the weights on the edges directly, we propose to attach an auxiliary network to the main network, and tune/optimize it such that this auxiliary network can effectively absorb and dissipate the excess energy from the resonance in the main network while minimizing the expected steady-state amplitude on the main network. We refer to this approach as Auxiliary Graph Optimization (Section 5).
In this work we only focus on optimizing the weights on the edges of a network graph with fixed topology. However it can be noted that in a weighted graph, a weight of zero on an edge is equivalent to the edge being removed from the graph as far as signal dynamics is concerned. Although it is possible to remove edges with low weight from the graph to sever the signal flow to reduce any potential resonance, this approach would undermine the transmission of the desired signals along the network. We thus use non-zero lower bounds on edge weights when formulating the optimization problems. While addition of edges to the graph is also not addressed within the framework of our optimization problems, starting with a complete graph topology can ensure that all possible edges are present to begin with.
4 Network graph optimization
Given an initial configuration of the main network specified via the graph
In this section, we formulate the spectrum optimization problem to minimize the vulnerability of the network (i.e., the expected value of the squared 2-norm of the steady state response).
4.1 Stochastic model of the adversarial forcing
We assume that the forcing vector
We assume that the adversarial agent has uncertain knowledge of the network (or equivalently precise knowledge of the network, but uncertainty/error in choosing a forcing frequency). This uncertainty/error manifests itself when the adversarial agent tries to pick a forcing frequency that matches one of the natural frequencies of the network. We model this uncertainty by considering
The Cauchy distribution, as opposed to other probability distributions, allows the integral representing the expected value of
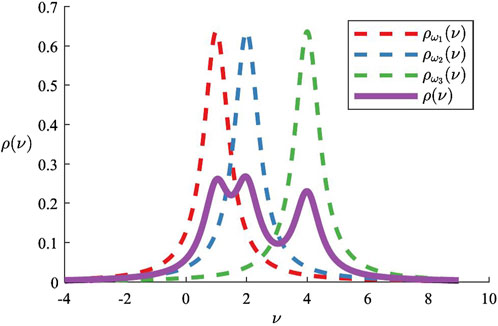
Figure 2. Cauchy distributions centered at the natural frequencies
4.2 Network vulnerability
Following proposition computes the network vulnerability in terms of the spectrum of the network.
Proposition 1. (Network vulnerability). If
In order to prove this result we need the following lemmas.
Lemma 1. If
The proof of the above lemma is deferred to Appendix 7.1 for better readability.
Lemma 2. If
The above lemma follows from the definition of the Frobenius norm,
Proof of Proposition 1. The expected value of
where
Since
Assuming
The objective is to minimize this expected value of the 2-norm of the steady-state amplitude, so as to mitigate the effects of resonance attacks on the network. We note that
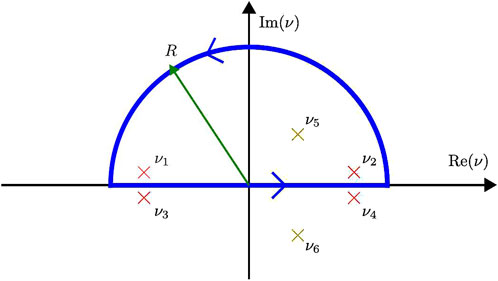
Figure 3. Integration contour for Equation 5. Poles
Proposition 2. For a sufficiently large value of
Proof Sketch. Define the symmetrized function
When
As a consequence of the above proposition, while
4.3 Spectrum optimization of the main network graph
We define the spectrum optimization problem of the main network graph as the problem of minimizing the expected steady-state amplitude of signal on the network under the described stochastic forcing:
where
We consider non-negative edge weights throughout the paper, which further imply
The optimal edge weights are denoted by
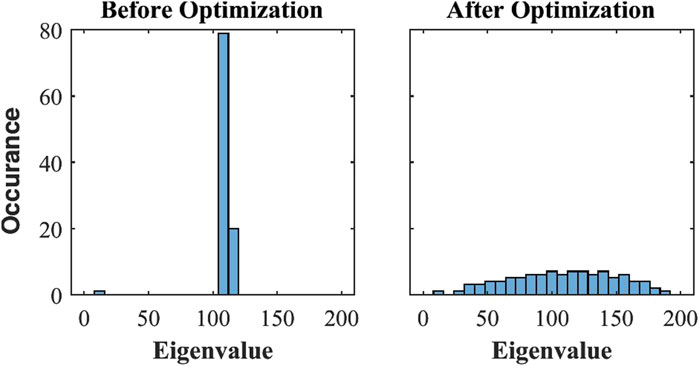
Figure 4. Histograms of the Laplacian matrix eigenvalues for the initial network graph
Observing that the eigenvalues of the graph Laplacian,
In this paper the optimization problem is solved in a centralized manner. A reformulation of
5 Auxiliary graph optimization
We consider the scenario where the main network cannot be manipulated directly and the edge weights of the main graph
In this section, we first reformulate the dynamics equations and the definition of vulnerability based on the combined network (main network
5.1 Formulation of combined dynamics
We denote the graph representation of the auxiliary network by
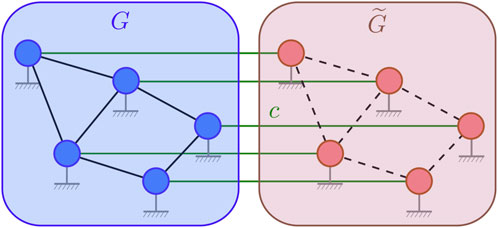
Figure 5. Illustration of an auxiliary graph
We make the following simplifying assumptions about the auxiliary network and its inter-connection with the main network.
