- 1Department of Aerospace Engineering, University of Michigan, Ann Arbor, MI, United States
- 2Department of Electrical Engineering and Computer Science, University of Michigan, Ann Arbor, MI, United States
This paper studies a defense approach against one or more swarms of adversarial agents. In our earlier work, we employed a closed formation (“StringNet”) of defending agents (defenders) around a swarm of adversarial agents (attackers) to confine their motion within given bounds, and guide them to a safe area. The adversarial agents were assumed to remain close enough to each other, i.e., within a prescribed connectivity region. To handle situations when the attackers no longer stay within such a connectivity region, but rather split into smaller swarms (clusters) to maximize the chance or impact of attack, this paper proposes an approach to learn the attacking sub-swarms and reassign defenders toward the attackers. We use a “Density-based Spatial Clustering of Application with Noise (DBSCAN)” algorithm to identify the spatially distributed swarms of the attackers. Then, the defenders are assigned to each identified swarm of attackers by solving a constrained generalized assignment problem. We also provide conditions under which defenders can successfully herd all the attackers. The efficacy of the approach is demonstrated via computer simulations, as well as hardware experiments with a fleet of quadrotors.
1. Introduction
Rapid advancements in swarm technology and its increasing presence in airspace pose significant threat to safety-critical infrastructure such as government facilities, airports, and military bases. The presence of adversarial swarms nearby such entities, with the aim of causing physical damage or collecting critical information, can lead to catastrophic consequences. This necessitates solutions for the protection of safety-critical infrastructure against such attacks, particularly in populated areas.
Counteracting an adversarial swarm by means of physical interception, as studied in Chen et al. (2017), Coon and Panagou (2017), and Shishika et al. (2020), may not be desirable at low altitudes in an urban environment due to human presence. Under the assumption of risk-averse and self-interested adversarial agents (attackers) that tend to move away from the defending agents (defenders) and from other dynamic objects, herding can be used as an indirect way of guiding the attackers to some safe area in order to safe-guard a safety-critical area (protected area).
In our recent work Chipade and Panagou (2019, 2020b), we developed a herding algorithm, called “StringNet Herding,” to herd a swarm of attackers away from a protected area. A closed formation (“StringNet”) of defending agents connected by string barriers is formed around a swarm of attackers to confine their motion within given bounds, and guide them to a safe area. However, the assumption that the attackers stay together in a circular region, and that they react to the defenders collectively as a single swarm while attacking the protected area, can be quite conservative in practice.
In this paper, we build upon our earlier work on “StringNet Herding” (Chipade and Panagou, 2020b) and study the problem of defending a protected area from attackers that may or may not stay together throughout their attack. We propose a “Multi-Swarm StringNet Herding” approach that uses clustering-based defender assignment, and the “StringNet Herding” method to herd the multiple swarms adversarial attackers' to known safe areas.
1.1. Related Work
Herding has been studied earlier in the literature, see for instance (Haque et al., 2011; Paranjape et al., 2018; Pierson and Schwager, 2018). The approach in Paranjape et al. (2018) uses an n-wavefront algorithm to herd a flock of birds away from an airport, where the birds on the boundary of the flock are influenced based on the locations of the airport and a safe area.
The herding method in Pierson and Schwager (2018) utilizes a circular-arc formation of herders to influence the non-linear dynamics of the herd based on a potential-field approach, and designs a point-offset controller to guide the herd close to a specified location. In Haque et al. (2011), biologically-inspired strategies are developed for confining a group of agents; the authors develop strategies based on the “wall” and “encirclement” methods that dolphins use to capture a school of fish. In addition, they compute regions from which this confinement is possible; however, the results are limited to constant-velocity motion. A similar approach called herding by caging is adopted in Varava et al. (2017), where a cage of high potential is formed around the attackers. An RRT approach is used to find a motion plan for the agents; however, the cage is assumed to have already been formed around the agents, while the caging of the agents thereafter is only ensured with constant velocity motion under additional assumptions on the distances between the agents. Forming such a cage could be more challenging in case of self-interested, risk-averse attackers under non-constant velocity motion.
