- 1Department of International Relations, University of Muhammadiyah Malang, Malang, Indonesia
- 2Department of Management, University of Muhammadiyah Malang, Malang, Indonesia
- 3Department of Government Studies, University of Muhammadiyah Malang, Malang, Indonesia
Social Media and Terrorism are often studied together and have become the focus of many authors in recent years. Therefore, this study aims to evaluate international publication trends on social media and terrorism, using the Scopus database through bibliometric analysis from 2009 to 2022. Data visualization and analysis were conducted using Microsoft Excel and VOSviewer. The results showed that the international publications trend reached a peak in 2018, with 103 publications emphasizing various topics, such as social media, terrorism, Twitter, terrorist attacks, and several issues related to terrorist activities and digital platforms. The United States was also the most common country of publication with the highest number of affiliated authors. In addition, the authors with the most published documents were Tsikrika T. and Vrochidis S., with the majority of reports prioritizing social sciences. These results are expected to contribute to the novelty of previous studies on social media and terrorism.
Introduction
Social media and terrorism are recently the focus of study for authors in several countries (Mussiraliyeva et al., 2020). Besides being interconnected, these topics also emphasize the development of increasingly sophisticated information and communication technology in the modern and globalized era (Almoqbel and Xu, 2019). From this context, the globalization era is the starting point for significant changes in the life of traditional society, regarding the development of a modern community with sophisticated technology (Tantray and Vishwavidyalya, 2021). In modern society, technology is diverse and originates from various fields, such as the industrial (Groumpos, 2021) and transportation (Chami, 2021) sectors. This diverse element is found to be continuously developing in other fields, to improve human life (Shilling and Mellor, 2017). In this case, the development of information and communication technology is one field playing a significant role in the lives of people during the modern era (Kumari, 2019; Omotosho, 2019), facilitating efficient and fast communication and sharing of information (Bibi et al., 2017). It also leads to the establishment of social media platforms, which commonly provides a range of benefits and functions (Giri and Vats, 2019).
Social media is a platform with an internet network, which allows people to connect with others or groups, toward sharing information and communicating about specific topics (Kaati et al., 2016). This is a technology that allows several people to communicate, share information and opinions, as well as portray specific expressions through a globally interconnected community or network (Abbas et al., 2022). It is also aa site for expressing various opinions regarding an event, information, product, etc. (Tran and Tran, 2018). These definitions highlight the diverse functions of social media (Xu et al., 2018), enabling people to stay connected despite the geographical distance (Royo-Vela and McBee, 2020). The technology is also capable of providing information about an event in a country, for the global awareness of other nations (Zhu et al., 2020). Therefore, social media prioritizes prompt, unlimited, as well as efficient communication and information sharing (Sanri and Goodwin, 2014).
The negative impacts of social media are also emphasized regardless of the positive features exhibited (Caton and Landman, 2022). For instance, hoaxes, hate speech, fraud and crime have become the new methods of propaganda and recruiting potential terrorists (Smith et al., 2018; Jamil et al., 2022). According to the data from The Ministry of Communication and Information of Indonesia (2018), the government blocked 10,499 pieces of content containing radicalism and terrorism in the country. This included 7,160, 1,316, 677, 502, 502, and 292 pieces of content on Facebook/Instagram, Twitter, YouTube, Telegram, file-sharing platforms, and websites, respectively. From this context, social media is used to communicate and share unlimited information about specific topics (Gaikwad et al., 2022). This explains that the perpetrators of extremism often misuse the technology to spread radical ideologies (Mugari, 2020), leading to a concern for the global community. In this case, terrorism is observed as an international threat negatively impacting foreign security and causing the destruction of life (Dwiwarno, 2018; Subagyo, 2021). Social media platforms such as Facebook and Twitter are also frequently implemented to quickly spread terrorism information (Tundis et al., 2019), leading to public awareness (Gialampoukidis et al., 2017a).
Based on several previous reports, a positive relationship was observed between social media usage and terrorism, specifically on Facebook, which was used for sharing extremism information (Asongu et al., 2019). The function of social media was also misused to spread radical ideology and other extreme content (Jain and Vaidya, 2021). Moreover, the technology development allowed Asia-Pacific extremist groups, such as Abu Sayyaf in the Philippines, to carry out propaganda, spread radical ideas, recruit members, and perform fundraising (Schreer and Tan, 2019). In some previous studies, various experimental emphases were prioritized, including the relationship between social media and terrorism and the function of the technological development for terrorist groups. However, a limited comprehensive understanding of social media and terrorism was observed, specifically its trends and scientific structures.
In an attempt to fill gaps in existing studies, this study aims to evaluate international publication trends on social media and terrorism, using the Scopus database through bibliometric analysis from 2009 to 2022. It aims to analyze the scientific production per year, the most author, affiliations, and countries contribution, research areas, funding information, and the theme cluster using co-occurrence. As a first step, the researchers created the following research questions (RQs);
RQ 1 What are the trends in international publications on the study of social media and terrorism?
RQ 2 What are the critical themes related social media and terrorism in the scientific literature?
Literature review
Bibliometric analysis
Bibliometric analysis is a widely used analytical method in present experimentation conditions (Mukherjee et al., 2022). In this analysis, several statistical methods are often initially applied to analyze the books published on a specific topic (Leung et al., 2017). The implementation of the analytical method has also increased with time, regarding its application in various fields, including economics and business (Wang et al., 2020; Donthu et al., 2021), health (Berta et al., 2022), technology (Cobo et al., 2018), social sciences (Carammia, 2022), political issues (Subekti et al., 2022; Congge et al., 2023), urban studies (Sulistyaningsih et al., 2023), public administration (Roziqin et al., 2022), etc.
The method is valuable for analyzing broad and open-ended topics with large data (Chaudhari and Pawar, 2021). This shows that the implementation of the method often involves large data and more than 100 documents (Kalantari et al., 2017), which are often obtained from Web of Science (WoS) and Scopus databases (Gaikwad et al., 2021). In addition, the use of bibliometric analysis method is able to help various scholars analyze the recent developments on a specific topic (Vujković et al., 2022).
Based on this analysis, the visualization of several outputs is often enabled and easily understood through various tools, such as VOSviewer. By applying this tool, data mapping is used to evaluate various trends in specific fields, including the number of yearly reports, the country with the highest published articles, the most prolific authors, the greatest funding affiliations and sponsors, as well as largest common types and fields of publication (Donthu et al., 2021). Moreover, several studies focusing on terrorism through bibliometric approaches included Mumtaz and Sultan (2011), which analyzed violent extremism from 1981 to 1990, regarding the Social Science Citation Index database (Web of Science). Klona and Menzies (2021) also evaluated terrorism within the scope of business studies, with Loan (2018) emphasizing the events of India and Pakistan.
Social media and terrorism
The impact of social media on daily lifestyles is very substantial, due to its proliferation ushering in a new era of communication since 2017. This was because the technological development has replaced television and newspapers as primary information sources for people (Ogunsuyi Opeyemi and Adebola, 2022). Despite its positive effects, the development of new Internet technology still pose information and communication dangers to consumers (Fedushko and Benova, 2019). Social networking platforms are also ideal for developing a virtual environment, where people are able to share their thoughts, ideas, and daily activities through text, photographs, and videos. From this context, social media users are capable of inciting self-harm or public pain through the publication of some controversial issues, without solid and good self-control (Fkih and Al-Turaif, 2023). This condition has recently led to various considerations from the global community, regarding the problems of social media and terrorism (Mohd et al., 2019). In this case, several studies have been conducted on the intersection of these phenomena in various countries (Scrivens et al., 2020). This is due to the criminal nature of terrorism, which globally threatens the security of every country (Kolajo and Daramola, 2017). In this case, vigilance is highly essential, specifically in the increasing sophistication of information and communication technology. Therefore, the digital age and the proliferation of social media platforms have facilitated the emergence of cyberterrorism (Odhiambo et al., 2018).
Cyberterrorism is the use of internet facilities, including social media, to carry out intense terrorist activities (Wilson, 2019). This indicates that several terrorist groups have used social media to globally locate and recruit new members (Combs, 2022), conduct propaganda, prepare logistics and funding, as well as commit hacking crimes (Winter et al., 2020). Social media has also facilitated the dissemination of information about terrorist incidents in various countries (Hatta et al., 2018). Based on various reports, the ISIS and Al Qaeda groups were among the most active and popular terrorist networks using the technology to spread their propaganda (Goyal et al., 2019). The groups also had a strong offline presence and a new generation of tech-savvy followers. Understanding the patterns by which terrorists use social media is capable of informing policy decisions about developed counter-terrorism programs, which need to emphasize the cyber security elements heavily implemented by extremist groups (Ogunlana, 2019). Governments and related parties should also develop various programs related to social network analysis, speech recognition, as well as face and object detection, to facilitate the early determination of digital terror threats (Naqvi et al., 2019).