i. We assume the auxiliary network has the same number of vertices as the main network (i.e.,
ii. The above assumption allows a one-to-one connection between the vertices of
iii. The inter-connecting edges between
iv. It is assumed that the adversarial agent can attack the main network, but not the auxiliary network.
v. The connectivity of the auxiliary graph is specified via one of the two types: (1) a mirrored auxiliary graph, which exactly mirrors the connectivity of the main graph, and (2) a complete auxiliary graph, which is a complete graph. Note that when the main graph is complete, both types correspond to the same auxiliary graph.
Since the auxiliary network is connected to the main network, with the purpose of mitigating the resonance on the main network under adversarial forcing, based on the above assumptions, the signal dynamics over
where the terms
5.2 Network vulnerability with attached auxiliary network
Following proposition gives the vulnerability of a network to which we attach the auxiliary network.
Proposition 3. (Network vulnerability with attached auxiliary network). The vulnerability of a network to which an auxiliary network is attached is given by
where
When
where
Note that in either of the expressions for
Proof. The steady-state solution to (8) is
However, we note that we are only interested in the response of the main network to the adversarial attacks, which from (Equations 6, 7) is:
where
(As a quick sanity check, note that when
indicating that the steady-state response on the main network is equivalent to the one derived in Equation 1, as expected. In Section 6 we use this theoretical result to perform further numerical sanity check on the Auxiliary Graph Optimization objective function.)
If
According to the stochastic model explained in Section 4.1,
Rest of the proof is similar to the proof of Proposition 1. We use Lemma 1 and Lemma 2, and Equation 11 to compute the expected value with respect to
Later on, we will show that there will be an approximation error between the computed expected value and the average squared 2-norm of the steady-state response when
A closed form expression for the integral in Proposition 3 is obtained using the Residue theorem with the same contour as before as described in Section 4.2. In order to use the Residue theorem as described, however, one needs to compute the roots of the quartic polynomial in
Assuming that the main graph
5.3 Spectrum optimization of the auxiliary network graph
We define the spectrum optimization problem of the auxiliary network graph as follows:
Here, we assume that the weight resource is specified as a multiple of the total weights on the main graph (denoted by
The optimal auxiliary graph edge weights are denoted by
Note that it is also possible to consider the case where the auxiliary damping multiplier
6 Results
In this section, we present experiments conducted to accomplish the following.
• Validate the accuracy of the objective functions,
• Analyze the effects of the problem parameters associated with the network dynamics and constraints on the relative vulnerability decrease that can be achieved via the proposed methods.
• Demonstrate the effectiveness of the proposed methods in decreasing the network vulnerability across a variety of problem instances.
• Perform numerical simulation of dynamics over a network to further validate the results achieved by the Network Graph Optimization.
• Apply the network graph optimization to the communication network among a team of mobile robots between which the signal strength decays with increasing distance.
6.1 Implementation details and setup
We solve the network graph and auxiliary graph spectrum optimizations using the interior-point algorithm The MathWorks (2023).
6.1.1 Network graph construction
All algorithms are implemented and tested on three classes of network graphs.
i. Random Complete Graphs (“RCG”): Given the number of vertices,
ii Random Incomplete Graphs (“RIG”): Given the number of vertices,
iii. Social Network Graphs (“Social”): As a representative of real-world networks, we extracted subgraphs from the “Government” graph category of the Gemsec Facebook Dataset Rozemberczki et al. (2019) which encompasses various graphs representing blue verified Facebook page networks. To generate the subgraphs, ego graphs with a radius of two were created. Nodes were randomly selected without replacement to serve as the center of each ego graph. Only the first 100 subgraphs containing between 25 and 200 vertices that were generated were selected, resulting in a set of 100 subgraphs with an average 109.82 vertices and 867.69 edges per subgraph.
6.1.2 Adversarial force sampling
For computing steady-state amplitudes for specific instances of simulation for a given graph, we need to sample the adversarial forcing vector,
As described in Section 4.1, we assume that the forcing vector
As described in Section 4.1, the forcing frequency needs to be sampled using a probability density function that is a uniformly weighted sum of multiple Cauchy distributions each of which are centered at the natural frequencies,
6.2 Network graph optimization
First we present the results from Network Graph Optimization.
