Abstract
This study proposes a polymorphic cooperative control system for microgrid consisting of a service layer, a control layer, a data layer, and a power layer to apply a resilient-distributed secondary control strategy to distributed generators (DGs) from different manufacturers more conveniently. Due to the improvement of network openness, external cyberattacks are more likely to tamper with the neighbor information transmitted in the cooperative control system. In this study, a discrete-time resilient-distributed secondary control strategy is designed to resist potential unbounded false data injection (FDI) attacks, which introduces a virtual network layer interconnecting the control network layer to form a layered network. The strategy can maintain the stability of voltage and frequency under unbounded attacks and then greatly suppress the state estimation difference of voltage and frequency. Meanwhile, the unbounded attack depending on voltage and frequency estimation difference is suppressed to a nearly bounded attack. Finally, a microgrid consisting of six inverter-based DGs is taken as an example to validate the effectiveness of the strategy against unbounded attacks.
1 Introduction
With the rapid development of power electronic devices and new energy technology, the power system has gradually transitioned to the stage of a new electric power system characterized by a high proportion of new energy and power electronic devices (Zhou et al., 2020; Tang et al., 2022). As an important part of the new electric power system, microgrid integrates geographically dispersed, intermittent and random new energy, and internal energy storage devices can adjust the flow of electric energy flexibly (Zhou J. et al., 2021; Wang et al., 2021). With the increase of the proportion of new energy, a large number of power electronic devices, such as rectifiers and inverters, have appeared in the microgrid to replace original generators with the rotor to generate power. Since power electronic devices cannot provide the inertia from generators with rotors, the frequency of microgrids is more susceptible to be disturbed. For microgrids with a high proportion of new energy and power electronic devices, distributed secondary control (Bidram et al., 2014) has attracted wide attention as an effective strategy to maintain voltage and frequency stability.
The distributed secondary control strategy relies on advanced communication facilities and network structure to exchange neighbor information. The development of the communication network structure of microgrid mainly includes three stages, i.e., IP-based network, software-defined network (SDN) (Nunes et al., 2014; Kreutz et al., 2015), and a polymorphic network with full-dimensional definition (Hu et al., 2020, 2022; Zhang et al., 2022). The IP-based network combines the function of the control layer and the data layer in the forwarding devices, which makes it difficult for researchers to test advanced control methods and hinders the innovation of network structure. SDN separates the function of the control layer and data layer. Network devices in the data layer only remain the function of forwarding data, and the function of calculating routes is centralized in the control layer. Due to the function separation, the control layer of SDN provides more programmable ports for microgrid managers to design and implement advanced control methods. In order to make the network requirements of various DGs produced by different manufacturers in microgrids can be realized on the same communication facilities in the data layer, a polymorphic network has been established which supports various network technology. A polymorphic network is integrated into a service layer, a control layer, and a data layer, where the control layer and the data layer still maintain the separated functions. A polymorphic network is an advanced network structure that can support a resilient distributed secondary control strategy applied in the microgrid. Neighbor information of various DGs can be exchanged on the same communication facilities, which benefits improving consensus performance of cooperative control among the DGs, and even microgrids.
The more advanced the network structure, the more open it will be. Both communication links and terminals are possibly subject to potential cyberattacks (Gao et al., 2022). Common attacks in the microgrid include denial of service (DoS) and FDI attacks. DoS attacks send a large number of packets to block the communication network to prevent information exchange between the neighbor DGs. Technologies such as firewalls (Salah et al., 2012) and gates (Condry and Nelson, 2016) can effectively defend against the threat of DoS attacks launched in the communication network of the microgrid. FDI attacks are characterized by tampering with the exchanged information between the neighbor DGs. The DG receives the tampered neighbor information but does not know it, and then transmits the tampered information to other neighboring DGs. In fact, it is difficult for us to defend FDI attacks by methods against DoS attacks because of their strong stealth. Therefore, how to design a proper distributed secondary control strategy against FDI attacks has been a noteworthy topic for researchers. At present, the solution to FDI attacks in the distributed secondary strategy mainly includes two scheme types. The first scheme is to design detection algorithms to isolate the attacked communication channels. The second scheme is to design resilient distributed secondary control strategies to mitigate the impact of FDI attacks in the microgrid. In such resilient strategies, FDI attacks exist together with the microgrid, and resilient distributed control strategies aim to minimize or even eliminate the impact of FDI attacks on consensus performance as much as possible. Liu et al. defined FDI attacks in state estimation of centralized power systems (Liu et al., 2009, 2011). After this, many algorithms emerged to detect FDI attacks in the microgrid. The work in Manandhar et al. (2014) shows that although the χ2 detector can detect faults and DoS attacks, it cannot detect well-designed FDI attacks. In order to overcome this limitation, a Euclidean detector that can effectively detect FDI attacks is proposed. Yang et al. (2022) proposed a method for detecting bad data in power transformers based on artificial intelligence. Fawzi et al. (2014) studied the estimation problem of linear systems when some sensors or actuators are destroyed by attackers, and especially pointed out that if more than half of the sensors are attacked, it is impossible to accurately reconstruct the state of the system. Wang et al. (2020) proposed a local detection and isolation algorithm which can solve the problem of undetectable attacks through the combination of observable PMU or smart sensors. Chen et al. (2021) proposed an aperiodic intermittent control strategy with random switching frequency to detect and isolate the attacked communication channels. Hu et al. (2018) and Pang et al. (2022) studied the impact of stealthy FDI attacks on the communication channels and points out that if some key communication channels are well protected, the attack behaviors will be detected.
