- 1Independent Researcher, San José, Costa Rica
- 2ARC Centre of Excellence for Coral Reef Studies, James Cook University, Townsville, QLD, Australia
- 3School of Earth and Environmental Sciences, The University of Queensland, Brisbane, QLD, Australia
- 4Australian Commonwealth Scientific and Industrial Research Organization, Hobart, TAS, Australia
Non-compliers typically avoid detection by authorities, benefiting from increased catch and income. While detection-avoidance strategies (e.g., secret compartments to hide illegal catch) are commonly used in the nature conservation context, they remain largely unstudied. We address this knowledge gap in three sections. First, we introduce and hypothesize the likelihood of non-compliers adopting detection-avoidance strategies in the broader conservation context. Second, we identify and categorize detection-avoidance strategies used by small-scale fishers. Third, we provide recommendations for countering detection-avoidance strategies (i.e., countermeasures). Because countermeasures are context-specific, they should be informed through systematic processes such as the intelligence cycle. If used properly, enforcement activities and countermeasures can help build voluntary compliance, particularly through procedural justice, or acting in a way that users perceive as fair and just.
Introduction
More than 90% of the world’s fisheries have been driven to, or beyond, their sustainable limits (FAO, 2018), threatening ecosystems, livelihoods, and food security. Fishers can mask signals of exploitation by fishing harder (Cinner, 2011), fishing new grounds (Morato et al., 2006; Roberts, 2010) and fishing illegally (Peterson and Stead, 2011; Brashares et al., 2014). While the solutions to overexploitation and non-compliance are complex and require context-specific interventions (Arias et al., 2015; Petrossian, 2015), most approaches need compliance management.
Multiple factors influence compliance, such as livelihoods, norms, and decision-making (Milner-Gulland and Rowcliffe, 2007; Peterson and Stead, 2011; Arias, 2015; Bergseth and Roscher, 2018). Therefore, bolstering voluntary compliance, which we define here as people complying as an act of approval with norms and institutions, should be more successful than when compliance is only coerced. Enforcement, however, is necessary for managing people who knowingly or repeatedly break rules. Enforcement demonstrates that non-compliance is punishable and discourages further non-compliance while signaling administrative competence.
Enforcement, often simplistically and mistakenly equated to patrols, is best described as a chain of four components: (1) the probability of detection, (2) the probability of arrest/citation given detection, (3) the probability of prosecution given arrest/citation, and (4) the probability of conviction given prosecution (Figure 1) (Sutinen, 1987; Akella and Cannon, 2004; Arias et al., 2016). Weakness in any component undermines effectiveness. Here, we focus on the probability of detection, and the techniques that small-scale fishers use to avoid detection while fishing illegally.
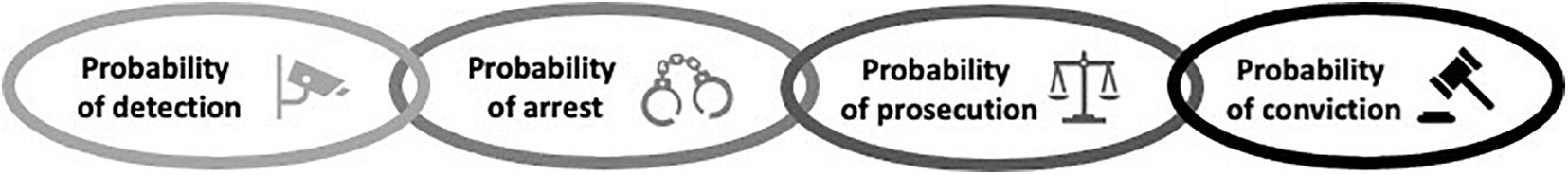
Figure 1. The components of the enforcement chain (see Sutinen, 1987; Akella and Cannon, 2004). Directionality of the chain (left to right) is represented using shading.
The probability of detection has two aspects: perceived and real probabilities. The perceived probability of detection is that which actors believe to occur. This can be estimated through social surveys (King and Sutinen, 2010; Arias and Sutton, 2013; Arias et al., 2015). The real probability of detection is the number of illegal acts detected versus the total number of illegal acts. This is difficult to determine because non-compliance is clandestine. In terrestrial contexts, the real probability of detection is estimated to be below 4% (Eliason, 1999). In fisheries, the real probability of detection is considered to be below 1% (Sutinen et al., 1990; Kuperan and Sutinen, 1998). Detecting illegal fishing is complex as it can involve many rules such quotas, size limits, zoning, and gear regulations. Hence, it is generally easier to estimate the perceived probability of detection than the real probability of detection.
