Abstract
Wireless sensor networks (WSNs) are extensively employed in various applications like environmental monitoring, healthcare, and industrial automation. However, their performance is severely affected by energy limitations and unreliable data communication because of low battery capacity and dynamic network scenarios. Optimal cluster head (CH) selection is one of the major challenges in WSNs, and it is a critical factor in network lifetime and energy efficiency. The proposed work introduces a clustering mechanism and self-healing and energy-efficient cluster-based routing (SHEER) for CH selection by considering various parameters like energy remaining, distance to the sink, and the trust metric. In contrast to traditional approaches, the proposed method not only maximizes CH selection but also enhances cluster member (CM) distribution for balanced energy consumption. Moreover, a self-healing mechanism is integrated to preserve network stability by dynamically redistributing CHs and CMs in the event of node failure. This increases network flexibility, minimizes energy loss, and extends network lifetime. To confirm the proposed strategy, a large-scale simulation is performed in Cooja software using 100 to 500 sensor nodes. The outcome showed that the proposed SHEER technique enhances WSN performance with a 98% packet delivery ratio (PDR), a 2% packet loss ratio (PLR), and less energy consumption while maintaining stable clusters. These results show that the clustering optimization technique significantly improves the energy efficiency, network lifetime, and data transmission reliability, ensuring a high packet delivery ratio.
1 Introduction
In the modern digital era, wireless sensor networks (WSNs) have become a cornerstone of intelligent systems. The ability to collect, process, and transmit data without human interaction makes various applications for healthcare, environmental, industrial, and smart cities possible. WSNs enhance efficiency through seamless communication between devices, which is useful for decision making and reducing operational costs. This is suitable for deployment in remote or hazardous environments where manual monitoring is not necessary. It ensures continuous data collection and transmission and encompasses various real-time applications of wireless sensor networks in health, agriculture, military, and even industrial monitoring. It also elaborates on the necessity of timely data transmission, energy efficiency, and reliability in these applications (Ali et al., 2017).
The architecture of WSNs describes the data flow from sensor nodes to the user and communication between the sensor nodes. The sensor network communication will have multiple sensor nodes that collect information and transmit it through multi-hop. Cluster-based communication provides a stable and energy-efficient communication in WSNs. The clustering of sensors can be done using various parameters such as residual energy, distance from the sink, communication costs, and topological factors (
Mukherjee et al., 2019). Sensor nodes are grouped into clusters based on parameters such as node proximity, which ensures seamless connectivity and the trustworthiness of individual nodes. Additional parameters may be considered to enhance the robustness of clustering. These clusters are designed to conserve energy by allowing nodes to communicate only with their respective cluster head (CH) rather than directly with the base station. The CH aggregates data from its cluster members (CMs) and forwards it to the base station, thereby reducing communication overhead. The base station then transmits the collected data over a wireless network (e.g., the Internet) to the end user, such as a mobile device or computer. Finally, the user analyses the sensor data and takes appropriate action, as illustrated in
Figure 1. The major components of WSNs are sensor nodes that are actively involved in sensing data. Sensor nodes are used to transmit data wirelessly. A sink node can also be called a destination node and base station, which acts as a gateway between sensor nodes and end users.
➢ Sensor nodes: The basic functional unit in WSN, which consists of a sensor, memory, and battery.
➢ Sensor field: Area where sensors communicate.
➢ Sink node: A node to which cluster heads carry packets.
➢ Base station: this acts as a gateway between sensor nodes and the end user as data are forwarded from the WSN to the server.
FIGURE 1

Cluster architecture of WSNs.
WSNs are widely used in diverse fields because they provide real-time monitoring and automation. WSNs affect our daily lives in various ways. In healthcare, wearable health tracking and early detection systems can monitor patients remotely, which helps doctors monitor patients, provide treatment, and balance work. It greatly improves patient quality of life by utilizing remote health data collection and processing (Tennina et al., 2014).
In environmental monitoring, WSNs are used to track climatic changes, air pollution, and natural disasters like earthquakes. The deployed sensors monitor environmental conditions and transmit critical information to the cluster head, enabling rapid response to mitigate potential threats and ensure public safety. They allow intelligent environmental management, monitoring factors such as temperature, humidity, and air quality (Jaladi et al., 2017).
Industrial supply chain monitoring, predictive maintenance, and process optimization are carried out by WSNs. WSN can be used in monitoring machine health by checking temperature, vibration, and pressure, reducing machine failure and downtime, and improving control by detecting defects in production. Increased data transmission efficiency, energy savings, and reliable communication have been maximized to support wireless communication for Industry 4.0 applications (Rani et al., 2021).
In the military, security sensors are used for battlefield surveillance and border security. They help detect enemy movements, provide detection at the border, and deliver real-time intelligence to commanders. They emphasize real-time data collection, energy efficiency, and secure communication to enhance defense capabilities (Prabhu and Professor, 2016). They play a very crucial role in agriculture in activities such as checking soil health, irrigation, and pest control.
Routing in WSNs is complex due to their dynamic topology and energy constraints. It relies on battery nodes that frequently change their positions or fail due to power depletion. Protocols forward data from sensor nodes to the sink while minimizing energy consumption. Routing techniques such as direct communication and multi-hop routing lead to uneven energy depletion, network partitioning, and reduced lifetime. Routing plays a vital role in the network layer and has different modes of transmitting by considering factors like node density, energy, mobility, and distance between nodes, which lead to different routing algorithms or protocols (Al-Karaki and Kamal, 2004).
Energy efficiency is the most critical challenge in WSNs, where sensor nodes are typically powered by batteries with limited capacity. Effective routing is essential for achieving energy efficiency in WSNs and for balancing the high energy consumption associated with data transmission. Energy is consumed in three ways: data sensing, processing, and communication, with data transmission being the most power-intensive task. Energy usage leads to node failure, reducing network lifetime. Various energy-efficient techniques such as duty cycling, energy-aware clustering, data aggregation, and energy harvesting have been introduced to manage energy efficiently. Nevertheless, energy-efficient protocols that do not compromise data accuracy and network reliability are still ongoing challenges in WSN research.
WSN nodes have limited memory, processing power, and storage capacity, which will restrict the complexity of algorithms and protocols that can be implemented. Sensor nodes have minimal RAM and flash memory in traditional computing systems, where many routing and clustering algorithms require high computational resources. To overcome these problems, researchers are focusing on finding lightweight protocols, in-network processing, and edge-computing solutions. The critical challenge is balancingthe computational efficiency while maintaining security and reliability in WSN protocol design (Pathak, 2013).
Various techniques have been developed in WSNs for efficient energy usage. Clustering algorithms, such as low-energy adaptive clustering hierarchy (LEACH) (Kandris et al., 2023) and hybrid energy-efficient distributed clustering (HEED) (Janani et al., 2016), help reduce energy consumption by grouping the nodes and selecting the efficient cluster head to reduce direct communication to the sink. Swarm intelligence-based optimization, particle swarm optimization (PSO) (Kulkarni and Venayagamoorthy, 2010), and ant colony optimization (ACO) (Han et al., 2024) improve CH selection and routing by dynamic-decision making. The ant algorithm is based on the behavior of ants as they search for food and explore their surroundings. One ant leads the group, and other ants follow because the first ant releases a chemical that other ants can follow to collect the food they need. This algorithm is used in IoT for real-time data collaboration. Bio-inspired algorithms are used in optimizing node deployment and communication paths to achieve energy-efficient, eco-friendly WSN operations (Kumar et al., 2019) by dynamically adapting network parameters. These are aimed at improving network lifetime, data reliability, and energy efficiency. Machine learning is used to predict node failures and detect anomalies in network trafficking (Alsheikh et al., 2014).
Self-healing techniques hold key properties of WSNs, like the routing process and dynamic power distribution, to create stable networking and secure data transmissions. Self-sufficient sensor nodes work together to collect and analyze data. Wireless sensor networks face various security threats, including jamming attacks that disrupt communication channels. To counter such disruptions, self-healing mechanisms are employed to restore network functionality. Self-healing mechanisms can also be triggered when a sensor node depletes its energy or becomes unresponsive due to malfunction. The main network properties are rerouting, which dynamically redirects the data through alternative paths. While maintaining network connectivity, a power allocation will adjust the transmission power. Nodes will work together in detecting, avoiding, or mitigating the effects of jamming attacks with the cooperation mechanism. This helps communication between the nodes and maintains the energy levels for better transition of packets. Self-healing has a strong connection with clustering approaches, where both aim to optimize network topology for improving energy efficiency and data integrity (Jiang et al., 2024).
The proposed work is based on multiple objectives, and sensor node clustering plays a vital role. Clustering is established based on parameters such as residual energy, distance to the sink node, trust metrics, and proximity to neighboring sensor nodes. Self-healing allows network communication to dynamically select CHs and CMs in case of node failure, maintain stability, and reduce energy wastage. The proposed work is done in the Contiki operating system, simulated in Cooja with 500 sensor nodes.