Such detection algorithms can effectively detect FDI attacks launched in the communication channels. When the DG exchanges information with its neighbors, detection algorithms will reduce the range of the attacked DGs through time iteration, and finally determine which DG has been attacked. The process is called computation response time that often requires the microgrid system to allocate resources to complete. Therefore, isolation measures will be delayed accordingly. The impact which FDI attacks can cause is serious during the detection time between attacks launched and eliminated. Researchers have become more interested in developing resilient distributed secondary control strategies against FDI attacks to address this problem. Zeng and Chow (2014) proposed a trust-based resilient distributed secondary control strategy, which embeds a recovery mechanism in the distributed control process and enhances the resilience against FDI attacks. Abhinav et al. (2018) designed a trust-based resilient distributed secondary control strategy against FDI attacks launched in sensors, actuators, and communication channels. Under the condition that at least half of the neighbors of each DG are secure, this strategy can defend against time-independent constant FDI attacks. Gharesifard and Başar (2012) introduced a virtual network interconnecting with the original control network to make the overall dynamic network resilient against FDI attacks with linear dynamics by designing appropriate interconnection matrices. Gusrialdi et al. (2014) extended the work of Gharesifard and Başar (2012) to the case of strongly connected directed graphs. Abhinav et al. (2018) studied the case of directed graphs and attacks with nonlinear dynamics based on the work of Gharesifard and Başar (2012) and Gusrialdi et al. (2014).
Researchers introduced the layered network theory proposed by some studies (Gharesifard and Başar, 2012; Gusrialdi et al., 2014; Abhinav et al., 2018) to the FDI attack problem of networked microgrids, and Zhou Q. et al. (2021) and Chen et al. (2021) introduced the layered network theory into distributed secondary control strategy to deal with FDI attacks launched in the communication network. Liu et al. (2022) proposed a resilient distributed optimal frequency control scheme to deal with the impact of FDI attacks by introducing the layered network theory. Zuo et al. (2020) proposed a novel concept of the cooperative and adversarial multigroup system consisting of leaders, followers, and adversaries. Zuo and Yue (2022) designed a resilient containment control method against the unbounded FDI attacks occurring in the communication network of the multigroup system proposed by Zuo et al. (2020), and it is worth mentioning that the unbounded FDI attack in this study is modeled as a proportional function of time. Unbounded attacks modeled in this way are very destructive but can be easily perceived by detectors. A more realistic attack design method is to generate a destructive and stealthy attack sequence based on the matrix parameters of the microgrid (Hu et al., 2018). The attack sequence can make the state estimation difference of the microgrid go to ∞ without being perceived by the χ2 detector. As mentioned previously, detection and isolation measures can cause a high computational burden for the microgrid. During the calculation process of detection and isolation measures, external FDI attacks will still cause irreparable impacts on the microgrid. Therefore, how to resist this kind of destructive and stealthy unbounded attack sequence has been a novel problem.
In this study, a discrete-time resilient distributed secondary control strategy is designed to resist the impact of unbounded attack sequences on the microgrid. The main contributions of this study are as follows.
1) A polymorphic cooperative control system for microgrids consisting of a service layer, a control layer, a data layer, and a power layer is established in this study, which can apply the resilient distributed secondary control strategy to DGs from different manufacturers.
2) Considering potential unbounded FDI attacks in the polymorphic cooperative control system, a discrete-time resilient distributed secondary control strategy is designed to maintain voltage and frequency stable against unbounded attacks.
3) The state estimation difference of voltage and frequency are suppressed by a large margin. Sufficient time is provided for the deployment of detection and isolation measures before the service layer of the polymorphic cooperative control system makes wrong decisions. Meanwhile, the unbounded attack depending on voltage and frequency estimation difference is suppressed to a nearly bounded attack, which is less threat to the microgrid.
The rest of this study is organized as follows. Section 2 introduces the microgrid polymorphic cooperative control system and the function of each layer. Section 3 describes the influence of unbounded FDI attack on the microgrid, then designs a resilient distributed secondary control strategy against attacks, and finally uses Lyapunov theory to prove the stability of the strategy. Section 4 validates the effectiveness of the proposed strategy by a test microgrid with six inverter-based DGs. Finally, Section 5 presents the summary of this study.
2 Structure of the polymorphic cooperative control system
A polymorphic network is an advanced network structure supporting the microgrid operation, which can change control strategy in real-time according to the operation characteristics of the microgrid. Moreover, various DGs produced by different manufacturers can transmit information in the data layer of the polymorphic network. The polymorphic cooperative control system established in this study is shown in Figure 1. The polymorphic cooperative control system consists of four layers: a service layer, a control layer, a data layer, and a power layer. The service layer, control layer, and data layer constitute the polymorphic network to support the cooperative control of DGs in the power layer. The service layer is the center of the polymorphic cooperative control system, which integrates data monitoring, resource allocation, control strategy design, and other functions; and is open to microgrid managers. Managers can design and deploy distributed secondary control strategies by obtaining matrix parameters of microgrids through the service layer. In the control layer, a polymorphic identification table is configured in the distributed controller, which supports the coexistence and collaboration of IP, content, identification, geospatial location, and other identities in the same data layer. In addition, the distributed secondary control strategy deployed through the service layer is also installed in the distributed controller. According to the polymorphic identification table configured in the control layer, the data layer divides the polymorphic data packets uploaded through terminals in the power layer into corresponding polymorphic data transmission channels. These polymorphic packets are encapsulated and forwarded to the next network device to realize the resilient distributed secondary control strategy installed in the distributed controller. The interaction between the layers is realized through programmable ports. The upper layer transmits instructions to the lower layer, and the lower layer feeds back the collected information to the upper layer.
FIGURE 1

Microgrid polymorphic cooperative control system.