6.2.1 Validation of the objective function
The objective function,
To validate the accuracy of the objective function in representing the expected value, we generate 400M adversarial forcing samples (using the procedure explained in Section 6.1), evaluate the closed-form steady state response,
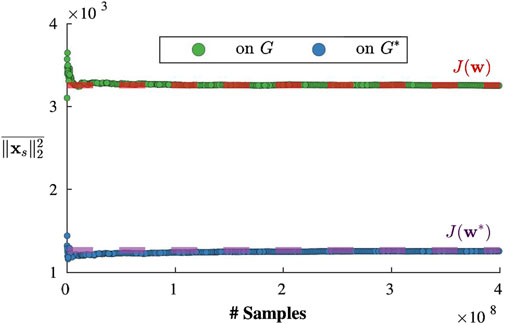
Figure 6. Squared 2-norm of the steady state response
It can be observed that over a large number of forcing samples, the average of the squared 2-norm of the steady-state responses is well approximated by the objective values for both initial and optimized graphs. Hence,
6.2.2 Parameter analysis
Each spectrum optimization problem on a network graph can be specified via a set of parameters regarding the second order dynamics of the network, the external forcing and the constraints. These parameters are the number of vertices on the graph
We analyze the effects of these parameters on the percentage reduction of objective value that can be achieved via the spectrum optimization, hence the reduction in the vulnerability of the main network graph using the Network Graph Optimization method. For this purpose, we start with set of parameter values,
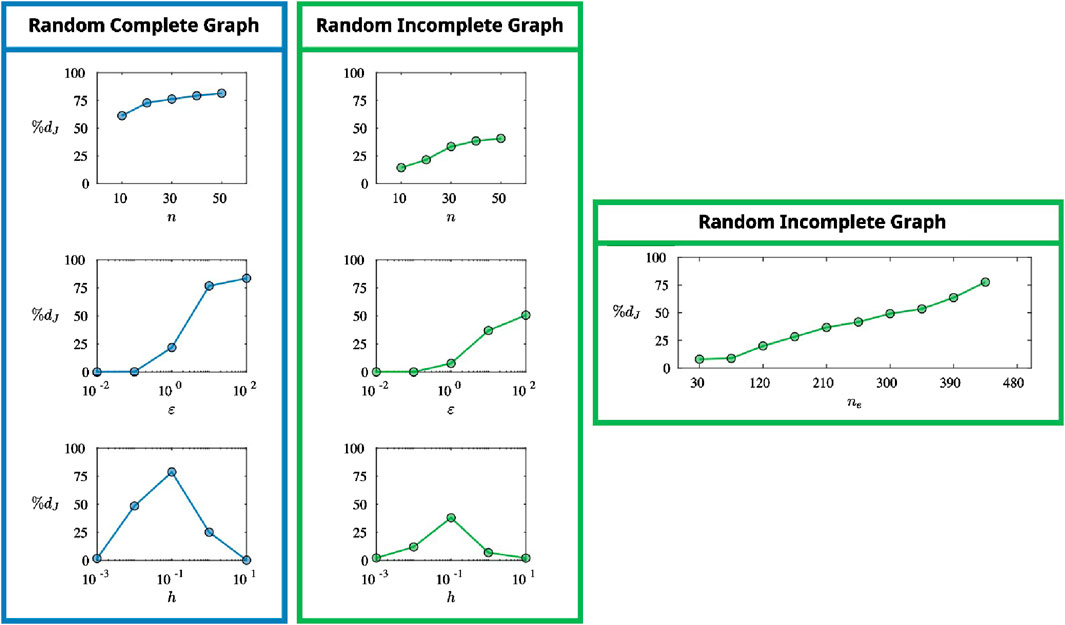
Figure 7. A RCG and a RIG are generated for the problem instances specified by each set of parameters (only a RIG is generated for the case where the variable parameter is the number of edges). The optimization problem is solved for each instance, and the percentage decrease in objective values are plotted against the varying parameter.
It can be observed from Figure 7 that a larger decrease in the objective value can be achieved as the number of vertices or the number of edges increase. Intuitively, more vertices and more edges correspond to more flexibility in distributing the weight resources, thus resulting in larger improvements to the vulnerability of the graph. As expected, larger stiffness yields better results, where the effect gets more significant with increased orders of magnitude. The spread of the external agent’s frequency distribution has a non-monotonic effect. As the spread gets smaller, the agent is able to pick the resonance frequencies more accurately, leaving the graph helpless against the attack, whereas a larger frequency spread corresponds to an agent that almost arbitrarily picks its frequencies, against which any modification of the graph based on reasoning would be less effective. Since the minimum weight constraint and the damping factor did not demonstrate a significant effect on the percentage decrease of the objective, corresponding plots are excluded. By observing the plots overall and the analysis on the number of edges, it is clear that the spectrum optimization on a main network graph is more effective when the graph is complete. This behavior will become more apparent in the next section.