The main contributions of the proposed work include the following:
➢ Developing a cluster-based communication framework for sensor nodes utilizing the self-healing and energy-efficient cluster-based routing (SHEER) algorithm to achieve energy-efficient data transmission.
➢ Designing and implementing a self-healing mechanism that maintains uninterrupted communication by dynamically regrouping sensor nodes in the event of node failures.
➢ Proposing an optimized shortest-path routing protocol for efficient intercluster communication.
➢ Strengthening secure communication in WSNs through a trust-based authentication scheme among sensor nodes.
2 Related work
An overview of energy efficiency techniques is presented by Rault et al. (2014), addressing all layers of the WSN protocol stack. Energy-efficient techniques from the physical to the application layer and topics such as data aggregation, duty cycling, and routing optimization are discussed. This survey puts great emphasis on the concept of cross-layer design for maximizing energy efficiency and extending the operational lifetime of the networks.
A low-energy fixed clustering algorithm (LEFCA) aimed at improving energy efficiencies in WSNs is proposed by Cengiz and Dag (2016). In LEFCA, clusters are formed during the setup phase and remain unchanged throughout the lifetime of the sensor nodes. Hence, the fixed clustering approach reduces energy overhead caused by the frequent reformation of dynamic clusters. Simulation results show that LEFCA substantially conserves energy and prolongs network lifetime compared to conventional clustering approaches. Traditional and advanced clustering protocols (Kaur and Kour) in WSNs concentrate on energy efficiency. The article shows how different clustering techniques impact network lifetime, data transmission, and energy consumption.
A multi-objective whale optimization algorithm (VL-MOWOA) (Saad et al., 2025) for trust-aware data gathering has been proposed. The trustworthiness of the node is calculated by considering factors like node reliability, energy consumption, and communication pattern.
An optimal routing algorithm for WSN using an ant-lifetime routing algorithm with multi-hop (Siddaramu and Ramaswamy, 2025) aims to reduce node energy, extend the network lifespan, and improve data transmission.
To improve the lifetime of the network, energy consumption is reduced in WSNs by using techniques such as efficient routing (Singh et al., 2019), data aggregation, duty cycling, and energy-aware protocols across all layers. This necessitates achieving energy efficiency because the limited battery resources of WSNs and the remote environment deployment factor into this.
An adaptive clustering approach to dynamic load balancing and energy efficiency in WSNs (Gherbi et al., 2016) provides a method of adaptively adjusting clusters according to energy and network conditions. By dynamically rotating the cluster head, the method ensures that consumption is balanced across the network. The adaptive mechanism boosts energy efficiency and increases the lifetime of the entire network. Blockchain technology (Rehman et al., 2022) is used for attaining data security and trust within WSNs. It enables secure data transmission while optimizing energy consumption based on lightweight mechanisms of blockchain technology. It determines a trade-off between security and energy efficiency, resulting in enhanced reliability and lifetime of the networks.
Routing protocols play a crucial role in conserving the limited battery energy of sensor nodes by selecting energy-efficient paths for data transmission. A comprehensive analysis of routing protocols is used for energy-efficient performance in the WSNs (Pantazis et al., 2013), categorized on the basis of various techniques, including clustering, data aggregation, and hierarchical routing. To develop an energy-efficient clustering technique conducive to energy conservation and prolongation of network lifetime, the focus of Wei et al. (2011) is on optimized CH selection based on a residue of energy and distances. The energy-saving capabilities of compressive sensing (CS) (Karakus et al., 2013) in data transmission are used in order to minimize the use of energy. The article reviews the balance between data precision and energy consumption. The findings demonstrated that CS would lead to drastic savings in energy and an acceptable standard of data reconstruction.
Enhancing the energy efficiency of wireless sensor networks for mining industry applications deals with energy-efficient WSN designs for rigorous mining environments. The optimized routing and clustering techniques will reduce energy consumption (Chehri et al., 2020). The method ensured reliable data transmission and a long network lifetime in mining applications. Dynamic techniques are used for clustering to enhance energy efficiency in heterogeneous WSNs (Alomari et al., 2022; Zagrouba and Kardi, 2021).
Machine learning algorithms like K-means clustering, Q-learning, and unsupervised learning could also be useful for forming efficient clusters where datasets must be properly trained and tested to provide the best outcome (Akram et al., 2025).
Energy efficiency and self-healing have been concentrated in fault-tolerant routing path identification with genetical swarm optimization (FTGSO), merging genetic algorithms (GA) and particle swarm optimization (PSO) to optimize CH selection based on factors like residual energy, coverage, communication costs, and proximity. The approach establishes a fault-free routing path while incorporating a self-healing mechanism to resolve network connectivity issues, ensuring the system can return to normal operations efficiently (Shyama and Anju, 2022).
Literature review shows that energy-efficient, self-healing, and secure WSNs provide a sustainable network providing highly efficient communication. Hence, the proposed work concentrates on energy-efficient, self-healing, and secure WSNs. Clustering is done in the proposed approach, concentrating on energy, proximity, and the trust metric to provide efficient communication.
3 Methodology
WSNs are needed for the sustainable development of smart cities, but the major challenge faced by WSNs is energy constraints. To optimize energy consumption during the formation of trusted sensor node groupings, clustering is performed considering various parameters. If a specific sensor node fails to respond within a predefined time threshold due to energy depletion or hardware malfunction, the network initiates a self-healing mechanism, rerouting communication through neighboring nodes, as shown in Figure 2. This multi-objective clustering, combined with self-healing capabilities, ensures reliable and energy-efficient data transmission from cluster members (CMs) to the cluster head (CH) and subsequently to the sink node and base station.
FIGURE 2
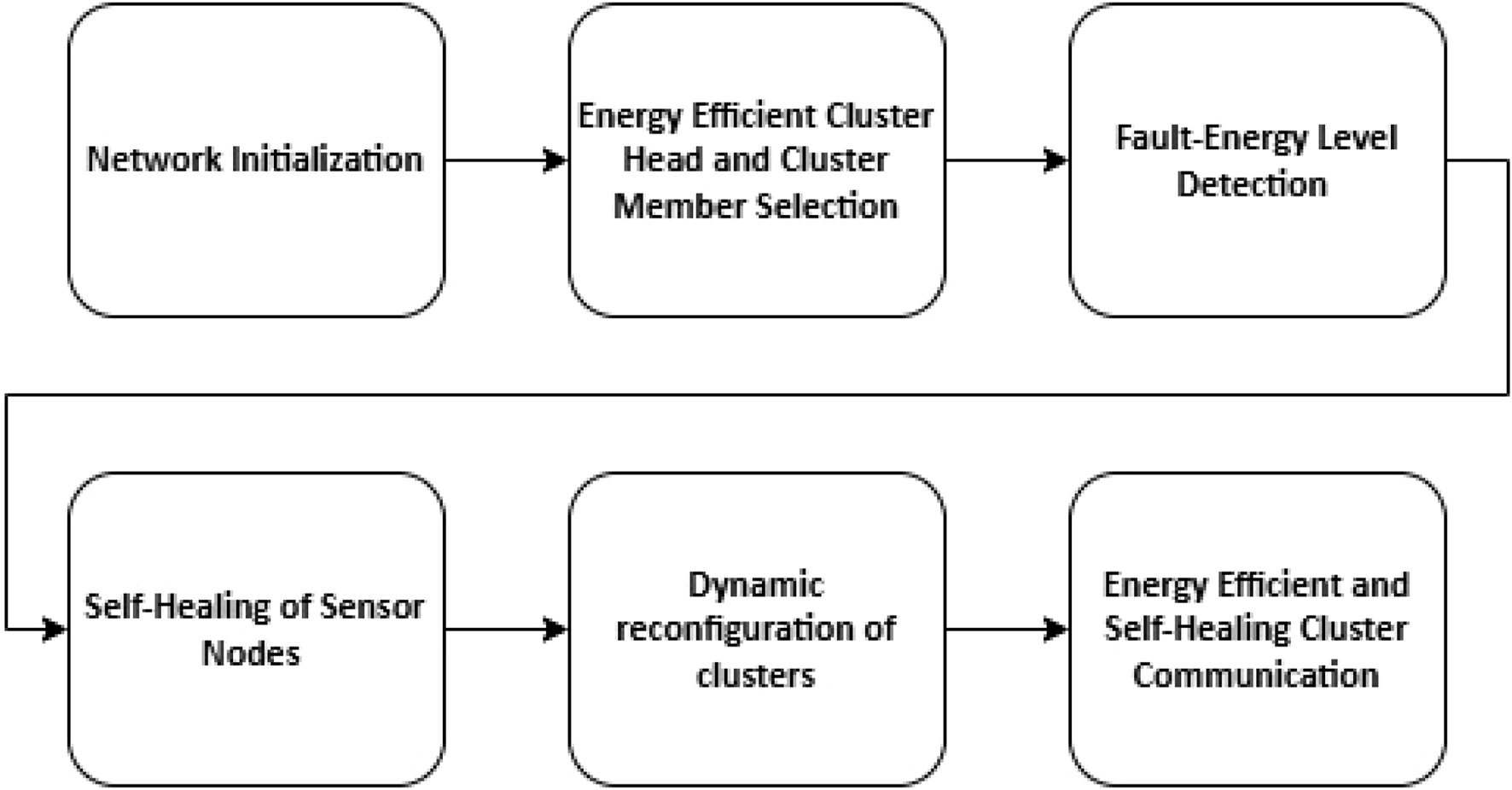
Block diagram of the proposed approach.