The service layer, control layer, and data layer of the microgrid polymorphic cooperative control system achieve the information transmission through programmable ports and separate the control function from the forwarding function. In fact, DGs in the microgrid are not provided by the same manufacturer and often support different network protocols and data package types. If a new control strategy is applied in the microgrid, managers need to manually adjust the configuration of DGs, which is undoubtedly not beneficial to the innovation of the control strategy. However, the polymorphic identification table configured in the control layer and the polymorphic data transmission channels in the data layer can make these various DGs plug and play in the same network environment. The control layer customizes the channels into processing units suitable for polymorphic data packets by programming FPGA. In this way, the microgrid polymorphic cooperative control system can define the functions of each network layer to support the realization of distributed secondary control strategy applied in the large-scale heterogeneous DGs.
3 Resilient-distributed secondary control strategy against the unbounded FDI attack sequence
3.1 Graph preliminaries
The communication topology of microgrid discussed in this study is described as a directed graph ς including N + m agents. Aa = [aij] ∈ RN×N is the weighted adjacency matrix of ς, and aij denotes the weight value of the edge between the follower nodes, aij > 0 represents DGi that can receive information from DGj, otherwise aij = 0. D = diag (di) ∈ RN×N is the in-degree matrix for ς, where . L = D − Aa means the Laplace matrix of ς. Define Gl = diag (gli) ∈ Rnxn, l = (1, 2, …, m), where gli denotes the gain between the lth leader and ith follower. And a nomenclature containing sets, parameters, and abbreviations is shown in Table 1.
TABLE 1
| Symbol | Description |
|---|---|
| Index and sets | |
| i, j | Index of DGs |
| (⋅)T | Transpose of the matrix |
| ‖ ⋅‖ | Euclidean norm of the vector |
| diag (⋅) | Diagonal matrix |
| Parameters | |
| N | Number of DGs |
| m | Number of leader DGs |
| aij | Gains between DGs |
| gli | Gains between leader DGs and follower DGs |
| In | n dimensional identity matrix |
| IN×n | N × n dimensional identity matrix |
| Ie | Identity matrix of uncertain dimensions that |
| aligns the dimensions of the equality matrix | |
| Θ(k) | Unbounded attack sequence |
| Σs | Control layer |
| Σh | Virtual layer |
| Abbreviations | |
| FDI | False data injection |
| DGs | Distributed generators |
| DoS | Denial of service |
| SDN | Software-defined network |
Nomenclature table.
3.2 Problem formulation
The inherent distributed characteristics of DGs in microgrid make distributed control a more suitable secondary control strategy to adjust voltage and frequency. Microgrid managers can design proper distributed secondary control strategy to maintain voltage and frequency stable around the rated value. Only part of DGs can receive the reference information, and then complete the task in a cooperative manner through the communication network. For first-order linear multi agent systems (MASs), the distributed secondary control of microgrid with N DGs can be transformed into a synchronization problem. The local expression for the distributed secondary control strategy used to control voltage and frequency iswhere T is the sampling time of microgrid. , Vi(k) denotes the voltage of DGi, fi(k) denotes the frequency of DGj. , Vj(k) denotes the voltage of DGj, fj(k) denotes the frequency of DGj. , Vl(k) denotes the reference voltage of DGs, fl(k) denotes the reference frequency of DGs, l = 1, 2, …, m denotes the number of leaders. Obviously, the influence caused by FDI attacks has not been considered in the distributed secondary control strategy. The neighbor information DGi received from DGj is when adversaries launched FDI attacks in the communication channels between DGi and DGj. represents the neighbor information DGi received from DGj has been tampered by Θi,j(k). The local expression for the distributed secondary control strategy when the communication channels have been launched FDI attacks is
Also, then the global form of Eqn. 2 can be obtained aswhere denotes all the DGs′ voltage and frequency state variable. Define , and denotes the global form of unbounded attack sequence. Define βl = 10L + Gl, and (L ⊗ Ie) (1n ⊗ xl) = 0. Eqn. 3 can be rewritten as
When there exists no attacks in the communication channels, the voltage and frequency state variable x(k) and measurement output y(k) are shown as
The following state estimator is proposed for voltage and frequency state variable x(k):where and C is the measurement matrix, and denotes the state estimation value at time k + 1. z(k) denotes the estimation residual difference at time k, which is related to whether FDI attacks can be detected. If z(k) is less than a constant value, the detector will not perceive the attacks. K denotes Kalman gain, although the standard Kalman filter is time-varying, the Kalman filter can rapidly enter steady state at exponential speed from any initial conditions (Huang et al., 2020). K can be obtained from Eqs. 7, 8where Q and R commonly denote the covariance of the noise in Kalman filter, and they can also be used as parameters for strategy design in noiseless environment. The application of state estimation in noiseless environment is discussed in Rapp and Nyman (2004) and Dutta et al. (2019). In principle, they can be selected as any positive definite matrices. Combine with Eqn. 4, when attacks have been launched in the communication channels, the voltage and frequency state variable x(k) and measurement output y(k) are shown aswhere xa (k + 1) denotes the voltage and frequency state variable under attacks, and ya(k) denotes the measurement output under attacks. Accordingly, the state estimator for voltage and frequency under attacks can be shown aswhere denotes under attacks at time k + 1, and za(k) denotes z(k) under attacks at time k. Define and Δz (k + 1), which denote state estimation difference and the estimation residual difference, respectively. And the dynamic expression of and Δz (k + 1) can be obtained aswhere , and xa (k + 1) − x (k + 1) ≠ 0 represents the iteration process of and Δz (k + 1) has been affected by the unbounded attack sequence Θ(k). The attack sequence Θ(k) that depends on can satisfy and simultaneously, where M is a positive predetermined detection threshold. represents that with the iteration of discrete time k, the voltage and frequency state estimation under unbounded attacks gradually deviates from the normal value. Since and the generation process of Θ(k) depend upon , can be achieved. This study considers that Θ(0) = 0 and the attack generation algorithm will be proposed later. represents , the unbounded attack sequence Θ(k) will not trigger the traditional χ2 detection.