Materials and methods
Data sources and search strategy
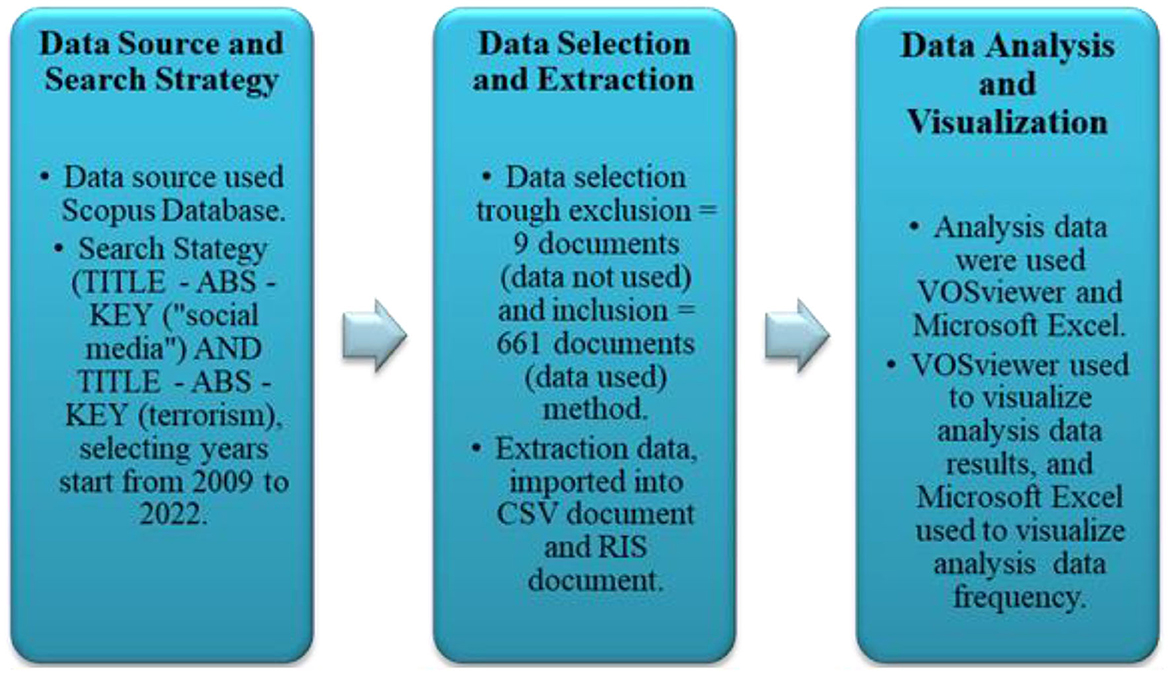
Figure 1 explains that the bibliometric data was obtained through the Scopus database, which was conducted in December 2022 using the TITLE—ABS—KEY (social media and terrorism) method. Since data were not limited to languages or regions, global search outputs and information were obtained. In this study, the specified period was from 2009 to 2022, to determine the publication trends on social media and terrorism.
Data selection and extraction
A total of 670 international published documents on social media and terrorism were obtained through the Scopus database from 2009 to 2022. Using exclusion and inclusion methods (Aroyewun et al., 2022), these documents were reduced to 660 publications, which met the study criteria. In this case, 10 of the initially published documents were excluded due to a lack of information on the authors. This led to the repetitive collection of the exclusion and inclusion-based publications, which were then converted into CSV (Comma Separated Values) and RIS (Research Information System) formats, to serve as analytical data (Shoaib et al., 2022). These data were used for analytical visualization regarding the international publication trend on social media and terrorism, as depicted in Figure 1.
Data analysis and visualization
Data analysis was a crucial aspect of the study, which involved observing, assessing, understanding, analyzing, and interpreting the outputs from the information collection stage. This indicated that data were obtained through the Scopus database and reduced through the exclusion and inclusion methods, with the outputs converted into CSV and RIS formats. VOSviewer and Microsoft Excel were also used to facilitate the data analysis process, accompanied by the visualization of outputs through previously obtained CSV and RIS information. These information were analyzed by grouping the published documents from 2009 to 2022, leading to several classifications regarding various factors, such as the authors, affiliations, funding sponsors, field of study, type of publication, and other relevant information.
Results
International published documents on social media and terrorism by year
Social media and terrorism were interconnected topics garnering attention from the general public and authors, as shown in Figure 2. Based on the international publication frequency on social media and terrorism, a consistent increase was observed in several related documents from 2009 to 2018. However, a decrease was found in these documents from 2019 to 2022.
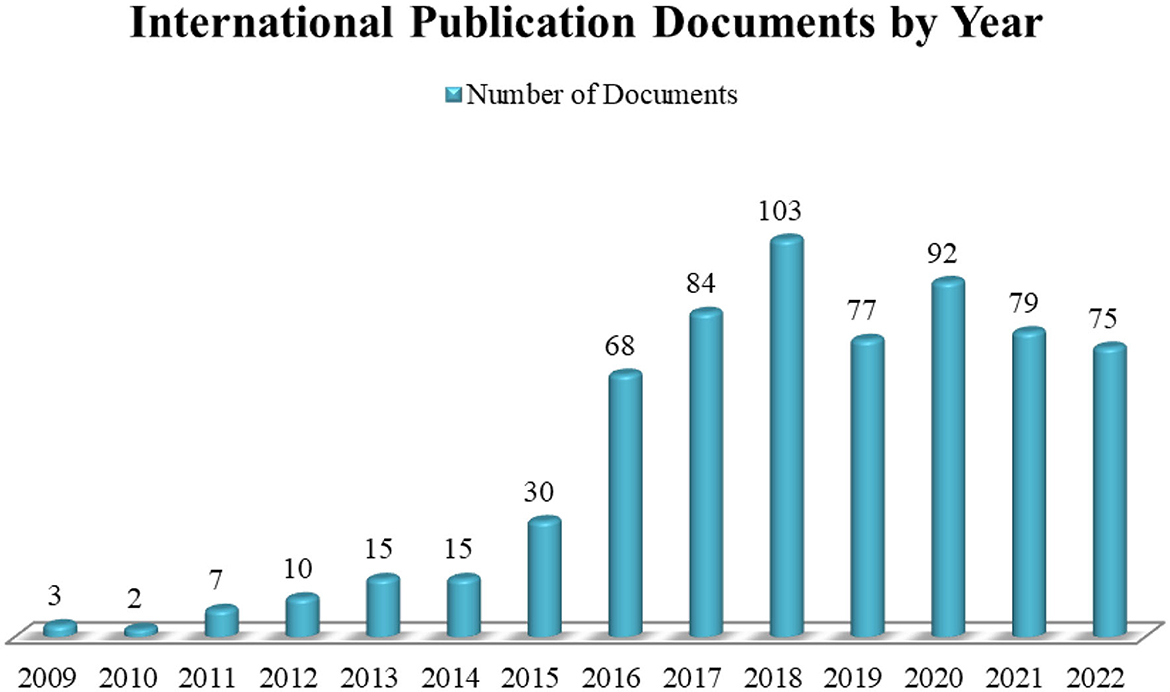
Figure 2. Published documents on social media and terrorism by year. Source: Author analysis from Scopus (2022) database.
The trend of international publications on social media and terrorism was initiated in 2009 with only three published documents. These documents emphasized the issues related to communication crises, as well as the development of the information and interaction technology enabling the occurrence of digital crimes, such as terrorist activities. In 2010, the documents decreased to two, the lowest number of publications among the periods included in this study. These publications emphasized the use of social media for communication and sharing information about terrorism. Moreover, a sentiment analysis was used to identify public bias on social media content (Petrushka et al., 2020). This showed that the number of published documents increased in 2011, prioritizing the challenges posed by digital terrorism activities. In 2012, the documents increased to 10, with the topics emphasizing terrorist events on social media (Bernardi et al., 2012; Cheong and Lundry, 2012; Lemieux and Boyle, 2012; Waskiewicz, 2012). In 2013 and 2014, these publications subsequently increased with 15 each, regarding anti-terrorism activities (Sandoval, 2012; Lee, 2013; Staniforth and Nitsch, 2013) and the role of social media in sharing terrorist information (Burnap et al., 2014; Cheong, 2014; Holman et al., 2014; Simon et al., 2014).
The published documents increased to 30 in 2015, focusing on the use of Twitter in terrorism (Chatfield et al., 2015; Sutton et al., 2015; Trang et al., 2015; Wei et al., 2015). In 2016, these documents increased to 68, encompassing several topics related to social media and terrorism. These topics included the strategies to combat terrorism (Aistrope, 2016), information extremism incidents (Brajawidagda et al., 2016), and the use of social media by terrorists, to expand their global influence (Weimann, 2016). Furthermore, the number of published documents improved to 84 in 2017, based on detecting and combating terrorism on social media platforms, such as Twitter (Debnath et al., 2017; Gialampoukidis et al., 2017a,b; Sraieb-Koepp, 2017). In 2018, these documents reached 103, the highest level among the 660 publications included in this study. This emphasized various aspects of social media and terrorism, such as the use of Twitter in terrorist activities (Barbe et al., 2018; Cvetojevic and Hochmair, 2018; Steensen, 2018). However, the publication rate decreased to 77 in 2019, with most of them prioritizing terrorist activities on social media platforms, such as Twitter (Abrar et al., 2019; Albadi et al., 2019; Fakhrurroja et al., 2019; Moussaoui et al., 2019).
In 2020, the publications slightly increased to 92, focusing on the conditions and activities of terrorism during the COVID-19 pandemic (Basit, 2020; Machitidze, 2020). These published documents then decreased to 79 and 75 in 2021 and 2022, encompassing the propaganda carried out by terrorists on social media (Pashentsev and Bazarkina, 2021; Kruglova, 2022). Based on these descriptions, the yearly elevation of the international publications on social media and terrorism demonstrated the interest and focus of the authors on this topic. This indicated that the publication rate declined when the authors were not specifically interested in studying the use of social media by terrorists. Meanwhile, the documents correspondingly increased when a high level of interest was observed among the authors. This is due to the increasingly widespread use of information and communication technology in terrorism and radicalism, especially social media.
International published documents on social media and terrorism by distribution country
In this study, understanding the distribution of published documents among different countries was essential, to identify those with the highest activity levels in producing social media and terrorism publications, as shown in Figure 3. The visualization of this data was also carried out by using the VOSviewer tool. Based on the results, the United States had the highest number of published documents on social media and terrorism, totaling 200 of the 660 publications being analyzed.