A high perceived probability of detection, even if the real probability is low, can have a strong deterrent effect (Furlong, 1991; Leader-Williams and Milner-Gulland, 1993). Methods to influence fishers’ perceived probability of detection include publicizing enforcement actions such as apprehensions and sanctions, as well as increasing the real probability of detection (Bergseth et al., 2017; Bergseth and Roscher, 2018). However, emphasizing high likelihoods of detection when the real probability of detection is low can be counter-productive if fishers notice that the chance of detection is much lower than that being touted by managers. This would likely decrease trust between fishers and managers, which is a key component of voluntary compliance (Stern, 2008). Therefore, increasing both the perceived and real probabilities of detection are key for deterrence.
The probability of detection can be maximized through patrol planning (Plumptre et al., 2014), because illegal fishing does not occur randomly in space or time (e.g., Bergseth et al., 2017; Weekers and Zahnow, 2019; Weekers et al., 2020). In Costa Rica, at Cocos Island National Park, illegal fishing was spatially clustered over seamounts, around new the moon, and between July and September (Arias et al., 2016). Ensuring that patrols follow identified spatial and temporal patterns should increase the probability of detection and, therefore, the perceived risk amongst fishers.
Fishers, however, can also employ counter-surveillance strategies that reduce the probability of being detected by authorities (hereafter: detection-avoidance strategies). For instance, fishermen can paint their buoys with low contrast colors, and fish at night and when moon light is limited (Arias et al., 2016). Therefore, the effectiveness of patrols, and the probability of detection, depends not only on allocating patrols adequately through space and time, but also on knowing and countering detection-avoidance strategies. Managers can then use intelligence (i.e., the collation, analysis, and dissemination of information) (ICCWC, 2012) to inform risk-based compliance management programs. For instance, if fishers perceive that the risk of being detected is low at first light, managers can conduct early patrols. Regardless of the amount of non-compliance detected during such patrols, the patrol boat’s presence should alter fishers’ future risk calculation as the perceived probability of detection increases. Importantly, such an approach relies on understanding fishers’ actions.
Detection-Avoidance Strategies
Detection-avoidance strategies are common in the nature conservation context, yet they remain largely unstudied. In the illegal wildlife trade, for instance, smugglers conceal or disguise wildlife and wildlife by-products as inconspicuous objects (e.g., ivory worked to look as wood or marble) (Rosen and Smith, 2010). Detection-avoidance is well-documented in large-scale fisheries, where non-compliant vessels can avoid detection by quickly and frequently changing their flags, identities and ownership structures (High Seas Task Force, 2006). By avoiding detection, non-compliers evade costs, such as fines and loss of licenses, therefore maximizing their benefits. The level of sophistication in detection-avoidance strategies is diverse and expected to be proportionate to the perceived probability of detection, and the economic gains realized from evasion; this determines the costs of each strategy.
Detection-avoidance strategies range from high-cost and complex to simple and inexpensive (Vira and Ewing, 2014). For example, an inexpensive strategy could be learning about patrol movements, whereas a costly strategy could be investing in technology. Ultimately, the effectiveness of a detection-avoidance strategy is likely a balance between the investment by authorities in detection and fishers’ investments in avoidance (Sutinen, 1987). The interaction of these two “investments” determines the effectiveness of an authority in its search for violations (Figure 2A). Thus, the profitability of non-compliance, and the related optimal investment in avoidance by fishers, is affected by the probability of detection, and the revenue and cost of non-compliance (Figure 2B). Comparing the expected profit of fishing illegally under the optimal avoidance strategy to the profit from fishing legally allows us to estimate the likely response of fishers to any level of enforcement investment: fish legally, fish illegally but don’t invest in avoidance, or fish illegally and invest in avoidance (Figure 2B). If avoidance is costly, the likelihood of fishers adopting detection-avoidance strategies is expected to decrease (Figure 2A; Anderson, 1989).
