- 1Department of Life Science and Informatics, Graduate School of Engineering, Maebashi Institute of Technology, Maebashi, Gunma, Japan
- 2Department of Life Engineering, Faculty of Engineering, Maebashi Institute of Technology, Maebashi, Gunma, Japan
In urban areas with many commercial facilities, patrolling by police officers or security guards is essential for crime prevention, in addition to the use of surveillance cameras. To address the challenge of planning effective patrol routes, Tohyama and Tomisawa introduced the Police Officer Patrolling Problem (POPP), an arc routing problem that allows for visual monitoring from intersections and is proven to be NP-complete. Building on this work, we propose the Generalized POPP (GPOPP), a more realistic bi-objective combinatorial optimization model. This model simultaneously minimizes the total patrol route length and maximizes the coverage of surveillance areas. The contributions of this paper are threefold: (1) we formulate the GPOPP by incorporating practical constraints, such as mandatory patrolling of high-security roads and visibility-based coverage from intersections; (2) we develop a novel hybrid heuristic method that combines a multi-objective evolutionary algorithm (MoEA-HSS) with an improved Jaya algorithm to solve the GPOPP effectively; and (3) we conduct comprehensive computational experiments using benchmark instances to evaluate the effectiveness and competitiveness of the proposed method. These contributions demonstrate the practicality and efficiency of our approach for addressing realistic urban patrolling problems.
1 Introduction
In the fields of information engineering and science, to solve various social and economic problems, these problems are generally structured as mathematical models, and solutions are found using algorithms that are suited to that structure. Many of these problems are modeled using discrete graphs, and there are many studies on them.
One of the problems modeled by discrete graphs is the routing problem. Routing problems are classified as node routing problems (NRPs), which traverse the nodes of a graph, and arc routing problems (ARPs), which traverse the edges (or arcs). A typical NRP is the traveling salesperson problem (TSP). The TSP is a problem that involves finding the minimum-cost route that visits every vertex exactly once. The vehicle routing problem (VRP) (Dantzig and Ramser, 1959) is a generalization of the TSP. This problem involves planning transportation from a distribution center to multiple customers using trucks or other transportation methods. Both the TSP and VRP are NP-hard; thus, evolutionary algorithms, such as genetic algorithms (GAs), have been studied (Elatar et al., 2023).
The most famous ARP is probably the Euler circuit problem. This problem determines whether there exists a circuit that traverses all edges exactly once for a given graph, and this problem is solvable in polynomial time. The Chinese postman problem (CPP) (Mei-Ko, 1962), which is a generalization of the Euler circuit problem, involves determining whether a tour exists for a post officer in a given area within a given amount of time that starts and ends at the post office. The post officer must traverse every street in the area at least once; however, they may traverse any street several times. The CPP on undirected or directed graphs can be solved in polynomial time (Edmonds and Johnson, 1973). Papadimitriou (1976) showed that the CPP on mixed graphs is NP-complete. Mixed graphs represent realistic situations in urban areas with both two- and one-way streets. The rural postman problem (RPP) is a generalization of the CPP with a given set of edges that must be traversed by a post officer. This problem considers the fact that, in rural areas, not every street has a delivery destination. Lenstra and Rinnooy-Kan (1976) and Lenstra and Rinnooy-Kan (1981) showed that the optimization version of the RPP on undirected or directed graphs is NP-hard. The capacitated ARP (CARP) is an ARP corresponding to the VRP, which belongs to the NRP. The CPP, RPP, and CARP correspond to mathematical models of real social problems such as postal delivery, delivery planning, snow shoveling, and garbage collection. Finding exact solutions for the CPP and RPP optimization problems is intractable, along with the TSP and VRP; thus, various heuristic methods have been proposed for these problems. Recent examples include methods using GAs (Gil-Gala et al., 2023), the Tabu search algorithm (Tang et al., 2024), and ant colony optimization (Sgarro and Grilli, 2024).
Police patrols play a crucial role in preventing crimes and accidents, thereby ensuring public safety within their jurisdictions. Recent studies such as (Kim et al., 2023; Dewinter et al., 2020; Samanta et al., 2022) have proposed methods for optimizing patrol routes. These approaches primarily employ heuristic algorithms to generate efficient patrol routes for multiple officers operating within the shared area.
Recently, Tohyama and Tomisawa (2022) proposed the police officer patrol problem (POPP) as a mathematical model of the patrolling route problem of police officers (or security guards), and showed that the decision problem is NP-complete (Tohyama and Tomisawa, 2022). Patrolling areas generally include one- and two-way streets; thus, the POPP is modeled using a mixed graph. At each intersection, police officers may conduct security checks visually even if they do not traverse the streets connecting to it. If the POPP is considered a CPP model, it is necessary to find a patrolling route that traverses all streets. The POPP model allows some streets to conduct visual security checks without traversing, making it possible to find more efficient patrolling routes. In addition, Tomisawa and Tohyama showed that the POPP on weighted digraphs is NP-complete (Tomisawa and Tohyama, 2024).
In this study, we introduce the generalized POPP (GPOPP) as a model to adapt the POPP to more realistic patrolling routes by police officers. The POPP model requires that all areas be guarded. However, in reality, some streets require security because important facilities are located there, and some roads do not necessarily require security (Chainey et al., 2021). In addition, there are cases where a patrolling route needs to be found that can be patrolled within a given time. Therefore, we define the GPOPP as an optimization problem with the following two objectives. The first objective is to find the shortest patrolling route among the routes that traverse all high-security streets. The second objective is to find a patrolling route that guards as large a given area as possible (maximizes coverage).