The work of Hu et al. (2018) also inspires that protecting key communication channels can detect this stealthy unbounded attack sequence. Currently, phase measurement units (PMUs) are the most common equipment to protect communication channels (Mabaning et al., 2017; Tahabilder et al., 2017; Pei et al., 2020), which are more reliable than detectors. Algorithms detecting and isolating attacks often need to consume a lot of computing resources, and the detection and isolation process that relies on the limited number of PMUs always has a certain time delay. The unbounded attack sequence which depends on will cause irreversible damage to the microgrid during the process. This study proposes a discrete-time resilient distributed secondary control strategy based on a layered network to greatly suppress the divergence degree of during the process, and the impact Θ(k) can cause will be equal to a bounded attack sequence accordingly. It can be seen from Eqn. 11 that although xa (k + 1) and x (k + 1) are extremely close under the strategy proposed in this study, xa (k + 1) − x (k + 1) keeps accumulating during the iteration process of , and still will tend to diverge after a long enough time. As shown in Figure 2, the strategy proposed in this study plays an essential role in the period from the beginning of FDI attack generation to the end of detection and isolation measures to enhance the resilience of the microgrid against attacks.
FIGURE 2

Function of the resilient-distributed control method proposed in this study in the process of unbounded attacks generation, state estimation, and detection.
The following assumptions are made in this study:
Assumption 1: This monotonous unbounded attack sequence can generate at a limited rate, in other words, , where c is a positive scalar.
Assumption 2: FDI attacks cannot be launched on sensor devices directly, but only in sensor communication networks.
Assumption 3: The attacker has perfect knowledge about the system model, that is, information the attacks generation algorithm requires can be obtained by the attacker.
3.3 Resilient-distributed secondary strategy based on the layered communication network
This section introduces a virtual layer Σh based on the layered network (Gusrialdi et al., 2018) to interconnect with the original control layer Σs to form a layered communication network to enhance the resilience of the control layer Σs against unbounded FDI attacks, the layered network is shown in Figure 3, where the virtual layer Σh has no physical meaning, and it would be difficult for adversaries to associate the information in the virtual layer Σh with the measurements of voltage and frequency in the control layer Σs. There exist studies that have investigated attacks in the virtual layer Σh, but it is obvious that adversaries need more computing resources to launch attacks in the virtual layer Σh. Therefore, most work based on the layered network prefer to study attacks in the control layer Σs. The discrete-time resilient distributed secondary control strategy proposed in this study considers the unbounded attack sequence launched in the control layer Σs, and Lyapunov theory is used to validate the stability of the strategy in this section.
FIGURE 3

Structure of the layered communication network formed by introducing a virtual network layer.
The layered network consisting of the control layer Σs and the virtual layer Σh can be shown in Figure 3. The control layer Σs and the virtual layer Σh have the same number of nodes, and the reference information is transmitted to the nodes in the control layer Σs and virtual layer Σh at the same time. After the unbounded attack sequence is launched in the control layer Σs, the layered network will generate a compensation sequence through the observer constituted by Eqs. 14, 15 so that the control layer Σs as shown in Eqn. 13 can resist the impact of the unbounded attack sequence Θ(k).where denotes the state of nodes in the virtual network layer Σh, v(k) = x(k) − η(k) denotes the difference between the control layer Σs and the virtual layer Σh at time k, and denotes the compensation sequence. It can be seen that Eqs. 14, 15 together form an observer to generate a compensation sequence through which the impact of unbounded attack sequence in the control layer can be eliminated. Define errors between information in the leader node and that in the nodes of control layer Σs and virtual layer Σh as (16) and (17) respectively:
Theorem 1: When the unbounded attack sequence Θ(k) which depends on state estimation difference satisfying assumption 1 has been launched in the communication network of microgrid as shown in Eqn. 5, the resilient distributed secondary control strategy based on the layered network as shown in Eqs. 13–15 is designed to resist the impact Θ(k) can cause. If e1(k) in Eqn. 16 is stable, it can be said that the control layer Σs shown in Eqn. 13 can resist the unbounded attack sequence Θ(k) and maintain voltage and frequency stable.
Proof: Define , and make the difference between Eqs. 13, 14 to obtain Eqn. 18:Eqn. 19 can be obtained from Eqn. 15:
Rewriting Eqs. 18, 19 in the following compact form yields
Define , , and m (k + 1) = A2m(k), where . Choose a Lyapunov function candidate as
Given assumption 1, is a monotonous and limited-growth unbounded attack sequence, and Θ(0) = 0. Therefore, is positive-definite at arbitrary time k. Next, choose a Lyapunov function candidate to prove the stability of Eqn. 20:where Ps > 0 is an arbitrary symmetric and positive-definite matrix, and Vd(k) > 0 is known from Eqn. 21. Therefore, V(k) is positive-definite at arbitrary time k. The difference form of Eqn. 22 is can be obtained asThere exists a symmetric and positive-definite matrix Ps such that for an arbitrary symmetric and positive-definite matrix Q. Given assumption 1, can be obtained, that is, . Through the aforementioned analysis, V (k + 1) − V(k) < 0 can be obtained at arbitrary time k. Therefore, v(k) and are stable. From Eqs. 16, 17, e1(k) = v(k) + e2(k) can be obtained. In order to prove the stability of e1(k), the stability of e2(k) also should be proved. Combine with Eqn. 14, the difference form of Eqn. 17 can be obtained as
Choose a Lyapunov function candidate as , its difference form can be shown asThere exists a symmetric and positive-definite matrix Q′ such that , that is, V′(k + 1) − V′(k) < 0. Therefore, e2(k) is stable. Since e1(k) = v(k) + e2(k), the stability of e1(k) can be proved. The proof of Theorem 1 has completed here, which indicates the distributed secondary strategy proposed in this study can defend attacks to maintain the voltage and frequency stable.