6.2.3 Demonstration of the effectiveness of network graph optimization
To demonstrate the overall effectiveness of spectrum optimization on the main network graph in reducing the network vulnerability, we solve the optimization problem for RCGs, RIGs and Social graphs, and show that significant decrease in objective values can be achieved. We generate 100 RCGs and RIGs with
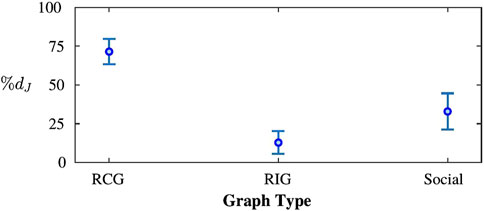
Figure 8. The network graph spectrum optimization problem is solved for instances featuring 100 RCGs, 100 RIGs and 100 social network graphs. On problems instances where the main network graphs are complete, the optimization consistently yielded larger relative decrease in the objective values.
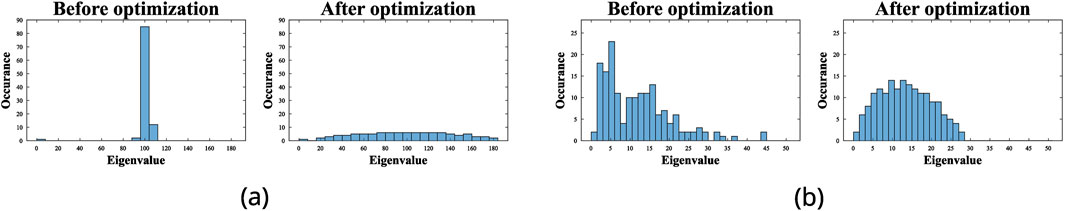
Figure 9. Left (a): Example of eigenvalue spectrum of a complete graph before and after optimization represented as histograms of the eigenvalues of the networks stiffness matrix,
As mentioned before, network graph spectrum optimization is more successful at reducing the objective value relative to the initial value of the objective when it is performed on complete graphs. A reason for this behavior is the greater vulnerability of the complete graphs to the resonance attacks, due to the fact that the natural frequencies of a complete graph are heavily accumulated around a value resulting in a peaky spectrum, compared to a relatively flatter/uniform distribution of the natural frequencies on an incomplete graph. A fewer number of optimization variables impose greater rigidity on incomplete graphs due to their fewer edges, whereas complete graphs, with their maximum possible number of edges, offer a greater flexibility in edge weight manipulations. Qualitatively, this is manifested by a lower relative flattening of the spectrum in case of the incomplete Social graph (Figure 9B) as compared to the complete graph (Figure 9A).
6.2.4 Numerical second-order dynamics simulation of the main network
We considered an unoptimized complete graph with uniform edge weights with an added perturbation as detailed in Section 6.1, as well as the corresponding optimized graph obtained using the network graph optimization method detailed in Section 4, and performed 100 numerical simulations (via numerical integration) of the second-order dynamics on each of these graphs with varying forcing vectors and sampled forcing frequencies. The simulations were run until a steady state was achieved. The squared amplitude of
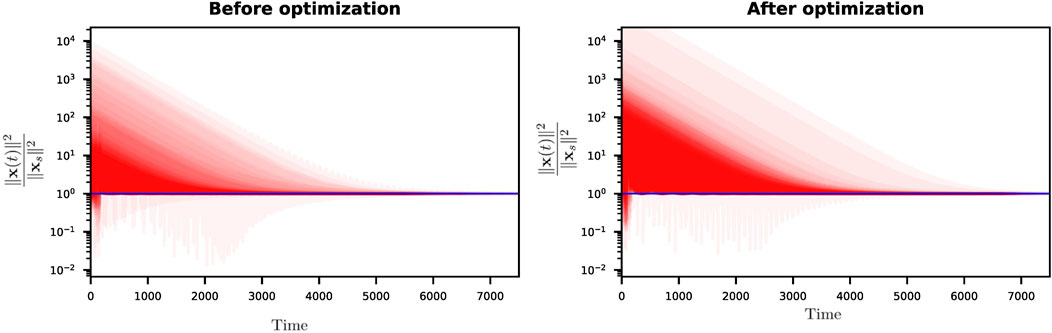
Figure 10. Normalized amplitude plot of 100 different numerical simulations of the second-order dynamics for both the initial and optimized complete graph, displaying their corresponding two-norm squared amplitude values divided by the steady-state squared amplitude value calculated by the closed-form evaluation for the respective forcing vector and forcing frequency (i.e.,
6.2.5 Network Vulnerability Reduction in a Mobile Robot Network
We consider a team of
Considering the weights to be functions of robot positions,
We consider three types of initial configurations for the robots: arbitrary placement within some bounding box, on a uniform grid, on a line. We generate 10 instances for each initial condition where some small random perturbation is applied to the robot locations. Following parameters are used for the experiments:
The mean and the standard deviation of the objective reduction achieved from each type of initial configuration is reported in the table in Figure 11. The initial and optimal robot locations for a problem instance with 64 robots is provided in Figure 11. Our observation suggests that optimization of the network vulnarability results in a reorganization of the robots in an approximate multi-layer formation.