Many GAs have been proposed to solve multi-objective problems (Deb et al., 2002; Sardinas et al., 2006; Pizzuti, 2009; Ghoseiri and Ghannadpour, 2010; Aiello et al., 2012; Akyurt et al., 2015; Yu et al., 2015; Lu et al., 2019). The hybrid sampling strategy based multi-objective evolutionary algorithm (MoEA-HSS) (Zhang et al., 2014) is based on a hybrid sampling strategy that combines a vector-valued GA (VEGA) (Schaffer, 2014) and a sampling strategy according to the Pareto dominating and dominated relationship-based fitness function (PDDR-FF) (a goodness-of-fit function based on Pareto dominance–dominance relations). The MoEA-HSS has demonstrated effectiveness for several problems. The Jaya algorithm (Rao, 2016) is a meta-heuristic algorithm with a very simple structure based on the concept that solutions obtained for a particular problem progress toward the best solution and avoid the worst solution. We propose a hybrid heuristic approach that combines the MoEA-HSS with an improved Jaya algorithm, and demonstrate its effectiveness through numerical experiments.
The remainder of this paper is organized as follows. In Section 2, we formally define the Generalized Police Officer Patrolling Problem (GPOPP) and present the necessary graph-theoretical concepts. Section 3 provides a mathematical formulation of the GPOPP as a bi-objective optimization problem. In Section 4, we describe the proposed hybrid heuristic method that combines the MoEA-HSS and an improved Jaya algorithm. Section 5 presents the results of the numerical experiments conducted to evaluate the performance of the proposed method. Finally, Section 6 concludes the paper and discusses potential directions for future research.
2 Generalized police officer patrolling problem (GPOPP)
In this study, we introduce a bi-objective problem that can be applied to more realistic problems based on the POPP, which is NP-complete edge routing decision problem, and propose a heuristic algorithm to solve the problem. One police officer (or security guard or robot) is assigned to a security area, and each officer patrols his/her assigned area. Each street through which a police officer is traversed during a patrol is considered guarded. In addition, except for streets with important facilities, police officers are allowed to visually confirm each street adjacent to an intersection without traversing it. The GPOPP is a bi-objective optimization problem with the following two objectives: One is to find the patrolling route with the shortest length, and the other is to find the route with the largest guarded area. Here, we note that all high-security streets must be traversed. In this section, we define the notion in graph theory necessary to formulate the GPOPP.
Throughout this paper, let
Let
1.
2.
3.
Here,
Let
1. The sequence
2. All edges in
3.
The length
For a patrolling route
Let
Similarly,
An example of a patrolling route for a mixed graph is illustrated in Figure 1. The red edges represent high-security edges, and the blue line indicates a patrolling route. The green area is guarded by this patrolling route. In particular, the green area not on the patrolling route is guarded by visual confirmation. The graph shown in Figure 1 has 60 vertices and 104 edges. Let us assume that the distance between any two vertices is one. Then, the length of the patrolling route is 44. The total sum of the distances of the guarded edges is 84, and the covered and noncovered ratios are 0.808 and 0.192, respectively.
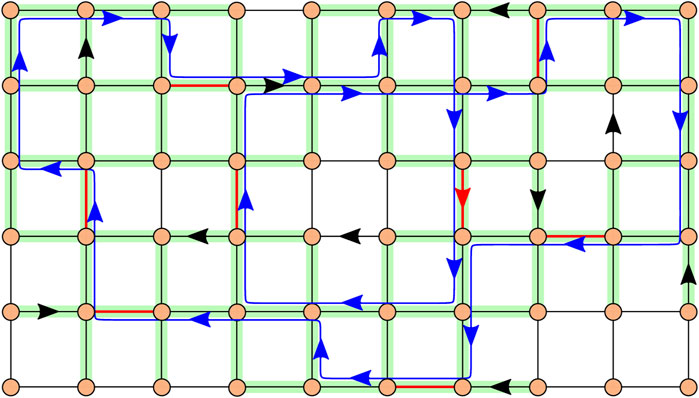
Figure 1. Patrolling route (blue line) on mixed graph. The red edges represent high-security edges, and the green area indicates a guarded area.
Let
3 Formulation
The GPOPP is a bi-objective optimization problem that obtains a patrolling route with the shortest length and the lowest noncovered ratio for a given connected simple mixed graph
(i)
(ii)
If
(iii)
Note that
(iv)
(v)
In other words,
The decision variables for the GPOPP are
(vi)
We remark that
Let
The objective function
The following constraints must be satisfied:
where
Suppose that
The notation used in formulating the mathematical programming model for GPOPP is summarized as follows:
Parameters
Decision variables
Objective functions
4 Proposed methods
4.1 Framework
The GPOPP requires two conflicting objectives to be considered simultaneously: minimizing the total length of the patrolling route and minimizing its noncoverage ratio. Many Pareto-optimal solutions with incomparable qualities must be generated for the decision-maker. In this section, we introduce a hybrid heuristic approach based on the MoEA-HSS and the improved Jaya algorithm for the GPOPP.
The MoEA-HSS is based on a hybrid sampling strategy that combines the VEGA and a sampling strategy according to the PDDR-FF. The sampling strategy of the VEGA is a natural extension of simple GAs in the sense that the individuals are divided and reproduced independently according to each objective function. It prefers the edge region of the Pareto front with less time complexity, and the qualities of the solution are not good because of the selection bias. Conversely, the PDDR-FF-based sampling strategy tends to converge toward the central area of the Pareto front. The combination of these two mechanisms is expected to maintain both the convergence rate and distribution performance. The Jaya algorithm modifies a given individual to move closer to the best solution and away from the worst solution based on the best and worst candidates in the population. The Jaya algorithm is expected to accelerate the convergence rate.