In Licitra et al. (2017, 2018), the authors discuss herding using a switched-system approach; the herder (defender) chases targets (evaders/attackers) sequentially by switching among them so that certain dwell-time conditions are satisfied to guarantee stability of the resulting trajectories. However, the assumption that only one of the targets is influenced by the herder at any time might be limiting and non-practical in real applications. The authors in Deptula et al. (2018) use approximate dynamic programming to obtain suboptimal control policies for the herder to chase a target agent to a goal location. A game-theoretic formulation is used in Nardi et al. (2018) to address the herding problem by constructing a virtual barrier similar to Pierson and Schwager (2018). However, the computational complexity due to the discretization of the state and control-action spaces limits its applicability.
Most of the aforementioned approaches for herding are limiting due to one or some of the following aspects: (1) simplified motion models (Varava et al., 2017; Pierson and Schwager, 2018), (2) absence of obstacles in the environment (Licitra et al., 2017, 2018; Paranjape et al., 2018), (3) no consideration of intra-team collisions (Varava et al., 2017; Pierson and Schwager, 2018), (4) assumption on a particular form of potential field to model the repulsive motion of the attackers with respect to the defenders (Licitra et al., 2017, 2018; Paranjape et al., 2018; Pierson and Schwager, 2018).
We have addressed the above issues in our recent work Chipade and Panagou (2019, 2020b), which develops a method termed as “StringNet Herding,” for defending a protected area from a swarm of attackers in a 2D obstacle environment. In “StringNet Herding,” a closed formation of strings (“StringNet”) is formed by the defenders to surround the swarm of attackers. It is assumed that the attackers will stay together within a circular footprint as a swarm and collectively avoid the defenders. It is also assumed that the string between two defenders serves as a barrier through which the attackers cannot escape (e.g., a physical straight-line barrier, or some other mechanism). The StringNet is then controlled to herd the swarm of attackers to a safe area. The control strategy for the defenders in “StringNet Herding” is a combination of time-optimal control actions and finite-time, state-feedback, bounded control actions, so that the attackers can be herded to safe area in a timely manner.
Clustering of data points is a popular machine learning technique (Xu and Tian, 2015). There are various types of clustering algorithms: partition based (K-means; MacQueen et al., 1967), hierarchy based (BIRCH; Zhang et al., 1996), density based (DBSCAN; Ester et al., 1996), stream based (STREAM; O'Callaghan et al., 2002), graph based (CLICK; Sharan and Shamir, 2000). In the context of dynamical systems, authors in Cai et al. (2017) develop a clustering method based on quasi-consensus motions of dynamic agents where agents belonging to a particular cluster are expected to aggregate together. This method however converges to clustering results asymptotically. In this paper, we are interested in spatial proximity of the agents during a finite future time. So, we focus mostly on the density based approaches, for example, DBSCAN, to solve the clustering problem in this paper.
Assignment problems have also been studied extensively (Burkard et al., 2012). A detailed survey of an assignment problem pertaining to defense scenarios called “weapon-target assignment (WTA)” problem is provided in Kline et al. (2019). In general, assignment problems are NP-hard, and hence can be solved only approximately for large number of decision variables. For example, authors in Rezende et al. (2018) provide a greedy approach based on ant colony system to solve the WTA problem. Multi-agent defense problems are difficult to solve optimally because the problem becomes computationally intractable for large number of agents. In such cases, all possible pairwise games are first solved, and then an assignment problem is solved to assign defending agents against attacking ones based on the cost of the pairwise games. For example in Chen et al. (2017) and Coon and Panagou (2017), after solving the pairwise games, the defenders are assigned to attackers by solving a bipartite matching problem using Hungarian algorithm (Kuhn, 1955). Similarly, in Yan et al. (2019) authors solve a mixed integer program to find assignment of defenders to attackers in a multiplayer reach-avoid game played in a convex domain. In this paper, we are interested in a generalized assignment problem (GAP) (Öncan, 2007), in which there are more number of objects than knapsacks to be filled, because we aim to assign groups of defenders to a number of attackers' clusters, which are typically small in number than the number of defenders. Similar to the standard assignment problems, GAP is known to be NP-hard, but there are approximation algorithms to solve an arbitrary instance of GAP (Öncan, 2007).
1.2. Overview of the Proposed Approach
In the preliminary work presented in Chipade and Panagou (2020c), we extended the “StringNet Herding” approach to scenarios where attackers no longer stay together and may split into smaller swarms in reaction to the defenders' presence. The proposed approach involves: (1) identification of the clusters (swarms) of the attackers that stay together, (2) distribution and assignment of the defenders to each of the identified swarms of the attackers, (3) use of “StringNet Herding” approach by the defenders to herd each identified swarm of attackers to the closest safe area.