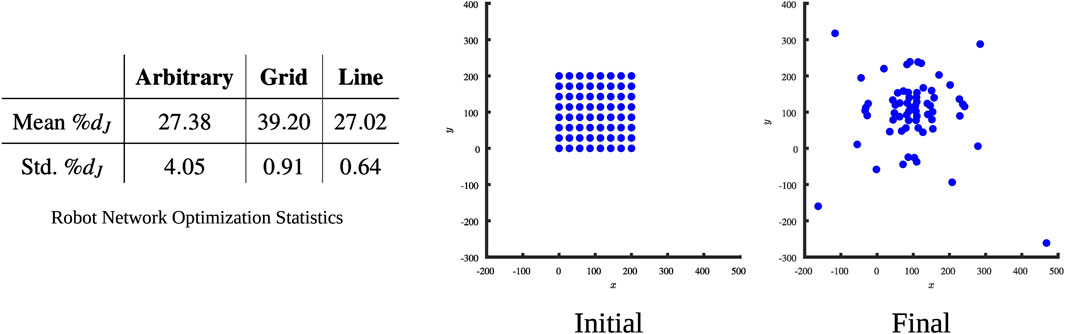
Figure 11. Vulnerability reduction in a mobile robot network. Left: Mean and the standard deviation of the objective reduction achieved. Right: an example initial and final (after network vulnerability minimization) arrangement of a group of 64 robots.
6.3 Auxiliary graph optimization
For the Auxiliary Graph Optimization approach, we conduct similar experiments and provide additional analysis on the effects of auxiliary damping.
6.3.1 Validation of the objective function
The objective function
To validate the accuracy of the objective function in representing the expected value, we generate 800M adversarial forcing samples, evaluate the closed-form steady state responses for each sample using Equation 8 and compute the average squared 2-norm of the responses. For the validation study, we generate a RCG with
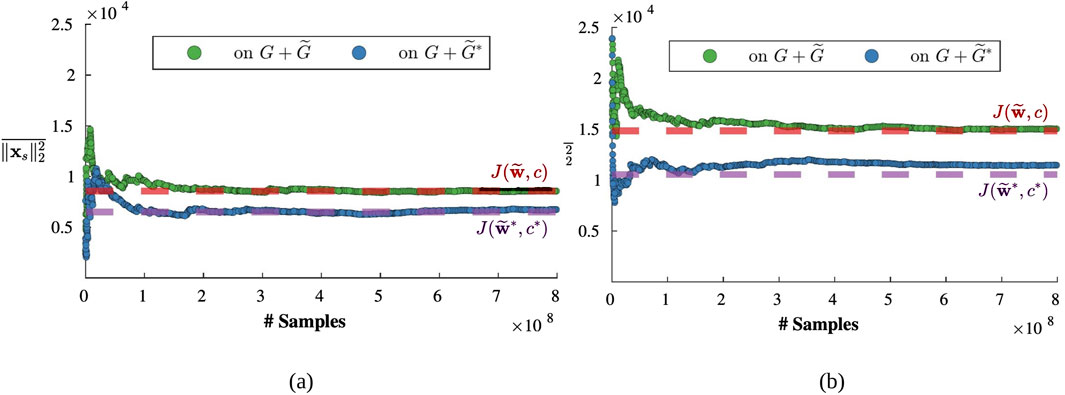
Figure 12. Squared 2-norm of the steady state response corresponding to the main graph
The problem instance generated for the validation study resulted in an optimized auxiliary graph for which
From Figures 12A, B, it can be observed that over a large number of forcing samples, the average of the squared 2-norm of the steady-state responses is well approximated by the objective values when
As a sanity check, we leverage the theoretical result provided in Equation 10 and confirm that
Following the validation of the objective function
6.3.2 Parameter analysis
Parameters that specify an spectrum optimization problem on an auxiliary graph is similar to those of network graph optimization. Since the auxiliary graph edges and inter-graph edges are assumed to have non-negative weights, we do not consider the minimum weight constraint
We analyze the effects of these parameters on the percentage reduction of objective value that can be achieved via the auxiliary graph optimization, hence the relative decrease in the vulnerability of the graph using the Auxiliary Graph Optimization method. We start with the same set of parameter values with the addition of
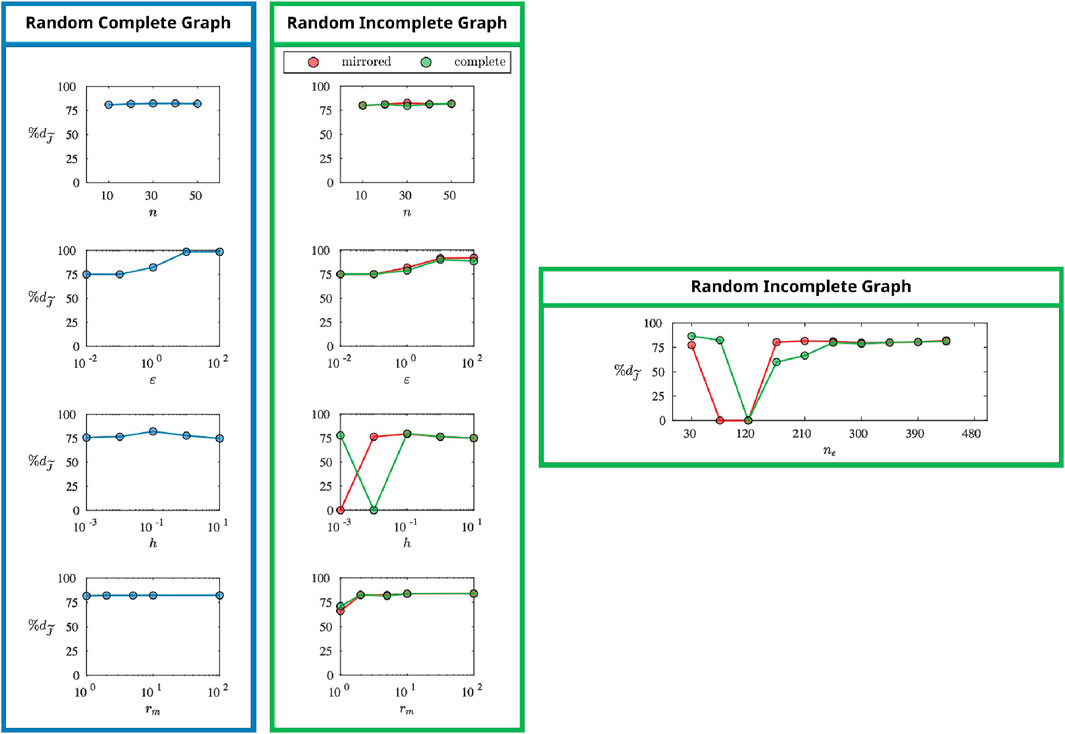
Figure 13. A RCG and a RIG is generated for the problems specified by each set of parameters (only a RIG is generated for variable
Here we highlight that the percentage reduction of the objective value is computed based on the value of the objective before the auxiliary graph is attached, that is