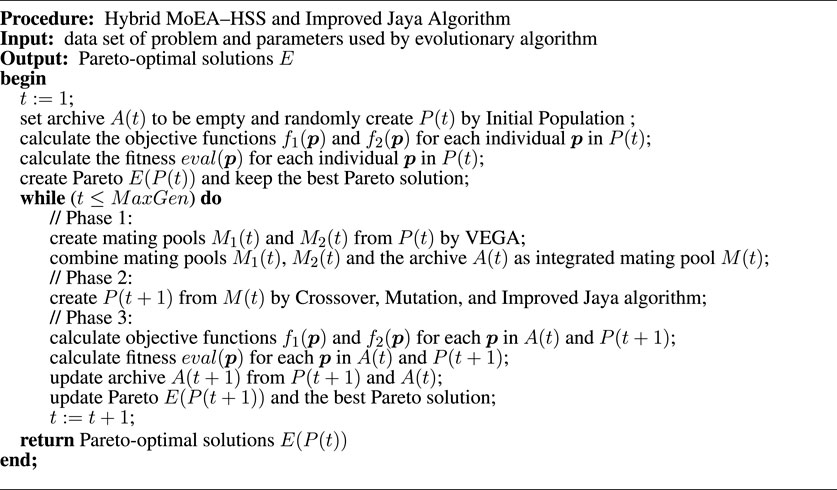
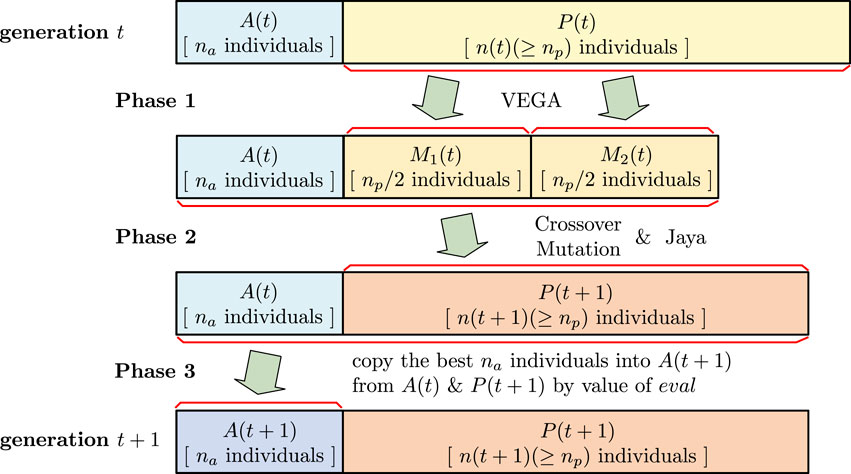
The main framework of the proposed method is shown in Figure 2. The assemblage of chromosomes in each generation
Let
Based on these values, the Pareto-optimal solution in the population is obtained and maintained.
The following three phases are executed in each generation
Phase 1: generating mating pools
1. Using the VEGA, two subpopulations
2. An integrated mating pool
Phase 2: create
For individuals in the integrated mating pool
Phase 3: create
1. For each
2.
Phases 1 – 3 of the proposed method are depicted in Figure 3.
4.2 Chromosome representation and notation
The most natural route expression is adopted as the chromosome expression in the proposed method. For example, if a sequence
Since GPOPP does not have a fixed starting point, all chromosomes
4.3 Initial population
As mentioned in Section 4.1, an initial population consisting of
1. First, the direction traversing each high-security undirected edge is decided randomly, since because all high-security edges are traversed on every patrolling route.
2. Determine the order of traversing high-security edges randomly.
3. Generate chromosome
4. The patrolling route represented by the generated chromosome
The pseudocode for the procedure generating the initial population
Let
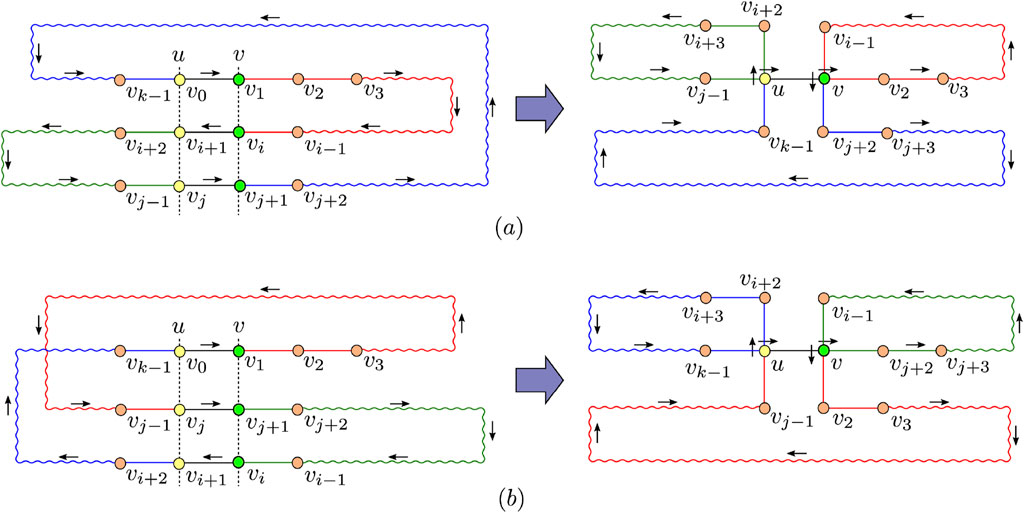
Figure 5. Construction of patrolling route from which redundant traversing of undirected edges is reduced: (a) case i < j, (b) case j < i.
