- 1Department of Electrical and Computer Engineering, Concordia University, Montreal, QC, Canada
- 2Concordia Institute for Information Systems Engineering, Concordia University, Montreal, QC, Canada
- 3Toronto Research Centre, Defence Research and Development Canada, Toronto, ON, Canada
- 4Department of Electrical Engineering and Computer Science, York University, Toronto, ON, Canada
Introduction: This article proposes a secure implementation for consensus using a dynamic event-triggered control (DETC) scheme for general autonomous multi-agent systems (MAS) under asynchronous (distributed) denial of service (DoS) attacks. The asynchronous DoS attacks can block each communication channel independently in an unknown pattern. Depending on the impact of DoS on the communication topology, the attacks are categorized into (i): connectivity-preserved DoS (CP-DoS), and (ii): connectivity-broken DoS (CB-DoS). In CP-DoS, the operating communication topology remains connected. On the other hand, in CB-DoS the adversary breaks the communication graph into isolated sub-graphs.
Methods: The DETC scheme is employed to reduce the control updates for each agent. To guarantee consensus under both the CP-DoS and CB-DoS, a linear matrix inequality (LMI) based optimization approach is proposed, which simultaneously designs all the unknown DETC parameters as well as the state feedback control gain.
Results: The proposed optimization method prioritizes the minimum inter-event interval (MIET) between consecutive control updates. The trade-off between relevant features of the MAS, namely the consensus convergence rate, intensity of control updates, and level of resilience to DoS can be handled by the proposed optimization.
Discussion: Simulation results quantify the effectiveness of the proposed approach, showcasing its ability to maintain secure consensus in MAS under varying DoS attack scenarios.
1 Introduction
Over the past decade, cooperative control in autonomous multi-agent systems (MASs) has been a topic of extensive research in different communities. These cooperative tasks mainly include formation control, leader-following, containment, and consensus. Consensus has attracted overwhelming attention due to its vast applications in many areas such as estimation in sensor networks (Meng and Chen, 2014), attitude alignment for spacecrafts (Ren, 2007), and control of microgrids (Zhang et al., 2019; Amini et al., 2022a), to name a few. This article studies the consensus problem for general linear MASs under a class of distributed cyber attacks, namely denial of service, and an advanced class of event-based control scheme referred to as the dynamic event-triggering control.
1.1 Literature review
An important subject in cooperative control of autonomous MASs is to design suitable control schemes which utilize a reasonable amount of energy and computation resources. Conventional consensus frameworks are based on continuous-time update of the control protocol which is energy consuming and difficult to implement from the actuator point of view. Recently, event-triggered control (ETC) strategies are employed which enable the control protocol to be updated only if a pre-designed condition is satisfied. Several ETC strategies have been proposed for consensus in MAS (Peng and Li, 2018; Ge et al., 2019). More recently, dynamic event-triggering control (DETC) schemes (Hu et al., 2018; Deng et al., 2020; Zhao and Hua, 2021; Yang R. et al., 2022) have been recognized as one of the most efficient ETC schemes. Unlike conventional ETC schemes, in DETC an auxiliary dynamic variable is designed which helps in reducing the amount of control updates. The advantage of DETC scheme in reducing the amount of events over other simplified schemes is proved in Girard (2014). Recently, there has been a surge of considerable interest on DETC methodologies in different applications as surveyed in Ge et al. (2019). For instance, Meng et al. (2023) focused on DETC fault interval estimation for aeroengine sensors, where to reconstruct sensor fault a DET-based robust augmented state observer is designed. In (Cao et al., 2023) effects of time-varying delay on observer-based DETC mechanisms for MASs have been investigated. Furthermore, design of DETC mechanisms for distributed bipartite consensus in MASs has been considered in Du X. et al. (2023). He et al. (2022) surveys different secure control problems associated with MASs. The intuition behind this survey is the increased attack surface of MASs due to network-enabled information sharing as a consequence of expanded connectivity in practical scenarios. Along a similar path, Wang et al. (2023) targets surveying recent literature on resilient consensus control for MASs. Please refer to this work for a complete treatment of state-of-the-art concerning DoS attacks, spoofing attacks and Byzantine attacks in MASs, where attack model and mechanisms are introduced together with associated resilient consensus control structure. As a final note, when it comes to secure consensus of MASs, Shang (2022) proposed a median-based consensus strategy for resilient consensus control of MAS considering a time-varying directed random network. The proposed approach is superior to Weighted-Mean-Subsequence-Reduced techniques eliminating the need for the number of malicious agents in vicinity of each cooperating agent. In Shang (2021), the problem of resilient coordinated control in MASs is considered in presence o malicious agents, where agents' dynamics can be continuous-time or discrete-time. Furthermore, this work introduces the intriguing concept of heterogeneous robustness, which facilitates convergence analysis, and aims at capturing topological structure of the underlying network. Finally, Shang (2023) focused on resilient tracking consensus with a single leader considering a time-varying random directed graph, where in addition to cooperative agents, Byzantine agents are present.
Generally speaking, the DETC schemes often depend on multiple unknown parameters which should be designed based on the stability of the closed-loop MAS. The capability of the event-triggering schemes in reducing the number of control updates highly depends on the operating values of the design parameters. Regarding the DETC schemes, it is often the case that some feasible regions are derived for the design parameters (Hu et al., 2018; Yi et al., 2018; He et al., 2019; He and Mo, 2022). However, even when the feasible regions are known, selecting proper operating values that efficiently reduces the control updates is still inexplicable and requires trial and error. It is, therefore, desirable to develop a systematic design framework that computes the exact values of the unknown parameters and guarantee a substantial reduction for the control updates. Motivated by Peng and Yang (2013); Abdelrahim et al. (2014); Amini et al. (2022), where the convex optimization techniques are utilized to include some performance objectives (such as H∞ optimization and inter-event interval maximization), in this article we develop a convex optimized design framework with a focus on reducing the control updates as much as possible.
Cyber security against malicious attacks is another important issue, which poses new challenges in performance and stability guarantees of the MASs. Generally, there exist three types of attacks targeted at cyber-physical systems, namely replay attacks, false data injection (FDI), and denial of service (DoS). In DoS (De Persis and Tesi, 2015; Zhang et al., 2018; Zhang and Feng, 2019; Liu et al., 2020), the adversary blocks the communication channels, hence the neighboring agents do not receive the transmitted signals. It is clear that DoS can significantly impact the behavior of the agents and, in extreme cases, can destabilize the MAS. In literature, the occurrence of DoS is often modeled either in a periodic (Hu et al., 2019; Xu Y. et al., 2019) or unknown pattern (Xu et al., 2018; Feng and Hu, 2019; Liu et al., 2020). In practice, the periodic scenario may not be able to fully model the pattern of DoS, as the adversary can launch the attacks in non-periodic patterns. A common assumption considered in many related works such as Xu et al. (2018); Feng and Hu (2019); Xu Y. et al. (2019); Zha et al. (2019); Amini et al. (2022); Deng and Wen (2020); Zhang and Ye (2021) is that DoS simultaneously paralyzes all communication channels. In this scenario, the MAS undergoes a binary situation based on the DoS being active or inactive. If DoS is inactive, the MAS operates normally based on the initially designated network. If DoS is active, the communication network is fully paralyzed and all agents are open-loop. In a more complex and more general DoS, which is referred to as the asynchronous (distributed) DoS (Lu and Yang, 2018; Xu W. et al., 2019; Yang Y. et al., 2020; Liu and Wang, 2021; Yang and Ye, 2022), the adversary attacks any arbitrary channel at different instants. Dealing with the asynchronous DoS is more challenging as the MAS may confront numerous connected or disconnected topologies depending on the status of each individual channel being healthy or under attack. Secure event-triggered consensus under asynchronous DoS is an important and challenging topic which, to date, has not been studied proportionately. It should be noted that the asynchronous DoS works (Lu and Yang, 2018; Xu W. et al., 2019; Yang Y. et al., 2020; Liu and Wang, 2021; Yang and Ye, 2022) have practical shortcomings which require further improvement. In particular, Lu and Yang (2018); Yang and Ye (2022); Liu and Wang (2021) are based on time-triggered or sampled-data control protocols, not event-triggered. Additionally, the ETC schemes used in Xu W. et al. (2019); Yang Y. et al. (2020) has lower inter-event interval compared to the more advanced schemes such as DETC. This motivates us to develop a DETC method for consensus under asynchronous DoS attack.
1.2 Contributions
Motivated by the above discussion and following our previous work (Amini et al., 2022), this article studies the dynamic event-triggered control for consensus in general linear MASs under unknown and asynchronous DoS attacks. The main contributions of the article are as follows:
• Unlike many existing works (Xu et al., 2018; Feng and Hu, 2019; Xu Y. et al., 2019; Zha et al., 2019; Deng and Wen, 2020; Zhang and Ye, 2021; Amini et al., 2022), where the DoS attack simply blocks all the communication channels at the same time (referred to as synchronous DoS), we consider a more general and realistic scenario where the adversary attacks any arbitrary channel at different time instants (hence called asynchronous DoS). The problem formulation for asynchronous DoS is fundamentally different from that of the synchronous DoS. In addition, we should point out that by stating asynchronous (distributed) attack in the context of this work, we eliminate imposition of any patterns on the DOS. In other words, each of the distributed agents can face a different DoS pattern.