A flow diagram for self-healing and energy-efficient clustering algorithm for WSN optimization is shown in Figure 3. It is a systematic sequence intended to address fundamental challenges like energy consumption, network stability, and dynamic node failures. The proposed approach combines several improvements, such as an adaptive clustering technique for effective CH selection, a self-healing process to dynamically recover from node failures, and an energy-conscious optimization technique. These elements cooperate to provide extended network lifetime, enhanced data transmission reliability, and reduced energy wastage. The initial phase is network initialization and clustering. It is the deployment of sensor nodes and grouping of sensor nodes on the basis of important feature parameters like energy, distance to the sink, and trust based on successful packets delivered by the node. In the proposed SHEER, the best CHs are dynamically chosen to achieve energy consumption balance and stability. The clustering process minimizes communication overhead while improving data aggregation efficiency.
FIGURE 3
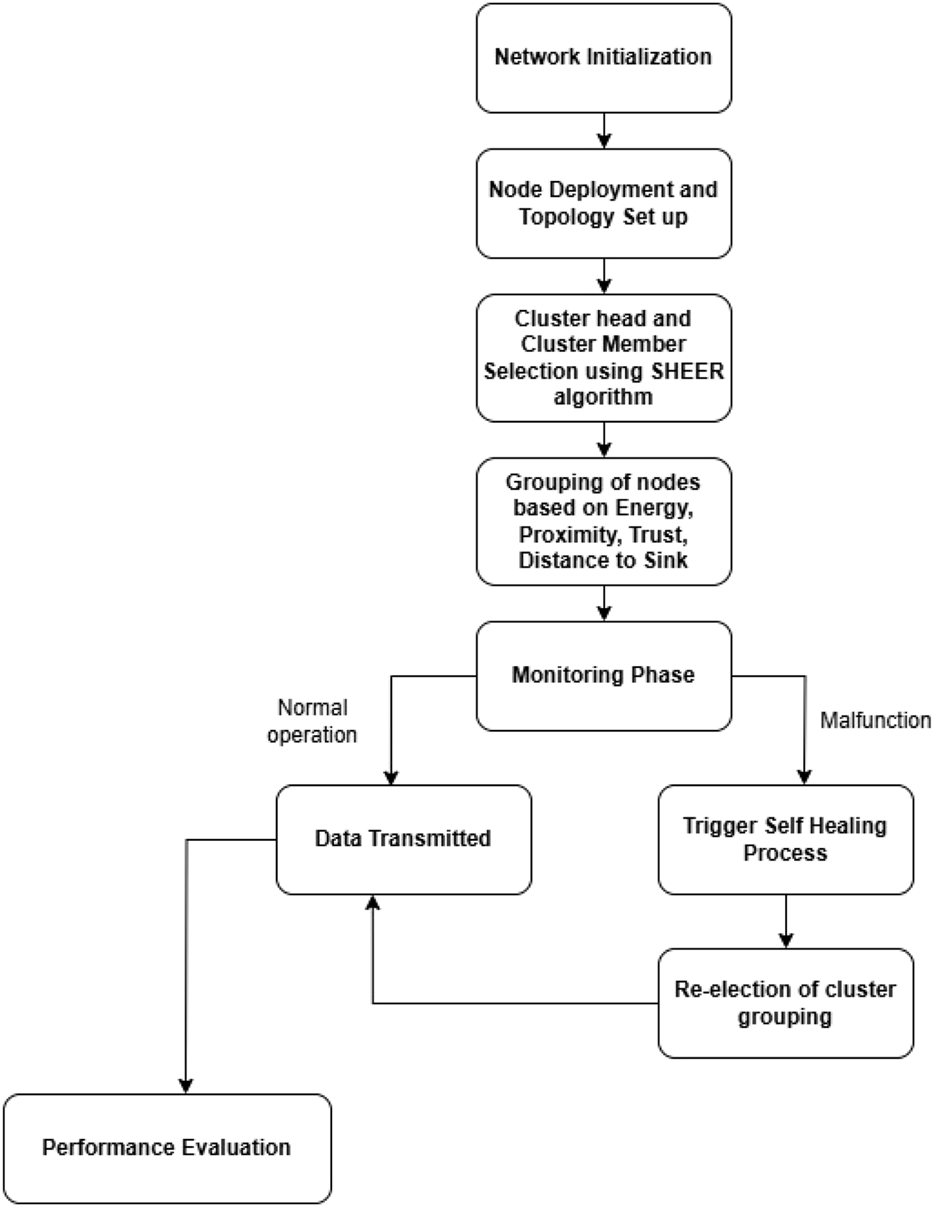
Flow diagram for the proposed approach.
When a CH fails or becomes inefficient, the self-healing mechanism dynamically reassigns roles, promoting continuous communication between nodes. Data transmission is optimized with multi-hop routing, which minimizes direct transmissions to the sink and enhances network longevity.
Sensor nodes are initialized in the network at the start of the process, and initial configurations are established. The nodes are provided with parameters like residual energy, proximity, and trust. The topology of the network is created during this step, and sensing and data transmission starts with the nodes. CHs and cluster members (CMs) are selected using the proposed algorithm. In order to minimize energy usage and improve the stability of the network, SHEER is used to dynamically select CHs based on several important features, such as node residual energy, distance to sink node, trust, and proximity. After the CHs are chosen, CMs are allocated to specific CHs considering parameters such as trust, node proximity to CH, and residual energy.
Once the cluster head and cluster member are grouped, packets are transmitted. If a malfunction is detected, then self-healing is triggered. As a result of energy drain, hardware faults, or communication faults, certain sensor nodes can fail in the long run. For this purpose, the proposed model incorporates a self-healing mechanism.
When a CH fails or becomes inefficient, the self-healing algorithm selects an optimal substitute CH from available CMs. If a sensor node fails to transmit, the network reconfigures itself to provide uninterrupted data flow, keeping packet loss minimal and stability ensured.
3.1 Clustering and self-healing of sensor nodes
3.1.1 Energy
The SHEER WSN clustering mechanism emphasizes energy in the selection of the CHs and the CMs. All nodes start at maximum energy, which dissipates steadily over time with consumption in different activities such as the sending, receiving, and processing of data. The residual energy of a node is renewed after every communication round. This energy includes transmission energy, reception energy, and processing energy. As the preferred CHs are those with above-average residual energy, network longevity is ensured by avoiding low-energy nodes when making these selections, preventing nodes from failing early, as shown in Equation 1. Thus, the energy-aware selection process balances the load in the network system, consequently prolonging the lifetime of the system.
3.1.2 Proximity
The selection of cluster heads and cluster members in WSN clustering based on the proposed algorithm is based on the key factor proximity. Proximity is the measure that defines how close a node is to its neighbors or the sink, thereby influencing the efficiency of communication and energy consumption. Euclidean distance is used to calculate the proximity between nodes. Nodes that are shorter in distance to the potential cluster head or sink are selected. CHs are selected from well-connected nodes, thus reducing transmission costs. CM members are selected based on joining the nearest CH and minimizing communication losses, as shown in Equation 2. This architecture boosts the stability of the network and extends its lifetime.
3.1.3 Distance to sink
Based on how far a CH is from the sink, the Euclidean distance is calculated for each node in order to determine its efficiency in relaying data. The closer nodes consume less energy for transmission to the sink; hence, they are suitable for choosing CHs. In CH selection, the nodes are connected to CHs with a lesser overall distance from the sink, resulting in energy and communication savings. This distance-aware approach aids in balancing energy consumption and prolonging the network lifetime, as well as improving data delivery efficiency. Distance to the sink is calculated based on Equation 3.