4.4 Crossover
Let
(a) Any patrolling route requires that all high-security edges are traversed. First, one high-security edge
(b) Find the high-security edge
(c) In the patrolling route corresponding to the chromosome
(1) When both
(2) When
(3) When
(4) When both
(d) Find the high-security edge
(e) Create offspring
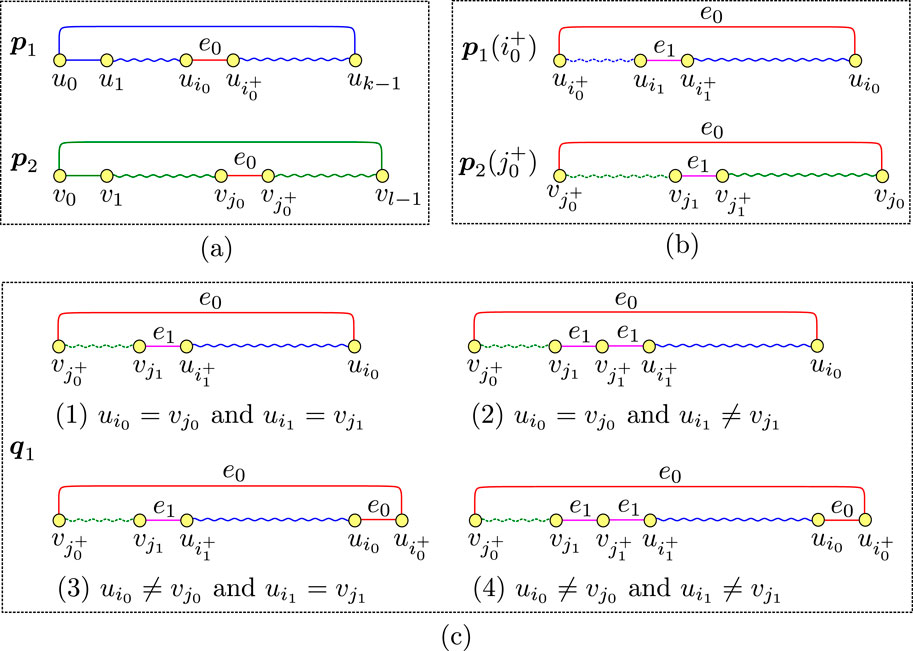
Figure 7. Creation of offspring from parent individuals in Crossover operation: (a) original parent individuals
The pseudocode for the proposed crossover operation is presented in Figure 8.
4.5 Mutation
In the crossover operation, the walk of parent individuals tends to be inherited by their offspring. Therefore, it is seldom that generated offspring will traverse vertices or edges that their parents do not. To maintain the diversity of the population, we introduce a mutation operation (Figure 9).
In this operation, the following steps are executed repeatedly: randomly select a gene (vertex)
1. if gene
2. if gene
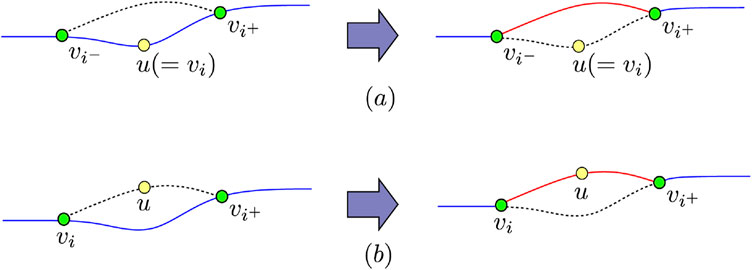
Figure 10. Mutation operation in which a vertex
4.6 Local search strategy based on the Jaya algorithm
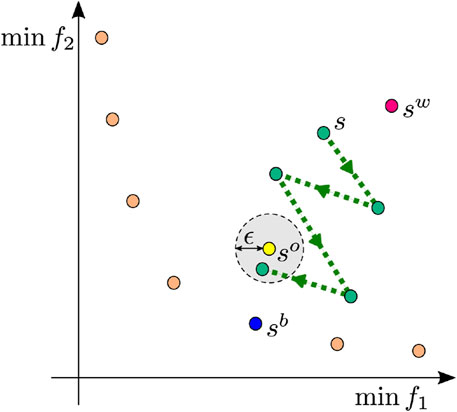
The crossover operation introduced in Section 4.4 is an order-based operation in which the orders of traversing the high-security edges of parents and other edges are inherited by offspring. To compensate for the ability to converge the solutions of this crossover, we introduce an improvement strategy that moves dominated solutions closer to a Pareto-optimal solution by combining the strategy used in the mutation operation with the Jaya algorithm.
As mention in Section 2, if the triangle inequality holds, removing a vertex
The approach we propose here (called the improved Jaya algorithm below) modifies a given individual to move closer to the best solution and away from the worst solution based on the best and worst candidates in the population. The outline of the proposed strategy is presented in Figure 11. Let
Remark that
5 Numerical experiments
In this section, we report the results of numerical experiments conducted to verify the effectiveness of the proposed method (the hybrid strategy of MoEA-HSS and the improved Jaya algorithm) for the GPOPP. In these experiments, we compared the proposed method (called pMH) with the NSGA-II (called NSGA-II) proposed by Deb et al. (2002) and the original MoEA-HSS without the improved Jaya algorithm (called MoEA-HSS). All these methods incorporated the crossover and mutation operations proposed in this paper.