• To the best of our knowledge, this is the first instance where a DETC protocol is formulated for consensus under unknown and asynchronous DoS attacks. Compared to Lu and Yang (2018); Xu W. et al. (2019); Yang Y. et al. (2020); Yang and Ye (2022); Liu and Wang (2021), the implementation of the DETC protocol under asynchronous DoS is novel and significantly reduces the burden of control updates.
• Unlike existing works related to DETC schemes (He et al., 2019; He and Mo, 2022), the design procedure in this article is based on a co-design optimization and simultaneously computes all required event-triggering parameters as well as the control gain. The optimization increases the minimum inter-event interval for a guaranteed level of resilience to asynchronous DoS attacks.
The remaining article is organized as follows. Section 2 introduces notation and discusses the problem to be studied. Section 3 formulates the consensus problem under DoS. Section 4 presents the main results and sufficient conditions to guarantee consensus. Simulation examples are included in Section 5. Finally, Section 6 concludes the paper.
2 Preliminaries and problem statement
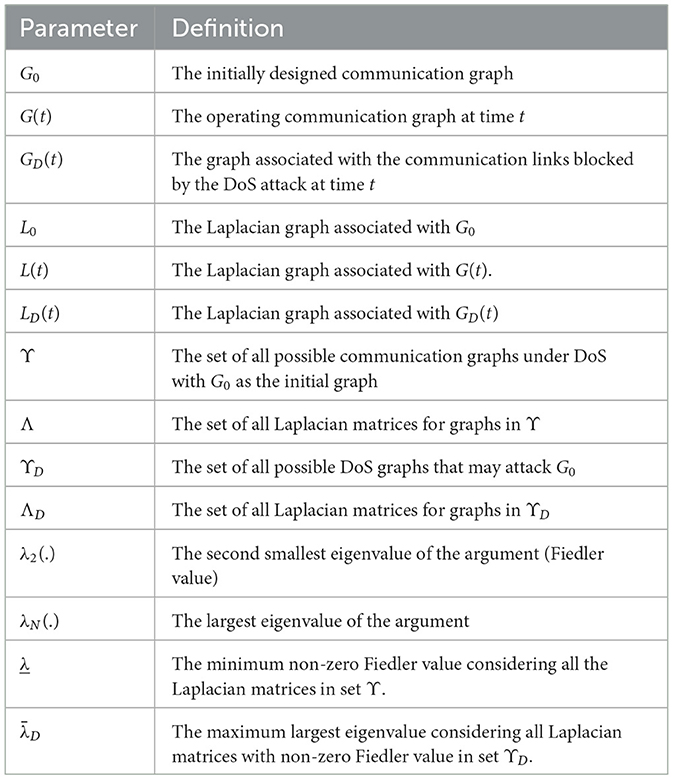
Throughout the article, vectors are denoted in bold font while matrices and scalars are represented by normal font. The following notation is used. ℕ: set of natural numbers; ℕ0 = ℕ ∪ 0; ℝ: set of real numbers; ∥.∥: L2 norm; M > 0: symmetric positive definite matrix M; M−1: inverse of matrix M; ⊗: Kronecker product; (.)T: transpose of a matrix or vector argument. For two sets A and B, notation A\B returns the elements which belong to set A but not to set B. The asterisk * in the lower triangle of symmetric matrices represents the transpose of the corresponding block from the upper triangle. The communication network of a MAS at time t is modeled by graph , where is the set of agents. The pair (i, j), (1 ≤ j, i ≤ N), is included in the edge set iff agent j is connected to agent i at time t. Matrix is the weighted adjacency matrix at time t, where ai,i = 0, ai,j ≠ 0 if , and ai,j = 0 if . The neighboring set for agent i at time t is defined by . Laplacian matrices are defined by letter L with different subscripts (depending on the associated graph). We refer to the second smallest eigenvalue of L, denoted by λ2(L), as the Fiedler value. The largest eigenvalue is denoted by λN(L). It is worth noting that, in our derivations, we need a symmetric Laplacian matrix where all its eigenvalues are real-valued. This is quite common practice in the LMI context. The main challenge here is that when Laplacian matrix is not symmetric, eigenvalues will be complex numbers rendering application of LMI infeasible.
Proposition 1. For a undirected graph G and λ2(L) as its Fiedler value, it holds that λ2(L) = 0 if and only if G is disconnected. The number of connected components of G is equal to the multiplicity of 0 in the eigenvalues of Laplacian (Newman, 2001, Thm. 1.3.4).
Consider the following general linear MAS
where and are, respectively, the state and control input for agent i. Matrices A and B are constant and known. The pair (A, B) is controllable.
Definition 1. MAS Equation (1) is said to achieve state consensus if for any initial condition , , it holds that , .
2.1 Control protocol and dynamic even-triggering scheme
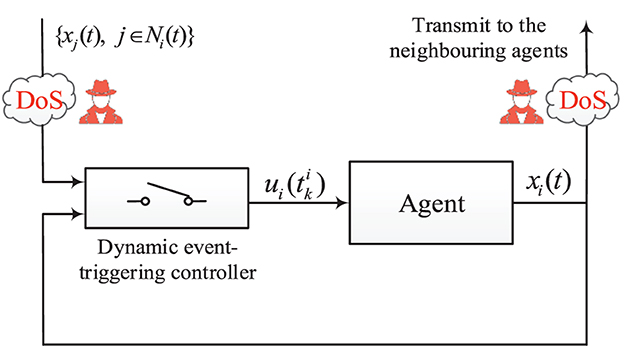
Each agent measures and transmits its state value xi(t) to its neighbors through an undirected network. As shown in Figure 1, a DETC scheme (which will be presented later) is employed to reduce the amount of control input updates. Only if the DETC condition is fulfilled an event is triggered and ui(t) is updated. We denote the sequence as the triggering times for agent i, where ui(t) is being updated. Using this notation, is the state value at the k-th event for agent i. The inter-event interval for agent i is given by which shows the time interval between two events in a row. We denote the following disagreement vector for agent i
Note that the neighboring set is time-varying since the DoS attack, as will be discussed later, can block the communication channel between agent i and any of its neighbors. The following control protocol is used for agent i to achieve consensus
where K ∈ ℝm×n is the control gain to be designed. Let , , denote the event-triggering error. Initialized by , , the next event instant is triggered by the following DETC condition (Yi et al., 2018)
where matrices Φ1 ≥ 0, Φ2 ≥ 0 and scalar ϕ3 ≥ 0 are design parameters. The auxiliary state ηi(t) follows
where ηi(0) > 0. Scalar ϕ4 ≥ 0 and matrix Φ5 ≥ 0 are the other unknown parameters to be designed.
Remark 1. As observed in Equation (5), the updating protocol for ηi(t) is based on the disagreement vector qi(t) and a negative quadratic self-feedback. Intuitively, ηi(t) can be regarded as a linear first-order filtered value of qi(t). Compared to the conventional ETC strategy ||ei(t)|| ≤ αi∥qi(t)∥ used in Hu et al. (2015), the utilization of the auxiliary variable ηi(t) helps in regulating the threshold (Equation 4) in a dynamic manner and in a better relationship with disagreement qi(t). It is also proved in Girard (2014) that the inter-event interval using DETC (Equation 4) is larger than the conventional ETC strategy ||ei(t)|| ≤ αi∥qi(t)∥, meaning less event triggering is proved. It is straightforward to show that the ETC schemes proposed in Qian et al. (2018); Wu et al. (2018); Xu W. et al. (2019); Yi et al. (2019) are all special cases of the DETC (Equation 4).
Next, we show that parameter ηi(t) remains positive over time.
Proposition 2. If Φ5 > Φ2 and ηi(0) > 0, , parameter ηi(t) remains positive over time. In particular the following condition holds
Proof: Based on Equation (4), it holds that for . If Φ5 > Φ2, we get that . Since is non-negative, it then follows that
By solving differential inequality (Equation 7) for , we obtain Considering one event-triggering interval back, i.e., , one obtains . By successively moving backward through intervals , , …, and comparing the associated inequalities the following is obtained
The proof is complete, noting that Equation (8) is equivalent to Equation (6). □
From the implementation point of view, in an event-triggering scheme the time interval between two arbitrary event instants must be strictly positive. Otherwise, the event-detector scheme would potentially detect an infinite number of events in a finite interval (He et al., 2019). This undesirable phenomenon is known as the Zeno-behavior in the context of event-triggering control schemes. Therefore, it is necessary to exclude the possibility of Zeno-behavior in the proposed scheme. The exclusion of the Zeno-behavior is usually accomplished by obtaining a strictly positive lower-bound between two potential event instants. In other words, if we guarantee that the minimum inter-event time (MIET) between two successive event instants in Equation (4) is strictly positive, then the possibility of detecting infinite number of events in a finite period is ruled out. To exclude Zeno-behavior in Equation (4), in what follows we prove that the minimum inter-event interval (MIET) between any two events is strictly positive.