3.4 Design of the unbounded attack sequence
This section will introduce the generation process of the unbounded attack sequence Θ(k), and how it destroys the state estimation of microgrid. The specific design principle of parameters required in algorithm is shown in Hu et al. (2018), The generation algorithm of unbounded attack sequence is shown in Table 2. where the length of is N × n, and all its elements equal to 0 except the sth element equal to 1. How to select s can only be determined after the matrix parameters of microgrid are selected, which will be given in the next section. The unbounded attack sequence depends on the state estimation difference at time k, and is a constant column vector. Since the existence of , Θ(k) will make be continuously increasing after time k = 1, and will make be continuously increasing in turn. Finally, when , . The resilient distributed secondary control strategy proposed in this study, mitigating attacks rather than eliminating them, can restore xa (k + 1) to x (k + 1), so that xa (k + 1) − x (k + 1) is close to 0. In this way, compared with the distributed secondary control strategy, the resilient strategy proposed in this study can suppress in Eqn. 11 and Δz (k + 1) in Eqn. 12. Since the unbounded attack sequence Θ(k) depends on which is greatly suppressed before detection and isolation mearsures completed, the divergence trend of Θ(k) is also greatly suppressed. The impact of Θ(k) can be equaled to that caused by a bounded attack sequence, which greatly alleviates the threat to the microgrid. The resilient distributed secondary strategy proposed in this study only plays a role in the suppression process of Θ(k) and , but cannot eliminate them completely. To eliminate the impact of this kind of unbounded attack sequence on microgrid, one should find a way to detect and isolate attacks is essential. How to protect key communication channels to detect stealthy unbounded attacks is an interesting topic, and authors will think about how to realize the idea in future research.
TABLE 2
| Algorithm for generating an unbounded attack sequence |
|---|
| Initialization parameter |
| Define |
| Choose a arbitrary φ ∈ (0, 1), and the detection threshold M = 2 |
| whilek ≥ 0 do |
| Set , φ(0) = 0 |
| Calculate |
| Calculate |
| + KC(xa (k + 1) − x (k + 1))] |
| k = k + 1 |
| φ(k) = φ |
| end while |
Algorithm for generating an unbounded attack sequence.
4 Case study
In this section, a test microgrid consisting of six inverter-based DGs is used to verify the effectiveness of the method proposed in this study against unbounded attack sequence Θ(k) (Bidram et al., 2013; Xu et al., 2019; Ge et al., 2021). The effectiveness of a resilient distributed secondary control strategy against unbounded attacks is that the voltage and frequency of each DG can still operate within the allowable fluctuation range near the rated value when the neighbor information has tampered. The influence of unbounded attack sequence on microgrids is analyzed by simulation when the elastic distributed secondary control strategy proposed in this study is adopted.
The power layer structure consisting of six inverter-based DGs illustrated in this study is shown in Figure 4. And the microgrid parameters are as follows:
FIGURE 4

Physical structure and communication network topology of the microgrid illustrated in this study.
T = 0.001s, aij = 10, gli = 0.001, N = 6, n = 2, m = 2, C = IN×n = I12,
Q = diag (0.01, 0.01, 0.01, 0.001, 0.001, 0.001, 0.01, 0.01, 0.01, 0.001, 0.001, 0.001),
R = diag (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1),
In the unbounded attack generation algorithm, φ = 0.1, . Define the reference information vector , which represents all the DGs need to follow the reference voltage 380V and frequency 50Hz.
First, the distributed secondary control strategy as shown in Eqn. 4 is used to maintain voltage and frequency stability. Next, the unbounded attack sequence is launched into the communication channels. As shown in Eqn. 9, Θ(k) destroys the iterative process in the form of TΘ(k). As shown in Figure 5A, the unbounded attack sequence given by algorithm 1 can destroy the iterative process of V2(k), V3(k), V5(k), and V6(k), that is, the voltage consensus performance of DG2, DG3, DG5, and DG6 is destroyed. Information exchange under attacks will make all the DGs’ voltage tend to ∞ with the iteration of the sampling time T. Figure 5B shows that the frequency of DGs has not been destroyed. Combine with Figure 5A and Figure 5B, the distributed secondary control strategy is still effective in the absence of Θ(k), but the voltage consensus performance will be destroyed under Θ(k).
FIGURE 5
Performance of the distributed secondary control strategy against unbounded attack sequence Θ(k): (A) voltage; (B) frequency.
Figure 6A shows the generation process of Θ(k) launched in Figure 5A. Figure 6B shows the voltage estimation difference of DGs under Θ(k). Since frequency has not been tampered, .
FIGURE 6

(A) Generation process of Θ(k) in Figure 5; (B) voltage estimation difference of DGs.
TΘex1(k) denotes TΘ1(k) and TΘ4(k), and denotes and . Figure 6 indicates the generation process of Θi1(k) depends on indeed. Also, then Θi1(k) will increase in turn. However, this phenomenon is profitless for voltage stability. During the period between the initialization of Θ(k) and completion of detection and isolation measures, the Θ(k) which diverges rapidly will cause irreversible effects on the microgrid. When the voltage exceeds the rated range allowed by the microgrid, the power circuit breakers inside the microgrid will act to disconnect the main circuit and stop operation. The renewable energy equipment inside the microgrid is expensive, which cannot stand the permanent damage such sudden breakdown causes. Obviously, it is not a wise choice to let such attacks diverge rapidly and put all hope in detection and isolation measures. The resilient distributed secondary control strategy proposed in this study can greatly suppress the divergence of Θ(k), and prevent the microgrid from being attacked to the point of crash before the completion of the whole process of detection and isolation measures.
It can be seen that Θ(k) is approximated into an attack sequence with minimal growth rate. Before completion of detection and isolation algorithms, relative to the original divergence, the impact of the suppressed Θ(k) can cause equal to a bounded attack sequence.