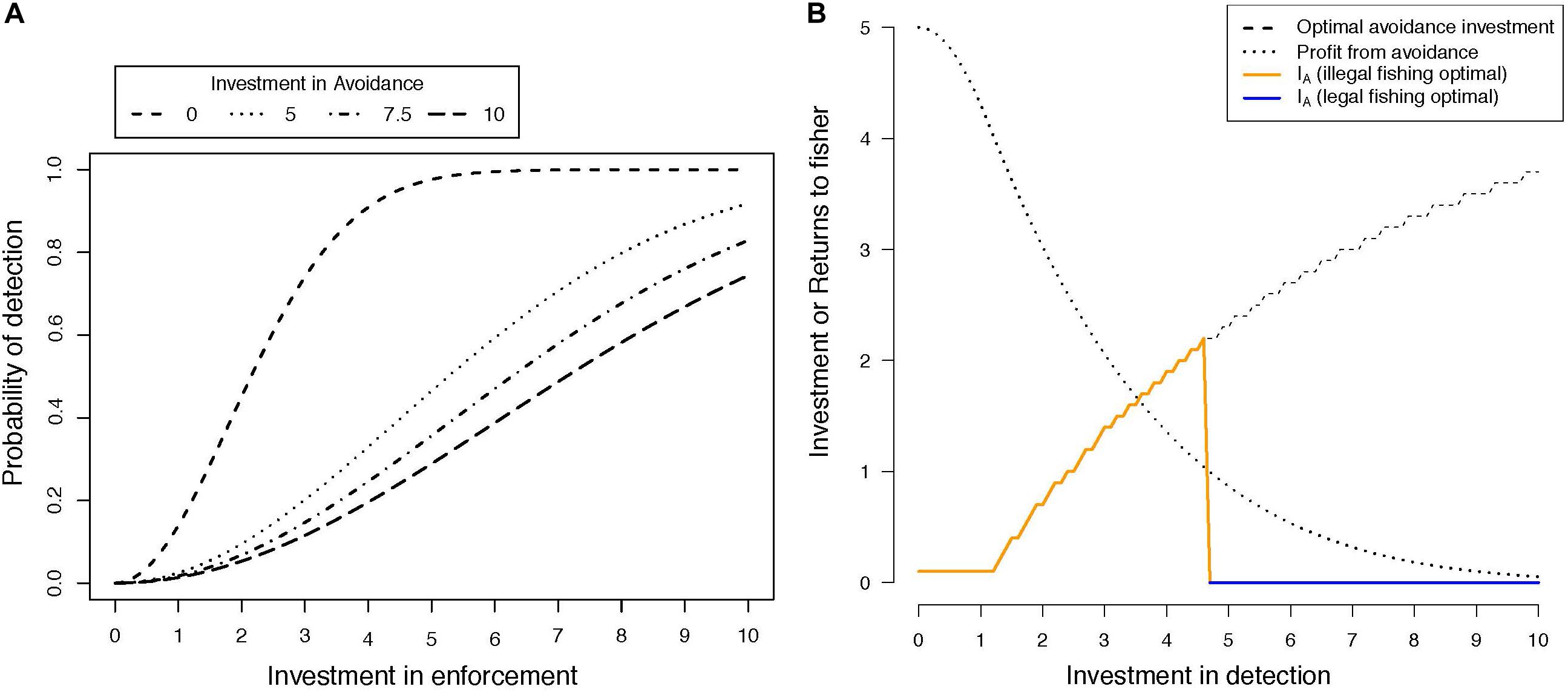
Figure 2. A conceptual model for the interaction between investment in avoidance by fishers, detection by enforcement agencies, and the resulting decision-making by fishers. (A) Shows the relationship between the probability of detecting illegal fishing, conditional on the investment by enforcement agencies in detection and the investment by fishers in avoiding detection. See the Supplementary Material for the underlying functional relationships and justification. (B) Shows the optimal investment in avoidance for a fisher, assuming a revenue of 10 and a cost of 5 for illegally fishing, including both the investment in avoidance as an additional cost and the probability of detection as shown in (A). This investment curve generates a profit curve, based on the difference between revenue, cost, and the cost of investing in avoidance. Assuming an arbitrary legal profit of one, the orange and blue lines show the investment in the avoidance for the profit maximizing strategy across the range of investments in detection by the enforcement agency.
Additional elements can influence the likelihood of fishers adopting detection-avoidance strategies. The cost of avoidance would likely be weighed against the profitability expected from using detection-avoidance strategies: the higher the profits expected from using detection-avoidance strategies, the higher the likelihood of adopting these strategies (Figure 2B). The perceived probability of detection can also affect the likelihood of adopting detection-avoidance strategies, shifting the perceived relationships underlying decision-making by fishers (Figure 2A). Fishers who perceive the detection probability as higher than it is would perceive a lower optimal return from detection-avoidance (Figure 2A), invest less, and would cease fishing illegally at a lower investment by the authorities (Figure 2B). Similarly, if fishers underestimate the probability of detection, they would overinvest in avoidance and continue fishing illegally even as enforcement investment increased.