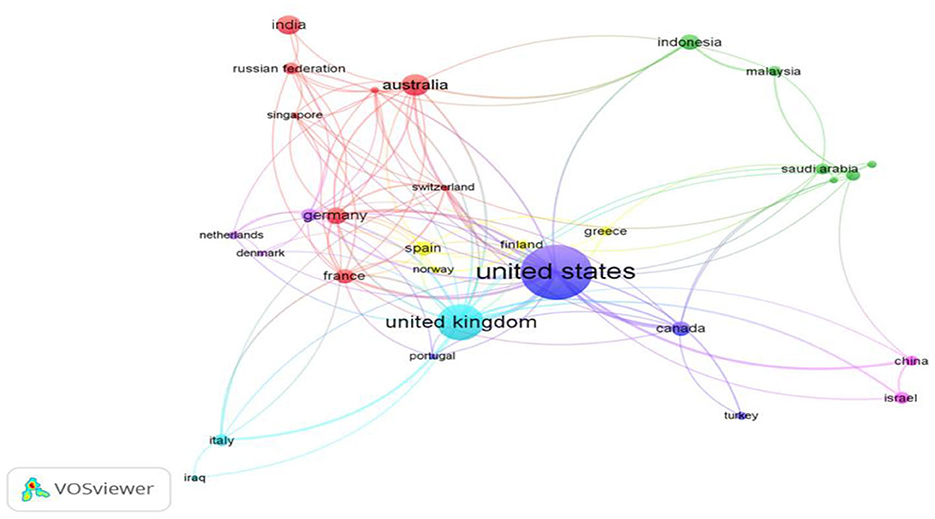
Figure 3. Published documents on social media and terrorism by country or territory distribution. Source: Author analysis from VOSviewer.
The United Kingdom was the next most significant contributor with 102 documents, accompanied by Australia, India, Germany, Indonesia, Spain/Canada, and France at 44, 36, 28, 26, 23, and 22 publications, respectively, as shown in Table 1.
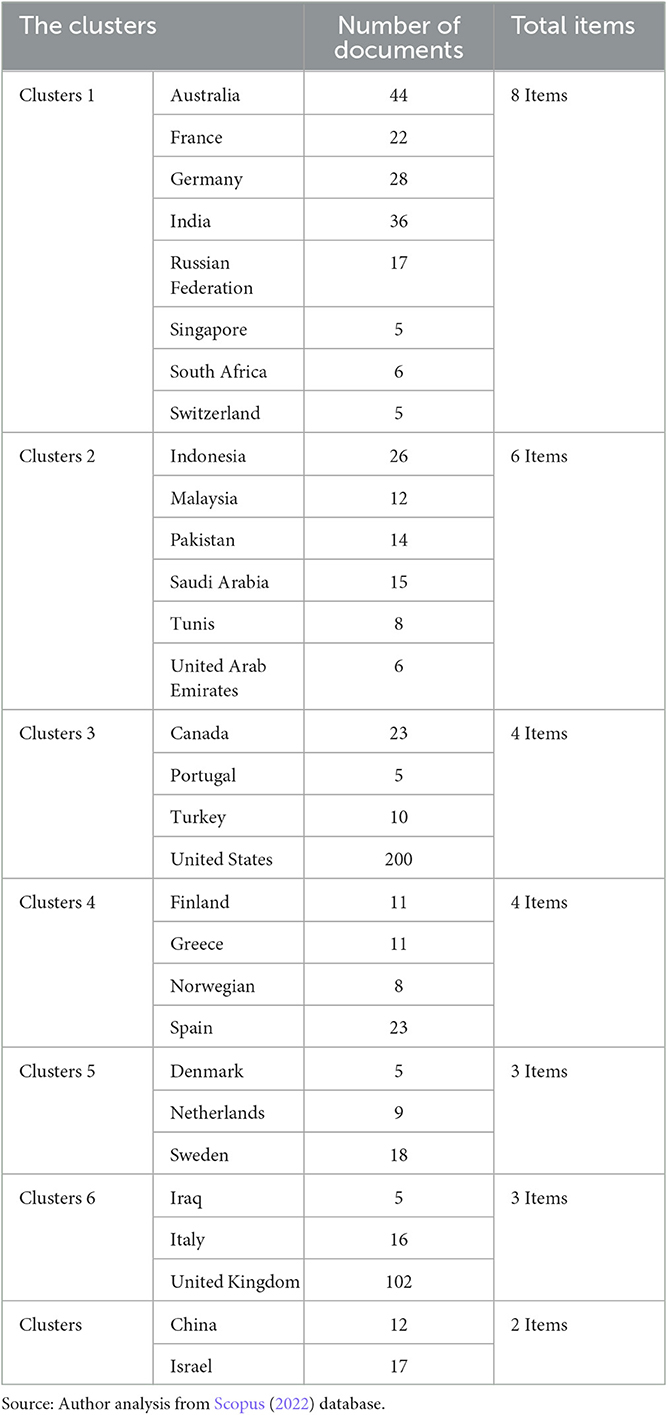
Table 1. Cluster items by country or territory distribution of published documents on social media and terrorism.
International published documents on social media and terrorism by authors and affiliations
The identification of authors and their affiliations was always crucial in any academic analysis. In this study, 660 published documents on social media and terrorism were analyzed, each of which had at least one author. To determine the authors with the most publications, a VOSviewer software was implemented, as depicted in Figure 4.
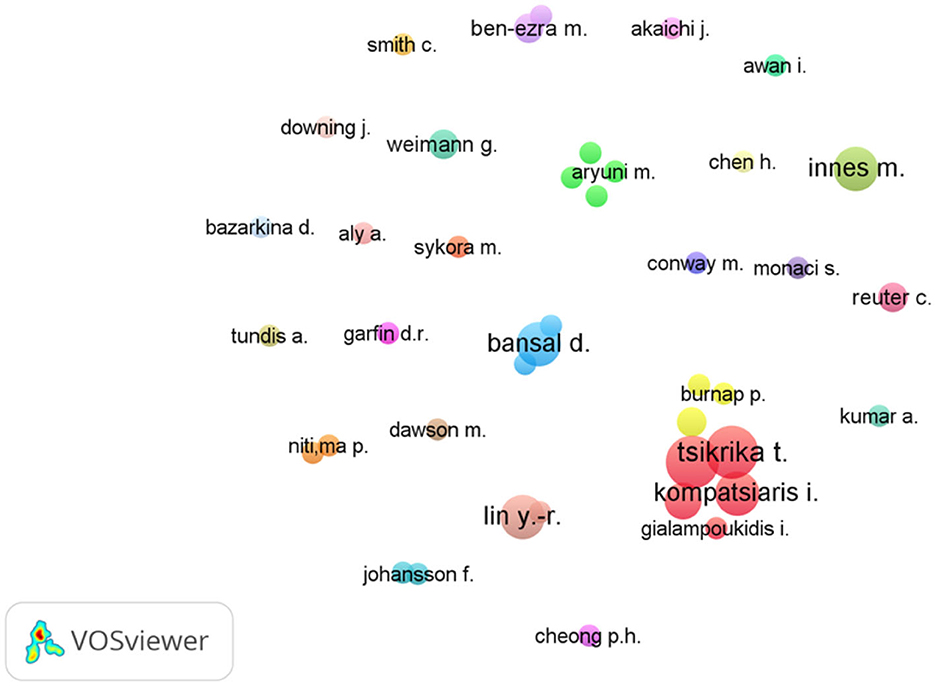
Figure 4. Published documents on social media and terrorism by author. Source: Author analysis from VOSviewer.
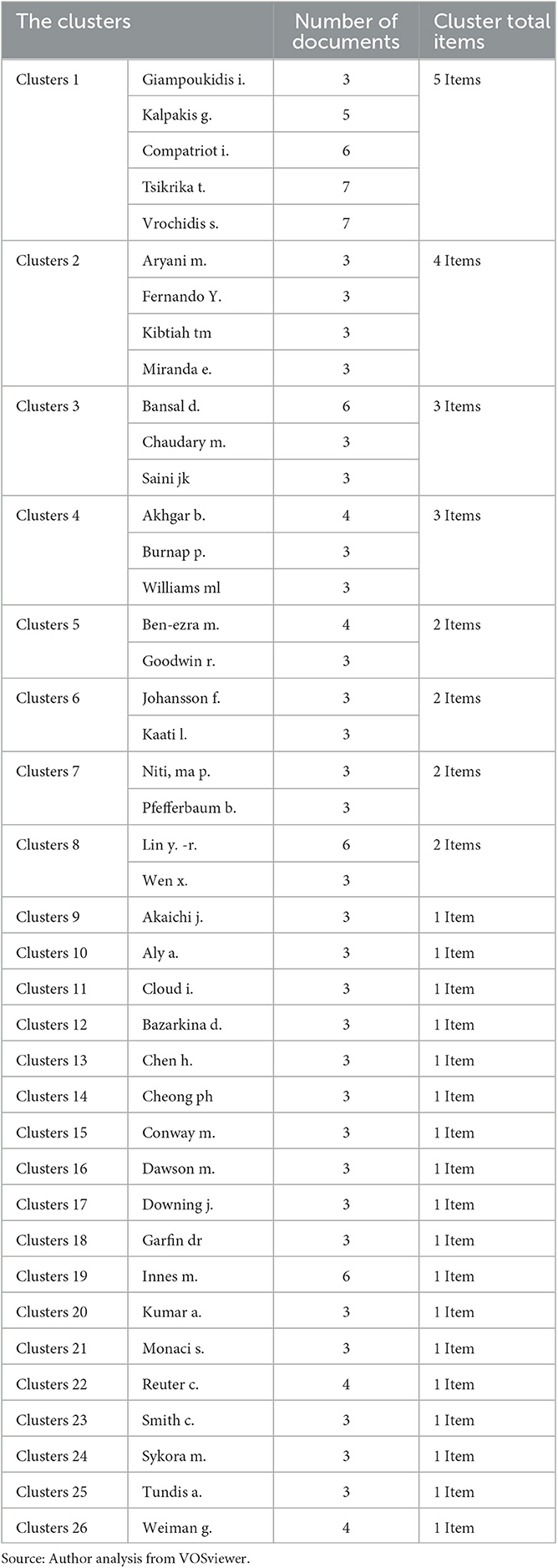
In this study, data visualization techniques were employed to identify the authors with the highest publications on social media and terrorism (Tsikrika et al., 2017). Based on the results, 41 authors were identified with international documents on this topic and divided into 26 groups, as depicted in Table 2. This indicated that Theodora Tsikrika and Stefanos Vrochidis had the highest number of published documents at six articles each, while other authors only had four or three publications.