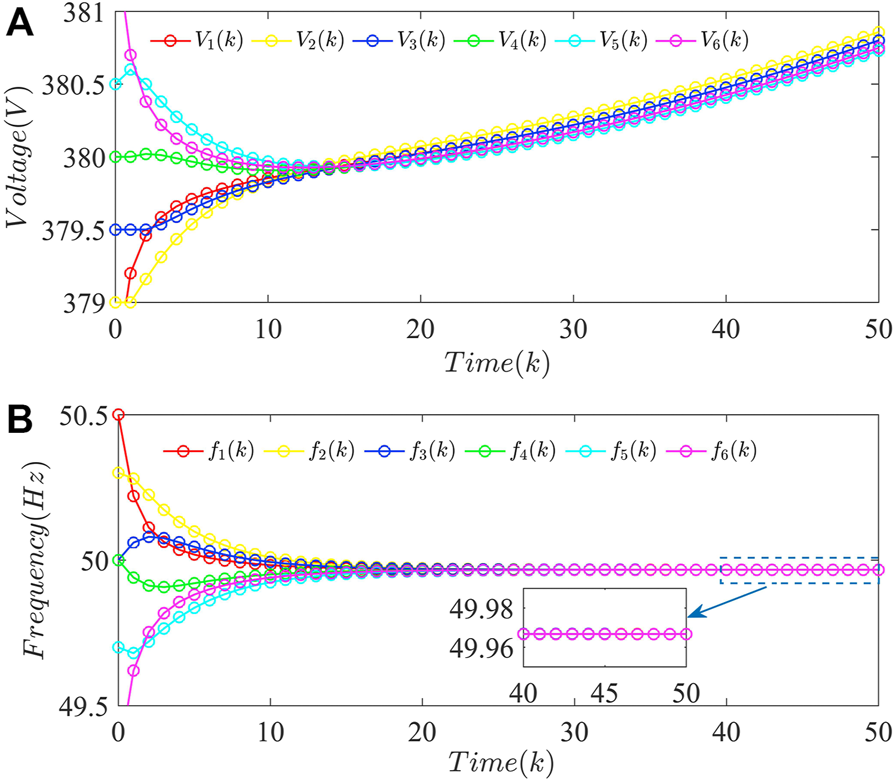
Figure 7 shows the performance of the resilient distributed secondary control strategy proposed in this study against the unbounded attack sequence Θ(k). It can be seen from Figure 7A that the voltage of DGs can still converge to the allowable range of the reference value 380 V under the impact of the unbounded attack sequence Θ(k). Moreover, Figure 7B shows the frequency of DGs can maintain stability, which indicates the resilient distributed secondary control strategy proposed in this study can also achieve the desired control objectives when there exist no attacks. It is worth mentioning that this strategy can make voltage under attacks Va(k) close to that without attacks V(k), that is, Va(k) − V(k) is close to 0. Given Algorithm 1, if can be suppressed, and then Θ(k) also will be extremely suppressed. Figure 8 shows the voltage estimation difference of DGs using the resilient distributed secondary control strategy proposed in this study. Combine with Figure 6 and Figure 8, it is obvious that can be suppressed by the distributed secondary control strategy proposed in this study.
FIGURE 7

Performance of the resilient-distributed secondary control strategy proposed in this study against the unbounded attack sequence Θ(k): (A) voltage; (B) frequency.
FIGURE 8

Voltage estimation difference using the resilient-distributed secondary control strategy proposed in this study.
Figure 9 shows performance of the generation process of Θ(k) which depends on after the voltage estimation difference has been suppressed. As shown in Figure 9, the unbounded attack sequence Θ(k) is approximated into an bounded attack sequence with minimal growth rate under the resilient distributed secondary control strategy. From Eqn. 12, can be obtained. The resilient distributed secondary control strategy suppresses and xa (k + 1) − x (k + 1), which leads to as shown in Figure 10. However, it does not violate the original intention of the resilient distributed secondary control strategy, which is designed to mitigate attacks rather than detect them. It is acceptable to gain greater resilience against unbounded attack sequence at the cost of reducing . The detection and isolation measures, such PMUs, will replace the traditional detectors by protecting key communication channels in the Σs to detect Θ(k). Face to well-designed unbounded attack sequence, how to deploy protection devices in the minimum number of key communication channels has become an important topic in future research. One of authors’ future work is how to integrate mitigation and detection processes to solve the problem of such unbounded attack sequence Θ(k) completely.
FIGURE 9

Unbounded attack sequence Θ(k) suppressed by the resilient-distributed secondary control strategy proposed in this study.
FIGURE 10

Voltage estimation residual difference Δzi1(k) of DGs using the resilient-distributed secondary control strategy proposed in this study.
5 Conclusion
This study has studied the impact of a class of unbounded attack sequence Θ(k) launched in the polymorphic cooperative control system. A discrete-time resilient distributed secondary control strategy based on the layered network has been used to restore the voltage and frequency under attacks and suppress the divergence of state estimation difference. At the same time, Θ(k) depending on state estimation difference has also been suppressed, and its destructiveness has been limited to the level of a bounded attack sequence. The strategy proposed in this study is suitable for the process between the initialization of generating attacks and completion of detection and isolation measures to alleviate the irreversible impact on the microgrid. The effectiveness of a resilient distributed secondary control strategy against unbounded attacks has been validated by a test microgrid consisting of six inverter-based DGs. The authors will focus on how to integrate mitigation, detection, and isolation processes into a more complete and effective strategy against unbounded attacks.
Statements
Data availability statement
The raw data supporting the conclusion of this article will be made available by the authors, without undue reservation.
Author contributions
FW and QS designed the experiments and research methods. QS performed the format analysis. The tools analysis, data processing, and writing the original draft were carried out by JZ. GX solved the application problem of research methods. GX performed the writing—review on references. JZ and QS contributed to proofreading and organization management.