Overall, the investment in avoidance strategies could increase rapidly from low perceived probabilities of detection, to peak at intermediate to high perceived probabilities of detection, and then diminish due to a shift to legal fishing with a perception of very high probabilities of detection (Figure 2B, orange and blue line). The overall level of illegal fishing would be expected to decrease as the perceived probabilities of detection increase (Figure 2A). Therefore, the likelihood of adopting detection-avoidance strategies could be expected to decrease when: (a) the marginal benefit expected from using the detection–avoidance strategy is low, (b) the cost of adopting the detection–avoidance strategy is high, and (c) the perceived probability of detection is extremely low or extremely high. The trends shown in Figure 2 derive from a simple model of search behavior. However, these are theoretical curves: we do not have data to determine the shapes of the curves, and we are unaware of any empirical examinations of these relationships in the conservation or fisheries literature.
In the following sections we identify some detection-avoidance strategies used by small-scale fishers and offer possible countermeasures that authorities could employ. The detection-avoidance strategies discussed here were revealed in the margins of social surveys in Costa Rica (Arias et al., 2015). The research was approved by the James Cook University Human Research Ethics Committee (Code H4804). The primary aim of these surveys was to examine drivers of compliance, not detection avoidance strategies. Hence, the strategies we uncovered and discuss were not systematically investigated and are not representative of all possible detection avoidance strategies employed by fishers. Accordingly, we are unable to provide quantitative analyses that may further explain the prevalence of these strategies among fishers, and consider the strategies as personal communications provided by the interviewer (AA). Importantly, these detection avoidance strategies address a knowledge gap in compliance management and research. This is not intended as an inclusive list of avoidance strategies but rather as an opportunity to generate information and discussion on a rarely considered topic of importance for conservation practitioners and scholars, and as a call for future systematic research.
Detection-Avoidance Strategies Used in Costa Rican Small-Scale Fisheries
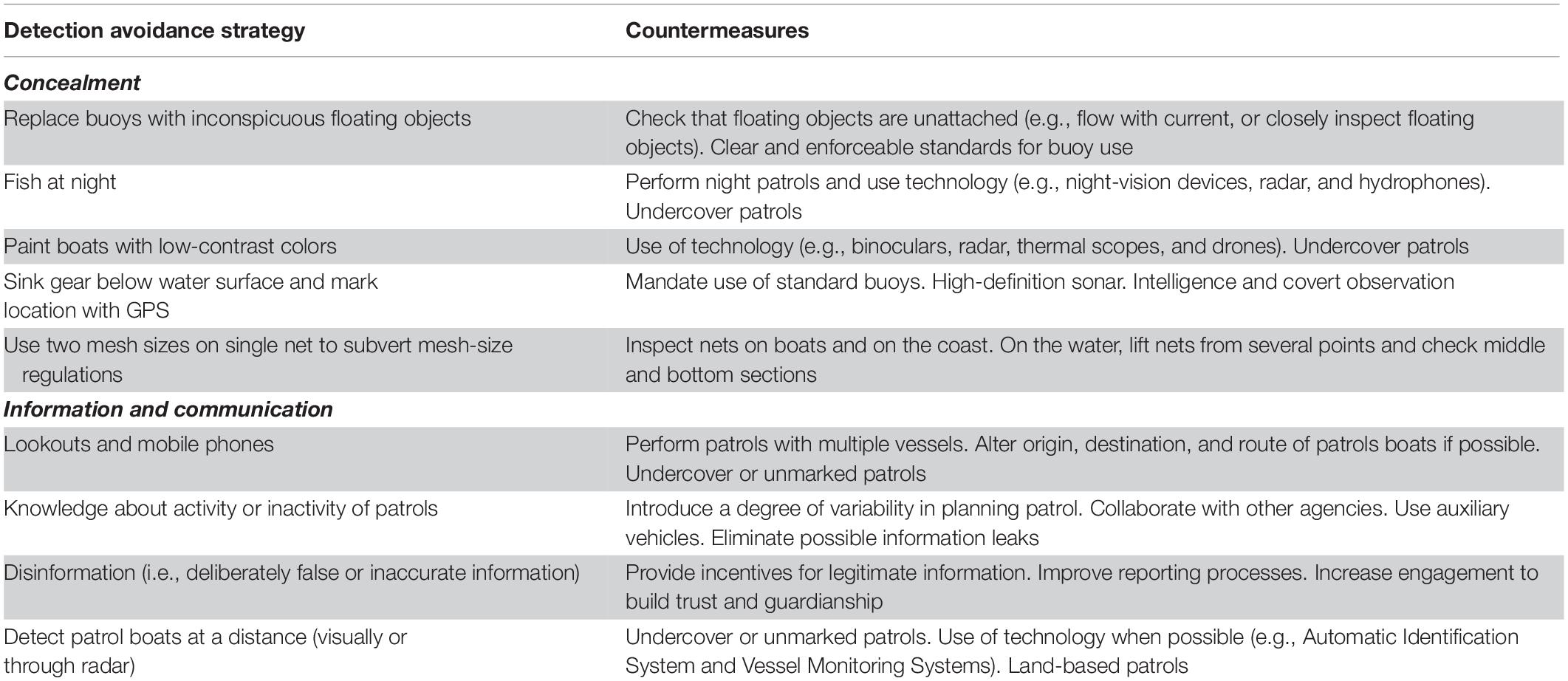
Small-scale fishermen can employ two types of detection-avoidance strategies: concealment, and use of information and communication (Table 1). Concealment strategies are typically aimed at modifying boats or gear so that non-compliance becomes difficult to detect. Information and communication strategies vary in sophistication, from knowing where and when patrols occur, to using lookouts and spreading disinformation to mislead authorities.