Evaluating the performance of multi-objective optimization methods is not easy since it is difficult to compare the Pareto-optimal solutions (also called the nondominated solutions) obtained by different methods. We compared pMH with NSGA-II and MoEA-HSS using three representative comparison methods. Let
The three evaluation criteria we used are as follows:
1. Number of nondominated solutions. For each method
2. Generational distance. For the nondominated solution set
where
3. Coverage of two sets. For two
where
The benchmark problems used in the experiments were created based on the Mixed Rural Postman Problem (MRPP) benchmark problems RB422 (
The experiments were conducted on a PC with Windows 11, an AMD Ryzen 5 3500 CPU, 3.59 GHz, and 16.0 GB RAM. We conducted preliminary experiments using the benchmark problem RB422_10 with eight high-security undirected edges and two high-security arcs. The parameters were set as follows: the positive constant
1. If
2. If
3. Randomly select one subset
We ran 10 numerical experiments for each method (that is,
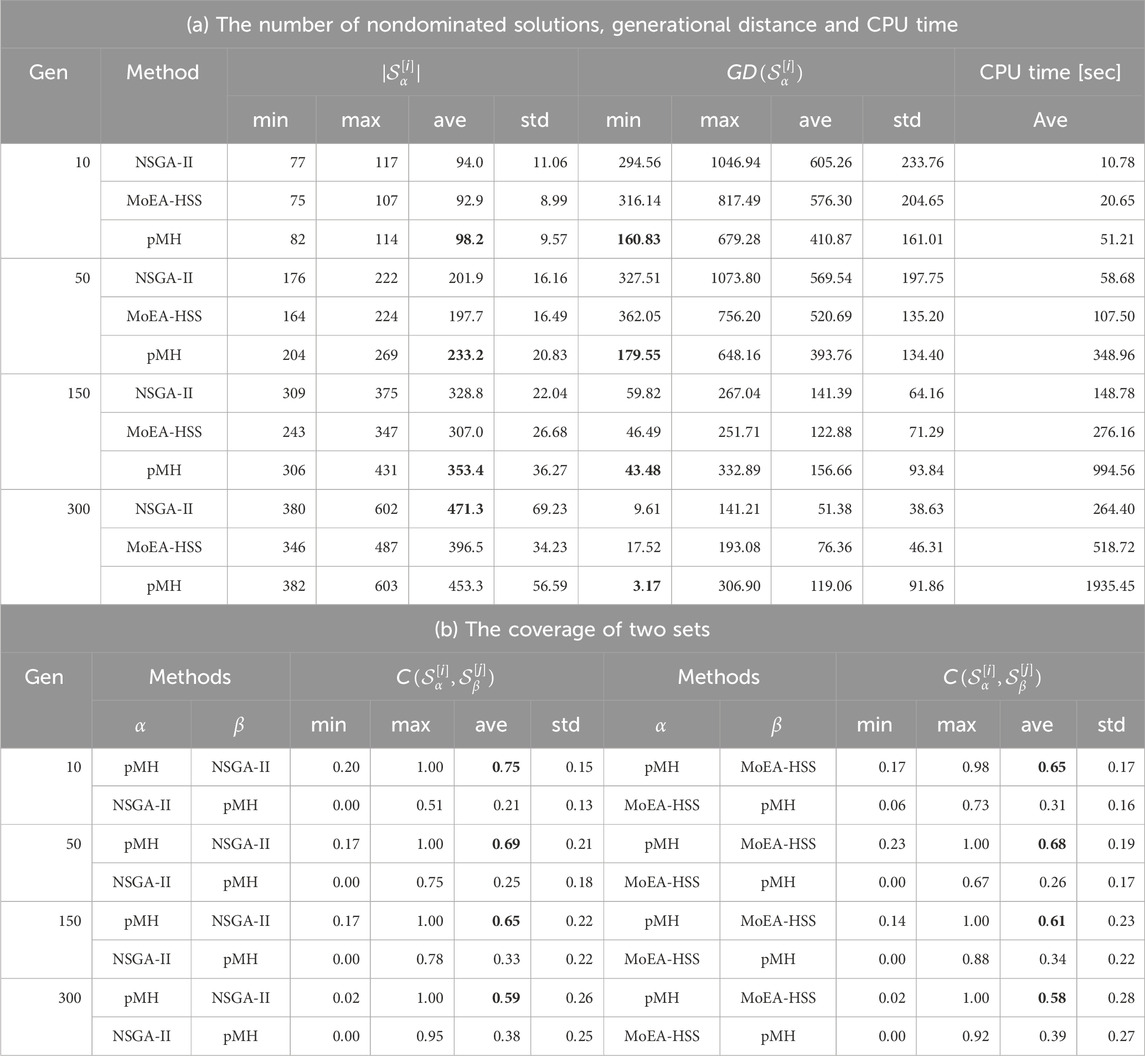
Table 1. Comparison of pMH with NSGA-II and MoEA-HSS during evolution (benchmark problem: RB422_10).

Figure 13. Evolution of nondominated solutions when executing NSGA-II, MoEA-HSS and pMH for RB422_10. (a) gen = 10 (b) gen = 50 (c) gen = 150 (d) gen = 300.