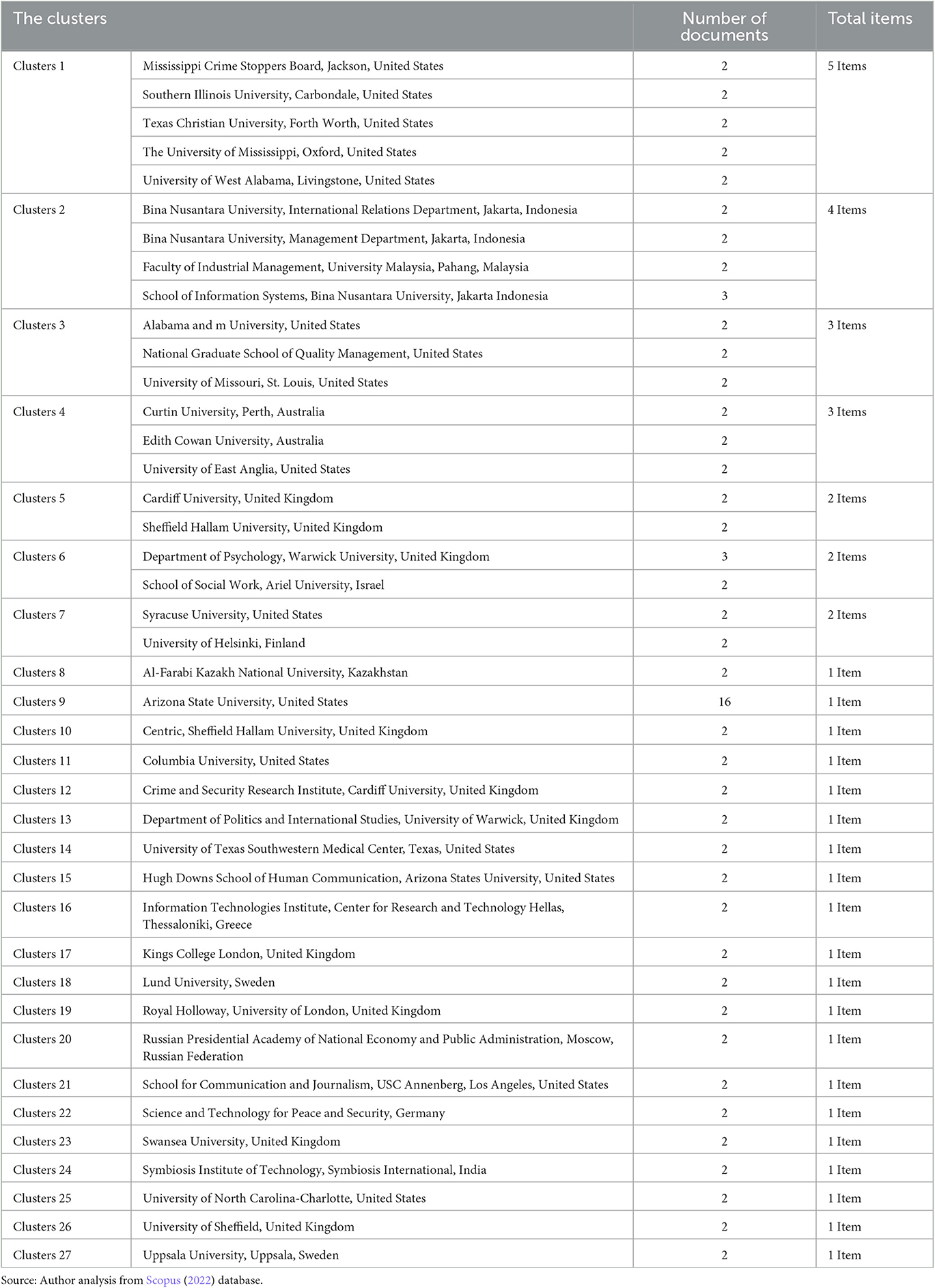
Tsikrika and Vrochidis were scholars at the Information Technologies Institute, CERTH, Greece, specializing in security studies and ICT (information and communication technology), with their works including social media and terrorism analyses. Besides examining the authors of published documents, their affiliations were also observed. Using VOSviewer (Figure 5), Arizona State University had the most prominent data visualization, with 16 published documents on social media and terrorism. The School of Information Systems, as well as Bina Nusantara and Warwick (Department of Psychology) Universities also had many publications, with three each. These three institutions had the highest number of documents among all the affiliates, as shown in Table 3. Meanwhile, other affiliates had only two published documents.
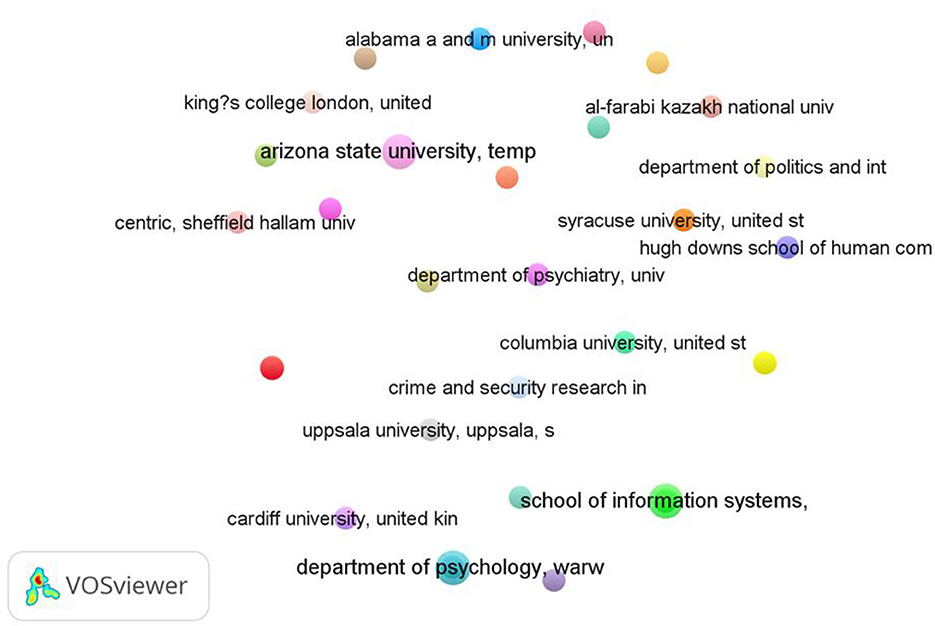
Figure 5. Published documents on social media and terrorism by affiliations. Source: Author analysis from VOSviewer.
International published documents on social media and terrorism by type and subject area
In this study, the types of research and knowledge fields represented in international publications on social media and terrorism were analyzed. Based on Figure 6, the articles comprising 52.70% or 348 published documents were highly common. This was accompanied by conference papers, book chapters, reviews, books, notes, editorials, conference reviews, letters, short surveys, and others at 21.80% (144 documents), 10.30% (68 publications), 5.20% (34 articles), 3.70% (24 documents), 2.10% (14 publications), 1.80% (12 articles), 1.00% (7 documents), 0.70% (5 publications), 0.40% (3 articles), and 0.10% or (1 document), respectively.
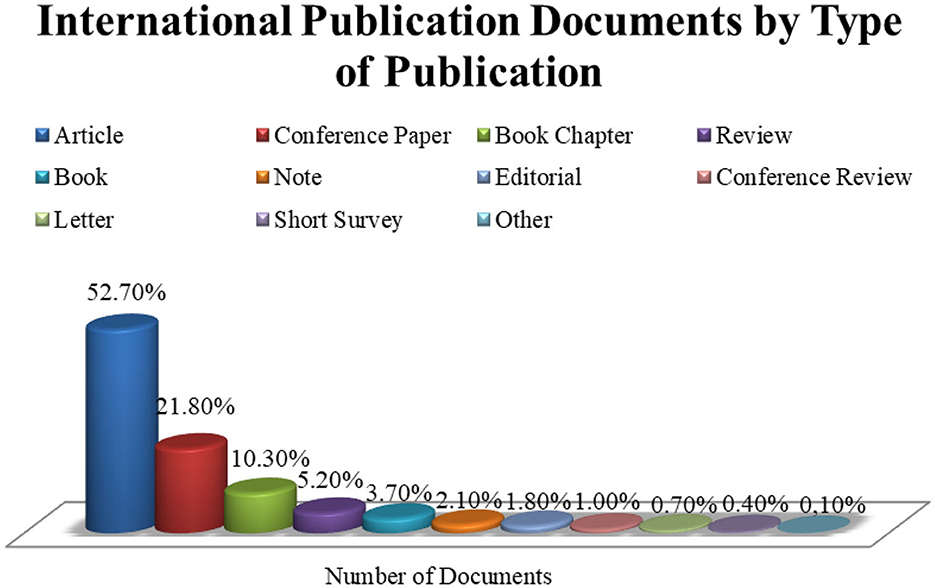
Figure 6. Published documents on social media and terrorism by type of publication. Source: Author analysis from Scopus (2022) database.