Proposition 3. The minimum inter-event time (MIET) for agent i, , is strictly positive and lower-bounded by
where
Proof: Consider two consecutive event instants ( and ) for agent i. Based on Equation (4), at it holds that . For , the event-triggering error ei(t) evolves from zero until Equation 4 is satisfied and the next event is detected. From we obtain that . From Equations (3) and (1), it holds that . Combining the last three equations leads to , or , . It, then, follows that or equivalently
where Fi(t) is defined in Equation (10). The next event is detected by Equation (4) at where . Then, from Equation (6), it follows that . By combining the latter inequality with Equation (11), expression (9) is obtained. The lower-bound derived in Equation (9) is strictly positive which implies that is strictly greater than , i.e., . Conceptually speaking, it is guaranteed that the next event instant is always greater than the current one. Therefore, the possibility of infinite event-triggering in finite time is ruled out and DETC (Equation 4) does not exhibit Zeno behavior.
Remark 2. In addition to excluding the possibility of the Zeno-behavior, another important observation can be made from expression (9). Based on the MIET, i.e., the right hand side of Equation (9), it can be shown that smaller values for ∥K∥, ∥Φ1∥, and ϕ4 increase the value of the MIET (i.e., the intensity of control updates is reduced). On the other hand, higher values for ||Φ2||, ||Φ3|| increase the MIET and help in reducing the control updates. Note that the impact of DETC parameters ||Φ1||, ||Φ2|| and ||Φ3|| on the intensity of events is intuitive from Equation (4) and also confirmed by Equation (9). We use this observation in the proposed objective function considered in Theorems 1 and 2.
2.2 Denial of service
As shown in Figure 1, the DoS attacks, when active, target the communication channels and block the state transmission between the neighboring agents. Unlike many existing works (Xu et al., 2018; Feng and Hu, 2019; Xu Y. et al., 2019; Zha et al., 2019; Deng and Wen, 2020; Zhang and Ye, 2021; Amini et al., 2022), where it is assumed that the DoS attacks simultaneously block all communication channels, in this article we consider a more general and realistic scenario where the adversary attacks any arbitrary link.
Let denote the initially designed communication topology. When the adversary is completely inactive (i.e., none of the communication links are blocked) the MAS operates based on G0. The associated Laplacian matrix to G0 is defined by L0. Let
denote the c-th DoS interval on channel (i, j). Parameter is the time instant when the adversary begins the c-th attack on channel (i, j) and is the duration of attack. Since DoS on channel (i, j) also implies DoS on channel (j, i), condition i < j is mentioned in Equation (12). Note that the first DoS can occur at t = 0, i.e., . Therefore, does not need to be strictly positive.
For channels (i, j) and (j, i), the state of “being under DoS" or “being healthy" is a binary variable. Hence, there exist possible communication topologies labeled by G0, G1, …, Gf, where . Let Υ and Λ, respectively, denote the set of all possible graphs under DoS attack and their corresponding Laplacian matrices, i.e.,
During consensus iterations, the operating communication topology at time instant t is denoted by . It is clear that G(t) ∈ Υ, ∀t ≥ 0. We refer to as the set of healthy edges (i.e., not under attack) at instant t.
The DoS graph is defined by the edges that are blocked by DoS. The DoS graph at instant t is denoted by , where if and only if the (i, j) communication channel is blocked by DoS at time t. In other words
It is straightforward to verify that the “healthy edges " and “blocked edges " satisfy
In a similar fashion to Equation (13), we define the following sets which include all possible DoS graphs and their corresponding Laplacian matrices
Now, we classify the DoS attack modes based on their impact on the initial communication graph G0.
Mode I. Connectivity-preserved DoS (CP-DoS): In this type of attack, a subset of the initial transmission links are attacked by DoS. However, the resultant communication topology remains connected.
Mode II. Connectivity-broken DoS (CB-DoS): In this scenario, a subset of the initial links are blocked and the resultant communication topology is disconnected. In the extreme case, all communication channels between the agents can be blocked which is referred to as the “full DoS".
Example: Consider a MAS with five nodes as shown in Figure 2. The initially designed communication topology is labeled with G0 which consists of 6 bidirectional edges. At t = 1, two of the edges are blocked by DoS. The corresponding DoS graphs are shown above each rightward arrows. The attack at t = 1 is a CP-DoS as the resulting graph is still connected. Then, a CB-DoS occurs at t = 2 which isolates node 4. Note that the DoS graph is always constructed based on G0, not the previously operating communication topology. Afterwards, the adversary is inactive at t = 3, so the MAS can operate based on G0. Finally, a full DoS is observed at t = 4 which isolates all the nodes. Note that the cardinality of Υ is 26 = 64 which implies that there exist 63 different topologies under DoS for graph G0. For ease of reference, Table 1 lists important parameters used to model the communication topology of the MAS and DoS attacks.
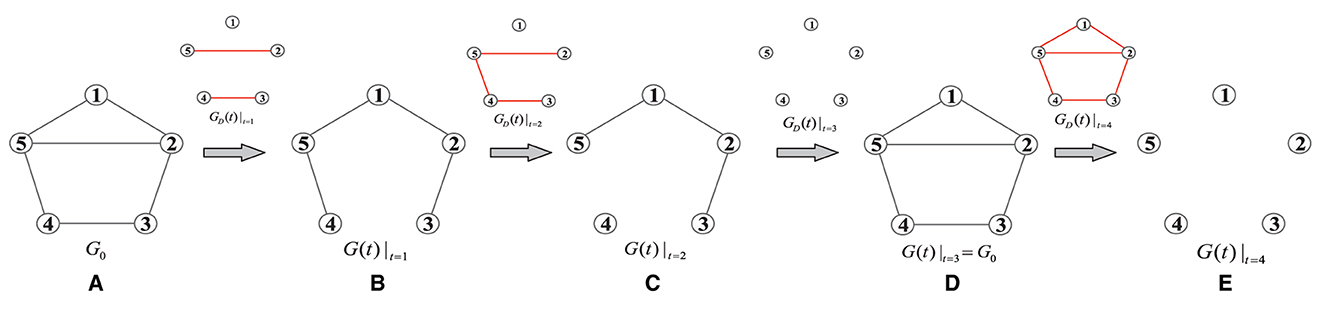
Figure 2. An illustrative example for different classes of DoS attacks. (A) The initially designed communication topology G0, (B) a connectivity-preserved DoS, (C) a connectivity-broken DoS, (D) an inactive cycle for DoS, (E) a full DoS.
2.3 Control objectives
The article addresses the following problems:
Problem 1. As observed earlier, the DETC protocol (Equation 4) and the auxiliary variable ηi(t) which follows Equation (5) depend on the knowledge of multiple unknown gains. These gains can significantly impact the consensus features such as the convergence rate, intensity of the events, and the amount of resilience to DoS. How to efficiently design these gains in a systematic way is a challenging matter. Many references such as Hu et al. (2018); Yi et al. (2018); He et al. (2019) derive some feasible regions for the DETC gains. However, even when the feasible regions are known, selecting the actual operating values that efficiently avoid unnecessary events remains an issue and requires some trial and error. As a more systematic approach, we propose a convex optimization to design the exact values of the unknown control and DETC gains based on an objective function which increases the minimum inter-event time (MIET). Increasing the MIET avoids unnecessary control updates.
Problem 2. In the presence of attack, it is important to develop a secure implementation under all the DoS modes and their different resulting topologies. While some of the variations may be homomorphic graphs, the exponential growth of the situations as per the number of edges makes dealing with all the possible scenarios difficult, especially for large networks. How to design proper control and DETC gains in response to CP-DoS and CB-DoS will be investigated. It is clear that if the MAS is subject to DoS attacks with unlimited duration, the control protocol cannot receive sufficient amount of information and consensus may not be achieved. Therefore, it is reasonable to consider an assumption regarding the finiteness of the attack duration and explicitly obtain the tolerable amount of resilience to DoS.
3 Problem formulation
In this section, we analyze the closed-loop MAS (Equation 12) under asynchronous DoS attacks.
3.1 Formulation of asynchronous DoS
The asynchronous DoS given in Equation (12) can lead to both the CP-DoS and CB-DoS attacks. According to Proposition (1), if the operating graph G(t) becomes disconnected under DoS, it holds that λ2(L(t)) = 0.