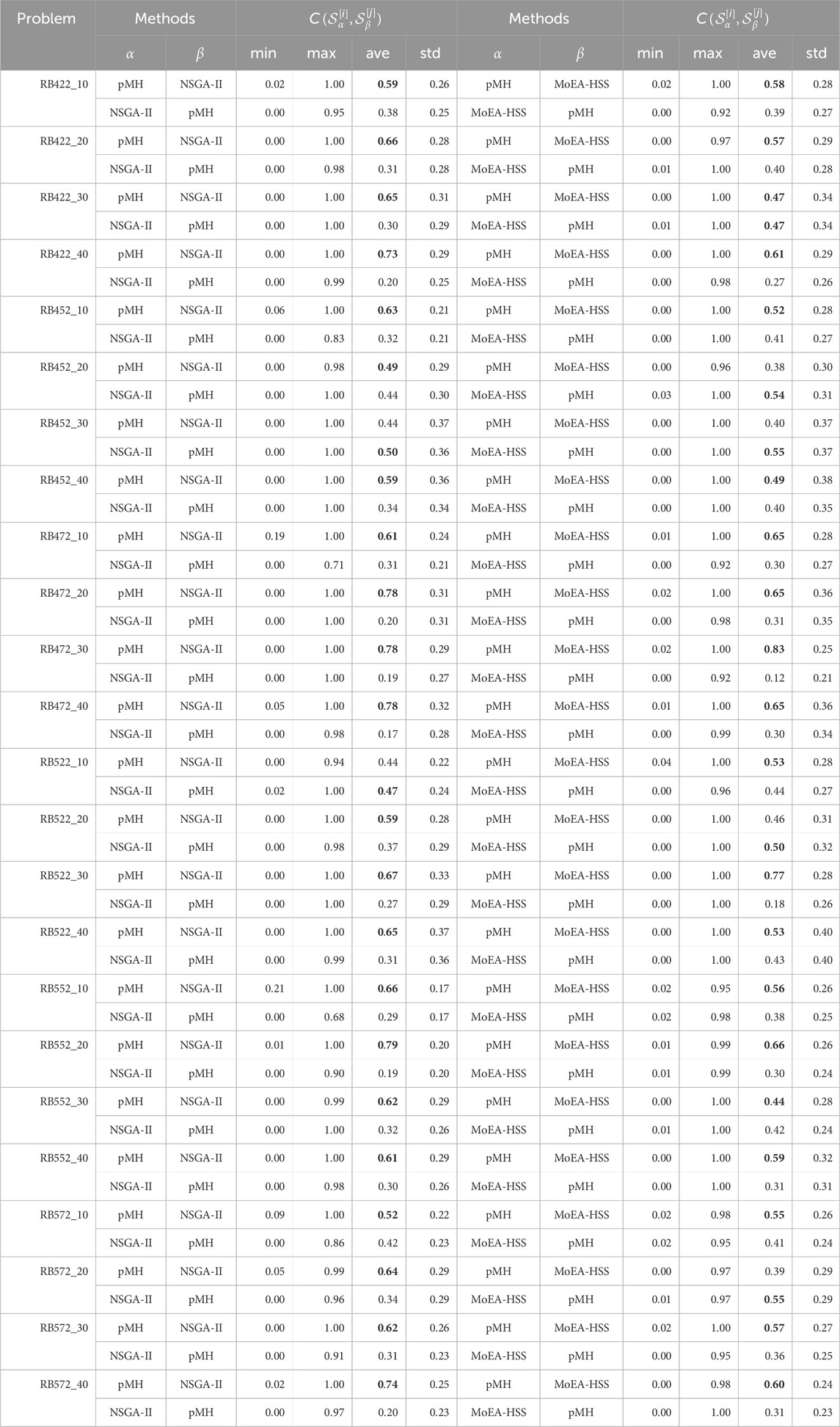
The number of nondominated solutions
The coverage
The experiment results of comparing pMH with NSGA-II and MoEA-HSS when we ran each method until 300 generations for all benchmark problems are shown in Tables 2, 3.
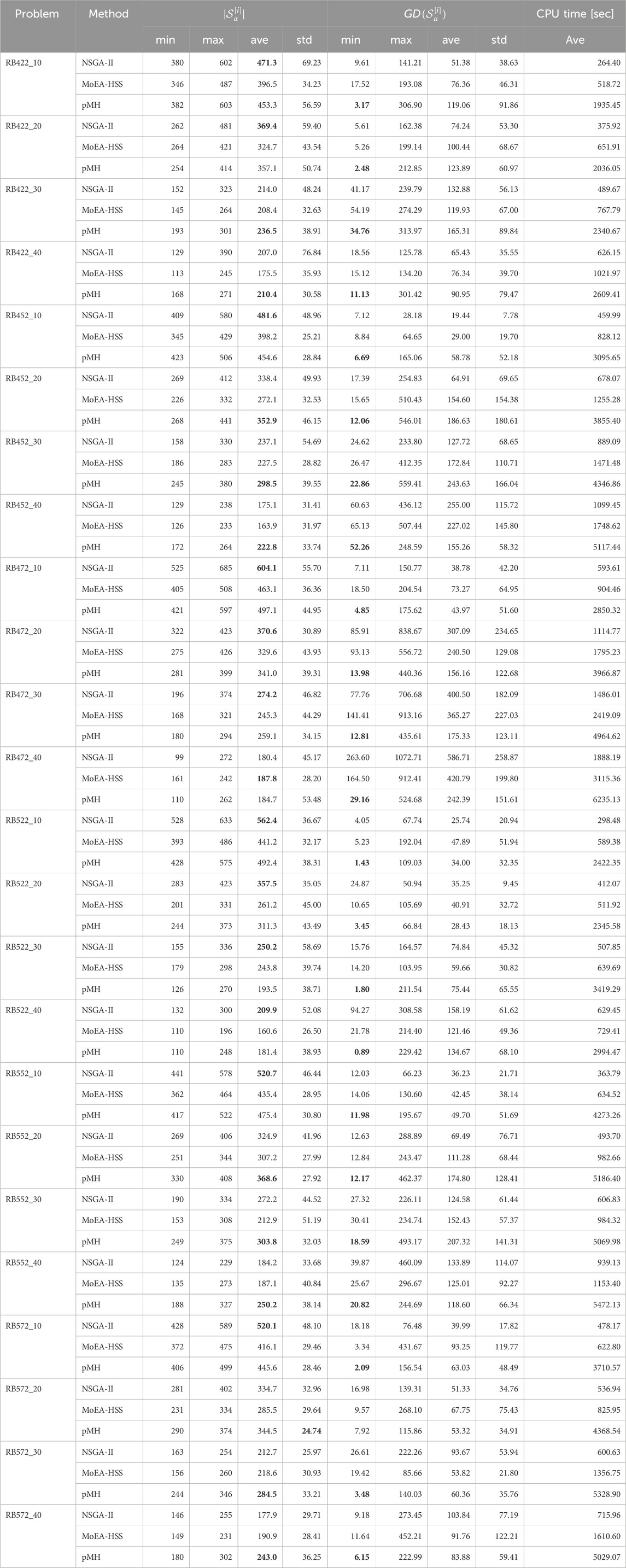
Table 2. Comparison of pMH with NSGA-II and MoEA-HSS by the number of nondominated solutions, generational distance and CPU time
Our method pMH achieved better results than other methods in all benchmark problems with respect to the generational distance and the coverage of two sets, although pMH and NSGA-II are evenly-matched at the criterion the number of nondominated solutions. Here, even if pMH is inferior to that of other methods
6 Conclusion
In this study, we defined a new arc routing bi-objective optimization problem (GPOPP) that models the patrol security of police officers (or security guards) based on the POPP and proposed a hybrid heuristic approach for the GPOPP. The proposed method combines the hybrid sampling strategy MoEA-HSS, which combines sampling strategies based on the VEGA and PDDR-FF, with a solution improvement strategy based on the improved Jaya algorithm. The solutions of the MoEA-HSS approach to the true Pareto differ in various directions because the VEGA-based sampling strategy has a preference for the edge region of the Pareto front and the PDDR-FF-based sampling strategy tends to converge toward the center area of the Pareto front. The proposed method (pMH) improves convergence by combining the MoEA-HSS with the improved Jaya algorithm-based local search method. The numerical experimental results demonstrate that the proposed method can obtain better solutions than the NSGA-II and the MoEA-HSS. The remaining challenge for us is to improve efficiency by reducing CPU time while maintaining high solution quality. In addition, extending GPOPP model will enable us to more accurately replicate the complex challenges of real-world urban policing. One extension would be to model situations where multiple officers work together, and we consider to adapt our method to address such extended problems.
Data availability statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Author contributions
FK: Writing – review and editing, Writing – original draft. HT: Writing – original draft, Writing – review and editing. MT: Writing – original draft, Writing – review and editing.
Funding
The author(s) declare that financial support was received for the research and/or publication of this article. This work was supported by research funding provided by the Maebashi Institute of Technology, Japan.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Generative AI statement