Figure 7 shows the visualization for the fields with the most published documents on social media and terrorism. These data indicated that the social sciences had the highest value of published documents, with 31.10% or ~206 publications. Other disciplines with a relatively high number of documents included computer sciences, engineering, medicine, arts and humanities, decision science, psychology, mathematics, business and management, economics, and other fields, at 20.70% (137 documents), 10.70% (71 publications), 7.30% (48 articles), 6.10% (40 documents), 4.10% (40 publications), 4.00% (27 articles), 3.70% (26 documents), 2.80% (25 publication), 1.50% (9 articles), and 8.00% (52 documents), respectively.
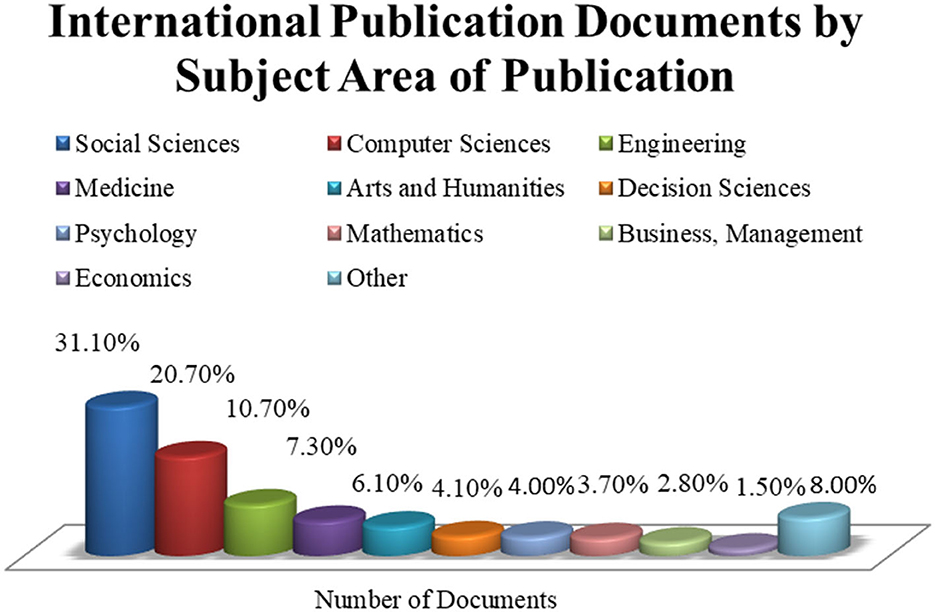
Figure 7. Published documents on social media and terrorism by subject area of publication. Source: Author analysis from Scopus (2022) database.
International published documents on social media and terrorism by funding sponsor
The Scopus database was used to identify the sponsoring agencies that funded publications on social media and terrorism. These funding institutions were observed through Microsoft Excel and visualized in Figure 8.
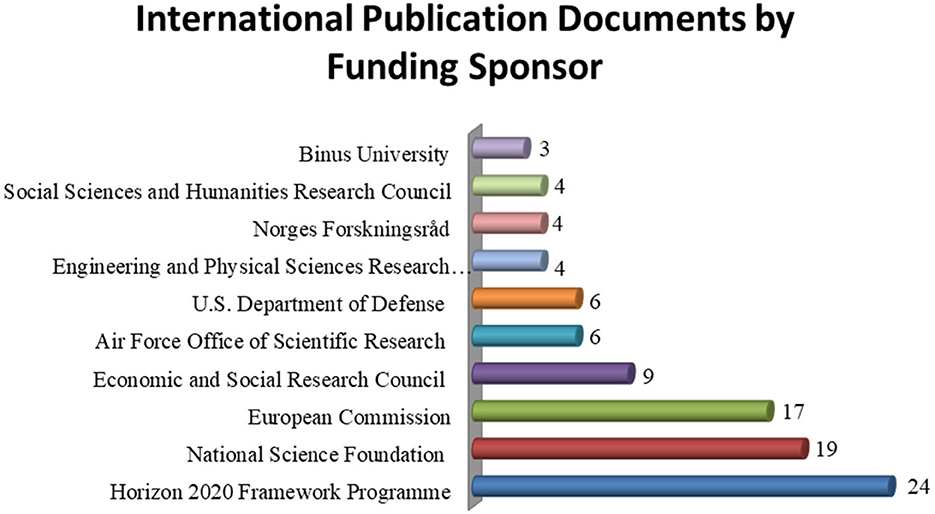
Figure 8. Published documents on social media and terrorism by funding sponsor of publication. Source: Author analysis from Scopus (2022) database.
Based on Figure 8, the highest funding sponsor for social media and terrorism publications was the Horizon 2020 Framework Program (Downing and Dron, 2022), which funded 24 documents. This was accompanied by the National Science Foundation (NSF) (Wormwood et al., 2019) and the European Commission (Jamil et al., 2022), which provided significant funding, with 19 and 17 articles, respectively. The ESRC (Economic and Social Research Council) also funded 9 documents, with the AFOSR (Air Force Office of Scientific Research) and the US Department of Defense each funding six publications. Moreover, the EPSRC (Engineering and Physical Sciences Research Council), Norges Forskningsråd, Social Sciences, and Humanitarian Research Council each funded four documents, with Binus University funding three publications.
Co-occurrence network of international published documents on social media and terrorism
In this study, the social media and terrorism publications had several keywords, which were used by various authors as experimental priorities (Miranda et al., 2020). The co-occurrence network of these keywords was also visualized using VOSviewer (Figure 9) and divided into cluster categories (Table 4). Based on the data visualization, specific keywords, such as social media, terrorism, and Twitter, were frequently used in the 660 Scopus-oriented published documents.
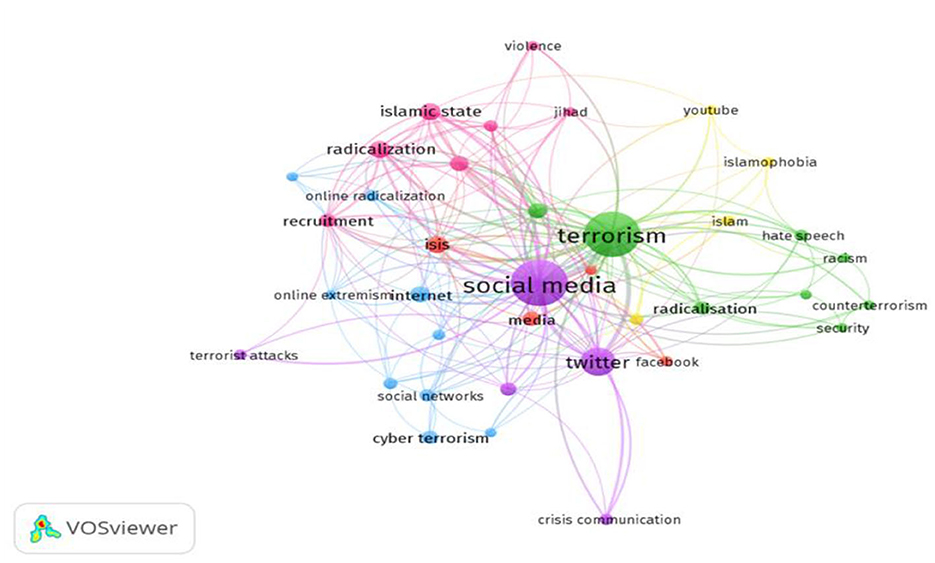
Figure 9. Co-occurrence network of published documents on social media and terrorism. Source: Author analysis from VOSviewer.
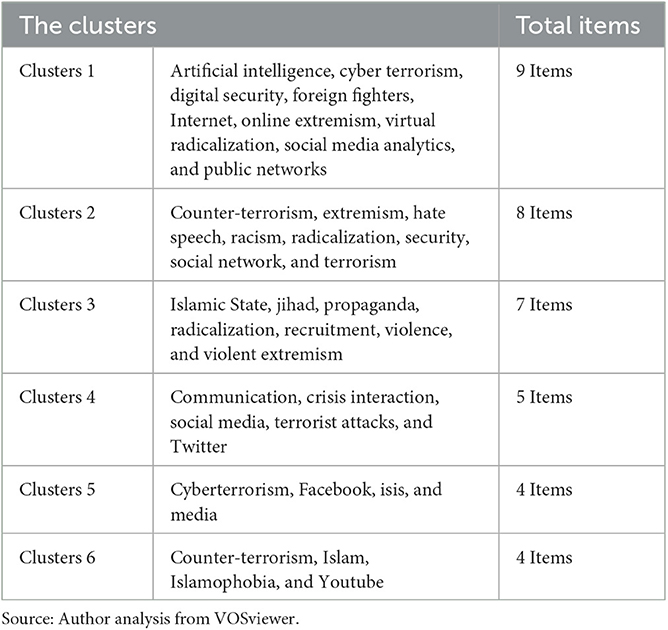
Table 4. Cluster items by co-occurrence network of published documents on social media and terrorism.
From these keywords, social media had the most prominent data visualization and was part of a cluster that included related terms such as communication, crisis interaction, terrorist attacks, and Twitter (Figure 9). Furthermore, terrorism was the next most prominent keyword, accompanied by Twitter. Based on Table 4, the co-occurrence network of social media and terrorism publications was also divided into 6 clusters, each containing different keywords.
Discussion
A bibliometric analysis was employed to examine the trends in international publications on social media and terrorism. This analysis emphasized various data visualization tools, to facilitate and expedite the evaluation of large published document volume. In this study, a total of 660 Scopus-oriented publications from 2009 to 2022 was analyzed, with several interesting trends identified.
Firstly, the published document trend significantly increased since 2015, with a peak of 103 publications in 2018. This trend was attributed to the rapid development of social media and its increasing use by terrorist groups, such as ISIS, to strengthen and intimidate their legitimacy and opponents, respectively (Sweeney and Kubit, 2020). From this context, the influence of terrorist movements was more conspicuous in carrying out their mission (Schreer and Tan, 2019). The patterns by which social media was used to counter terrorism and rebuild normalcy within society was also examined regarding terrorist attacks. For example, the hashtags, #KitaTidakTakut (“We are not afraid”) and #JakartaBerani (“Jakarta is brave”), were used following the bomb attack in Jakarta on January 14, 2016 (Berewot et al., 2019). Similarly, emergency organizations and military or police forces had employed social media, to detect and understand the movements and actions of terrorist groups during attacks (Jain and Vaidya, 2021).