We define the c-th CB-DoS interval as follows
where
with r−1+v−1 = −1. Conceptually speaking, rm is the earliest time when DoS on a link (i, j) leads to a disconnected graph [i.e., λ2(L(t)) = 0]. Also, vm is the duration of Rm, i.e., the earliest time after rm when the graph becomes connected again [i.e., λ2(L(t)) > 0]. Expression r−1+v−1 = −1 is selected for the initialization of r0 as the first instance where connectivity of the network is broken. The union of all CB-DoS intervals for t ∈ [t1, t2) is
The complement of Rm is Wm, which represents either healthy or CP-DoS intervals. More precisely,
The union of all healthy or CP-DoS intervals for t ∈ [t1, t2) is given by
Based on Equations (14)–(19), let |R(t1, t2)| and |W(t1, t2)|, respectively, denote the accumulative length of corresponding intervals for t ∈ [t1, t2). Since W(t1, t2) and R(t1, t2) are complements of each other, one concludes that
The following assumption holds for the duration of the DoS attacks.
Assumption 1. There exist positive constants T0, and T1 such that the following upper-bounds hold (De Persis and Tesi, 2015)
The DoS attacks considered in Hu et al. (2019); Xu Y. et al. (2019) are assumed to follow a periodic pattern. Considering a periodic pattern for DoS may not fully represent the unknown and malicious nature of the adversary. Our considered asynchronous attack is more general, where the DoS is assumed to occur with an unknown pattern. Such a DoS model with unknown pattern can be characterized only by the energy constraints of the adversary. Assumption 1, which is widely used for formulation of unknown DoS attacks, constrains DoS in terms of its average duration. In other words, the strength of the DoS attacks (in terms of duration) is scalable with time. Inequality (Equation 21) expresses property that the DoS intervals satisfy a slow-on-the-average type condition. It implies that the total duration for DoS, on average, should not exceed a certain fraction of time, which is scaled by 1/T1. Parameter T0 is included to allow for consideration of DoS at the start time.
3.2 Closed-loop system
Let , , , . From Equations (1) and (3), the closed-loop MAS under DoS is given below
Next, we transform system (21) through the eigenvalue decomposition of L0. It is straightforward to show that
where is a diagonal matrix consisting the eigenvalues of L0 and matrix includes the normalized eigenvectors of L0. We construct the (N−1) × N dimensional matrix V0 which includes rows 2 to N of matrix . In other words, matrix V0 is obtained by removing the first row of matrix (the corresponding eigenvector to eigenvalue zero). With this definition, it holds that . Now, consider the following transformation
It is proved in Ge and Han (2017) that consensus is achieved in Equation (21) iff . Using Equation 22, system (21) is converted to
where and JD(t) = diag(λ2(LD(t)), …, λN(LD(t))). Matrix VD(t) with unity norm includes the eigenvectors of LD(t).
4 Stability analysis and parameter design
In this section, we propose a co-design approach to compute the control and DETC parameters under asynchronous DoS attacks. For ease of comprehension, the results are presented in two theorems.
• In Theorem 1, we assume that only CP-DoS occurs. Considering this situation, we propose an optimization framework that co-designs all the unknown control and DETC parameters with a given desired rate for exponential consensus convergence.
• Theorem 2 extends Theorem 1 by considering both the CB-DoS and CP-DoS. A desired level of tolerance to asynchronous DoS can be selected a priori. The trade-offs between the rate of consensus convergence, intensity of control updates, and the amount of resilience to DoS can be controlled by Theorem 2.
4.1 Parameter design under connectivity-preserved DoS
In this section, we propose a theorem that guarantees consensus under the situation where MAS (Equation 23) is only subjected to CP-DoS. Section 4.2 extends the framework to both the DoS cases.
Theorem 1. Consider MAS (Equation 23) with the initially designed communication topology under CP-DoS attacks. Given a desired consensus convergence rate ω1, if there exist positive definite matrices Pn×n > 0, M1n×n > 0, M2n×n > 0, M5n×n > 0, free matrix Ωm×n, positive scalars m3 > 0, m4 > 0, ϵ1 > 0, and θc > 0, (1 ≤ c ≤ 7), such that the following convex minimization problem is feasible
subject to:
where
then the unknown parameters for control protocol (Equation 2) and DETC scheme (Equation 4) are designed as follows
The following bounds are guaranteed for the designed parameters associated with the convex minimization problem defined through Equations (24)–(30)
Using Equation (31), the convergence rate of z(t) satisfies
where .
Proof: For the sake of readability, we remove the time argument t in the proof. Consider the following expression
where V = V1+V2 and
If (34) is guaranteed, condition (33) is satisfied and ω1 determines the exponential consensus convergence rate. We compute the time derivative for V1 as follows
where Remind that in this theorem we assume that the MAS is either in healthy intervals or under CP-DoS. In this situation, all the diagonal elements of J0−JD are non-zero. Under condition (P−1BK)T + P−1BK > 0, the following holds
We expand based on Equation (5)
Since LD ≥ 0, it holds that . Recalling that , , and using transformation (22), it is straightforward to show
Considering Equations (38, 39), and inequality , we conclude that
As for the DETC (Equation 4), it holds that , . In a collective sense, we obtain . Similar to Equation (39), we can derive that . Therefore, the following condition is obtained
Let ν = [zT, eT, ηT]T. Based on Equations (36, 37, 40), and (41), we re-arrange Equation (34) as follows
Inequality (Equation 34) is guaranteed if . We pre- and post multiply by ℙ = diag(IN−1⊗P, IN⊗P, IN), which results in . Denote the following alternative variables
Now, re-arrange as follows
where
According to Young's inequality, condition (44) is guaranteed if there exists a positive scalar ϵ1 such that
The only non-zero element of YTY is . Now, we consider the following upper-bound
Considering the upper-bound in Equation (46) and using the Schur complement Lemma with respect to the term , inequality (Equation 45) turns into Ψ1 < 0 given in Equation (25). The condition above (Equation 37) is pre- and post-multiplied by P and that results in LMI Π < 0 given in Equation (26).
Formulation of the objective function: Similar to Amini et al. (2022), a weighted-sum approach is employed to decrease/increase the control gain and DETC parameters according to their impact on MIET (Equation 9). For decision variables θc > 0, (1 ≤ c ≤ 7), we consider the following constraints
Note that from Equations (43) and (47) one can obtain the bounds given in Equation (32). According to Equation (32), if one decreases the values of θc > 0 (1 ≤ c ≤ 7), parameters {∥K∥, ∥Φ1∥, ϕ4} are decreased and {∥Φ2∥, ϕ3, ∥Φ5∥} are increased. This increases MIET (Equation 9). The objective function F (given in Equation 9) is constructed based on minimizing the sum of θc, (1 ≤ c ≤ 7). The constraints given in Equation (24) are not in the form of LMIs. To make convex constraints, we employ the Schur complement and LMIs Ci, (1 ≤ i ≤ 7), are obtained from Equation (47). Once the convex problem (Equation 24) is solved the control gain and DETC parameters are computed from Equation (31). □
Remark 3. In fact, Theorem 1 guarantees consensus based on the smallest possible Fiedler value (λ) and the maximum largest eigenvalue for the DoS graph (). These eigenvalues correspond to the strongest possible CP-DoS attacks on G0. As for the performance trade-offs, a faster desired convergence rate (i.e., a larger value for ω1) leads to a faster consensus convergence according to Equation (33). However, as ω1 is increased the intensity of the events is increased and less saving in control updates is expected.
4.2 Extension to connectivity-broken DoS
In the following theorem, we extend Theorem 1 for the situation where both the CB-DoS and CP-DoS may occur.
Theorem 2. Consider MAS (Equation 23) with the initially designed communication topology G0 under both the CP-DoS and CB-DoS attacks. Let ω1 be the desired consensus convergence rate under only CP-DoS and α < 1 be the desired resilience level to CB-DoS attacks. If there exist positive definite matrices Pn×n > 0, M1n×n > 0, M2n×n > 0, M5n×n > 0, free matrix Ωm×n, positive scalars m3 > 0, m4 > 0, ϵ1 > 0, ϵ2 > 0, and θc > 0, (1 ≤ c ≤ 7), such that the following convex minimization problem is feasible
subject to:
where Ψ1, Π, and Ci, (1 ≤ i ≤ 7), are previously defined in Theorem 1 and
then the unknown parameters for control protocol (Equation 2) and DETC (Equation 4) are designed from the same expressions given in Equation (31). These parameters guarantee resilient to CB-DoS attacks satisfying
Additionally, the system trajectories satisfy the following exponentially bounded stability
where
Proof: The proof considers three possible situations that the MAS may undergo: (i) Healthy or CP-DoS, (ii) CB-DoS where there exists at least one healthy channel, (iii) CB-DoS where all channels are blocked (full DoS).
(i) Healthy or CP-DoS: From Theorem 1, for healthy or CP-DoS intervals (t ∈ Wm) it is guaranteed that if Ψ1 < 0 and Π < 0. This leads to the following expression
(ii) CB-DoS where there exists at least one healthy channel: In the presence of CB-DoS (t ∈ Rm), MAS (Equation 23) is disconnected and the agents may diverge. There exists a positive scalar ω2 that the divergence rate satisfies
where V = V1+V2 is given in Equation (35). We expand Equation (56) as
Since V2 > 0, if condition
is guaranteed, then Equation (57) is also guaranteed. The time derivatives for V1 and V2 are given in the proof of Theorem 1 and are re-produced below for ease of reference
with Ξ given below Equation (36). When CB-DoS occurs, there exists at least one zero diagonal entry in J0−JD. Hence
For CB-DoS with at least one healthy channel it still holds that Therefore, the proof follows similar steps given in expressions (39) to (46). This results in Ψ2 < 0 given in Equation (50).