Concealment
Concealment strategies aim to hide the presence of fishermen or gear. Fishing at night and painting boats with low-contrast colors hinders visual detection. However, most strategies (Table 1) are directed at concealing illegal gear. For example, if gillnets are permitted, fishermen can use a legal mesh for the upper portion of the net—which is the more likely to be checked by authorities when the net is set—and a smaller, illegal, mesh for a larger and deeper portion of the net. In this case, the gear appears to be a legal set.
In cases where non-compliant fishermen seek to avoid the detection of their entire gear, they can camouflage it by using inconspicuous floating materials as buoys (e.g., coconuts), or by completely immersing and later extracting it using a grapnel. Notably, most of these detection-avoidance strategies involve a cost—an investment of time, resources, and effort. These investments in detection-avoidance strategies imply that the economic gains from non-compliance outweigh their costs (Figure 2B), and that enforcement exists and warrants these strategies (Figure 2B).
Information and Communication
The availability of communication technology enables non-compliant fishermen to share the location of patrol boats and thereby circumvent detection (King et al., 2009). In addition, patrol boats can be distinguished at a distance, allowing non-compliers to cease illegal actions or flee. These strategies have been reported elsewhere; commercial fishermen can detect patrol vessels via radar, and then alert other fishers by radio or telephone (King et al., 2009).
Fishers can also disinform authorities to avoid detection. For instance, Costa Rican fishers misdirected patrols using false reports, with negative repercussions. When the coastguard suspected about the false reports, they began asking for the identity of the informants. Fishers that were reporting authentic offenses became alarmed by a lack of anonymity, which can reduce or eliminate willingness to report, particularly if retaliation may occur (Mesmer-Magnus and Viswesvaran, 2005). Indeed, some respondents stated that they often chose not to report illegal fishing either to avoid potential confrontations with other fishers, or because of perceived inaction or ineptitude of the authorities (AA, personal communication). The latter scenario signifies a lack of confidence in authorities, which can erode people’s sense of cooperation. Thus, a simple and virtually cost-free strategy of disinformation likely escalated into an intricate problem, further emphasizing the need for an adaptive approach from managers.
Countermeasures to Detection-Avoidance Strategies
Countermeasures can prevent or neutralize detection-avoidance strategies by increasing the probability of detection, the effort required to avoid detection, and the costs associated with non-compliance (Sutinen, 1987; Table 1). Some countermeasures can address a particular detection-avoidance strategy (e.g., mandating standard buoys), while others can address multiple strategies (Table 1). For instance, land-based patrols can help counter concealment (e.g., illegal nets), and information and communication strategies (e.g., detection of patrol boats at a distance; Table 1). Additionally, enforcement can be further strengthened through adequate legislation (Arias, 2015).
Explicitly regulating fishing reduces legal loopholes. For instance, if the legislation does not describe the buoys that must be used to mark fishing gear, the use of a coconut as a buoy (Table 1) would be legal and authorities would not be able to act against it. In Queensland, Australia, crab traps must be tagged with the owner’s surname and address, and must have a “light colored surface float” of “no less than 15 cm in any dimension” (DAF, 2015). This limits what can be used as buoys and increases the probability of identifying non-compliers, enabling enforcement actions. Legislation must give authorities the powers to fully address non-compliance—clear and enforceable rules are key for tackling illegal fishing and ensuring that the enforcement chain is not undermined by loopholes (Arias, 2016).
Countering Detection-Avoidance in the Field
There are multiple ways of countering detection-avoidance strategies in the field, namely through technological tools, and field procedures. Overall, technological advancements are reshaping enforcement, and their costs are decreasing (Vira and Ewing, 2014). For example, using drones for surveillance and monitoring is an underutilized, but emerging area of interest for fisheries enforcement (Orlowski, 2020), given their ability to provide regular surveillance presence (e.g., sUAS News, 2019). If publicized, surveillance technologies can increase both the actual and perceived likelihoods of detection (Bergseth et al., 2017). Nevertheless, the availability of some of these technologies also implies that non-compliers can use it. The use of GPS devices to mark sunken fishing gear (Table 1) exemplifies this. In extreme examples, such as rhino and elephant poaching in Africa, poachers use night-vision, silenced weapons, and even helicopters (Vira and Ewing, 2014). Authorities need to adapt their field procedures and technologies to stay abreast of those made by non-compliers.