Secondly, the US (United States), the UK (United Kingdom), and Australia conducted the most studies on social media and terrorism. These countries had a strong interest in ensuring the security of their citizens and national likenesses in various regions, as terrorism and the use of internet media had become global threats (Nobles and Williams, 2017). This indicated that various publications on the threat of terrorism, including the use of social media, were the focus of the studies proposed by the US, the UK, and Australia. The uncontrolled dissemination of information through social media also negatively affected society, such as causing trauma and fear (Holman et al., 2014). For these three countries, the existence of internet platforms need to be controlled to protect their national interests. This should align with various social media facilities such as websites, blogs, public networking sites, forums, video sharing services, Facebook, Twitter, Instagram, YouTube, etc, which were predominantly owned by western companies, specifically America (Weimann, 2016).
Thirdly, the most commonly discussed topics were terrorism, Twitter, cyberterrorism, extremism, radicalization, violence, recruitment, terrorist attacks, and propaganda. These topics reflected the observations of the authors studying social media and terrorism, which identified the need to anticipate and mitigate the various threats posed through online platforms and friends (Waskiewicz, 2012). Moreover, the evaluation of these topics required subsequent investigation, to minimize the negative impact of social media on the increasing activities of terrorist groups. Some stakeholders were also expected to immediately perform some actions against various social accounts capable of spreading radical ideology through the Internet (Kibtiah et al., 2020).
Conclusion
Based on the results, the international publications on social media and terrorism specifically experienced a significant increase since 2015, due to the influence of internet media platforms. This showed that the trend peaked in 2018, with a total of 103 published documents emphasizing various topics related to social media, terrorism, Twitter, cyberterrorism, extremism, recruitment, radicalization, propaganda, and terrorist attacks.
The results also showed that the articles in the field of social sciences dominated these international publications. This proved that the US, the UK, and Australia were the most common countries of publication, due to the protection of their national interests from the terrorism threats. From the results, the authors having the most published documents were Tsikrika T. and Vrochidis S., with Horizon 2020 Framework Program being the top funding sponsor. Besides examining the relationship between social media and terrorist attacks, the potential impacts of terrorism through internet facilities, specifically social media, were anticipated and mitigated.
Data availability statement
The datasets presented in this article are not readily available because for preliminary analysis, raw data is not accessible. Don't hesitate to get in touch with GY if you would like to request access to this dataset. Requests to access the datasets should be directed to Z29uZGFAdW1tLmFjLmlk.
Author contributions
All authors provided equal contributions to the writing of this article. All authors contributed to the article and approved the submitted version.
Funding
This study was supported by the University of Muhammadiyah Malang and the Directorate General of Higher Education, Research, and Technology of the Ministry of Education, Culture, Research, and Technology of Indonesia, through the Basic Research for Excellence in Higher Education (PDUPT) research grant scheme (number 195/E5/P6.02.00.PT/202).
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
Abbas, A. F., Jusoh, A., Mas'od, A., Alsharif, A. H., and Ali, J. (2022). Bibliometrix analysis of information sharing in social media. Cogent. Bus. Manag. 9, 2016556. doi: 10.1080/23311975.2021.2016556
Abrar, M. F., Arefin, M. S., and Hossain, M. S. (2019). “A framework for analyzing real-time tweets to detect terrorist activities,” in 2nd International Conference on Electrical, Computer and Communication Engineering, ECCE (Cox's Bazar: IEEE), 1–6.
Aistrope, T. (2016). Social media and counterterrorism strategy. Aust. J. Int. Aff. 70, 121–138. doi: 10.1080/10357718.2015.1113230
Albadi, N., Kurdi, M., and Mishra, S. (2019). Investigating the effect of combining GRU neural networks with handcrafted features for religious hatred detection on Arabic Twitter space. Soc. Netw. Anal. Mining 9, 41. doi: 10.1007/s13278-019-0587-5
Almoqbel, M., and Xu, S. (2019). Computational mining of social media to curb terrorism. ACM Comp. Surv. 52, 1–25. doi: 10.1145/3342101
Aroyewun, T. F., Olaleye, S. O., Adebisi, Y. A., and Perveen, A. (2022). Bibliometric analysis of contributions to COVID-19 research in Malaysia. Ann. Med. Surg. 84, 104823. doi: 10.1016/j.amsu.2022.104823
Asongu, S. A., Orim, S.-M. I., and Nting, R. T. (2019). Terrorism and social media: global evidence. J. Global Inf. Technol. Manag. 22, 208–228. doi: 10.1080/1097198X.2019.1642023
Barbe, D., Pennington-Gray, L., and Schroeder, A. (2018). Destinations' response to terrorism on Twitter. Int. J. Tour. Cities 4, 495–512. doi: 10.1108/IJTC-04-2018-0027
Basit, A. (2020). COVID-19: a challenge or opportunity for terrorist groups? J. Policing Intell. Counter Terror. 15, 263–275. doi: 10.1080/18335330.2020.1828603
Berewot, J., Fibra, A., and Supria. (2019). “The roles of social media toward Indonesian's resilience after terrorist bombing in Jakarta 2016,” 1st International Conference on Advance and Scientific Innovation, ICASI (Medan: IOP Publishing).
Bernardi, D. L., Cheong, P. H., Lundry, C., and & Ruston, S. W. (2012). Narrative Landmines: Rumors, Islamist Extremism, and the Struggle for Strategic Influence. Rutgers University.
Berta, A., Miguel Ángel, C., Clara, G. S., and Rubén, H. (2022). A bibliometric analysis of 10 years of research on symptom networks in psychopathology and mental health. Psychiatry Res. 308, 114380. doi: 10.1016/j.psychres.2021.114380
Bibi, A., Hussain, Z., Khan, F., and Maqsood, A. (2017). “Quantitative evaluation of security and privacy perceptions in online social networks: a case study,” in 14th International Bhurban Conference on Applied Sciences and Technology, IBCAST 2017 (Islamabad: Institute of Electrical and Electronics Engineers Inc.), 425–433.
Brajawidagda, U., Reddick, C. G., and Chatfield, A. T. (2016). “Social media and urban resilience: a case study of the 2016 Jakarta terror attack,” in 17th Annual International Conference on Digital Government Research, dg.o 2016, eds Y. Kim and M. Liu (Shanghai: Association for Computing Machinery), 445–454.
Burnap, P., Williams, M. L., Sloan, L., Rana, O., Housley, W., Edwards, A., et al. (2014). Tweeting the terror: modelling the social media reaction to the Woolwich terrorist attack. Soc. Netw. Anal. Mining 4, 1–14. doi: 10.1007/s13278-014-0206-4
Carammia, M. (2022). A bibliometric analysis of the internationalisation of political science in Europe. Euro. Polit. Sci. 21, 564–595. doi: 10.1057/s41304-022-00367-9
Caton, S., and Landman, R. (2022). Internet safety, online radicalisation and young people with learning disabilities. Br. J. Learn. Disabil. 50, 88–97. doi: 10.1111/bld.12372
Chami, M. B. (2021). Role of technological revolution in tansport and communications developments. BAU J. Sci. Technol. 3, 1–8. doi: 10.54729/2959-331X.1058
Chatfield, A. T., Reddick, C. G., and Brajawidagda, U. (2015). “Tweeting propaganda, radicalization and recruitment: Islamic state supporters multi-sided twitter networks,” in 16th Annual International Conference on Digital Government Research, dg.o 2015, Vols 27 (Phoenix, AZ: Association for Computing Machinery), 239–249. doi: 10.1145/2757401.2757408
Chaudhari, D. D., and Pawar, A. V. (2021). Propaganda analysis in social media: a bibliometric review. Inf. Discov. Deliv. 49, 57–70. doi: 10.1108/IDD-06-2020-0065
Cheong, P. H. (2014). “New media and terrorism,” in Exchanging Terrorism Oxygen for Media Airwaves: The Age of Terroredia (IGI Global), 184–196.
Cheong, P. H., and Lundry, C. (2012). Prosumption, transmediation, and resistance: terrorism and man-hunting in Southeast asia. Am. Behav. Sci. 56, 488–510. doi: 10.1177/0002764211429365
Cobo, M. J., Jürgens, B., Herrero-Solana, V., Martínez, M. A., and Herrera-Viedma, E. (2018). Industry 4.0: a perspective based on bibliometric analysis. Proc. Comput. Sci. 139, 364–371. doi: 10.1016/j.procs.2018.10.278
Congge, U., Guillamón, M., and Nurmandi, A. (2023). Digital democracy : a systematic literature review. Front. Polit. Sci. 5, 1–11. doi: 10.3389/fpos.2023.972802
Cvetojevic, S., and Hochmair, H. H. (2018). Analyzing the spread of tweets in response to Paris attacks. Comput. Environ. Urban Syst. 71, 14–26. doi: 10.1016/j.compenvurbsys.2018.03.010
Debnath, S., Das, D., and Das, B. (2017). “Identifying terrorist index (T+) for ranking homogeneous twitter users and groups by employing citation parameters and vulnerability lexicon,” in 5th International Conference on Mining Intelligence and Knowledge Exploration, MIKE 2017: Vol. 10682 LNAI (Hyderabad: Springer Verlag), 391–401.