(iii) CB-DoS where all channels are blocked: In the situation that all communication links are blocked we have LD(t) = L0 and qi(t) = 0, . Expanding Equation (58) for this situation results in
Condition (59) is guaranteed if . Pre- and post multiplying this condition by P results in Ψ3 < 0 given in Equation (51).
Now, we merge the Lyapunov conditions derived for the Wm and Rm intervals from expressions (55) and (56). Let us first expand Equation (56):
Consecutively using Equations (55) and (60), and assuming t ∈ Rm, we obtain that
From Equations (20) and (21), the first term in the right hand side of Equation (61) is upper-bounded as follows
where ρ1 and ζ are defined in Equations (54) and (63).1 From De Persis and Tesi (2015) (Lemma 4) the summation term in Equation (61) lies within the following upper-bound
Expressions (62) and (64) lead to exponential bounded consensus given in Equation (53).
Let α = ω1/(ω1+ω2). If the CB-DoS attacks satisfy , parameter ζ remains positive and system (Equation 1) is exponentially stable according to Equation (53). Parameter α represents the level of resilience to CB-DoS attacks. This completes the proof. □
Remark 4. In simple terms, Theorem 2 computes the control gain and DETC parameters by considering three situations: (i) All channels are healthy or the MAS is under CP-DoS. LMI Ψ1 < 0 given in Equation (49) represents this situation. (ii) The MAS is under CB-DoS, however, at least one channel is healthy in the communication topology. This situation is represented by LMI Ψ2 < 0 given in Equation (50). (iii) The MAS is under full CB-DoS and all communication channels are blocked. LMI Ψ3 < 0 given in Equation (51) represents this situation. With ω1 as the rate of consensus convergence for situation (i), ω2 as the rate of divergence for situations (ii) and (iii), and T1 as the time ratio of CB-DoS attacks, the condition decides whether consensus is guaranteed or not.
Remark 5. Increasing the desired resilience level to CB-DoS α, by construction, would make the MAS more resilient to CB-DoS, i.e., higher overall duration for DoS is tolerable. However, higher values for α lead to lower values for ω2 which makes LMI Ψ3 < 0 (given in Equation 51) unlikelier to be satisfied; especially if A is inherently unstable. Additionally, a performance drop is expected in the event savings and consensus convergence when α is increased for the sake of higher tolerance to DoS. This is the trade-off between the system performance and its amount of security to DoS.
Remark 6. As observed in Theorem 2, the knowledge of parameters T0 and T1 is only useful for the consensus convergence rate (Equation 53). In other words, the implementation of optimization (Equation 48) does not depend on T0 or T1. However, for selecting a reasonable value for α and run optimization (Equation 48), it is helpful if the designer has a priori estimation of parameter T1 (which roughly represents the average ratio of CB-DoS duration to total time).
Remark 7. The computational complexities of solving Theorems 1 and 2 grow at the , where the problem size Np = max{dm, nv}, the duality gap denoted by ϵg, dm is “the highest dimension of the LMIs associated with the optimization problem", and nv is the “total number of decision variables” involved (Amini, 2020, Remark 3.11). Both dm and nv are sensitive to addition of the DETC state η, and will be increased compared to the scenario without dynamic event-triggering. Consequently, the computational complexity of solving LMIs in Theorems 1 and 2 slightly grows.
Remark 8. We remind that Theorem 2 guarantees consensus in the bounded sense with system trajectories satisfying inequality (Equation 53). The reason that an asymptotic or exponential rate without a residual cannot be guaranteed comes from inequality which is used to make condition 38 quadratic. Intuitively, parameter η may not converge to zero which creates a bounded consensus error in the system.
Remark 9. Recently there has been an increasing interest in the fully distributed consensus control where no global knowledge of multi-agent system is required. While our proposed implementation in this article requires the knowledge of the minimum non-zero Laplacian eigenvalue which is a global information, we have identified important simplifying assumptions and practical shortcomings in existing references on fully distributed consensus approaches compared to our work. For example, in a vast majority of the proposed approaches such as Cheng and Li (2019); Li et al. (2020); Xu et al. (2022) an ideal scenario where no attack is targeted on the network is considered. Therefore, consensus in these references are not guaranteed in the presence of DoS attacks. In Wang et al. (2022); Du S. et al. (2023) a fully distributed event-triggered consensus under DoS is formulated. However, the DoS considered in Wang et al. (2022); Du S. et al. (2023) is synchronous which significantly simplifies the formulation compared to asynchronous DoS considered in our work. A fully distributed consensus under DoS attacks represented by Markov process (which can be regarded as asynchronous DoS) is proposed in Wang et al. (2022). However, the communication and control schemes in Wang et al. (2022) is not event-triggered.
Remark 10. This article considers a continuous-time model for the agents. Additionally, the dynamic event-triggering scheme (4) needs continuous-time monitoring of the condition to detect possible events. We note that it is not challenging to extend the proposed implementation in this work to a sampled-data dynamic event-triggering scheme where continuous-time measurement and event monitoring are relaxed. In fact, without compromising other novelties of the work one can adopt the well-known family of LMI-based Lyapunov-Krasovskii functionals (LKFs) stability method developed in our prior works [Amini et al., 2021, Equation (26)] and [Amini et al., 2022b, Equation (45)]. However, in order not to overshadow the main ideas of this work (i.e, incorporation of dynamic event triggering control under asynchronous DoS attacks) under overwhelmed formulation caused by the LKF approach we have opted to consider the continuous time formulation in this article.
4.3 Special case: DoS-free situation
The DoS-free situation (where no CP-DoS and no CB-DoS occur) is a special case of Theorems 1 and 2. The following corollary shows how the results in Theorem 1 can be reduced to the DoS-free situation
Corollary 1 (DoS-free situation). Consider MAS (Equation 23) with communication topology . Given a desired consensus convergence rate ω1, if there exist positive definite matrices Pn×n > 0, M1n×n > 0, M2n×n > 0, M5n×n > 0, free matrix Ωm×n, positive scalars m3 > 0, m4 > 0, and θc > 0, (1 ≤ c ≤ 7), such that the following convex minimization problem is feasible
subject to:
where Ci, (1 ≤ i ≤ 7), are defined in Theorem 1 and
then the unknown parameters for control protocol (Equation 2) and DETC (Equation 4) are designed from the same expressions given in Equation (31). The bounds given in Equation (32) are also guaranteed
Proof: The proof of feasibility of the convex minimization problem defined through Equations (65)–(68) can be followed from proof of Theorem 1 with LD = 0.
5 Simulation
To evaluate the performance of the proposed theorems, we conduct two different experiments as detailed below.
Example 1: Consider a MAS comprising of five agents with the following dynamics (Xu Y. et al., 2019)
The initially designed network topology for Equation (69) is defined by the following Laplacian matrix
For illustration, we consider an example of a sequence of distributed attacks with 4 CP-DoS and 4 CB-DoS given below:
We remind that the definition of is given in Equation (12). For better visualization, the attack sequence (Equation 71) is shown in Figure 3 where the highlighted areas in “orange” are CP-DoS attack intervals and in “red" are CB-DoS ones.
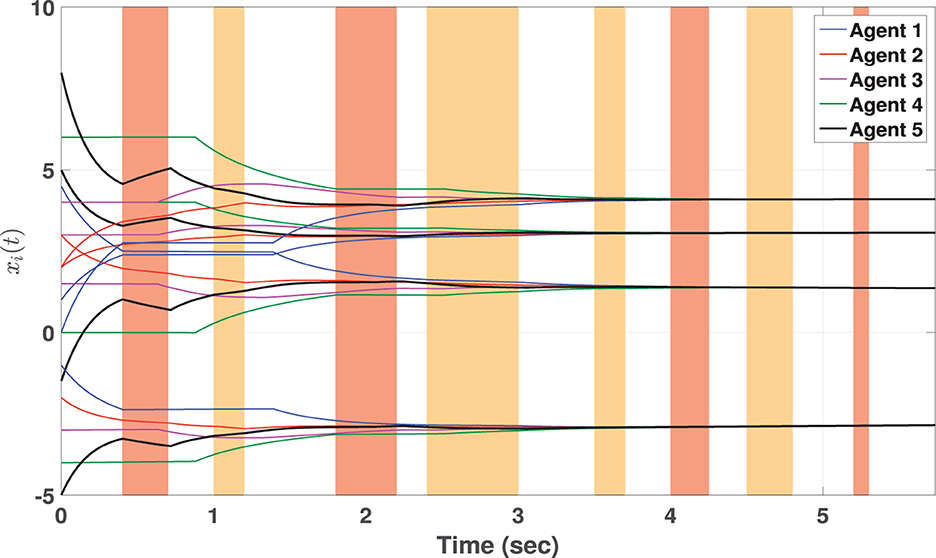
Figure 3. State consensus in MAS (Equation 69). Highlighted areas in “orange” are CP-DoS and in “red” are CB-DoS attack intervals (Equation 71).