For all parameters, effects are similar to those on the network graph optimization. However, even for the parameter values for which the network graph optimization was less effective, the Auxiliary Graph Optimization method can achieve larger decreases in the objective, which makes the approach less sensitive to the choice of the parameters. The same insensitivity is observed to the weight resource multiplier parameter. For the instances where the network graph was incomplete, some of the optimizations of the mirrored auxiliary graph failed to converge in the maximum number of iterations considered, which is indicated by a
6.3.3 Demonstration of the effectiveness of auxiliary graph optimization
To demonstrate the overall effectiveness of spectrum optimization on the auxiliary graph in reducing the network vulnerability, we solve the optimization problem for RCGs and RIGs and show that significant decrease in objective values can be achieved. We use the same problem instances generated for the network graph optimization, with
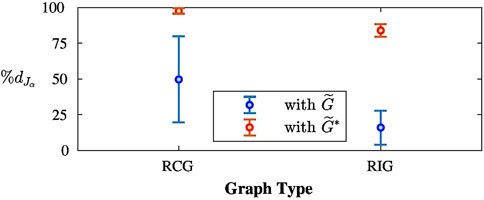
Figure 14. The auxiliary graph spectrum optimization problem is solved for instances featuring 100 RCGs and 100 RIGs. We report the average and standard deviation of the percentage decrease in the objective achieved by both going from the network configuration
It can be seen that attaching even an arbitrary auxiliary graph decreases the vulnerability of the network significantly. However, performing the optimization over the auxiliary edge weights and inter-graph edges results in a further decrease of the vulnerability and provides more consistent behavior.
6.3.4 Effect of the auxiliary damping and auxiliary damping optimization
Assuming that the auxiliary graph weights and the inter-graph edge weights are constant, the auxiliary objective function
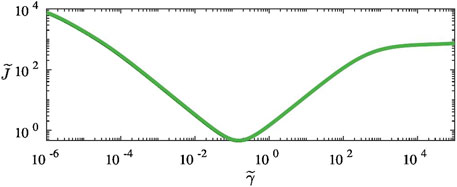
Figure 15. Value of the auxiliary objective function
We observe that the objective function
7 Conclusion and discussions
In this paper, we developed the notion of vulnerability of a network with second order signal dynamics under adversarial forcing that obeys a known stochastic model. To minimize the network vulnerability, we proposed two methods that optimize the network structure: i. The Network Graph Optimization method provides an optimal set of network edge weights under the condition that the edge weights can be directly manipulated, and, ii. The Auxiliary Graph Optimization method allows us to design an auxiliary network that can be attached to the main network with the purpose of minimizing the vulnerability, when the main network edge weights cannot be adjusted directly. We conducted numerical experiments to analyze the two methods in detail.