Donthu, N., Kumar, S., Mukherjee, D., Pandey, N., and Lim, W. M. (2021). How to conduct a bibliometric analysis: an overview and guidelines. J. Bus. Res. 133, 285–296. doi: 10.1016/j.jbusres.2021.04.070
Downing, J., and Dron, R. (2022). Theorising the ‘security influencer': speaking security, terror and muslims on social media during the manchester bombings. New Media Soc. 24, 1234–1257. doi: 10.1177/1461444820971786
Dwiwarno, N. (2018). “Terrorism as transnational organized crime and government's attemp to elliminate terrorism,” in IOP Conference Series: Earth and Environmental Science, Vol. 175 (IOP Publishing).
Fakhrurroja, H., Atmaja, M. N., Panjaitan, J. N. C. G., Alamsyah, A., and Munandar, A. (2019). “Crisis communication on twitter: a social network analysis of christchurch terrorist attack in 2019,” in 10th International Conference on ICT for Smart Society, ICISS 2019 (Bandung: Institute of Electrical and Electronics Engineers Inc.), 1–6. doi: 10.1109/ICISS48059.2019.8969839
Fedushko, S., and Benova, E. (2019). Semantic analysis for information and communication threats detection of online service users. Proc. Comput. Sci. 160, 254–259. doi: 10.1016/j.procs.2019.09.465
Fkih, F., and Al-Turaif, G. (2023). Threat modelling and detection using semantic network for improving social media safety. Int. J. Comp. Netw. Inf. Sec. 15, 39–53. doi: 10.5815/ijcnis.2023.01.04
Gaikwad, M., Ahirrao, S., Kotecha, K., and Abraham, A. (2022). Multi-ideology multi-class extremism classification using deep learning techniques. IEEE Access 10, 104829–104843. doi: 10.1109/ACCESS.2022.3205744
Gaikwad, M., Ahirrao, S., Phansalkar, S., and Kotecha, K. (2021). Online extremism detection: a systematic literature review with emphasis on datasets, classification techniques, validation methods, and tools. IEEE Access 9, 48364–48404. doi: 10.1109/ACCESS.2021.3068313
Gialampoukidis, I., Kalpakis, G., Tsikrika, T., Papadopoulos, S., Vrochidis, S., and Kompatsiaris, I. (2017a). “Detection of terrorism-related twitter communities using centrality scores,” in 2nd International Workshop on Multimedia Forensics and Security, MFSec, 21–25.
Gialampoukidis, I., Kalpakis, G., Tsikrika, T., Vrochidis, S., and Kompatsiaris, I. (2017b). “Key player identification in terrorism-related social media networks using centrality measures,” in 7th European Intelligence and Security Informatics Conference, EISIC 2016 (Uppsala: Institute of Electrical and Electronics Engineers Inc.), 112–115.
Giri, D., and Vats, A. (2019). “Social media and disaster management in india: scope and limitations,” in Advances in Science, Technology and Innovation (Cham: Springer Nature), 349–356.
Goyal, T., Saini, J. K., and Bansal, D. (2019). “Analyzing behavior of ISIS and Al-Qaeda using association rule mining,” in Lecture Notes in Networks and Systems, Vol. 46 (Singapore: Springer), 669–675.
Groumpos, P. P. (2021). A critical historical and scientific overview of all industrial revolutions. IFAC-PapersOnLine 54, 464–471. doi: 10.1016/j.ifacol.2021.10.492
Hatta, M., Rajamanickam, R., Abdullah, D., Hartono, H., Bunga, M., Adji, H. S., et al. (2018). “Efforts to overcome cyber crime actions in Indonesia,” in Journal of Physics: Conference Series, Vol. 1114 (IOP Publishing).
Holman, E. A., Garfin, D. R., and Silver, R. C. (2014). Media's role in broadcasting acute stress following the Boston Marathon bombings. Proc. Natl. Acad. Sci. U. S. A. 111, 93–98. doi: 10.1073/pnas.1316265110
Jain, P. N., and Vaidya, A. S. (2021). Analysis of social media based on terrorism - a review. Viet. J. Comp. Sci. 8, 1–21. doi: 10.1142/S2196888821300015
Jamil, M. L., Pais, S., and Cordeiro, J. (2022). Detection of dangerous events on social media: a critical review. Soc. Netw. Anal. Mining 12, 1–17. doi: 10.1007/s13278-022-00980-y
Kaati, L., Shrestha, A., and Cohen, K. (2016). “Linguistic analysis of lone offender manifestos,” in 4th IEEE International Conference on Cybercrime and Computer Forensic, ICCCF 2016 (Vancouver, BC: Institute of Electrical and Electronics Engineers Inc.), 1–6. doi: 10.1109/ICCCF.2016.7740427
Kalantari, A., Kamsin, A., Kamaruddin, H. S., Ale Ebrahim, N., Gani, A., Ebrahimi, A., et al. (2017). A bibliometric approach to tracking big data research trends. J. Big Data 4, 1–18. doi: 10.1186/s40537-017-0088-1
Kibtiah, T. M., Miranda, E., Fernando, Y., and Aryuni, M. (2020). “Terrorism, social media and text mining technique: review of six years past studies,” in 5th International Conference on Information Management and Technology, ICIMTech 2020 (Bandung: IEEE), 571–576. doi: 10.1109/ICIMTech50083.2020.9211148
Klona, M., and Menzies, J. (2021). Mapping terrorism in the academic landscape of business fi eld of study : a bibliometric study of the past 30 years. Int. J. Conflict Manage. 32, 791–825. doi: 10.1108/IJCMA-12-2020-0200
Kolajo, T., and Daramola, O. (2017). “Leveraging big data to combat terrorism in developing countries,” in 2017 Conference on Information Communication Technology and Society, ICTAS 2017 (Durban: IEEE), 1–6. doi: 10.1109/ICTAS.2017.7920662
Kruglova, A. (2022). Terrorist Recruitment, Propaganda and Branding: Selling Terror Online. Taylor and Francis.
Kumari, S. (2019). Impact Of ICT and social media on society. J. Emerg. Technol. Innov. Res. 6, 406–408.
Lee, N. (2013). Counterterrorism and Cybersecurity: Total Information Awareness, Vol. 9781461472. New York, NY: Springer.
Lemieux, A. F., and Boyle, M. J. (2012). “Terrorism,” in Encyclopedia of Human Behavior: Second Edn (Elsevier Inc.), 595–603.
Leung, X. Y., Sun, J., and Bai, B. (2017). Bibliometrics of social media research: a co-citation and co-word analysis. Int. J. Hosp. Manag. 66, 35–45. doi: 10.1016/j.ijhm.2017.06.012
Loan, F. A. (2018). Research output on terrorism by India and Pakistan: a bibliometric study. 3 134–139. doi: 10.1108/CC-01-2017-0004
Machitidze, G. G. (2020). Comparative analyses of terrorist threats under conditions of covid-19. World Econ. Int. Relat. 64, 5–12. doi: 10.20542/0131-2227-2020-64-11-5-12
Miranda, E., Aryuni, M., Fernando, Y., and Kibtiah, T. M. (2020). “A study of radicalism contents detection in twitter: Insights from support vector machine technique,” 5th International Conference on Information Management and Technology, ICIMTech 2020 (Bandung), 549–554. doi: 10.1109/ICIMTech50083.2020.9211229
Mohd, N., Azlan, E., and Yunos, Z. (2019). “Terrorism indoctrination via social media: a Malaysian case study,” in 6th European Conference on Social Media, ECSM 2019 (Academic Conferences and Publishing International Limited), 387–391.
Moussaoui, M., Zaghdoud, M., and Akaichi, J. (2019). A possibilistic framework for the detection of terrorism-related Twitter communities in social media. Concurr. Comput. Pract. Exp. 31, e5077. doi: 10.1002/cpe.5077
Mugari, I. (2020). The dark side of social media in Zimbabwe: unpacking the legal framework conundrum. Cogent. Soc. Sci. 6, 1825058. doi: 10.1080/23311886.2020.1825058
Mukherjee, D., Lim, W. M., Kumar, S., and Donthu, N. (2022). Guidelines for advancing theory and practice through bibliometric research. J. Bus. Res. 148, 101–115. doi: 10.1016/j.jbusres.2022.04.042
Mumtaz, A. A., and Sultan, A. D. (2011). Literature on terrorism: A bibliometric analysis of articles published during 1981-1990. Malaysian J. Library Infm. Sci. 16, 33–43.
Mussiraliyeva, S., Bolatbek, M., Omarov, B., and Bagitova, K. (2020). “Detection of extremist ideation on social media using machine learning techniques,” in 12th International Conference on Computational Collective Intelligence, ICCCI 2020: Vol. 12496 LNAI (Springer: International Publishing),743–752.
Naqvi, S., Williams, I., Enderby, S., Pollner, P., Abel, D., Biescas, B., et al. (2019). “Towards fully integrated real-time detection framework for online contents analysis-RED-alert approach,” in 4th IEEE European Symposium on Security and Privacy Workshops, EUROS and PW 2019 (Stockholm: IEEE), 257–263. doi: 10.1109/EuroSPW.2019.00035
Nobles, H., and Williams, B. N. (2017). “The challenge of crisis communication in contemporary American society: an opportunity for co-producing public safety and security,” in Homeland Security: Perceptions, Threats and Challenges (Nova Science Publishers, Inc.), 79–110.
Odhiambo, N. A., Ochara, N. M., and Kadymatimba, A. (2018). “Structuring of the terrorism problem in the digital age: a systems perspective,” in 2018 Open Innovations Conference, OI 2018 (Johannesburg: IEEE), 148–154. doi: 10.1109/OI.2018.8535619
Ogunlana, S. O. (2019). Halting Boko Haram / Islamic State's West Africa Province propaganda in cyberspace with cybersecurity technologies. J. Strat. Sec. 12, 72–106. doi: 10.5038/1944-0472.12.1.1707
Ogunsuyi Opeyemi, J., and Adebola, K. (2022). K-nearest neighbors bayesian approach to false news detection from text on social media. Int. J. Educ. Manag. Eng. 12, 22–32. doi: 10.5815/ijeme.2022.04.03
Omotosho, M. O. (2019). Information revolution and growing power of communication: a foundation of new diplomacy. Jadavpur J. Int. Relat. 23, 142–157. doi: 10.1177/0973598419861472
Pashentsev, E. N., and Bazarkina, D. Y. (2021). ISIS propaganda on the internet, and effective counteraction. J. Polit. Market. 20, 17–33. doi: 10.1080/15377857.2020.1869812
Petrushka, A., Komova, M., and Fedushko, S. (2020). Scientific content: language expansion in bibliometric databases. CEUR Workshop Proc. 2654,375–389.