3.1.4 Trust
Trust is assessed using in-built consideration of the node’s historical behavior, inclusive of successful packet transmission, maintaining the integrity of data throughout transmission, and participating in some network activities. The trust of a node is calculated by considering direct and indirect trust, as given in Equation 4. Each entity, node, and CH alike is given a trust score associated with parameters such as packet delivery ratio (PDR), which comes under direct trust, and indirect trust is past cooperation. Higher-trust nodes are preferred to be chosen as CHs to prevent malicious or faulty nodes from being chosen. The nodes select CHs with a high trust score for CM selection to achieve secure data transmission. This trust-aware strategy enhances the overall reliability of the network, reduces the risk of data loss, and strengthens security against various types of threats or attacks. Equation 5 shows weights reflecting the importance of each metric. The trust threshold is established at 0.7, and only sensor nodes with trust scores higher than this value are selected for clustering, thereby guaranteeing secure communication.
Only nodes with are considered eligible for CH roles, ensuring security and operational stability.
Overall, the fitness function for cluster selection is given by Equation 6, and Table 1 shows the notations used.
TABLE 1
| Residual energy of the node | |
| Maximum initial energy of particular node | |
| Distance to neighbors (for CH) or distance to CH (for CM) | |
| Maximum communication range | |
| Distance to the sink node | |
| Maximum possible distance to the sink | |
| Trust value of the node (0–1) | |
| Direct trust | |
| Indirect trust | |
| Cooperation history trust | |
| PDR | Packet delivery ratio |
| PLR | Packet loss ratio |
Notation used.
3.1.4.1 Significance of trust metric in mitigating a malicious node.
A secure mechanism plays a vital role in providing sustainable WSNs. The trust of the node is calculated based on direct and indirect communication of the node. When nodes are deployed, their communication links are monitored continuously. If a node does not respond in a predefined threshold time or intentionally drops a packet without forwarding the data, then it is considered to be a malicious node or a malfunctioning sensor node. Received signal strength, packet forwarding rate, and dropping rate are continuously monitored to remove a malicious node from the communication link. Some of the attacks are discussed below to ensure how trust plays a significant role in providing safer communication.
3.1.4.2 Selective forwarding attack
If a sensor node is hacked and behaves as a selective forwarding attacker, then the packet forwarding rate varies, and PDR will be low. The packet originated in the source node will not be forwarded as a whole, and the selective packet will be dropped by the compromised node, which will reduce the trust score of the node, thus removing the compromised node.
3.1.4.3 Denial of service attack
A denial-of-service (DoS) attack in WSNs is a cybersecurity threat where adversaries seek to impair network operations by flooding it with excessive traffic or taking advantage of system weaknesses. This disruption can degrade performance, exhaust resources, and hinder communication between sensor nodes. If a node is compromised, its signal strength will be greater than that of another genuine node. Because it does not forward data, its trust score will be reduced, and the communication link will not be provided to the compromised node.
3.1.4.4 Sybil attack
A Sybil attack in WSNs occurs when a malicious node generates multiple fake identities to manipulate routing and data aggregation. This deception disrupts network operations, leading to security vulnerabilities. The trust-based authentication scheme would be able to identify and remove compromised Sybil nodes.
3.1.4.5 Wormhole attack
When an attacker creates a false tunnel between distant nodes, it can trick the network into rerouting data through their controlled link. This manipulation can disrupt routing protocols and enable data interception. Trust-based detection is used to identify and mitigate the attack.
The trust metric plays a very significant role in providing stable and smoother communication in WSNs, thus ensuring secure communication.
3.2 Self-healing
The self-healing mechanism concentrates on network stability by detecting and replacing the failing CHs and CMs. In the proposed self-healing mechanism for WSNs, the reliability of the node is assessed using a dual-parameter evaluation strategy: residual energy and response time. A node is considered unreliable and is subject to replacement if it fails to meet either of the defined thresholds. The node is marked as failed under the condition shown in Equation 7.
This approach enhances sustainable network configuration by ensuring that sensor nodes suffering from energy depletion or processing delays due to node malfunctions are replaced by the self-healing mechanism, thereby maintaining network stability, communication efficiency, and timely data delivery. Algorithm 1 shows the proposed SHEER algorithm.
Algorithm 1
Input: Clustering of sensor nodes N,
Output: Stable clustering, self-healing, re-election of cluster head, performance analysis
1. Initialize the network with N randomly deployed sensor nodes
2. For each node i ∈ N
a. Assign initial values: residual energy, trust, node proximity, and distance to sink
3. For each node i ∈ N, compute the fitness function
CS =
Select highly efficient nodes as cluster heads (CHs)
b. For each non-CH node, join the CH as a cluster member
c. Assign next-hop routing for intra- and inter-cluster communication
d. Monitor CHs and CMs for failure
e. If any CH or CM fails:
- Trigger self-healing
- Detect failure
- Re-select CH or reroute
- Update cluster memberships
g. Perform data transmission: Nodes → CHs → Sink
h. Evaluate performance metrics: PDR, PLR, energy consumption, CH stability
3.3 Intercommunication between CH and CM
Inter-cluster communication in SHEER-based WSNs can be effectively managed by extending the fitness evaluation beyond CH selection, as shown in
Equation 8. After forming clusters, each CH is responsible not only for aggregating data from its cluster members but also for forwarding that data toward the sink. To determine the optimal next-hop CH for inter-cluster forwarding, each CH evaluates its neighboring CHs based on a communication fitness function. This function typically includes parameters such as the distance between CHs, the residual energy of the candidate CH, and its trust score. By applying the SHEER algorithm, each CH selects the neighbor with the highest communication fitness score as the next relay node. This approach ensures that inter-cluster routing is both energy-aware and trustworthy, thereby enhancing network longevity and reliability. The process continues in a multi-hop manner until the data reaches the sink node. This routing model supports adaptive and intelligent forwarding decisions, making it highly suitable for dynamic and resource-constrained WSN environments.
: distance between current CH and candidate CH
: trust score of candidate CH
: residual energy of candidate CH
4 Results and discussion
The proposed SHEER clustering algorithms for WSNs were tested on important feature performance factors, such as PDR, packet loss ratio (PLR), energy utilization, and cluster stability. Simulation has been performed using the Contiki-OS on a Cooja simulator using 500 sensor nodes. The Cooja simulator is selected over other WSN simulators because of its ability to emulate real operating system behavior, specifically the Contiki-NG OS, at the instruction level. Unlike abstract simulators such as NS-3 or OMNeT++, Cooja allows us to run the exact embedded C code that would be deployed on real sensor nodes, such as Zolertia Z1 or Tmote Sky. It focuses on self-healing and energy-efficient cluster-based routing. Cooja supports fine-grained simulation of media access control (MAC) and routing protocols, precise energy consumption estimation through the Energest module, and realistic debugging of node-level failures. These features enable a more accurate approximation of real-world deployment environments, thereby ensuring that the evaluated performance metrics closely align with practical implementation results rather than remaining confined to abstract simulation outcomes. The core of SHEER’s scalability lies in its optimized cluster formation and adaptive CH selection process, which relies on dynamic metrics such as residual energy, distance to the sink, trust, and node proximity. These parameters ensure that CHs are selected efficiently, regardless of network size, avoiding overloading any single node.
Moreover, the self-healing mechanism in SHEER dynamically redistributes CHs and CMs when nodes fail or move out of range. This allows the network to reconfigure itself without manual intervention, maintaining stable and balanced clusters even in very large-scale networks. As the number of nodes increases, this mechanism prevents cluster congestion and ensures even energy distribution across the network, which is critical for sustaining network lifetime and performance.
The proposed approach selects CHs and CMs dynamically using parameters such as remaining energy, proximity, and trust values. The outcomes prove that the suggested method has an excellent 98% PDR, showing highly efficient and effective data transfer. Moreover, the PLR was only 2%, which indicates negligible packet loss during communication. In energy efficiency, the SHEER clustering mechanism drastically optimized energy usage by providing balanced load distribution among CHs.
Nodes with more residual energy and greater connectivity were given priority for CH election, minimizing the repeated election of CHs, thus improving network stability. The overall energy drain was only 2%, reflecting the efficiency in extending the network lifetime. In addition, with trust-based CH selection, the system enhanced network security and robustness against malicious nodes, resulting in improved overall performance. The method also revealed high flexibility in adapting to network dynamics. Upon failure or malfunction of sensor nodes, the network adapted CH and CM selection dynamically, avoiding communication loss and ensuring consistent routing. With respect to common clustering algorithms, the method indicated greater stability and reduced energy consumption, proving ideal for mass IoT applications. In general, the findings verify that the SHEER clustering improves WSN efficiency, robustness, and longevity and thus emerges as a valid solution for actual deployment.
Figures 4, 5 show a simulation within Cooja, the commonly used Contiki network simulator for WSN simulations. The simulation depicts several motes (sensor nodes) represented by green circles, with one node potentially being a sink or central node that makes multiple connections with other nodes. The area in green signifies the communication range of a node, and the lines between motes denote active communication links.