It is easy to verify that the above DoS satisfies Assumption 1 with T0 = 0.3 and T1 = 7. The eigenvalues required in Equations (29), (30), and (52) are computed as λ = 0.38, , and . To compute necessary control and DETC design parameters from Theorem 2, we select ω1 = 0.2 and α = 0.15. With T1 = 7, it holds that . The following parameters are obtained by solving optimization (Equation 48) through the MOSEK solver
Let and ηi(0) = 1, (1 ≤ i ≤ 5). The sampling period Ts for simulation is selected as Ts = 0.001s.
Consensus iteration is run until the settling time t⋆ defined below
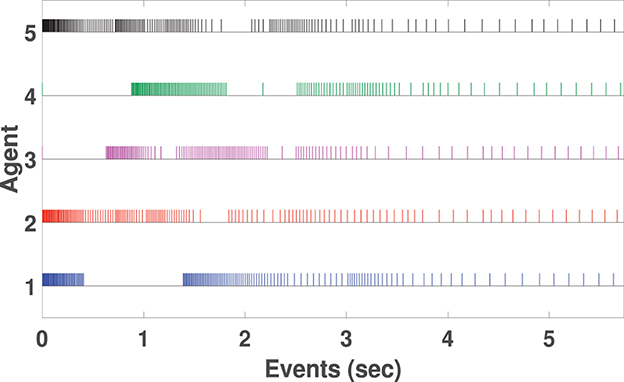
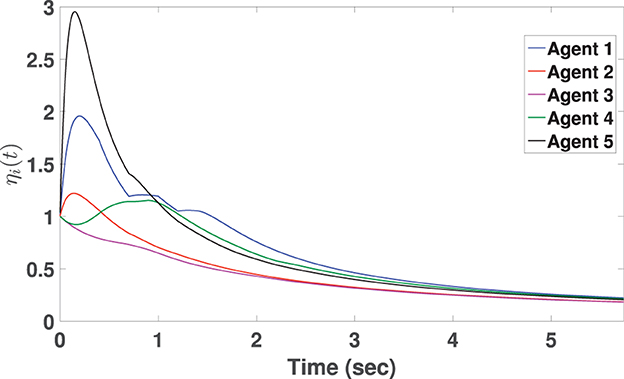
Conceptually speaking, time t⋆ determines the consensus settling time within the 0.05% of the initial disagreement z(0). Therefore, a higher value of t⋆ shows a slower rate of convergence and vice versa. We introduce t⋆ as an index to compare the settling time (convergence rate) for consensus. In this example, t⋆ = 5.73s. The states of MAS (Equation 69) are shown in Figure 3, where the agents reach consensus on respective states, despite the CB-DoS and CP-DoS given in Equation (71). In Figure 3, the highlighted areas in orange color show the CP-DoS and those in red represent intervals where CB-DoS is activated based on Equation (71). Controllers for agent 1 to agent 5 are, respectively, updated on 159, 151, 130, 138, and 176 occasions shown in Figure 4. For the sake of comparison, we introduce two parameters related to the amount of controller updates: (i) The average number of events (denoted by AE), and (ii) The average inter-event time (denoted by AIET). Parameter AE is computed by AE = (total events of all agents)/(number of agents). Additionally, AIET = t⋆/AE. In fact, parameter AIET is an index to measure the intensity of events. For this example, we have AE=150.8 and AIET= 0.038. Figure 5 depicts the trajectories of the dynamic threshold ηi(t), (1 ≤ i ≤ 5). As observed in Figure 5, variable ηi(t) rises from its initial condition ηi(0) = 1 and greatly contributes to reducing the number of events.
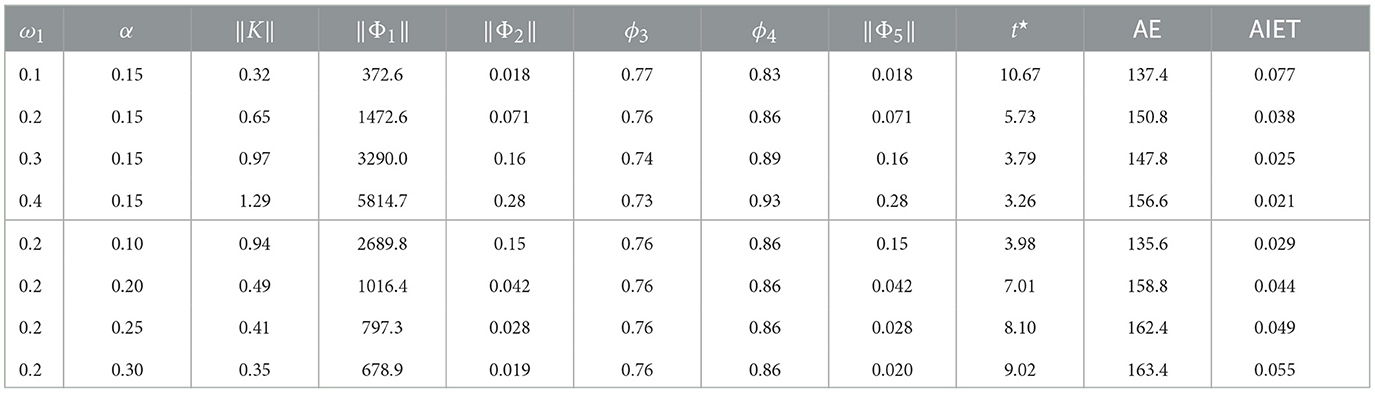
Next, we investigate how different values for convergence rate ω1 and resilience level to CB-DoS α influence the designed parameters and consensus features. To this end, we consider two simulation scenarios. In the first scenario, α is fixed at 0.15 and ω1 is incrementally increased in set {0.1, 0.2, 0.3, 0.4}. The purpose of this scenario is to observe the impact of ω1 while α is fixed. In the second scenario, ω1 is fixed at 0.2 and α is increased in set {0.1, 0.2, 0.25, 0.3}. Optimization (Equation 48) is solved for given values of ω1 and α listed in Table 2. Using the obtained parameters, a separate consensus is run for Equation (69) with similar L0, DoS attacks (Equation 71), and the initial conditions mentioned earlier. According to Table 2, the following design trade-offs are observed:
• When α is fixed and ω1 is increased, we demand a faster rate of consensus. As expected, the settling time t⋆ is reduced with higher values for ω1 and fixed α. This scenario is useful for applications where a fast rate of convergence is important.
• However, the higher rate of consensus is achieved at the expense of more intense control updates. Looking at Table 2, this observation is verified from the reduced values of AIET with larger ω1. This implies that the average inter-event time gets smaller and more frequent control update is demanded.
• As another observation, a higher value for α (i.e., demanding a higher resilience to CB-DoS attacks) a more conservative solution in terms of the consensus rate is obtained. In other words, consensus is achieved slower (i.e., higher t⋆) when α is increased.
These results verify the efficiency of the proposed method for a structured design based on the trade-off between consensus convergence rate, intensity of events, and resilience to DoS.
Example 2: In this section, we compare our work with He and Mo (2022) where another DETC scheme is formulated for consensus. The goals of this comparison are twofold: (i) Compare the essence of the parameter design approaches, and (ii) Compare the amount of savings in control updates. He and Mo (2022) studies consensus under a type of adversary known as the scaling attack. In order to focus only on the efficiency of the two event-triggering schemes and the basics of the design stages, we consider an attack-free situation. Consider the following MAS (Guo et al., 2014) with give agents and Laplacian (Equation 70)
The attack-free situation in He and Mo (2022) requires setting μ = 1. The control gain K = BTP is obtained by solving the generalized eigenvalue problem given in He and Mo (2022) (Equation 13). Except for Γ = PBBTP, the required parameters for DETC [He and Mo, 2022, Equation (34)] (namely ξ, ζ, θ, σ) should satisfy some feasibility regions specified by conditions (38) and (39) in He and Mo (2022). With , we have tested several different values satisfying the feasible regions and run consensus for Equation (72). These parameters are selected in such a way that conditions (38) and (39) in He and Mo (2022) are “just" satisfied so that we get the full advantage of the DETC. Three of the selected set of parameters are reported in Table 3. As for our proposed framework, we use Corollary 1 (DoS-free situation) with ω1 ∈ {0.9, 1.0, 1.2} to compute necessary parameters for MAS (Equation 72) and run consensus. Comparing the results with He and Mo (2022), the following matters worth mentioning:
• The employed objective function 𝔽 in our design stage helps in reducing the intensity of events as compared to He and Mo (2022). This is concluded by comparing the values of AIET for the rows with almost the same range of t⋆.