Funding
This work is supported in part by the National Key R&D Program of China (2019YFB1802501), the Key Research Project of Zhejiang Lab (2021LE0AC02), the High-Level Talents Innovation Support Plan of Dalian (Young Science and Technology Star Project) (under Grant No. 2021RQ058), the National Natural Science Foundation of China (under Grant Nos. 51939001, 61803064, 61751202, 61903092, 61976033, and U1813203), the Science and Technology Innovation Funds of Dalian (under Grant No. 2018J11CY022), the Liaoning Revitalization Talents Program (under Grant Nos. XLYC1908018 and XLYC1807046), the Natural Science Foundation of Liaoning (2019-ZD-0151 and 20170540098), and the Fundamental Research Funds for the Central Universities (under Grant Nos. 3132019345, 3132020103, and 3132020125).
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors, and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1
AbhinavS.ModaresH.LewisF. L.FerreseF.DavoudiA. (2018). Synchrony in networked microgrids under attacks. IEEE Trans. Smart Grid9, 6731–6741. 10.1109/TSG.2017.2721382
2
BidramA.DavoudiA.LewisF. L.GuerreroJ. M. (2013). Distributed cooperative secondary control of microgrids using feedback linearization. IEEE Trans. Power Syst.28, 3462–3470. 10.1109/TPWRS.2013.2247071
3
BidramA.LewisF. L.DavoudiA. (2014). Distributed control systems for small-scale power networks: Using multiagent cooperative control theory. IEEE Control Syst. Mag.34, 56–77. 10.1109/MCS.2014.2350571
4
ChenY.QiD.DongH.LiC.LiZ.ZhangJ.et al (2021). A fdi attack-resilient distributed secondary control strategy for islanded microgrids. IEEE Trans. Smart Grid12, 1929–1938. 10.1109/TSG.2020.3047949
5
CondryM. W.NelsonC. B. (2016). Using smart edge iot devices for safer, rapid response with industry iot control operations. Proc. IEEE104, 938–946. 10.1109/JPROC.2015.2513672
6
DuttaR. G.ZhangT.JinY. (2019). “Resilient distributed filter for state estimation of cyber-physical systems under attack,” in 2019 American Control Conference (ACC), 5141–5147. 10.23919/ACC.2019.8815298
7
FawziH.TabuadaP.DiggaviS. (2014). Secure estimation and control for cyber-physical systems under adversarial attacks. IEEE Trans. Autom. Contr.59, 1454–1467. 10.1109/TAC.2014.2303233
8
GaoS.PengZ.LiuL.WangD.HanQ.-L. (2022). Fixed-time resilient edge-triggered estimation and control of surface vehicles for cooperative target tracking under attacks. IEEE Trans. Intell. Veh.1, 1–10. 10.1109/TIV.2022.3184076
9
GeP.ZhuY.GreenT. C.TengF. (2021). Resilient secondary voltage control of islanded microgrids: An eskbf-based distributed fast terminal sliding mode control approach. IEEE Trans. Power Syst.36, 1059–1070. 10.1109/TPWRS.2020.3012026
10
GharesifardB.BaşarT. (2012). Resilience in consensus dynamics via competitive interconnections. IFAC Proc. Vol.45, 234–239. 10.3182/20120914-2-US-4030.00018
11
GusrialdiA.QuZ.SimaanM. A. (2018). Competitive interaction design of cooperative systems against attacks. IEEE Trans. Autom. Contr.63, 3159–3166. 10.1109/TAC.2018.2793164
12
GusrialdiA.QuZ.SimaanM. A. (2014). “Robust design of cooperative systems against attacks,” in 2014 American Control Conference, 1456–1462. 10.1109/ACC.2014.6858789
13
HuL.WangZ.HanQ.-L.LiuX. (2018). State estimation under false data injection attacks: Security analysis and system protection. Automatica87, 176–183. 10.1016/j.automatica.2017.09.028
14
HuY.CuiZ.LiZ.DongY.CuiP.WuJ. (2022). Construction technologies of polymorphic network environment based on codesign of domain-specific software/hardware. J. Commun.43, 3–13. 10.11959/j.issn.1000436x.2022086
15
HuY.LiD.SunP.YiP.WuJ. (2020). Polymorphic smart network: An open, flexible and universal architecture for future heterogeneous networks. IEEE Trans. Netw. Sci. Eng.7, 2515–2525. 10.1109/TNSE.2020.3006249
16
HuangJ.HoD. W.LiF.YangW.TangY. (2020). Secure remote state estimation against linear man-in-the-middle attacks using watermarking. Automatica121, 109182. 10.1016/j.automatica.2020.109182
17
KreutzD.RamosF. M. V.VeríssimoP. E.RothenbergC. E.AzodolmolkyS.UhligS.et al (2015). Software-defined networking: A comprehensive survey. Proc. IEEE103, 14–76. 10.1109/JPROC.2014.2371999
18
LiuY.LiY.WangY.ZhangX.GooiH. B.XinH.et al (2022). Robust and resilient distributed optimal frequency control for microgrids against cyber attacks. IEEE Trans. Ind. Inf.18, 375–386. 10.1109/TII.2021.3071753
19
LiuY.NingP.ReiterM. K. (2009). “False data injection attacks against state estimation in electric power grids,” in Proceedings of the 16th ACM Conference on Computer and Communications Security, 21–32. 10.1145/1653662.1653666
20
LiuY.NingP.ReiterM. K. (2011). False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur.14, 1–33. 10.1145/1952982.1952995
21
MabaningA. A. G.OrillazaJ. R. C.von MeierA. (2017). “Optimal pmu placement for distribution networks,” in 2017 IEEE Innovative Smart Grid Technologies - Asia (ISGT-Asia), 1–6. 10.1109/ISGT-Asia.2017.8378415