FIGURE 4
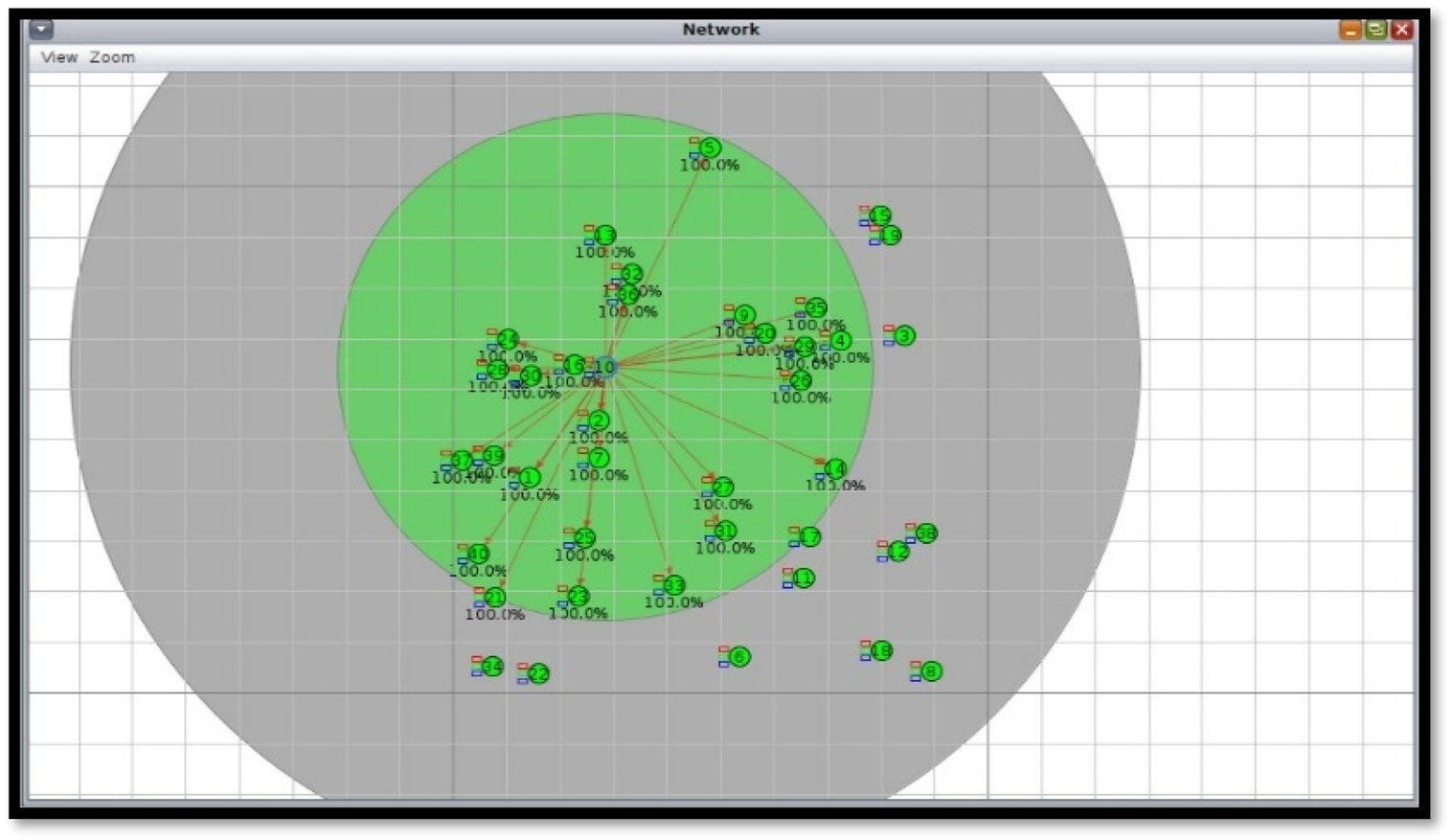
Cooja simulator view with 50 nodes.
FIGURE 5
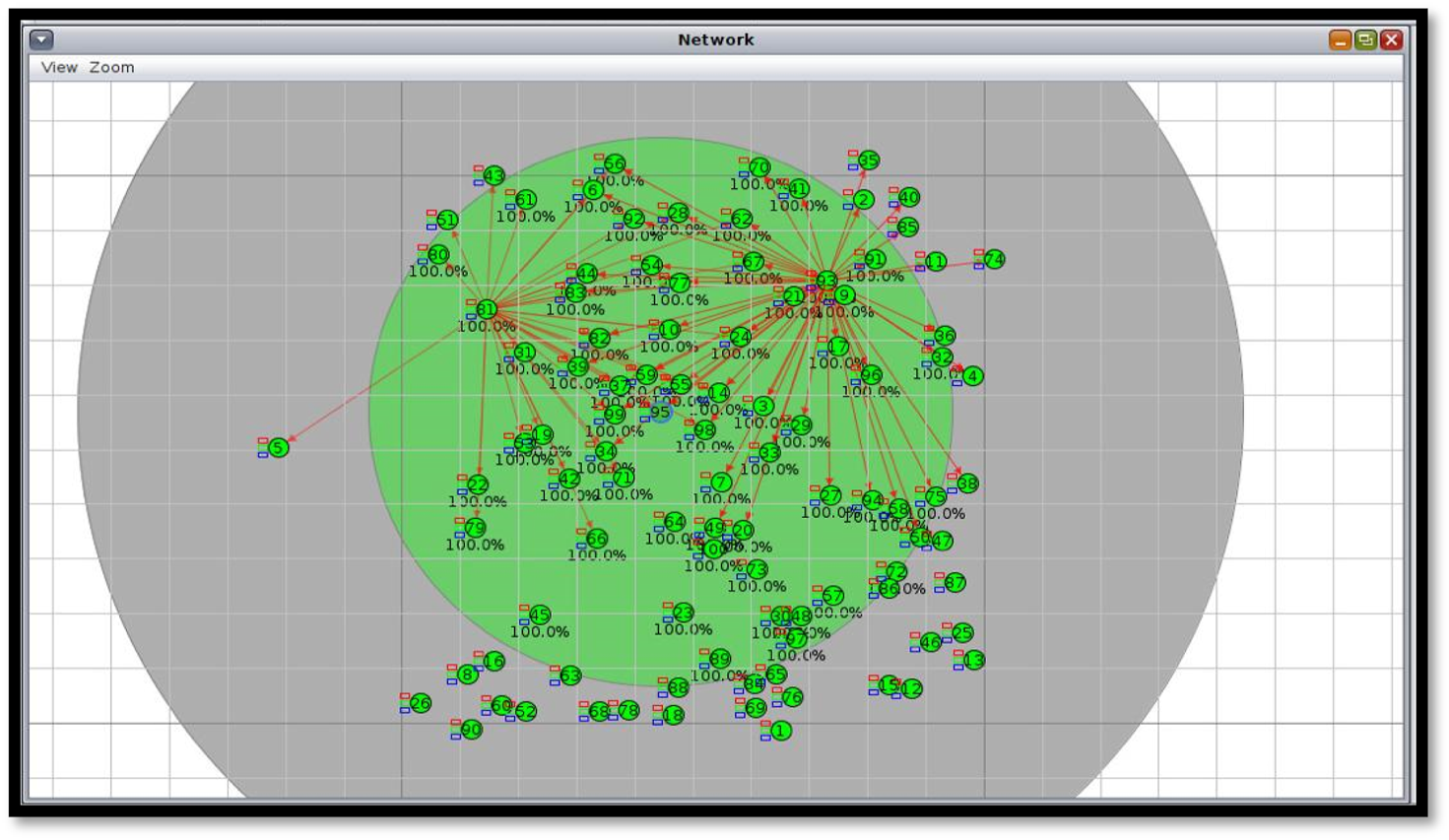
Cooja simulator view with 100 nodes.
Packet delivery ratio (PDR)
PDR is the ratio of total packets reached at the sink node from the source node.
Packet Delivery Ratio =
Packet loss ratio (PLR)
PLR is the total loss of packets from the entire packets delivered from CMs
End-to-end delay (ms)
The total amount of time taken for the packet transmission
The proposed SHEER algorithm is quite effective with regard to comparisons in performance with other algorithms such as PSO, GWO, and ALO (Nilsaz Dezfouli and Barati, 2020; Vellaichamy et al., 2023) in terms of PDR from Figure 6 and PLR from Figure 7. Figure 8 shows the energy consumed, and cluster stability is shown in Figure 9. Table 2 compares end-to-end delay with the proposed and existing approaches.