The author(s) declare that no Generative AI was used in the creation of this manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Aiello, G., La Scalia, G., and Enea, M. (2012). A multi objective genetic algorithm for the facility layout problem based upon slicing structure encoding. Expert Syst. Appl. 39, 10352–10358. doi:10.1016/j.eswa.2012.01.125
Akyurt, İ. Z., Keskinturk, T., and Kalkancı, Ç. (2015). Using genetic algorithm for winter maintenance operations: multi depot K-Chinese postman problem. EMAJ Emerg. Mark. J. 5, 50–59. doi:10.5195/emaj.2015.69
Chainey, S. P., Matias, J. A., Nunes Junior, F. C. F., Coelho da Silva, T. L., de Macêdo, J. A. F., Magalhães, R. P., et al. (2021). Improving the creation of hot spot policing patrol routes: comparing cognitive heuristic performance to an automated spatial computation approach. ISPRS Int. J. Geo-Information 10, 560. doi:10.3390/ijgi10080560
Dantzig, G. B., and Ramser, J. H. (1959). The truck dispatching problem. Manag. Sci. 6, 80–91. doi:10.1287/mnsc.6.1.80
Deb, K., Pratap, A., Agarwal, S., and Meyarivan, T. (2002). A fast and elitist multiobjective genetic algorithm: NSGA-II. IEEE Trans. Evol. Comput. 6, 182–197. doi:10.1109/4235.996017
Dewinter, M., Vandeviver, C., Vander Beken, T., and Witlox, F. (2020). Analysing the police patrol routing problem: a review. ISPRS Int. J. Geo-Information 9, 157. doi:10.3390/ijgi9030157
Edmonds, J., and Johnson, E. (1973). Matching, euler tours and the chinese postman. Math. Program. 5, 88–124. doi:10.1007/bf01580113
Elatar, S., Abouelmehdi, K., and Riffi, M. E. (2023). The vehicle routing problem in the last decade: variants, taxonomy and metaheuristics. Procedia Comput. Sci. 220, 398–404. doi:10.1016/j.procs.2023.03.051
Ghoseiri, K., and Ghannadpour, S. F. (2010). Multi-objective vehicle routing problem with time windows using goal programming and genetic algorithm. Appl. Soft Comput. 10, 1096–1107. doi:10.1016/j.asoc.2010.04.001
Gil-Gala, F. J., Afsar, S., Durasevic, M., Palacios, J. J., and Afsar, M. (2023). “Genetic programming for the vehicle routing problem with zone-based pricing,” in Proceedings of the genetic and evolutionary computation conference, 1118–1126. doi:10.1145/3583131.3590366
Ishibuchi, H., Masuda, H., Tanigaki, Y., and Nojima, Y. (2015). “Modified distance calculation in generational distance and inverted generational distance,” in Evolutionary multi-criterion optimization: 8Th international conference, EMO 2015, guimarães, Portugal, march 29–April 1, 2015. Proceedings, part II 8 (Springer), 110–125.