More specifically, we use the “Density based Spatial Clustering of Application with Noise (DBSCAN)" algorithm (Ester et al., 1996) to identify swarms of the attackers based on the proximity of the attackers to each other. We then formulate a generalized assignment problem with additional constraints on the connectivity of the defenders, to find which defender should go against which swarm of attackers and herd it to one of the safe areas. This connectivity constrained generalized assignment problem (C2GAP) is modeled as a mixed integer quadratically constrained program (MIQCP) to obtain an optimal assignment solution. Additionally, we provide a hierarchical algorithm to find the assignment quickly.
In this paper, we further improve the clustering based multi-swarm herding approach by developing a decentralized variant of the MIQCP that is used to assign the defenders to the identified swarms of the attackers. Furthermore, we address the question of whether the defenders starting at some known positions can gather on the shortest path of the attackers, starting at some states, to the protected area and can successfully herd the attackers to safe areas. We also demonstrate the “StringNet Herding” algorithm for single attacking swarm case via hardware experiments with a fleet of quadrotor vehicles that are capable of flying autonomously in an outdoor aerial robotics facility at the University of Michigan campus.
1.3. Summary of our Contributions
In summary, compared to the prior literature and our prior work presented in the conference version (Chipade and Panagou, 2020c), the novelties and contribution of this work are:
• a decentralized cooperative algorithm to group and assign the defenders to herd the identified different swarms of the attackers to the closest safe areas;
• a set of conditions under which the defenders are able to gather on the shortest path of the oncoming attackers to the protected area before the attackers could reach the gathering location and thereafter herd all the attackers to the safe areas;
• a demonstration of the “StringNet Herding” approach for a single attacking swarm case in hardware experiments using a fleet of quadrotor vehicles equipped with autonomous flight capability.
1.4. Structure of the Paper
Section 2 describes the mathematical modeling and problem statement. The “StringNet Herding” approach to herd a single swarm of attackers is briefly discussed in section 3. The approach on identification of attackers' swarms (clusters) and the defenders' assignment to these identified swarms for multiple-swarm herding is discussed in section 4. Simulations are provided in section 7, and the hardware experiments are discussed in section 8. Finally, the paper is concluded in section 10.
2. Modeling and Problem Statement
Notation: We use r, v and u to denote position, velocity and input acceleration vector, respectively. We use ξ and η to denote desired position and velocity vector, respectively. We use A and D to denote the indices of attackers and defenders, respectively, while I denotes order set of positive integers starting at 1. The variables ai, ack, dj, dck used as subscripts of the above variables correspond to the ith attacker, center of mass of kth swarm of attackers, jth defender and the kth group of defenders, respectively. Similarly, subscripts p, sm denote the protected area and mth safe area, respectively. We use subscript d to denote common variables that correspond to all the defenders and subscripts a to denote common variables corresponding to all the attackers. We use sn and sb as a subscripts to denote StringNet and string barrier, respectively. Any variable with superscript g, s, e, h correspond to gathering, seeking, enclosing and herding phase, respectively.
The set of integers greater than 0 is denoted by ℤ>0. ‖.‖ denotes the Euclidean norm of its argument. |.| denotes the absolute value of a scalar, and cardinality if the argument is a set. ⌊·⌋ gives the largest integer smaller than the argument number. A ball of radius ρ centered at the origin is defined as .