FIGURE 6
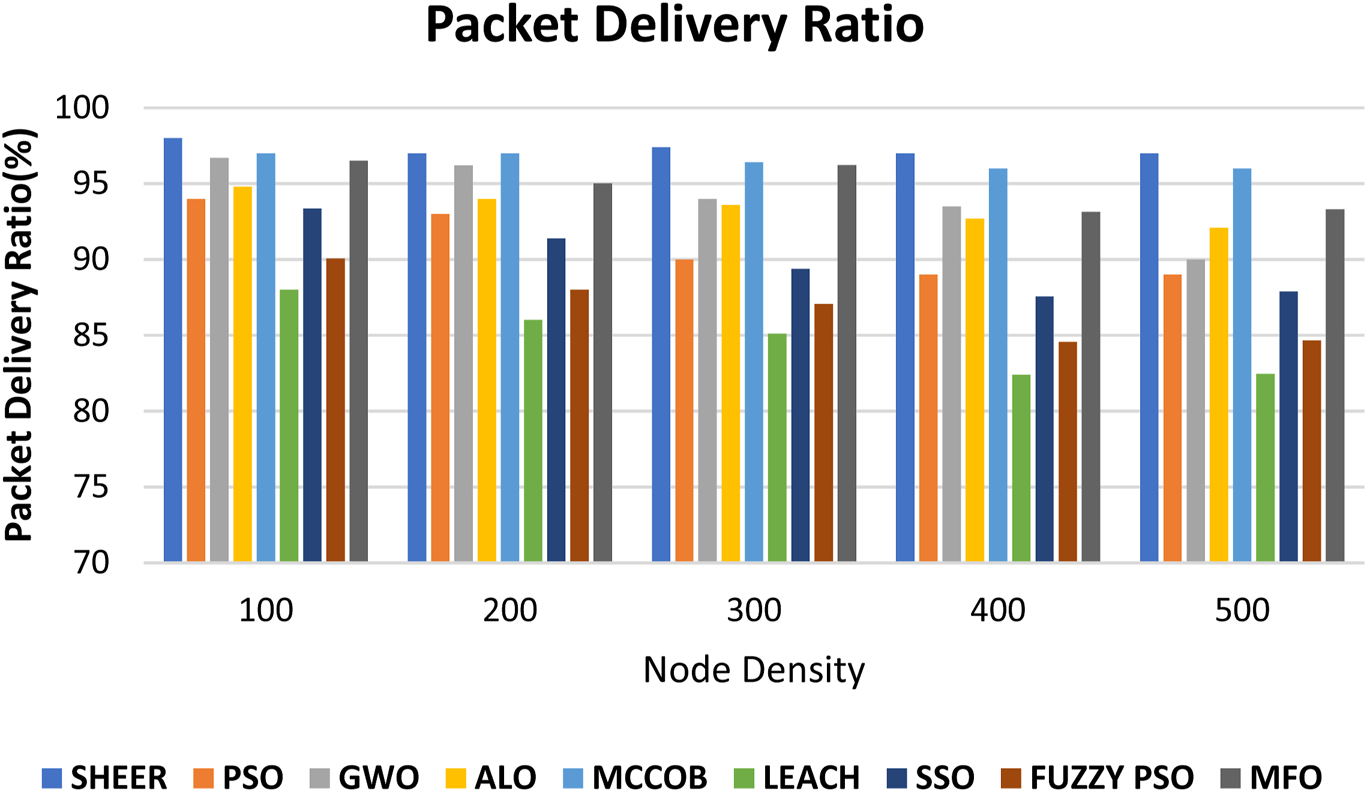
Packet delivery ratio.
FIGURE 7
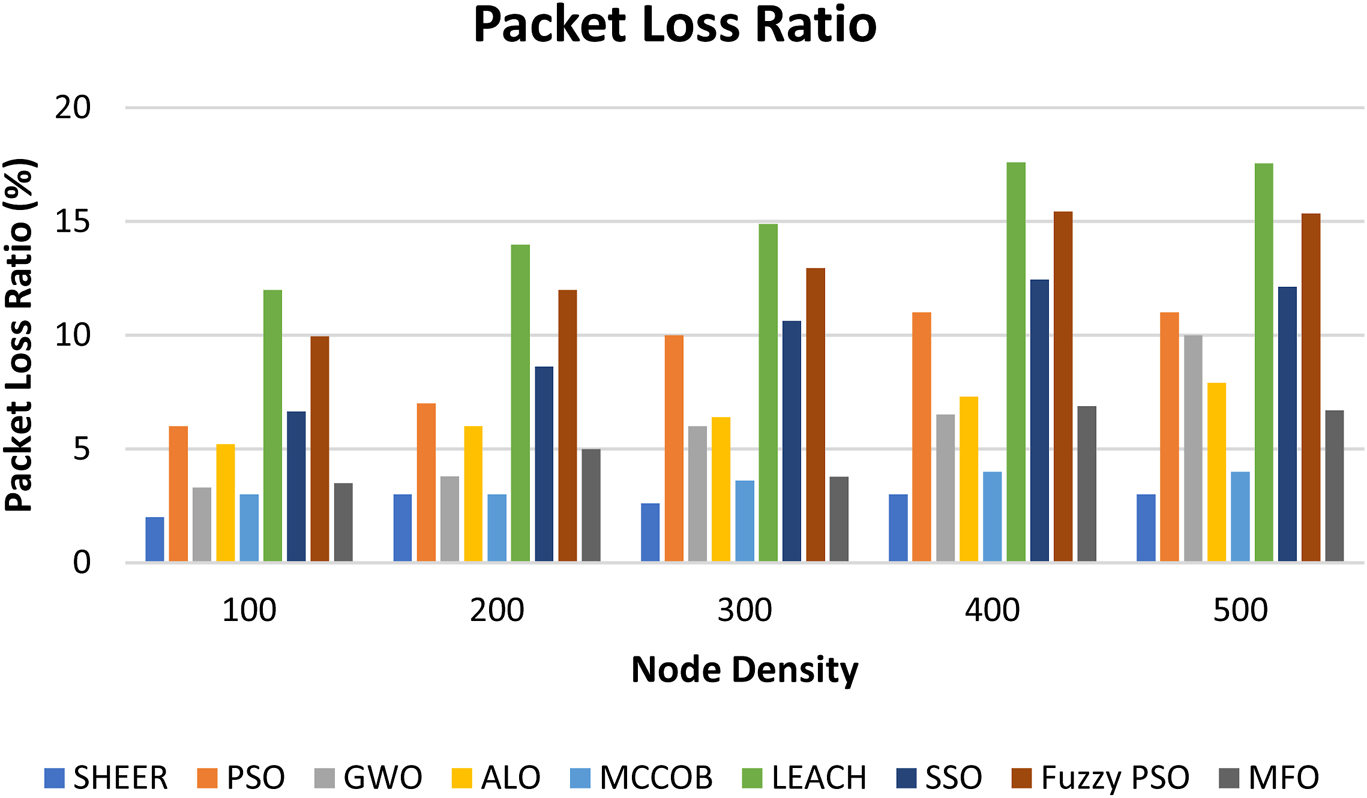
Packet loss ratio.
FIGURE 8
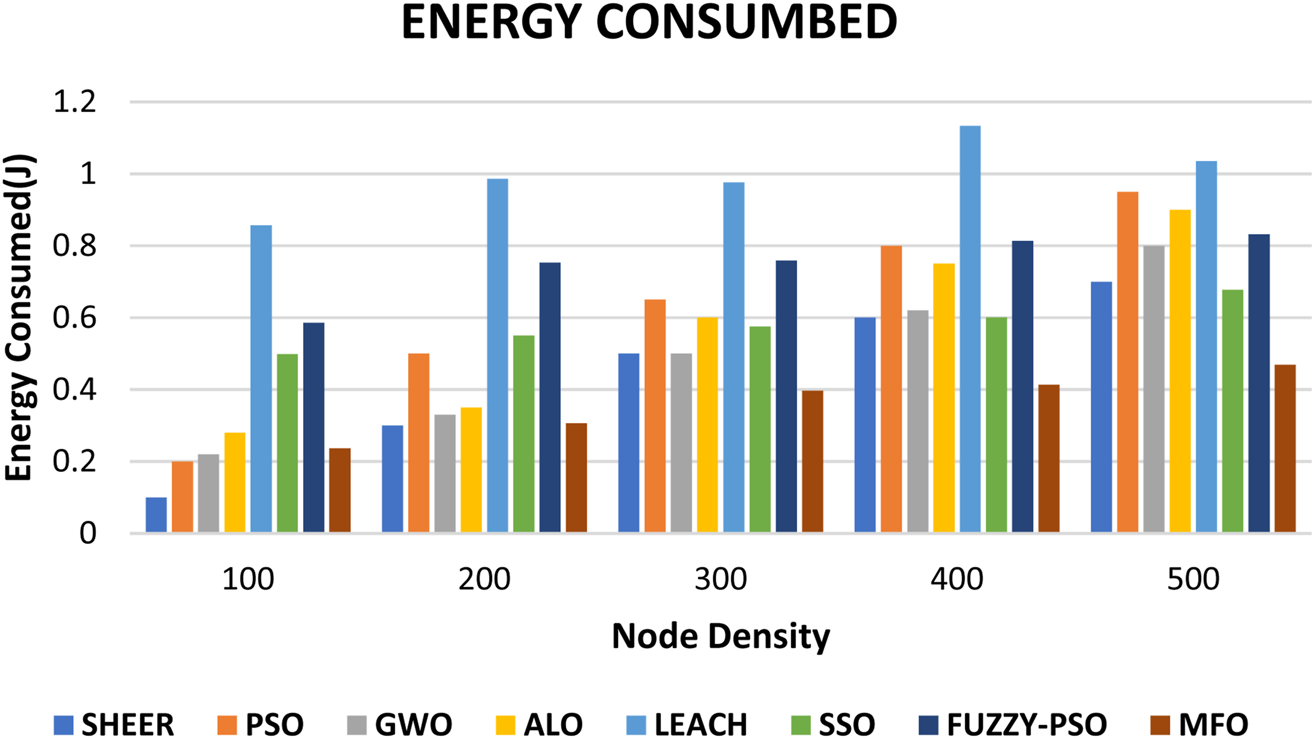
Energy consumed.