22
ManandharK.CaoX.HuF.LiuY. (2014). Detection of faults and attacks including false data injection attack in smart grid using kalman filter. IEEE Trans. Control Netw. Syst.1, 370–379. 10.1109/TCNS.2014.2357531
23
NunesB. A. A.MendoncaM.NguyenX.-N.ObraczkaK.TurlettiT. (2014). A survey of software-defined networking: Past, present, and future of programmable networks. IEEE Commun. Surv. Tutorials16, 1617–1634. 10.1109/SURV.2014.012214.00180
24
PangZ.-H.FanL.-Z.DongZ.HanQ.-L.LiuG.-P. (2022). False data injection attacks against partial sensor measurements of networked control systems. IEEE Trans. Circuits Syst. Ii.69, 149–153. 10.1109/TCSII.2021.3073724
25
PeiC.XiaoY.LiangW.HanX. (2020). Pmu placement protection against coordinated false data injection attacks in smart grid. IEEE Trans. Ind. Appl.56, 4381. 10.1109/TIA.2020.2979793
26
RappK.NymanP.-O. (2004). Stability properties of the discrete-time extended kalman filter. IFAC Proc. Vol.37, 1377–1382. 10.1016/S1474-6670(17)31420-9
27
SalahK.ElbadawiK.BoutabaR. (2012). Performance modeling and analysis of network firewalls. IEEE Trans. Netw. Serv. Manage.9, 12–21. 10.1109/TNSM.2011.122011.110151
28
TahabilderA.GhoshP. K.ChatterjeeS.RahmanN. (2017). “Distribution system monitoring by using micro-pmu in graph-theoretic way,” in 2017 4th International Conference on Advances in Electrical Engineering (ICAEE), 159–163. 10.1109/ICAEE.2017.8255346
29
TangZ.YangY.BlaabjergF. (2022). Power electronics: The enabling technology for renewable energy integration. CSEE J. Power Energy Syst.8, 39–52. 10.17775/CSEEJPES.2021.02850
30
WangX.LuoX.ZhangM.JiangZ.GuanX. (2020). Detection and isolation of false data injection attacks in smart grid via unknown input interval observer. IEEE Internet Things J.7, 3214–3229. 10.1109/JIOT.2020.2966221
31
WangR.SunQ.SunC.ZhangH.GuiY.WangP. (2021). Vehicle-Vehicle Energy Interaction Converter of Electric Vehicles: A Disturbance Observer Based Sliding Mode Control Algorithm. IEEE Trans. Veh. Technol70, 9910–9921. 10.1109/TVT.2021.3105433
32
XuY.GuoQ.SunH.FeiZ. (2019). Distributed discrete robust secondary cooperative control for islanded microgrids. IEEE Trans. Smart Grid10, 3620–3629. 10.1109/TSG.2018.2833100
33
YangD.QinJ.PangY.HuangT. (2022). A novel double-stacked autoencoder for power transformers dga signals with an imbalanced data structure. IEEE Trans. Ind. Electron.69, 1977–1987. 10.1109/TIE.2021.3059543
34
ZengW.ChowM.-Y. (2014). Resilient distributed control in the presence of misbehaving agents in networked control systems. IEEE Trans. Cybern.44, 2038–2049. 10.1109/TCYB.2014.2301434
35
ZhangR.XiaoG.ShanQ.ZouT.LiD.TengF. (2022). Communication topology reconstruction method for multi-agent cooperative control in polymorphic networks. J. Commun.43, 50–59. 10.11959/j.issn.1000436x.2022077
36
ZhouJ.SunH.XuY.HanR.YiZ.WangL.et al (2021a). Distributed power sharing control for islanded single-/three-phase microgrids with admissible voltage and energy storage constraints. IEEE Trans. Smart Grid12, 2760–2775. 10.1109/TSG.2021.3057899
37
ZhouJ.XuY.SunH.LiY.ChowM.-Y. (2020). Distributed power management for networked ac–dc microgrids with unbalanced microgrids. IEEE Trans. Ind. Inf.16, 1655–1667. 10.1109/TII.2019.2925133
38
ZhouQ.ShahidehpourM.AlabdulwahabA.AbusorrahA.CheL.LiuX.et al (2021b). Cross-layer distributed control strategy for cyber resilient microgrids. IEEE Trans. Smart Grid12, 3705–3717. 10.1109/TSG.2021.3069331
39
ZuoS.YueD. (2022). Resilient containment of multigroup systems against unknown unbounded fdi attacks. IEEE Trans. Ind. Electron.69, 2864–2873. 10.1109/TIE.2021.3066941
40
ZuoS.LewisF. L.DavoudiA. (2020). Resilient output containment of heterogeneous cooperative and adversarial multigroup systems. IEEE Trans. Autom. Contr.65, 3104–3111. 10.1109/TAC.2019.2947620
Summary
Keywords
unbounded attack sequence, discrete-time, polymorphic network, virtual layer, resilient distributed secondary control strategy
Citation
Wang F, Shan Q, Zhu J and Xiao G (2022) Discrete-time resilient-distributed secondary control strategy against unbounded attacks in polymorphic microgrid. Front. Energy Res. 10:961488. doi: 10.3389/fenrg.2022.961488
Received
04 June 2022
Accepted
28 June 2022
Published
16 August 2022
Volume
10 - 2022
Edited by
Xiao Wang, Wuhan University, China
Reviewed by
Yue Wu, Southwest Jiaotong University, China
Wang Lina, China Jiliang University, China
Nannan Rong, Tianjin Polytechnic University, China
Updates
Copyright
© 2022 Wang, Shan, Zhu and Xiao.
This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Qihe Shan, shanqihe@163.com; Jun Zhu, zhu_j@aliyun.com
This article was submitted to Smart Grids, a section of the journal Frontiers in Energy Research
Disclaimer
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.