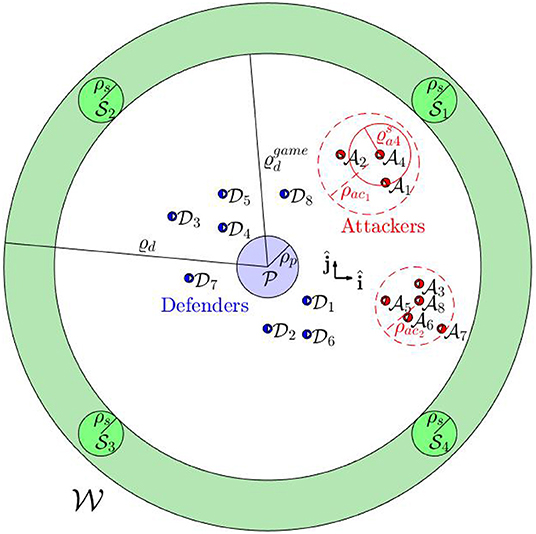
We consider Na attackers , i ∈ Ia = {1, 2, …, Na}, and Nd defenders , j ∈ Id = {1, 2, …, Nd}, operating in a 2D environment that contains a protected area , defined as , and Ns safe areas , defined as , for all m ∈ Is = {1, 2, …, Ns}, where (rp, ρp) and (rsm, ρsm) are the centers and radii of the corresponding areas, respectively. The attackers aim to reach the protected area . The attackers may use flocking controllers (Dai and Li, 2014) to stay together, or they may choose to split into different smaller swarms (Raghuwaiya et al., 2016; Goel et al., 2019). The defenders aim to herd each of these attackers to one of the safe areas in before they reach .
The agents and are modeled as discs of radii ρa and ρd(≤ ρa), respectively and move under double integrator (DI) dynamics with quadratic drag (damped double integrator):
where CD is the drag coefficient, and are the position vectors of and , respectively; , are the velocity vectors, respectively, and , are the accelerations (the control inputs), respectively. This model poses a speed bound on each player with limited acceleration control, i.e., and . The defenders are assumed to be faster than the attackers, i.e., (i.e., ūa < ūd). The number of defenders is assumed to be no less than that of attackers, i.e., Nd ≥ Na.
There is a distributed navigation system that senses the position rai and velocity vai of the attacker that lies inside a circular sensing zone for all i ∈ Ia, where ϱd > 0 is the radius of the defenders' sensing zone. The navigation system communicates the sensed information to the defenders , for all j ∈ Id. Every attacker has a local sensing zone , where ϱai > 0 is the radius of the attacker 's sensing zone (Figure 1). This navigation system can include sensors such as radars, lidars, cameras that are spatially distributed around the protected area and provide measurements of positions and velocities of the attackers and the defenders. The defenders are also assumed to have sufficient computational power available on board to solve the assignment problems that are discussed later in the paper.
Formally, we consider the followin g problems.
Problem 1 (Swarm Identification). Identify the swarms of the attackers for some unknown Nac ≥ 1 such that attackers in the same swarm , and only them, are physically close to each other and satisfy prescribed conditions (described later) on spatial density, where , Ack ⊆ Ia, for all k ∈ Iac = {1, 2, …, Nac}.
Problem 2 (Multi-Swarm Herding). Find subgroups of the defenders and their assignment to the attackers' swarms identified in Problem 1, such that all the defenders in the same subgroup are connected via string barriers to enclose and herd the assigned attacker's swarm.
Problem 3 (Defenders' Dominance Region). Given the initial positions of the defenders rdj(0), for all j ∈ Id, provide conditions on the initial positions rai(0), for all i ∈ Ia, of the attackers for which the defenders are able to gather as a specified formation centered at a point on the expected path of the attackers before any attacker reaches the center of the formation.
Before we discuss the solutions to the above three problems, we first briefly describe the “StringNet Herding” approach used to herd a single swarm of the attackers in the following section.
3. Herding a Single Swarm of Attackers
To herd a swarm of attackers to , we use “StringNet Herding,” developed in Chipade and Panagou (2020b). StringNet is a closed net of strings formed by the defenders as shown in Figure 3. The strings are realized as impenetrable and extendable line barriers (e.g., spring-loaded pulley and a rope or other similar mechanism; Mirjan et al., 2016) that prevent attackers from passing through them. The extendable string barrier allows free relative motion of the two defenders connected by the string. The string barrier can have a maximum length of . If the string barrier were to be physical one, then it can be established between two defenders and only when they are close to each other and have almost same velocity, i.e., and , where ϵ1 and ϵ2 are small numbers. The underlying graph structure for the two different “StringNet” formations defined for a subset of defenders , where , are defined as follows:
Definition 1 (Closed-StringNet). The Closed-StringNet is a cycle graph consisting of: 1) a subset of defenders as the vertices, , 2) a set of edges, , where the operator denotes an impenetrable line barrier between the defenders.
Definition 2 (Open-StringNet). The Open-StringNet is a path graph consisting of: 1) a set of vertices, and 2) a set of edges, , similar to that in Definition 1.