Field procedures can also influence both the perceived probability of detection and fishers’ perceptions of legitimacy via procedural justice. Procedural justice is the product of how authorities treat those being regulated, and the quality of the decisions made by the authorities (Tyler, 2003). People who are treated justly are more likely to recognize the legitimacy of the authorities (Mazerolle et al., 2013), and are therefore more likely to comply. Procedural justice and legitimacy are particularly relevant in the context of the disinformation strategy discussed earlier and how it might have eroded cooperation. Reporting and response systems that are procedurally just can provide benefits, including increased cooperation and trust between fishers and management authorities (Bergseth et al., 2018). Technology can facilitate this cooperation and increase cost-effectiveness; in this case it could be through communication tools such as social media and mobile applications. Institutions should allow closer relationships with the public (ICCWC, 2012), but these steps must be well-planned to avoid counterproductive actions (Arias, 2015).
Countering Detection-Avoidance Using an Intelligence-Led Approach
Intelligence-led policing is a central feature of contemporary enforcement and can be defined as the incorporation of information collection and analysis (intelligence) into the decision-making process to maximize compliance (Ratcliffe, 2016). Intelligence-driven patrol planning can be a cost neutral way of enhancing the effectiveness of compliance resources (Leader-Williams et al., 1990; Hilborn et al., 2006; Moore et al., 2018). In Australia, compliance management in the Great Barrier Reef Marine Park uses a risk-based and intelligence-led framework (Weekers and Zahnow, 2019; Weekers et al., 2020). For example, to determine operational priorities, managers firstly consider the risk (likelihood and consequence) of activities such as illegal fishing. Intelligence is then used to identify patterns and targets to ensure that resources are allocated in space and time (Weekers et al., 2020). Regulations that require catch and sales documentation, can provide additional information to support intelligence analysis.
The application of an intelligence-led approach to managing fishery compliance is supported by a conceptual model known as the “intelligence cycle” (Garner and McGlynn, 2018). The cycle represents an adaptive management process focused at decision points of: direction, information collection, data storage, information analysis (intelligence), intelligence reporting, and dissemination (Garner and McGlynn, 2018). The use of adaptive management techniques through conceptual modeling is familiar to natural resource managers, and the intelligence cycle is well-designed to address non-compliance and counter detection-avoidance strategies.
Conclusion
The success of compliance management is partly determined by enforcement. Effective enforcement in turn must successfully counter detection-avoidance strategies. The likelihood of fishers using detection-avoidance strategies is expected to depend on the costs of adopting them, the benefits expected from their use, and the perceived probability of detection. The latter, however, is typically the easiest for managers to influence. We proposed a series of tools and processes that managers can use to counter detection-avoidance strategies and ultimately increase the perceived probability of detection. A key consideration is the efficiency of these detection innovations: those that shift detection probabilities the most per implementation cost are likely to have the greatest effect. An important component is improving information management, which can be achieved by using frameworks for intelligence-led planning and practices. In addition, enforcement will benefit if bolstered by actions that aim to increase both voluntary compliance and cooperation with the authorities. In this regard, processes that promote procedural justice are often successful in increasing the perceived legitimacy of authorities, normally resulting in higher voluntary compliance and cooperation.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author/s.
Author Contributions
AA conceived and led the project, including data collection, and contribution to the analysis. BB contributed to the analysis and writing of the manuscript. DW contributed to the writing of the manuscript. CW led the analysis and contributed to the writing of the manuscript. All authors contributed to the article and approved the submitted version.
Funding
Funding to AA was provided by AusAID, the PADI Foundation, and the ARC Centre of Excellence for Coral Reef Studies.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Acknowledgments
AA thanks the Australian people for their support through AusAID. We would like to thank Robert L. Pressey, Jorge Alvarez-Romero, Joshua E. Cinner, the reviewers, and editor for their useful feedback on this piece.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fmars.2021.619349/full#supplementary-material
References
Akella, A. S., and Cannon, J. B. (2004). Strengthening the weakest links: strategies for improving the enforcement of environmental laws globally. Virginia: Center for Conservation and Government at Conservation International.