Currently, the notion of vulnerability and the optimization problems posed in this work depend on a linear model of the signal dynamics and a specific stochastic model of adversarial forcing. While the adaptation of some aspects of the model to other setting (e.g., a different stochastic model of adversarial forcing) can be straight-forward re-derivation of the objective functions, a more general formulation that encompasses more complicated signal models, forcing models, and potentially nonlinear signal dynamics, is within the scope of future work. The optimization formulations presented in this paper lead to generally non-convex problems which are in turn solved by gradient based solvers. While we do show convexity (Proposition 2) of the objective function of the Network Graph Optimization problem under the assumption that the parameter
The current optimization problem is formulated as a centralized one that assumes complete knowledge of the network graph edge weights. This limits the scalability of the optimization problem to larger networks. A potential future work involves the development of a distributed optimization scheme in which each vertex would use information about its local subgraph and would only adjusts weights on its incident edges in order to optimize the network. A distributed method would allow the approach to scale to larger networks and generalize to settings where global information regarding the network may not be available due to privacy restrictions. In future we will work towards implementing the proposed methods on real-world, physical networks such as electrical grids, robot networks and social networks.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
AS: Data curation, Software, Visualization, Writing – original draft, Writing – review and editing, Formal Analysis, Validation. NK: Data curation, Software, Writing – original draft, Writing – review and editing. RB: Conceptualization, Investigation, Supervision, Writing – original draft, Writing – review and editing. SB: Conceptualization, Formal Analysis, Investigation, Methodology, Project administration, Software, Supervision, Writing – original draft, Writing – review and editing.
Funding
The author(s) declare that financial support was received for the research and/or publication of this article. This work was supported by AFOSR award number FA9550-23-1-0046.
Acknowledgments
We gratefully acknowledge the support of AFOSR award number FA9550-23-1-0046. We would like to thank Brian M. Sadler, Senior Research Fellow, University of Texas at Austin, for his valuable insights and discussions on the motivation and potential applications of this work during the course of writing this paper.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Generative AI statement
The author(s) declare that no Generative AI was used in the creation of this manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Aly, A. M. (2014). Proposed robust tuned mass damper for response mitigation in buildings exposed to multidirectional wind. Struct. Des. Tall Special Build. 23, 664–691. doi:10.1002/tal.1068
Bhattacharya, S. (2025). Trace of multi-variable matrix functions and its application to function of graph spectrum. arXiv e-prints. arXiv:2501.14515. doi:10.48550/arXiv.2501.14515
Chan, H., and Akoglu, L. (2016). Optimizing network robustness by edge rewiring: a general framework. Data Min. Knowl. Discov. 30, 1395–1425. doi:10.1007/s10618-015-0447-5
Chen, Y., Ye, H., Vedula, S., Bronstein, A., Dreslinski, R., Mudge, T., et al. (2023). Demystifying graph sparsification algorithms in graph properties preservation. Proc. VLDB Endow. 17, 427–440. doi:10.14778/3632093.3632106
Cheng, X., Kawano, Y., and Scherpen, J. M. A. (2017). Reduction of second-order network systems with structure preservation. IEEE Trans. Automatic Control 62, 5026–5038. doi:10.1109/TAC.2017.2679479
Chow, J., and Kokotovic, P. (1985). Time scale modeling of sparse dynamic networks. IEEE Trans. Automatic Control 30, 714–722. doi:10.1109/TAC.1985.1104055
De Gennaro, M. C., and Jadbabaie, A. (2006). “Decentralized control of connectivity for multi-agent systems,” in Proceedings of the 45th IEEE conference on decision and control, 3628–3633. doi:10.1109/CDC.2006.377041
Deheuvels, P. (1983). Strong bounds for multidimensional spacings. Z. für Wahrscheinlichkeitstheorie Verwandte Geb. 64, 411–424. doi:10.1007/BF00534948
Dorfler, F., Simpson-Porco, J. W., and Bullo, F. (2018). Electrical networks and algebraic graph theory: models, properties, and applications. Proc. IEEE 106, 977–1005. doi:10.1109/JPROC.2018.2821924
Freitas, S., Yang, D., Kumar, S., Tong, H., and Chau, D. H. (2022). Graph vulnerability and robustness: a survey. IEEE Trans. Knowl. Data Eng. 35, 1–5934. doi:10.1109/TKDE.2022.3163672
Godsil, C., Royle, C., and Royle, G. (2001). “Algebraic graph theory,” in Graduate texts in mathematics (Springer).
Griparic, K., Polic, M., Krizmancic, M., and Bogdan, S. (2022). Consensus-based distributed connectivity control in multi-agent systems. IEEE Trans. Netw. Sci. Eng. 9, 1264–1281. doi:10.1109/TNSE.2021.3139045
Hashemi, M., Gong, S., Ni, J., Fan, W., Prakash, B. A., and Jin, W. (2024). A comprehensive survey on graph reduction: sparsification, coarsening, and condensation. Proc. Thirty-ThirdInternational Jt. Conf. Artif. Intell., 8058–8066. doi:10.24963/ijcai.2024/891
Mirzaev, I., and Gunawardena, J. (2013). Laplacian dynamics on general graphs. Bull. Math. Biol. 75, 2118–2149. doi:10.1007/s11538-013-9884-8
Mox, D., Kumar, V., and Ribeiro, A. (2022). Learning connectivity-maximizing network configurations. IEEE Robotics Automation Lett. 7, 5552–5559. doi:10.1109/LRA.2022.3146524
Muller, M. E. (1959). A note on a method for generating points uniformly on n-dimensional spheres. Commun. ACM 2, 19–20. doi:10.1145/377939.377946
Nagpal, S. V., Nair, G. G., Parise, F., and Anderson, C. L. (2023). Designing robust networks of coupled phase oscillators with applications to the high voltage electric grid. IEEE Trans. Control Netw. Syst. 10, 1046–1057. doi:10.1109/tcns.2022.3214778
Olfati-Saber, R. (2006). Flocking for multi-agent dynamic systems: algorithms and theory. IEEE Trans. Automatic Control 51, 401–420. doi:10.1109/TAC.2005.864190
Olfati-Saber, R., and Murray, R. (2004). Consensus problems in networks of agents with switching topology and time-delays. IEEE Trans. Automatic Control 49, 1520–1533. doi:10.1109/TAC.2004.834113
Pan, L., Shao, H., and Mesbahi, M. (2016). “Laplacian dynamics on signed networks,” in 2016 IEEE 55th conference on decision and control (CDC), 891–896. doi:10.1109/CDC.2016.7798380
Ren, W., Beard, R., and Atkins, E. (2005). A survey of consensus problems in multi-agent coordination. Proc. 2005, Am. Control Conf. 2005, 1859–1864. doi:10.1109/ACC.2005.1470239
Riley, K. F., Hobson, M. P., and Bence, S. J. (2006). Mathematical methods for physics and engineering: a comprehensive guide. Cambridge University Press.