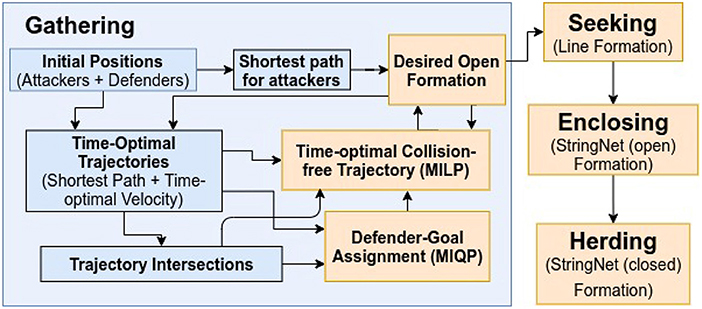
The StringNet herding consists of four phases: (1) gathering, (2) seeking,(3) enclosing, and (4) herding to a safe area, see the block diagram in Figure 2.
These phases are discussed as follows.
3.1. Gathering
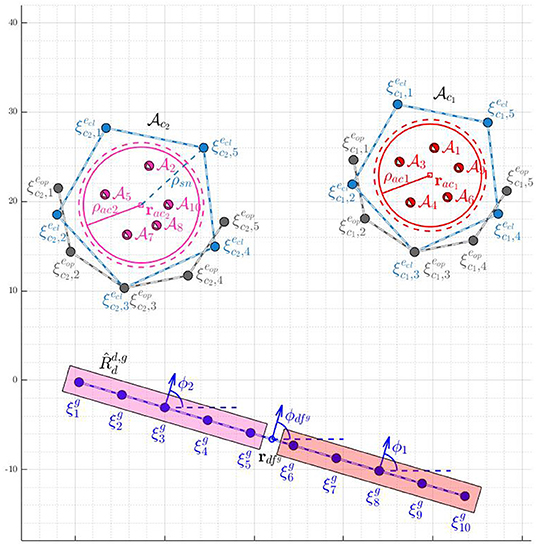
We assume that the attackers start as single swarm that stays together and they may start splitting into smaller groups as they sense the defenders in their path. The aim of the defenders is to converge to an open formation 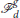 centered at the gathering center located on the expected path of the attackers, where the expected path is defined as the shortest path of the attackers to the protected area, before the attackers reach (see Figure 3). Let
centered at the gathering center located on the expected path of the attackers, where the expected path is defined as the shortest path of the attackers to the protected area, before the attackers reach (see Figure 3). Let 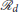 (Na):ℤ>0 → ℤ>0 be the resource allocation function that outputs the number of the defenders that can be assigned to the given Na attackers. We make the following assumption about the resource allocation function.
(Na):ℤ>0 → ℤ>0 be the resource allocation function that outputs the number of the defenders that can be assigned to the given Na attackers. We make the following assumption about the resource allocation function.
Assumption 1. The resource allocation function is a strictly monotonically increasing function, i.e., 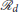 (Na) <
(Na) < 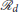 (Na + 1) and satisfies
(Na + 1) and satisfies 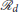 (Na) ≥ Na.
(Na) ≥ Na.
Assumption 1 ensures that there are adequate number of defenders to go after each attacker in the event the attackers in the swarm disintegrate into singular swarms (swarms with less than 3 attackers). In the case of large number of singular swarms, herding may not be the most economical way of defense as there needs to be at least 3 defenders to form a Closed-StringNet. In which case, one could employ a different mechanism to counteract the attack, for example, physical capture or interception of the attacker. In this paper we only the consider the attackers' swarms with greater than or equal to 3 attackers. The case of singular swarms will be studied in our future work.