Anderson, L. G. (1989). Enforcement Issues in Selecting Fisheries Management Policy. Mar. Resour. Econom. 6, 261–277. doi: 10.1086/mre.6.3.42871974
Arias, A. (2015). Understanding and managing compliance in the nature conservation context. J. Environ. Manage. 153, 134–143. doi: 10.1016/j.jenvman.2015.02.013
Arias, A. (2016). Avoiding and reversing ‘paper parks’: integrating fishers’ compliance into conservation efforts. Ph D. Thesis, Townsville: James Cook University
Arias, A., and Sutton, S. G. (2013). Understanding recreational fishers’ compliance with no-take zones in the Great Barrier Reef Marine Park. Ecol. Soc. 18:18.
Arias, A., Cinner, J., Jones, R. E., and Pressey, R. L. (2015). Levels and drivers of fishers’ compliance with marine protected areas. Ecol. Soc. 20:19.
Arias, A., Pressey, R. L., Jones, R. E., Álvarez-Romero, J., and Cinner, J. E. (2016). Optimizing enforcement and compliance in offshore marine protected areas: A case study from Cocos Island, Costa Rica. Oryx 50, 18–26. doi: 10.1017/s0030605314000337
Bergseth, B. J., and Roscher, M. (2018). Discerning the culture of compliance through recreational fisher’s perceptions of poaching. Mar. Policy 89, 132–141. doi: 10.1016/j.marpol.2017.12.022
Bergseth, B. J., Gurney, G. G., Barnes, M. L., Arias, A., and Cinner, J. E. (2018). Addressing poaching in marine protected areas through voluntary surveillance and enforcement. Nat. Sustainabil. 1, 421–426. doi: 10.1038/s41893-018-0117-x
Bergseth, B. J., Williamson, D. H., Russ, G. R., Sutton, S. G., and Cinner, J. E. (2017). A social–ecological approach to assessing and managing poaching by recreational fishers. Front. Ecol. Environ. 15:67–73. doi: 10.1002/fee.1457
Brashares, J. S., Abrahms, B., Fiorella, K. J., Golden, C. D., Hojnowski, C. E., Marsh, R. A., et al. (2014). Wildlife decline and social conflict. Science 345, 376–378.
Cinner, J. E. (2011). Social-ecological traps in reef fisheries. Glob. Environ. Change 21, 835–839. doi: 10.1016/j.gloenvcha.2011.04.012
Eliason, S. L. (1999). The illegal taking of wildlife: Toward a theoretical understanding of poaching. Hum. Dimens. Wildlife 4, 27–39. doi: 10.1080/10871209909359149
FAO (2018). The State of World Fisheries and Aquaculture 2018 - Meeting the sustainable development goals. Rome: Food and Agriculture Organization of the United Nations.
Furlong, W. J. (1991). The Deterrent Effect of Regulatory Enforcement in the Fishery. Land Econom. 67, 116–129. doi: 10.2307/3146490
High Seas Task Force (2006). Closing the net: Stopping illegal fishing on the high seas. Paris: High Seas Task Force.
Hilborn, R., Arcese, P., Borner, M., Hando, J., Hopcraft, G., Loibooki, M., et al. (2006). Effective enforcement in a conservation area. Science 314, 1266–1266. doi: 10.1126/science.1132780
ICCWC (2012). Wildlife and Forest Crime Analytic Toolkit. Vienna: International Consortium on Combatting Wildlife Crime.
King, D. M., and Sutinen, J. G. (2010). Rational noncompliance and the liquidation of Northeast groundfish resources. Mar. Policy 34, 7–21. doi: 10.1016/j.marpol.2009.04.023
King, D. M., Porter, R. D., and Price, E. W. (2009). Reassessing the Value of U.S. Coast Guard At-Sea Fishery Enforcement. Ocean Dev. Int. Law 40, 350–372. doi: 10.1080/00908320903285414
Kuperan, K., and Sutinen, J. G. (1998). Blue Water Crime: Deterrence, Legitimacy, and Compliance in Fisheries. Law Soc. Rev. 32, 309–338. doi: 10.2307/827765
Leader-Williams, N., Albon, S. D., and Berry, P. S. M. (1990). Illegal exploitation of black rhinoceros and elephant populations: patterns of decline, law enforcement and patrol effort in Luangwa Valley, Zambia. J. Appl. Ecol. 27, 1055–1087. doi: 10.2307/2404395
Leader-Williams, N., and Milner-Gulland, E. J. (1993). Policies for the Enforcement of Wildlife Laws: The Balance between Detection and Penalties in Luangwa Valley, Zambia. Conserv. Biol. 7, 611–617. doi: 10.1046/j.1523-1739.1993.07030611.x
Mazerolle, L., Bennett, S., Davis, J., Sargeant, E., and Manning, M. (2013). Procedural justice and police legitimacy: a systematic review of the research evidence. J. Exp. Criminol. 9, 245–274. doi: 10.1007/s11292-013-9175-2
Mesmer-Magnus, J., and Viswesvaran, C. (2005). Whistleblowing in Organizations: An Examination of Correlates of Whistleblowing Intentions, Actions, and Retaliation. J. Bus. Ethics 62, 277–297. doi: 10.1007/s10551-005-0849-1
Milner-Gulland, E. J., and Rowcliffe, J. M. (2007). Conservation and sustainable use: a handbook of techniques. Oxford: OUP Catalogue.