Royo-Vela, M., and McBee, K. A. (2020). Is IS online chatter just noise?: An analysis of the islamic state strategic communications. Int. J. Strat. Commun. 14, 179–202. doi: 10.1080/1553118X.2020.1770768
Roziqin, A., Kismartini Fajrina, A. N., and Salahudin Sulistyaningsih, T. (2022). The development of Indonesian e-Government : a bibliometric analysis. COLLNET J. Scientometr. Inf. Manag. 16, 49–74. doi: 10.1080/09737766.2021.2007036
Sandoval, M. (2012). Internet and Surveillance: The Challenges of Web 2.0 and Social Media, Vol. 16, eds C. Fuchs, K. Boersma, and A. Albrechtslund (New York, NY: Routledge).
Sanri, Ç., and Goodwin, R. (2014). “The influence of globalization and technological development on intimate relationships,” in Social Influences on Romantic Relationships: Beyond the Dyad, ed C. R. Agnew (Cambridge University Press), 11–32. doi: 10.1017/CBO9781139333610.003
Schreer, B., and Tan, A. T. (2019). Terrorism and Insurgency in Asia: A Contemporary Examination of Terrorist and Separatist Movements. Routledge.
Scopus. (2022). Available online at: www.scopus.com
Scrivens, R., Gill, P., and Conway, M. (2020). “The role of the internet in facilitating violent extremism and terrorism: suggestions for progressing research,” in The Palgrave Handbook of International Cybercrime and Cyberdeviance (Palgrave Macmillan), 1417–1435.
Shilling, C., and Mellor, P. A. (2017). Uncovering Social Life: Critical Perspectives From sociology. Taylor and Francis.
Shoaib, M., Zhang, S., and Ali, H. (2022). A bibliometric study on blockchain-based supply chain: a theme analysis, adopted methodologies, and future research agenda. Environ. Sci. Pollut. Res. 30, 14029–14049. doi: 10.1007/s11356-022-24844-2
Simon, T., Goldberg, A., Aharonson-Daniel, L., Leykin, D., and Adini, B. (2014). Twitter in the cross fire - The use of social media in the Westgate mall terror attack in Kenya. PLoS ONE 9, e104136. doi: 10.1371/journal.pone.0104136
Smith, C., von der Borch, R., Isakhan, B., Sukendar, S., Sulistiyanto, P., Ravenscrroft, I., et al. (2018). The manipulation of social, cultural and religious values in socially mediated terrorism. Religions 9, 1–19. doi: 10.3390/rel9050168
Sraieb-Koepp, N. (2017). “The role of media in public advocacy and countering violent extremism,” in Routledge Companion to Media and Humanitarian Action (Routledge), 261–267.
Staniforth, A., and Nitsch, H. (2013). “Preventing terrorism together. a framework to provide social media anti-radicalization training for credible community voices,” in Emerging Trends in ICT Security (Morgan Kaufmann), 549–556. doi: 10.1016/B978-0-12-411474-6.00034-7
Steensen, S. (2018). “Tweeting terror: an analysis of the norwegian twitter-sphere during and in the aftermath of the 22 July 2011 terrorist attack,” in Social Media Use In Crisis and Risk Communication: Emergencies, Concerns and Awareness (Emerald Group Publishing Ltd.), 15–41.
Subagyo, A. (2021). The implementation of the pentahelix model for the terrorism deradicalization program in Indonesia. Cogent. Soc. Sci. 7, 1964720. doi: 10.1080/23311886.2021.1964720
Subekti, D., Nurmandi, A., and Mutiarin, D. (2022). Mapping publication trend of political parties campaign in social media: a bibliometric analysis. J. Polit. Market. 1–19. doi: 10.1080/15377857.2022.2104424. [Epub ahead of print].
Sulistyaningsih, T., Loilatu, M. J., and Roziqin, A. (2023). Research trends on smart urban governance in Asia : a bibliometric analysis. J. Sci. Technol. Policy Manag. doi: 10.1108/JSTPM-03-2022-0045. [Epub ahead of print].
Sutton, J., Ben Gibson, C., Phillips, N. E., Spiro, E. S., League, C., Johnson, B., et al. (2015). A cross-hazard analysis of terse message retransmission on Twitter. Proc. Natl. Acad. Sci. U. S. A. 112, 14793–14798. doi: 10.1073/pnas.1508916112
Sweeney, M. M., and Kubit, M. (2020). Blood and scripture: how the Islamic State frames religion in violent video propaganda. Dyn. Asymmetr. Conflict 13, 172–190. doi: 10.1080/17467586.2019.1680853
Tantray, M. A., and Vishwavidyalya, R. D. (2021). Traditional and Modern Society : An Analytical Exploration. Oriental Research Madras.
The Ministry of Communication Information of Indonesia. (2018). BNPT: Internet Jadi Media Penyebarluasan Terorisme. Available online at: https://www.kominfo.go.id/content/detail/18602/bnpt-internet-jadi-media-penyebarluasan-terorisme/0/berita_satker
Tran, Y. H., and Tran, Q. N. (2018). “Estimating public opinion in social media content using aspect-based opinion mining,” in 9th International Conference on Mobile Networks and Management, MONAMI 2017, Vol. 235 (Melbourne, VIC: Springer Verlag), 101–115.
Trang, D., Johansson, F., and Rosell, M. (2015). “Evaluating algorithms for detection of compromised social media user accounts,” in 2nd European Network Intelligence Conference, ENIC 2015 (Karlskrona: IEEE), 75–82.
Tsikrika, T., Vrochidis, S., Akhgar, B., Burnap, P., Katos, V., and Williams, M. L. (2017). “1st international workshop on search and mining terrorist online content and advances in data science for cyber security and risk on the web,” in 10th ACM International Conference on Web Search and Data Mining, WSDM 2017 (Cambridge), 823–824. doi: 10.1145/3018661.3022760
Tundis, A., Jain, A., Bhatia, G., and Muhlhauser, M. (2019). “Similarity analysis of criminals on social networks: an example on twitter,” in 28th International Conference on Computer Communications and Networks, ICCCN 2019, 2019-July (Valencia: IEEE), 1–6. doi: 10.1109/ICCCN.2019.8847028
Vujković, P., Ravšelj, D., Umek, L., and Aristovnik, A. (2022). Bibliometric analysis of smart public governance research: smart city and smart government in comparative perspective. Soc. Sci. 11, 293. doi: 10.3390/socsci11070293
Wang, X., Xu, Z., and Škare, M. (2020). A bibliometric analysis of Economic Research-Ekonomska IstraŽivanja (2007–2019). Econ. Res. 33, 865–886. doi: 10.1080/1331677X.2020.1737558
Waskiewicz, T. (2012). “Friend of a friend influence in terrorist social networks,” in 2012 International Conference on Artificial Intelligence, ICAI 2012, 1044–1048.
Wei, W., Joseph, K., Liu, H., and Carley, K. M. (2015). “The fragility of twitter social networks against suspended users,” in IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, ASONAM 2015 (Long Beach, CA: Association for Computing Machinery, Inc.), 9–16. doi: 10.1145/2808797.2809316
Weimann, G. (2016). “Why do terrorists migrate to social media?,” in Violent Extremism Online: New Perspectives on Terrorism and the Internet (Routledge), 45–64.
Wilson, R. (2019). “Cyber warfare, terrorist narratives and counter terrorist narratives: an anticipatory ethical analysis,” in 18th European Conference on Cyber Warfare and Security, ECCWS 2019 (Curran Associates Inc.), 577–586.
Winter, C., Neumann, P., Meleagrou-Hitchens, A., Ranstorp, M., Vidino, L., and Fürst, J. (2020). Online extremism: Research trends in internet activism, radicalization, and counter-strategies. Int. J. Conf. Violence 14, 1–20.
Wormwood, J. B., Lin, Y.-R., Lynn, S. K., Barrett, L. F., and Quigley, K. S. (2019). Psychological impact of mass violence depends on affective tone of media content. PLoS ONE 14, e0213891. doi: 10.1371/journal.pone.0213891
Xu, M., David, J. M., and Kim, S. H. (2018). The fourth industrial revolution: opportunities and challenges. J. Financ. Res. 9, 90–95. doi: 10.5430/ijfr.v9n2p90
Keywords: bibliometric, Scopus, social media, terrorism, trends
Citation: Yumitro G, Febriani R, Roziqin A and Indraningtyas A (2023) Bibliometric analysis of international publication trends on social media and terrorism by using the Scopus database. Front. Commun. 8:1140461. doi: 10.3389/fcomm.2023.1140461
Received: 19 January 2023; Accepted: 22 May 2023;
Published: 13 June 2023.
Edited by:
Achmad Nurmandi, Universitas Muhammadiyah Yogyakarta, IndonesiaReviewed by:
Solomiia Fedushko, Lviv Polytechnic, UkraineHasbi Aswar, Islamic University of Indonesia, Indonesia
Copyright © 2023 Yumitro, Febriani, Roziqin and Indraningtyas. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Gonda Yumitro, Z29uZGFAdW1tLmFjLmlk
 Gonda Yumitro
Gonda Yumitro Rizki Febriani2
Rizki Febriani2 Ali Roziqin
Ali Roziqin