The open formation 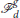 is characterized by the positions , for all l ∈ Idc0 = {1, 2, …,
is characterized by the positions , for all l ∈ Idc0 = {1, 2, …, 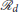 (Na)}, and is chosen to be a straight line formation1 (see Figure 3). Once the defenders arrive at these positions, the defenders get connected by strings as follows: the defender at gets connected to the defender at for all
(Na)}, and is chosen to be a straight line formation1 (see Figure 3). Once the defenders arrive at these positions, the defenders get connected by strings as follows: the defender at gets connected to the defender at for all 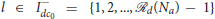 (see Figure 3). The angle made by the normal to the line joining and (clockwise from , see Figure 3) is the orientation ϕ of the formation. The formation
(see Figure 3). The angle made by the normal to the line joining and (clockwise from , see Figure 3) is the orientation ϕ of the formation. The formation 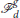 is chosen such that its orientation is toward the attackers on their expected path (defined above), see the blue formation in Figure 3. The desired positions on
is chosen such that its orientation is toward the attackers on their expected path (defined above), see the blue formation in Figure 3. The desired positions on 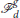 centered at are:
centered at are:
where 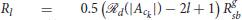 , is the unit vector making an angle θ with x-axis, , where is the angle made by the line segment joining the attackers' center of mass (ACoM) to the center of the protected area (the shortest path from the initial position of ACoM to ) with x-axis. These positions are static, i.e., . The gathering center is such that . We define the defender-goal assignment as:
, is the unit vector making an angle θ with x-axis, , where is the angle made by the line segment joining the attackers' center of mass (ACoM) to the center of the protected area (the shortest path from the initial position of ACoM to ) with x-axis. These positions are static, i.e., . The gathering center is such that . We define the defender-goal assignment as:
Definition 3 (Defender-Goal Assignment). An injective mapping β0:{1, 2, …, 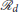 (Na)} → Id such that the defender is assigned to go to the goal .
(Na)} → Id such that the defender is assigned to go to the goal .
As discussed in Algorithm 1 in Chipade and Panagou (2020b) and as shown in Figure 2, we design a time-optimal motion plan so that the defenders gather at the desired formation 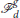 as early as possible and before the attackers reach close to
as early as possible and before the attackers reach close to 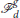 . The idea in Algorithm 1 in Chipade and Panagou (2020b) is to iteratively solve a mixed integer quadratic program (MIQP) until a gathering center for the gathering formation is found which is as far as possible from the protected area and such that the defenders are able to gather at the formation
. The idea in Algorithm 1 in Chipade and Panagou (2020b) is to iteratively solve a mixed integer quadratic program (MIQP) until a gathering center for the gathering formation is found which is as far as possible from the protected area and such that the defenders are able to gather at the formation 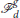 centered at the gathering center with bounded acceleration before the attackers can.
centered at the gathering center with bounded acceleration before the attackers can.
3.2. Seeking
After the defenders accomplish gathering, suppose a group of defenders , Dck ⊆ Id, is tasked to herd a swarm of attackers , Ack ⊆ Ia, the details are discussed later in section 4. Denote and let βk:Idck → Dck be the mapping that gives the indexing order of the defenders in on the Open-StringNet line formation 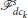 (similar to
(similar to 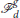 but with being the distance of each defender from their immediate neighbor). In the seeking phase, the defenders in maintain the line formation
but with being the distance of each defender from their immediate neighbor). In the seeking phase, the defenders in maintain the line formation 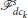 and try to get closer to the swarm of attackers by using state-feedback, finite-time convergent, bounded control laws as discussed in Chipade and Panagou (2020b). The control actions in Chipade and Panagou (2020b) for the defenders in are modified to incorporate collision avoidance from the other StringNet formations formed by , for k′ ≠ k.
and try to get closer to the swarm of attackers by using state-feedback, finite-time convergent, bounded control laws as discussed in Chipade and Panagou (2020b). The control actions in Chipade and Panagou (2020b) for the defenders in are modified to incorporate collision avoidance from the other StringNet formations formed by , for k′ ≠ k.
3.3. Enclosing: Closed-StringNet Formation
Once the Open-StringNet formation reaches close to the attackers' formation, the defenders start enclosing the attackers by moving to their desired positions on the enclosing formations while staying connected to their neighbors. We choose two formations for this phase that the defenders sequentially achieve: (1) Semi-circular Open-StringNet formation (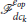 ), (2) Circular Closed-StringNet formation (
), (2) Circular Closed-StringNet formation (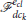 ). When the defenders directly try to converge to a circular formation from a line formation during this phase, the defenders at the either end of the Open-StringNet formation will start coming closer to each other reducing the length of the overall barrier in the attackers' path significantly. This is because the desired positions of these terminal defenders in the circular formation would be very close to each other on the opposite side of the circular formation (see Figure 3) and collision avoidance part of the controller is only active locally near the circle of maximum radius around the swarm . So the defenders would first converge to a semi-circular formation and would converge to a circular formation after the former is achieved.