Moore, J. F., Mulindahabi, F., Masozera, M. K., Nichols, J. D., Hines, J. E., Turikunkiko, E., et al. (2018). Are ranger patrols effective in reducing poaching−related threats within protected areas? J. Appl. Ecol. 55, 99–107. doi: 10.1111/1365-2664.12965
Morato, T., Watson, R., Pitcher, T. J., and Pauly, D. (2006). Fishing down the deep. Fish Fisheries 7, 24–34. doi: 10.1111/j.1467-2979.2006.00205.x
Orlowski, A. (2020). Drones fisheries enforcement potential remains untapped, even as projects advance. Seafood Sour. 2:2020.
Peterson, A. M., and Stead, S. M. (2011). Rule breaking and livelihood options in marine protected areas. Environ. Conserv. 38, 342–352. doi: 10.1017/s0376892911000178
Petrossian, G. A. (2015). Preventing illegal, unreported and unregulated (IUU) fishing: A situational approach. Biol. Conserv. 189, 39–48. doi: 10.1016/j.biocon.2014.09.005
Plumptre, A. J., Fuller, R. A., Rwetsiba, A., Wanyama, F., Kujirakwinja, D., Driciru, M., et al. (2014). Efficiently targeting resources to deter illegal activities in protected areas. J. Appl. Ecol. 51, 714–725. doi: 10.1111/1365-2664.12227
Rosen, G., and Smith, K. (2010). Summarizing the Evidence on the International Trade in Illegal Wildlife. EcoHealth 7, 24–32. doi: 10.1007/s10393-010-0317-y
Stern, M. J. (2008). Coercion, voluntary compliance and protest: the role of trust and legitimacy in combating local opposition to protected areas. Environ. Conserv. 35, 200–210. doi: 10.1017/S037689290800502X
sUAS News (2019). Water-landing drones routinely fly BVLOS missions over marine reserve against illegal fishing and pro-biodiversity. Gloucestershire: sUAS News.
Sutinen, J. G. (1987). Enforcement of the MFCMA: an economist’s perspective. Mar. Fish. Rev. 49, 36–43.
Sutinen, J. G., Rieser, A., and Gauvin, J. R. (1990). Measuring and explaining noncompliance in federally managed fisheries. Ocean Dev. Int. Law 21, 335–372. doi: 10.1080/00908329009545942
Tyler, T. R. (2003). Procedural Justice, Legitimacy, and the Effective Rule of Law. Crime Justice 30, 283–357. doi: 10.1086/652233
Vira, V., and Ewing, T. (2014). Ivory’s curse: the militarization and professionalization of poaching in Africa. Washington, D.C: Born Free USA and C4ADS.
Weekers, D. P., and Zahnow, R. (2019). Risky facilities: Analysis of illegal recreational fishing in the Great Barrier Reef Marine Park, Australia. Austral. NZ. J. Criminol. 52, 368–389. doi: 10.1177/0004865818804021
Keywords: fisheries enforcement, compliance, illegal fishing, illegal fishing techniques, poaching and conservation, intelligence cycle, enforcement chain
Citation: Arias A, Bergseth BJ, Weekers D and Wilcox C (2021) Countering Avoidance Strategies Used by Fishers to Avoid Detection During Illegal Fishing. Front. Mar. Sci. 8:619349. doi: 10.3389/fmars.2021.619349
Received: 20 October 2020; Accepted: 20 January 2021;
Published: 23 February 2021.
Edited by:
Steven W. Purcell, Southern Cross University, AustraliaReviewed by:
Dimitrios K. Moutopoulos, University of Patras, GreeceTommaso Russo, University of Rome Tor Vergata, Italy
Copyright © 2021 Arias, Bergseth, Weekers and Wilcox. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Brock J. Bergseth, YnJvY2suYmVyZ3NldGhAbXkuamN1LmVkdS5hdQ==
†These authors have contributed equally to this work
 Adrian Arias1†
Adrian Arias1† Brock J. Bergseth
Brock J. Bergseth Chris Wilcox
Chris Wilcox