• Our proposed co-design framework computes the exact values of the necessary DETC parameters and there is no need for the process of trial and error to find efficient parameters within a region.
• Although the design stage in He and Mo (2022) has reduced complexity compared to our approach, since the extreme eigenvalues of the Laplacian matrix are used to derive the feasible regions for the DETC parameters, it inherently introduces some conservation in the DETC performance (i.e., more events are triggered than our work).
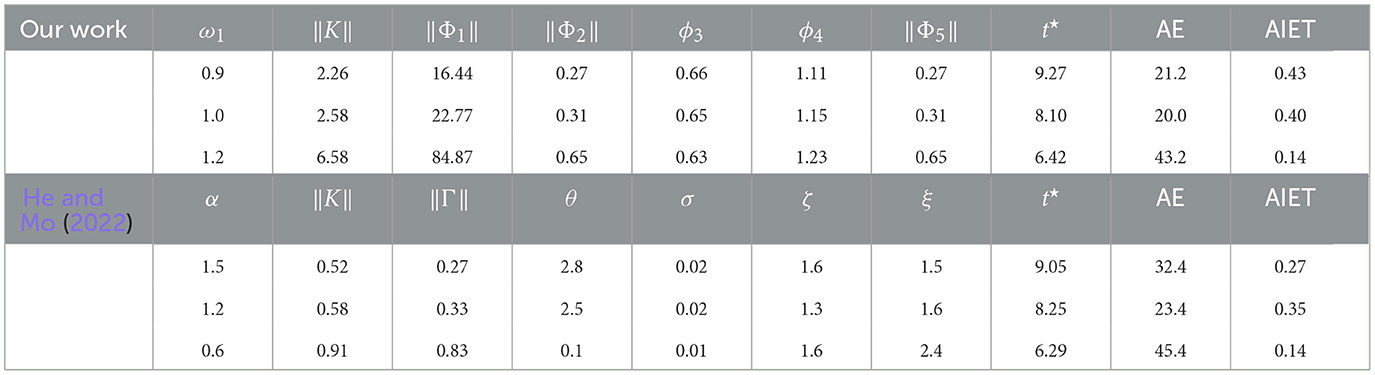
Table 3. Comparison between our work and He and Mo (2022).
6 Conclusion
This article proposes a resilient framework for consensus in multi-agent systems (MAS) using a distributed dynamic event-triggering control (DETC) protocol which reduces the burden of control updates. The MAS is under denial of service (DoS) attacks. In a general scenario, it is assumed that the DoS attack may target any arbitrary communication link between two agents in an asynchronous manner. The DoS attacks are thus categorized into connectivity-preserved DoS (CP-DoS) which does not impair the connectivity of the network, and connectivity-broken DoS (CB-DoS) which breaks the network into isolated sub-graphs. The implementation is based on the knowledge of the control gain and several DETC parameters. These parameters are co-designed through a unified distributed convex optimization. Numerical simulations are conducted to illustrate the capability of the proposed method. In future, we will study the sampled-data dynamic event-triggered control scheme for secondary control in microgrids under communication delay and asynchronous DoS attacks.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
AAm performed theoretical derivations with AM, MH, and AAs. AAm wrote the paper together with AM. AM and AAs supervised the study. All authors reviewed and revised the manuscript. All authors contributed to the article and approved the submitted version.
Funding
This project was partially supported by the Department of National Defence's Innovation for Defence Excellence and Security (IDEaS) program, Canada.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Footnotes
1. ^It is straightforward to show that Equation (61) also holds if t ∈ Wm.
References
Abdelrahim, M., Postoyan, R., Daafouz, J., and Nešić, D. (2014). “Co-design of output feedback laws and event-triggering conditions for linear systems,” in 53rd IEEE Conference on Decision and Control (Los Angeles, CA), 3560–3565. doi: 10.1109/CDC.2014.7039942
Amini, A., Asif, A., and Mohammadi, A. (2022). A unified optimization for resilient dynamic event-triggering consensus under denial of service. IEEE Trans. Cybernet. 52, 2872–2884. doi: 10.1109/TCYB.2020.3022568
Amini, A., Asif, A., Mohammadi, A., and Azarbahram, A. (2021). Sampled-data dynamic event-triggering control for networked systems subject to dos attacks. IEEE Transact. Netw. Sci. Eng. 8, 1978–1990. doi: 10.1109/TNSE.2021.3070804
Amini, A., Ghafouri, M., Mohammadi, A., Hou, M., Asif, A., and Plataniotis, K. (2022a). Secure sampled-data observer-based control for wind turbine oscillation under cyber attacks. IEEE Trans. Smart Grid 13, 3188–3202. doi: 10.1109/TSG.2022.3159582
Amini, A., Mohammadi, A., Asif, A., Hou, M., and Plataniotis, K. N. (2022b). Fault-tolerant periodic event-triggered consensus under communication delay and multiple attacks. IEEE Syst. J. 16, 6338–6349. doi: 10.1109/JSYST.2022.3183863
Amini, A. (2020). Event-Triggered Consensus Frameworks for Multi-agent Systems (PhD thesis), Concordia University, Montreal, QC, Canada.
Cao, L., Pan, Y., Liang, H., and Huang, T. (2023). Observer-based dynamic event-triggered control for multiagent systems with time-varying delay. IEEE Trans. Cybern. 53, 3376–3387. doi: 10.1109/TCYB.2022.3226873
Cheng, B., and Li, Z. (2019). Coordinated tracking control with asynchronous edge-based event-triggered communications. IEEE Trans. Automat. Contr. 64, 4321–4328. doi: 10.1109/TAC.2019.2895927
De Persis, C., and Tesi, P. (2015). Input-to-state stabilizing control under denial-of-service. IEEE Trans. Automat. Contr. 60, 2930–2944. doi: 10.1109/TAC.2015.2416924
Deng, C., Che, W.-W., and Wu, Z.-G. (2020). A dynamic periodic event-triggered approach to consensus of heterogeneous linear multiagent systems with time-varying communication delays. IEEE Trans. Cybern. 51, 1812–1821. doi: 10.1109/TCYB.2020.3015746
Deng, C., and Wen, C. (2020). Distributed resilient observer-based fault-tolerant control for heterogeneous multiagent systems under actuator faults and DoS attacks. IEEE Trans. Control. Netw. Syst. 7, 1308–1318. doi: 10.1109/TCNS.2020.2972601
Du, S., Sheng, H., Ho, D. W. C., and Qiao, J. (2023). Secure consensus of multiagent systems with DoS attacks via fully distributed dynamic event-triggered control. IEEE Trans. Systems Man Cybernet. 53, 6588–6597. doi: 10.1109/TSMC.2023.3283969
Du, X., Qu, S., Zhang, H., Xu, W., and Tang, Q. (2023). Distributed bipartite consensus for multi-agent systems with dynamic event-triggered mechanism. J. Franklin Inst. 360, 8877–8897. doi: 10.1016/j.jfranklin.2022.05.022
Feng, Z., and Hu, G. (2019). Secure cooperative event-triggered control of linear multiagent systems under DoS attacks. IEEE Trans. Control Syst. Technol. 28, 741–752. doi: 10.1109/TCST.2019.2892032
Ge, X., and Han, Q.-L. (2017). Distributed formation control of networked multi-agent systems using a dynamic event-triggered communication mechanism. IEEE Trans. Ind. Electron. 64, 8118–8127. doi: 10.1109/TIE.2017.2701778
Ge, X., Han, Q.-L., Zhang, X.-M., Ding, L., and Yang, F. (2019). Distributed event-triggered estimation over sensor networks: a survey. IEEE Trans. Cybern. 50, 1306–1320. doi: 10.1109/TCYB.2019.2917179
Girard, A. (2014). Dynamic triggering mechanisms for event-triggered control. IEEE Trans. Automat. Contr. 60, 1992–1997. doi: 10.1109/TAC.2014.2366855
Guo, G., Ding, L., and Han, Q.-L. (2014). A distributed event-triggered transmission strategy for sampled-data consensus of multi-agent systems. Automatica 50, 1489–1496. doi: 10.1016/j.automatica.2014.03.017
He, W., and Mo, Z. (2022). Secure event-triggered consensus control of linear multiagent systems subject to sequential scaling attacks. IEEE Trans. Cybernet. 52, 10314–10327. doi: 10.1109/TCYB.2021.3070356
He, W., Xu, B., Han, Q.-L., and Qian, F. (2019). Adaptive consensus control of linear multiagent systems with dynamic event-triggered strategies. IEEE Trans. Cybern. 50, 2996–3008. doi: 10.1109/TCYB.2019.2920093
He, W., Xu, W., Ge, X., Han, Q.-L., Du, W., and Qian, F. (2022). Secure control of multiagent systems against malicious attacks: a brief survey. IEEE Transact. Ind. Inform. 18, 3595–3608. doi: 10.1109/TII.2021.3126644
Hu, S., Yue, D., Xie, X., Chen, X., and Yin, X. (2019). Resilient event-triggered controller synthesis of networked control systems under periodic DoS jamming attacks. IEEE Trans. Cybern. 49, 4271–4281. doi: 10.1109/TCYB.2018.2861834
Hu, W., Liu, L., and Feng, G. (2015). Consensus of linear multi-agent systems by distributed event-triggered strategy. IEEE Trans. Cybern. 46, 148–157. doi: 10.1109/TCYB.2015.2398892