Romeres, D., Dã¶rfler, F., and Bullo, F. (2013). “Novel results on slow coherency in consensus and power networks,” in 2013 European control conference (ECC), 742–747. doi:10.23919/ECC.2013.6669400
Rozemberczki, B., Davies, R., Sarkar, R., and Sutton, C. (2019). “Gemsec: graph embedding with self clustering,” in Proceedings of the 2019 IEEE/ACM international Conference on Advances in social networks Analysis and mining 2019 (ACM), 65–72.
Saif, M., Javad-Kalbasi, M., and Valaee, S. (2024). Effectiveness of reconfigurable intelligent surfaces to enhance connectivity in uav networks. IEEE Trans. Wirel. Commun. 23, 18757–18773. doi:10.1109/TWC.2024.3476422
Sheng, L., Lou, G., Gu, W., Lu, S., Ding, S., and Ye, Z. (2022). Optimal communication network design of microgrids considering cyber-attacks and time-delays. IEEE Trans. Smart Grid 13, 3774–3785. doi:10.1109/TSG.2022.3169343
Spielman, D. A., and Srivastava, N. (2008). “Graph sparsification by effective resistances,” in Proceedings of the fortieth annual ACM symposium on theory of computing (New York, NY, USA: Association for Computing Machinery), STOC ’08), 563â€, 568. doi:10.1145/1374376.1374456
Sukharev, A. (1971). Optimal strategies of the search for an extremum. USSR Comput. Math. Math. Phys. 11, 119–137. doi:10.1016/0041-5553(71)90008-5
Sun, C., Dai, R., and Mesbahi, M. (2018). Weighted network design with cardinality constraints via alternating direction method of multipliers. IEEE Trans. Control Netw. Syst. 5, 2073–2084. doi:10.1109/tcns.2018.2789726
The MathWorks (2023). Optimization toolbox user’s guide. r2023b edn. Natick, MA, USA: The MathWorks, Inc.
van der Schaft, A. J., and Maschke, B. M. (2013). Port-Hamiltonian systems on graphs. SIAM J. Control Optim. 51, 906–937. doi:10.1137/110840091
Zhang, L., Sadler, B. M., Blum, R. S., and Bhattacharya, S. (2021). Inter-cluster transmission control using graph modal barriers. IEEE Trans. Signal Inf. Process. over Netw. 7, 275–293. doi:10.1109/TSIPN.2021.3071219
Appendix
7.1 Proof of lemma one
Statement of the Lemma If
where
Proof. Suppose
Because of rotational symmetry of the distribution of
where
However, we note that because of the spherical symmetry of the distribution of
Hence from (Equation 12) we have,
7.2 Approximate root computation using linearization
Consider a polynomial in the variable
If
Evaluating the above at
This gives first order approximations for
Keywords: second-order signal dynamics on graphs, graph signal control, graph optimization, network vulnerability reduction, algebraic graph theory 1
Citation: Sahin A, Kozachuk N, Blum RS and Bhattacharya S (2025) Spectrum optimization of dynamic networks for reduction of vulnerability against adversarial resonance attacks. Front. Complex Syst. 3:1575210. doi: 10.3389/fcpxs.2025.1575210
Received: 13 February 2025; Accepted: 07 May 2025;
Published: 30 May 2025.
Edited by:
Sergi Lozano, University of Barcelona, SpainReviewed by:
Huan Li, Hainan University, ChinaBibhas Adhikari, Fujitsu Research of America, Inc., United States
Copyright © 2025 Sahin, Kozachuk, Blum and Bhattacharya. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Subhrajit Bhattacharya, c3ViMjE2QGxlaGlnaC5lZHU=
 Alp Sahin
Alp Sahin Nicolas Kozachuk
Nicolas Kozachuk Rick S. Blum
Rick S. Blum Subhrajit Bhattacharya
Subhrajit Bhattacharya