FIGURE 9
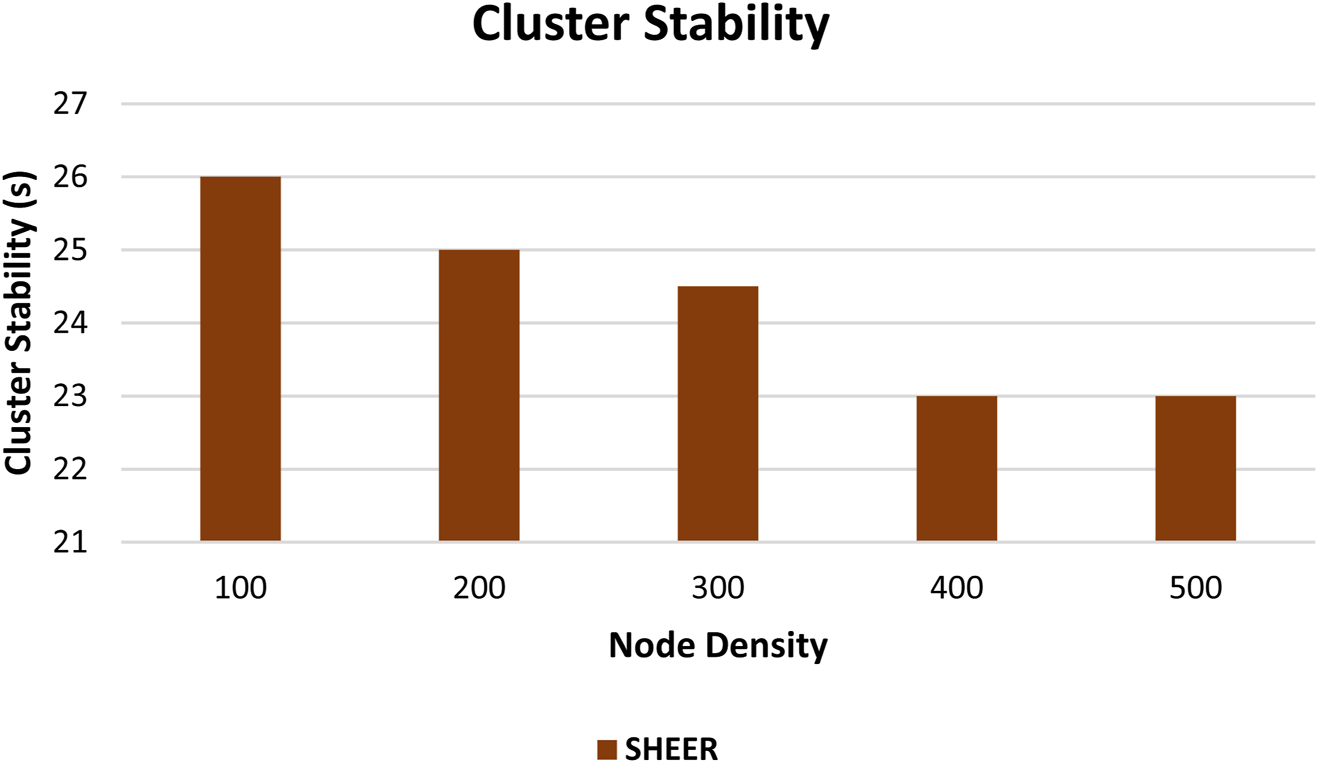
Cluster stability.
TABLE 2
| End-to-end delay (s) | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| Node density | SHEER | PSO | GWO | ALO | Mccob | LEACH | SSO | Fuzzy PSO | Mfo |
| 100 | 1.8 | 30 | 50 | 50 | 3.107 | 8.9 | 6.1 | 8.56 | 4.35 |
| 200 | 2 | 70 | 35 | 55 | 2.81 | 9.3 | 7.011 | 7.723 | 6.126 |
| 300 | 2.5 | 95 | 45 | 75 | 3.3 | 10.14 | 9.193 | 9.38 | 6.589 |
| 400 | 3 | 120 | 60 | 100 | 4.1 | 9.52 | 6.914 | 8.016 | 7.0275 |
| 500 | 4.3 | 125 | 80 | 130 | 5.06 | 13.99 | 10.11 | 13.0811 | 9.15 |
End-to-end delay.
As per the simulation, from 20 to 200 nodes, there are differences in energy used and stability based on the nodes of nodes simulating and according to the PDR value of all the simulated nodes. The cluster stability is defined as the amount of time the cluster remains stable. The cluster stability of 100, 200, 300, 400, and 500 nodes is 26 s, 25 s, 24.5 s, 23 s, and 23 s respectively, as shown in Figure 9. When communications are complete and the CH energy decreases, the other CH will be re-elected for the next communication.
Computational cost analysis is calculated based on the transmission of packets from the sensor source node to the sink node. The time that it takes to transmit one packet per second is 2.048 ms, and 50 packets per second take 102.4 ms. It takes approximately 102.4 ms to transmit 50 packets of 64 bytes at a data rate of 250 kbps.
The SHEER algorithm supports scalability in large-scale WSNs by incorporating several key mechanisms that ensure efficient performance as the number of sensor nodes increases. Specifically, the algorithm employs hierarchical clustering to reduce communication overhead by grouping nodes into clusters, with CHs handling inter-cluster communication. As the network size grows, the algorithm dynamically adjusts the CM distribution to maintain a balanced energy consumption across the network.
Moreover, the self-healing mechanism in SHEER plays a critical role in scalability by redistributing the roles of CHs and CMs in response to node failures, which helps maintain network stability and flexibility in large-scale scenarios. This dynamic reconfiguration ensures that the network remains resilient and energy-efficient even as the number of nodes increases. Additionally, the algorithm leverages energy-efficient routing and localized decision making to minimize communication costs and extend the lifetime of the network, making it capable of scaling to thousands of sensor nodes without any performance degradation.
5 Conclusion
Wireless sensor networks provide a way to manage smart cities. Their sensing and real-time decision making provide an optimal solution for various hazardous effects. Meanwhile, energy consumption and malfunctions in remote areas remain a critical challenge in implementing the WSN model in various sectors. The proposed model SHEER addresses this issue by providing an energy-efficient and self-healing mechanism to provide a sustainable WSN network. When it senses failure, the SHEER model automatically re-elects CHs dynamically. This minimizes the downtime of the network and its energy overhead, which improves the overall reliability of the system. Compared to existing protocols, the SHEER-based model performs better in achieving lower packet loss and higher cluster stability, with uninterrupted network operations devoid of interventions from outside. The SHEER approach achieves 98% PDR in all case scenarios, consistently outperforming these existing methods, thus indicating robustness in delivering reliable data transmission for WSN. The simulation results demonstrate the effectiveness of the proposed method, with improvements in PDR, energy efficiency, and E2E delay. Compared to existing optimization techniques, our method ensures a higher packet delivery ratio, lower energy consumption, and reduced delay due to its adaptive and self-healing nature. By analyzing and comparing performance metrics, it is evident that the SHEER clustering and the self-healing mechanism provide a more robust and efficient solution for WSNs, significantly enhancing network lifetime and reliability.
Future work will implement the proposed approach to check performance, and this algorithm will be extended to the agriculture Internet of Things to provide sustainable networking.
Statements
Data availability statement
The original contributions presented in the study are included in the article/supplementary material; further inquiries can be directed to the corresponding author.
Author contributions
GM: Investigation, Methodology, Software, Supervision, Validation, Writing – review and editing. VV: Conceptualization, Methodology, Software, Visualization, Writing – original draft.