Hu, W., Yang, C., Huang, T., and Gui, W. (2018). A distributed dynamic event-triggered control approach to consensus of linear multiagent systems with directed networks. IEEE Trans. Cybern. 50, 869–874. doi: 10.1109/TCYB.2018.2868778
Li, X., Tang, Y., and Karimi, H. R. (2020). Consensus of multi-agent systems via fully distributed event-triggered control. Automatica 116, 108898. doi: 10.1016/j.automatica.2020.108898
Liu, H., and Wang, Z. (2021). Sampled-data-based consensus of multi-agent systems under asynchronous denial-of-service attacks. Nonlinear Anal. Hybr. 39, 100969. doi: 10.1016/j.nahs.2020.100969
Liu, J., Yin, T., Yue, D., Karimi, H. R., and Cao, J. (2020). Event-based secure leader-following consensus control for multiagent systems with multiple cyber attacks. IEEE Trans. Cybern. 51, 162–173. doi: 10.1109/TCYB.2020.2970556
Lu, A.-Y., and Yang, G.-H. (2018). Distributed consensus control for multi-agent systems under denial-of-service. Inf. Sci. 439, 95–107. doi: 10.1016/j.ins.2018.02.008
Meng, R., Hua, C., Li, K., and Ning, P. (2023). Dynamic event-triggered control for nonlinear stochastic systems with unknown measurement sensitivity. IEEE Transact. Circ. Syst. I Regular Pap. 70, 1710–1719. doi: 10.1109/TCSI.2022.3232915
Meng, X., and Chen, T. (2014). “Optimality and stability of event triggered consensus state estimation for wireless sensor networks,” in 2014 American Control Conference (Portland, OR), 3565–3570. doi: 10.1109/ACC.2014.6859035
Peng, C., and Li, F. (2018). A survey on recent advances in event-triggered communication and control. Inf. Sci. 457, 113–125. doi: 10.1016/j.ins.2018.04.055
Peng, C., and Yang, T. C. (2013). Event-triggered communication and H∞ control co-design for networked control systems. Automatica 49, 1326–1332. doi: 10.1016/j.automatica.2013.01.038
Qian, Y.-Y., Liu, L., and Feng, G. (2018). Distributed event-triggered adaptive control for consensus of linear multi-agent systems with external disturbances. IEEE Trans. Cybern. 50, 2197–2208. doi: 10.1109/TCYB.2018.2881484
Ren, W. (2007). Formation keeping and attitude alignment for multiple spacecraft through local interactions. J. Guid. Control Dynam. 30, 633–638. doi: 10.2514/1.25629
Shang, Y. (2021). Resilient group consensus in heterogeneously robust networks with hybrid dynamics. Math. Methods Appl. Sci. 44, 1456–1469. doi: 10.1002/mma.6844
Shang, Y. (2022). Median-based resilient consensus over time-varying random networks. IEEE Transact. Circ. Syst. II Exp. Briefs 69, 1203–1207. doi: 10.1109/TCSII.2021.3093466
Shang, Y. (2023). Resilient tracking consensus over dynamic random graphs: a linear system approach. Eur. J. Appl. Math. 34, 408–423. doi: 10.1017/S0956792522000225
Wang, J., Deng, X., Guo, J., and Zeng, Z. (2023). Resilient consensus control for multi-agent systems: a comparative survey. Sensors 23, 2904. doi: 10.3390/s23062904
Wang, J., Li, Y., Duan, Z., and Zeng, J. (2022). A fully distributed robust secure consensus protocol for linear multi-agent systems. IEEE Transact. Circ. Syst. II Exp. Briefs 69, 3264–3268. doi: 10.1109/TCSII.2022.3153698
Wu, Z.-G., Xu, Y., Pan, Y.-J., Su, H., and Tang, Y. (2018). Event-triggered control for consensus problem in multi-agent systems with quantized relative state measurements and external disturbance. IEEE Trans. Circuits Syst. I Reg. Pap. 65, 2232–2242. doi: 10.1109/TCSI.2017.2777504
Xu, W., He, W., Ho, D. W., and Kurths, J. (2022). Fully distributed observer-based consensus protocol: adaptive dynamic event-triggered schemes. Automatica 139, 110188. doi: 10.1016/j.automatica.2022.110188
Xu, W., Ho, D. W., Zhong, J., and Chen, B. (2019). Event/self-triggered control for leader-following consensus over unreliable network with DoS attacks. IEEE. T. Neur. Net. Lear. 30, 3137–3149. doi: 10.1109/TNNLS.2018.2890119
Xu, Y., Fang, M., Shi, P., and Wu, Z.-G. (2019). Event-based secure consensus of mutiagent systems against DoS attacks. IEEE Trans. Cybern. 50, 3468–3476. doi: 10.1109/TCYB.2019.2918402
Xu, Y., Fang, M., Wu, Z.-G., Pan, Y.-J., Chadli, M., and Huang, T. (2018). Input-based event-triggering consensus of multiagent systems under denial-of-service attacks. IEEE Trans. Syst., Man, Cybern. 50, 1455–1464. doi: 10.1109/TSMC.2018.2875250
Yang, H., and Ye, D. (2022). Observer-based fixed-time secure tracking consensus for networked high-order multiagent systems against DoS attacks. IEEE Trans. Cybernet. 52, 2018–2031. doi: 10.1109/TCYB.2020.3005354
Yang, R., Liu, L., and Feng, G. (2022). Leader-following output consensus of heterogeneous uncertain linear multiagent systems with dynamic event-triggered strategy. IEEE Trans. Syst. Man Cybernet. 52, 1626–1637. doi: 10.1109/TSMC.2020.3034352
Yang, Y., Li, Y., and Yue, D. (2020). Event-trigger-based consensus secure control of linear multi-agent systems under DoS attacks over multiple transmission channels. Sci. China Inf. Sci. 63, 1–14. doi: 10.1007/s11432-019-2687-7
Yi, X., Liu, K., Dimarogonas, D. V., and Johansson, K. H. (2018). Dynamic event-triggered and self-triggered control for multi-agent systems. IEEE Trans. Autom. Control 64, 3300–3307. doi: 10.1109/TAC.2018.2874703
Yi, X., Yang, T., Wu, J., and Johansson, K. H. (2019). Distributed event-triggered control for global consensus of multi-agent systems with input saturation. Automatica 100, 1–9. doi: 10.1016/j.automatica.2018.10.032
Zha, L., Liu, J., and Cao, J. (2019). Resilient event-triggered consensus control for nonlinear muti-agent systems with DoS attacks. J. Franklin Inst. 356, 7071–7090. doi: 10.1016/j.jfranklin.2019.06.014
Zhang, B., Dou, C., Yue, D., Zhang, Z., and Zhang, T. (2019). A packet loss-dependent event-triggered cyber-physical cooperative control strategy for islanded microgrid. IEEE Trans. Cybern. 51, 267–282. doi: 10.1109/TCYB.2019.2954181
Zhang, D., and Feng, G. (2019). A new switched system approach to leader-follower consensus of heterogeneous linear multiagent systems with dos attack. IEEE Trans. Syst. Man Cybern. Syst. 51, 1258–1266. doi: 10.1109/TSMC.2019.2895097
Zhang, D., Liu, L., and Feng, G. (2018). Consensus of heterogeneous linear multiagent systems subject to aperiodic sampled-data and DoS attack. IEEE Trans. Cybern. 49, 1501–1511. doi: 10.1109/TCYB.2018.2806387
Zhang, T.-Y., and Ye, D. (2021). Distributed event-triggered control for multi-agent systems under intermittently random denial-of-service attacks. Inf. Sci. 542, 380–390. doi: 10.1016/j.ins.2020.06.070
Keywords: multi-agent systems, consensus, dynamic event-triggering control, asynchronous DoS, autonomous systems
Citation: Amini A, Mohammadi A, Hou M and Asif A (2024) Secure dynamic event-triggering control for consensus under asynchronous denial of service. Front. Comput. Sci. 5:1125124. doi: 10.3389/fcomp.2023.1125124
Received: 15 December 2022; Accepted: 11 December 2023;
Published: 09 February 2024.
Edited by:
Haibin Zhu, Nipissing University, CanadaReviewed by:
Yilun Shang, Northumbria University, United KingdomShaohua Teng, Guangdong University of Technology, China
Copyright © 2024 Amini, Mohammadi, Hou and Asif. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Arash Mohammadi, YXJhc2gubW9oYW1tYWRpQGNvbmNvcmRpYS5jYQ==
 Amir Amini
Amir Amini Arash Mohammadi
Arash Mohammadi Ming Hou3
Ming Hou3