Kim, D., Kan, Y., Aum, Y., Lee, W., and Yi, G. (2023). Hotspots-based patrol route optimization algorithm for smart policing. Heliyon 9, e20931. doi:10.1016/j.heliyon.2023.e20931
Lenstra, J. K., and Kan, A. H. G. R. (1976). On general routing problems. Networks 6, 273–280. doi:10.1002/net.3230060305
Lenstra, J. K., and Kan, A. H. G. R. (1981). Complexity of vehicle routing and scheduling problems. Networks 11, 221–227. doi:10.1002/net.3230110211
Lu, Z., Whalen, I., Boddeti, V., Dhebar, Y., Deb, K., Goodman, E., et al. (2019). “NSGA-Net: neural architecture search using multi-objective genetic algorithm,” in Proceedings of the genetic and evolutionary computation conference, 419–427. doi:10.1145/3321707.3321729
Papadimitriou, C. H. (1976). On the complexity of edge traversing. J. ACM (JACM) 23, 544–554. doi:10.1145/321958.321974
Pizzuti, C. (2009). “A multi-objective genetic algorithm for community detection in networks,” in 2009 21st IEEE international conference on tools with artificial intelligence (IEEE), 379–386.
Quiza Sardiñas, R., Rivas Santana, M., and Alfonso Brindis, E. (2006). Genetic algorithm-based multi-objective optimization of cutting parameters in turning processes. Eng. Appl. Artif. Intell. 19, 127–133. doi:10.1016/j.engappai.2005.06.007
Samanta, S., Sen, G., and Ghosh, S. K. (2022). A literature review on police patrolling problems. Ann. Operations Res. 316, 1063–1106. doi:10.1007/s10479-021-04167-0
Schaffer, J. D. (2014). “Multiple objective optimization with vector evaluated genetic algorithms,” in Proceedings of the first international conference on genetic algorithms and their applications, 93–100.
Sgarro, G. A., and Grilli, L. (2024). Ant colony optimization for Chinese postman problem. Neural Comput. Appl. 36, 2901–2920. doi:10.1007/s00521-023-09195-4
Tang, J., He, L., Cao, Y., and Bai, H. (2024). Critical-edge based tabu search algorithm for solving large-scale multi-vehicle Chinese postman problem. Sci. Rep. 14, 12437. doi:10.1038/s41598-024-62992-2
Tohyama, H., and Tomisawa, M. (2022). Complexity of the police officer patrol problem. J. Inf. Process. 30, 307–314. doi:10.2197/ipsjjip.30.307
Tomisawa, M., and Tohyama, H. (2024). Computational complexity of the police officer patrol problem on weighted digraphs. Electron. J. Graph Theory Appl. 12, 297–313. doi:10.5614/ejgta.2024.12.2.10
Van Veldhuizen, D. A. (1999). Multiobjective evolutionary algorithms: classifications, analyses, and new innovations. Air Force Institute of Technology, 6–15.
Venkata Rao, R. (2016). Jaya: a simple and new optimization algorithm for solving constrained and unconstrained optimization problems. Int. J. Industrial Eng. Comput. 7, 19–34. doi:10.5267/j.ijiec.2015.8.004
Yu, W., Li, B., Jia, H., Zhang, M., and Wang, D. (2015). Application of multi-objective genetic algorithm to optimize energy efficiency and thermal comfort in building design. Energy Build. 88, 135–143. doi:10.1016/j.enbuild.2014.11.063
Zhang, W., Gen, M., and Jo, J. (2014). Hybrid sampling strategy-based multiobjective evolutionary algorithm for process planning and scheduling problem. J. Intelligent Manuf. 25, 881–897. doi:10.1007/s10845-013-0814-2
Keywords: arc routing problem, police officer patrolling problem, genetic algorithm, MoEA-HSS, Jaya algorithm
Citation: Kudo F, Tohyama H and Tomisawa M (2025) Hybrid heuristic approach for generalized police officer patrolling problem. Front. Ind. Eng. 3:1620422. doi: 10.3389/fieng.2025.1620422
Received: 29 April 2025; Accepted: 09 July 2025;
Published: 25 August 2025.
Edited by:
Mitsuo Gen, Tokyo University of Science, JapanReviewed by:
Wenqiang Zhang, Henan University of Technology, ChinaHuizhen Zhang, University of Shanghai for Science and Technology, China
Copyright © 2025 Kudo, Tohyama and Tomisawa. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Masaki Tomisawa, dG9taXNhd2FAbWFlYmFzaGktaXQuYWMuanA=
 Fumito Kudo1
Fumito Kudo1 Hiroaki Tohyama
Hiroaki Tohyama Masaki Tomisawa
Masaki Tomisawa