Funding
The author(s) declare that no financial support was received for the research and/or publication of this article.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Generative AI statement
The author(s) declare that no Generative AI was used in the creation of this manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1
Akram M. Ullah Bazai S. Imran Ghafoor M. Akram S. Ilyas Q. M. Mehmood A. et al (2025). EEMLCR: energy-efficient machine learning-based clustering and routing for wireless sensor networks. IEEE Access13, 70849–70871. 10.1109/ACCESS.2025.3562368
2
Ali A. Ming Y. Chakraborty S. Iram S. (2017). A comprehensive survey on real-time applications of WSN. Future Internet9 (4), 77. 10.3390/fi9040077
3
Al-Karaki J. N. Kamal A. E. (2004). Routing techniques in wireless sensor networks: a survey. IEEE Wirel. Commun.11 (6), 6–28. 10.1109/mwc.2004.1368893
4
Alomari M. F. Mahmoud M. A. Ramli R. (2022). A systematic review on the energy efficiency of dynamic clustering in a heterogeneous environment of wireless sensor networks (WSNs). Electron. Switz.11 (18), 2837. 10.3390/electronics11182837
5
Alsheikh M. A. Lin S. Niyato D. Tan H. P. (2014). Machine learning in wireless sensor networks: algorithms, strategies, and applications. IEEE Commun. Surv. Tutorials16 (4), 1996–2018. 10.1109/COMST.2014.2320099
6
Cengiz K. Dag T. (2016). Improving energy-efficiency of WSNs through LEFCA. Int. J. Distributed Sens. Netw.12 (8), 8139401. 10.1177/155014778139401
7
Chehri A. Saadane R. Hakem N. Chaibi H. (2020). Enhancing energy efficiency of wireless sensor network for mining industry applications. Procedia Comput. Sci.176, 261–270. 10.1016/j.procs.2020.08.028
8
Gherbi C. Aliouat Z. Benmohammed M. (2016). An adaptive clustering approach to dynamic load balancing and energy efficiency in wireless sensor networks. Energy114, 647–662. 10.1016/j.energy.2016.08.012
9
Han H. Tang J. Jing Z. (2024). Wireless sensor network routing optimization based on improved ant colony algorithm in the Internet of Things. Heliyon10 (1), e23577. 10.1016/j.heliyon.2023.e23577
10
Jaladi A. R. Khithani K. Pawar P. Malvi K. Sahoo G. (2017). Environmental monitoring using wireless sensor networks (WSN) based on IOT. Int. Res. J. Eng. Technol. 4 (1), 1371–1378.
11
Janani S. Ramaswamy M. Samuel Manoharan J. (2016). Clustered heed-based data transfer strategy for cognitive radio sensor networks. ARPN J. Eng. Appl. Sci. 11 (21), 12631–12642.
12
Jiang H. Bai Y. Wang J. Wang X. Huang X. Dong X. et al (2024). A strain rate response and self-healing organohydrogel for use in impact-protective materials. Mater. Today Commun.41, 110591. 10.1016/j.mtcomm.2024.110591
13
Kandris D. Evangelakos E. A. Rountos D. Tselikis G. Anastasiadis E. (2023). LEACH-based hierarchical energy efficient routing in wireless sensor networks. AEU - Int. J. Electron. Commun.169 (March), 154758. 10.1016/j.aeue.2023.154758
14
Karakus C. Gurbuz A. C. Tavli B. (2013). Analysis of energy efficiency of compressive sensing in wireless sensor networks. IEEE Sensors J.13 (5), 1999–2008. 10.1109/JSEN.2013.2244036
15
Kaur S. Kour S. Singh M. (2025). Energy efficiency in wireless sensor networks: comparing traditional and advanced clustering protocols. Engineering Research Express.
16
Kulkarni R. V. Venayagamoorthy G. K. (2010). Particle swarm optimization in wireless-sensor networks: a brief survey. IEEE Trans. Syst. Man, Cybern. Part C Appl. Rev.41 (2), 262–267. 10.1109/tsmcc.2010.2054080
17
Kumar S. Kumar V. Kaiwartya O. Dohare U. Kumar N. Lloret J. (2019). Towards green communication in wireless sensor network: GA enabled distributed zone approach. Ad Hoc Netw.93, 101903. 10.1016/j.adhoc.2019.101903
18
Mukherjee P. Pattnaik P. K. Swain T. (2019). The criteria for the cluster selection for single hop and multi-hop based sensor-cloud environment. Int. J. Knowledge-Based Intelligent Eng. Syst.23 (1), 33–40. 10.3233/KES-190397
19
Nilsaz Dezfouli N. Barati H. (2020). A distributed energy-efficient approach for hole repair in wireless sensor networks. Wirel. Netw.26, 1839–1855. 10.1007/s11276-018-1867-0
20
Pantazis N. A. Nikolidakis S. A. Vergados D. D. (2013). Energy-efficient routing protocols in wireless sensor networks: a survey. IEEE Commun. Surv. Tutorials15 (2), 551–591. 10.1109/SURV.2012.062612.00084
21
Pathak M. (2013). An approach to memory management in wireless sensor networks. Int. J. Comput. Sci. and Eng. Technol.4 (8), 1171–qq76.
22
Prabhu Boselin M. Pradeep Gajendran E. (2016). “Military applications of wireless sensor network system,” in A Multidisciplinary Journal of Scientific Research & Education, 2 (12).
23
Rani S. Koundal D. Ijaz M. F. Elhoseny M. Alghamdi M. I. (2021). An optimized framework for WSN routing in the context of industry 4.0. Sensors Basel, Switz.21 (19), 6474–15. 10.3390/s21196474
24
Rault T. Bouabdallah A. Challal Y. (2014). Energy efficiency in wireless sensor networks: a top-down survey. Comput. Netw.67, 104–122. 10.1016/j.comnet.2014.03.027
25
Rehman A. Abdullah S. Fatima M. Iqbal M. W. Almarhabi K. A. Ashraf M. U. et al (2022). Ensuring security and energy efficiency of wireless sensor network by using blockchain. Appl. Sci. Switz.12 (21), 10794. 10.3390/app122110794
26
Saad M. A. Jaafar R. Chellappan K. (2025). Variable length multi-objective whale optimization for trust aware data gathering in wireless sensor network. IEEE Access13, 32100–32121. 10.1109/ACCESS.2025.3538276
27
Shyama M. Anju S. (2022). Pillai, Alagan Anpalagan,Self-healing and optimal fault tolerant routing in wireless sensor networks using genetical swarm optimization. Comput. Netw.217, 109359. 10.1016/j.comnet.2022.109359
28
Siddaramu S. M. Ramaswamy R. K. (2025). Optimal wireless sensor network ant-lifetime routing algorithm using multi-phase pheromone. Ing. Des. Syst. d’Information30 (1), 83–100. 10.18280/isi.300108
29
Singh A. K. Mishra S. K. Dixit S. (2019). Energy efficiency in wireless sensor networks: cooperative MIMO-OFDM. Lect. Notes Electr. Eng.524, 147–154. 10.1007/978-981-13-2685-1_16
30
Tennina S. Di Renzo M. Kartsakli E. Graziosi F. Lalos A. S. Antonopoulos A. et al (2014). WSN4QoL: a WSN-oriented healthcare system architecture. Int. J. Distributed Sens. Netw.2014, 503417. 10.1155/2014/503417
31
Vellaichamy J. Basheer S. Bai P. S. M. Khan M. Kumar Mathivanan S. Jayagopal P. et al (2023). Wireless sensor networks based on multi-criteria clustering and optimal bio-inspired algorithm for energy-efficient routing. Appl. Sci.13, 2801. 10.3390/app13052801
32
Wei D. Jin Y. Vural S. Moessner K. Tafazolli R. (2011). An energy-efficient clustering solution for wireless sensor networks. IEEE Trans. Wirel. Commun.10 (11), 3973–3983. 10.1109/TWC.2011.092011.110717
33
Zagrouba R. Kardi A. (2021). Comparative study of energy efficient routing techniques in wireless sensor networks. Inf. Switz.12 (1), 42–28. 10.3390/info12010042
Summary
Keywords
SHEER algorithm, cluster head selection, energy efficiency, network stability, self-healing mechanism
Citation
Gayathri M and Veera Snigdha V (2025) Self-healing and energy-efficient cluster-based routing for sustainable wireless sensor networks. Front. Commun. Netw. 6:1602928. doi: 10.3389/frcmn.2025.1602928
Received
30 March 2025
Accepted
29 May 2025
Published
03 July 2025
Volume
6 - 2025
Edited by
Faraz Hasan, Massey University, New Zealand
Reviewed by
Saeed Ur Rehman, Flinders University, Australia
Yawar Abbas Bangash, Sunway University, Malaysia
Updates
Copyright
© 2025 Gayathri M and Veera Snigdha.
This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Gayathri M, m_gayathri@ch.amrita.edu
Disclaimer
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.