). When the defenders directly try to converge to a circular formation from a line formation during this phase, the defenders at the either end of the Open-StringNet formation will start coming closer to each other reducing the length of the overall barrier in the attackers' path significantly. This is because the desired positions of these terminal defenders in the circular formation would be very close to each other on the opposite side of the circular formation (see Figure 3) and collision avoidance part of the controller is only active locally near the circle of maximum radius around the swarm . So the defenders would first converge to a semi-circular formation and would converge to a circular formation after the former is achieved.
The desired position on the Open-StringNet formation 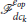 (Figure 3) is chosen on the circle with radius ρsnk centered at rack as:
(Figure 3) is chosen on the circle with radius ρsnk centered at rack as:
for all l ∈ Idck, where . is the center of mass of . The radius ρsnk should satisfy, , where is maximum radius of swarm . The parameter bd is the tracking error for the defenders in this phase (Chipade and Panagou, 2020b).
Similarly, the desired positions on the Closed-StringNet formation 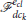 same as in Equation (5) with , for all l ∈ Idck. Both formations move with the same velocity as that of the attackers' center of mass, i.e., .
same as in Equation (5) with , for all l ∈ Idck. Both formations move with the same velocity as that of the attackers' center of mass, i.e., .
The defenders first track the desired goal positions by using the finite-time convergent, bounded control actions given in Chipade and Panagou (2020b). Once the defender and reach within a distance of bd from and , i.e., and , respectively, the desired goal positions are changed from to for all l ∈ Idck. The StringNet is achieved when for all l ∈ Idck during this phase.
3.4. Herding: Moving the Closed-StringNet to Safe Area
Once a group of defenders forms a StringNet around a swarm of attackers , they move while tracking a desired rigid closed circular formation 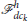 centered at a virtual agent as discussed in Chipade and Panagou (2020b). The swarm is herded to the closest safe area Sς(k), where .
centered at a virtual agent as discussed in Chipade and Panagou (2020b). The swarm is herded to the closest safe area Sς(k), where .
4. Multi-Swarm Herding
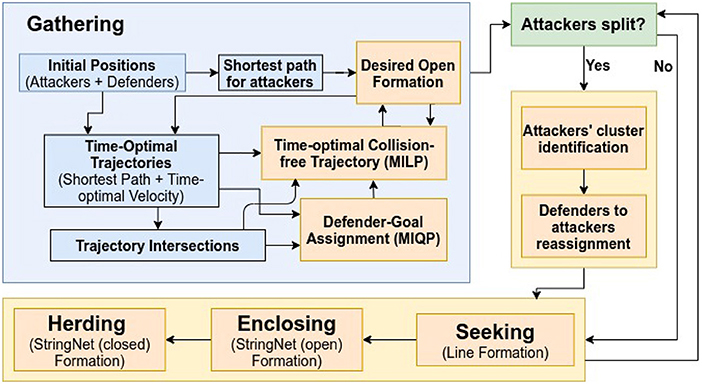
In this section, we consider that the attackers split into smaller groups as they sense the defenders along their way to the protected area, to maximize the chance of at least some attackers reaching the protected area by circumnavigating the oncoming defenders. To respond to such strategic movements of the attackers, the defenders need to collaborate intelligently. In the approach presented in this paper, as shown in the block diagram in Figure 4, the defenders continuously keep checking whether the attackers have split, i.e., whether the attackers no longer satisfy certain spatial proximity constraints (defined later in the text). After a split event has happened, the defenders first identify the spatial clusters of the attackers. Then, the defenders distribute themselves into smaller connected groups, and these connected groups are assigned to the herd different spatial clusters (swarms) of the attackers to safe areas. Here, by “connected group of defenders" we mean that the defenders have already been connected via string barriers and established an Open-StringNet formation, see for example the defenders at the locations and as shown in Figure 3. In the next subsections, we discuss how the swarms (clusters) of the attackers are identified and how the defenders are assigned to these identified swarms of the attackers.
4.1. Identifying Swarms of the Attackers
In order to identify the spatially distributed clusters (swarms) of the attackers, the defenders utilize the Density Based Spatial Clustering of Applications with Noise (DBSCAN) algorithm (Ester et al., 1996). Given a set of points, DBSCAN algorithm finds clusters of high density points (i.e., points with many nearby neighbors), and marks the points as outliers if they lie alone in low-density regions (whose nearest neighbors are too far away). DBSCAN algorithm can identify clusters of any shape in the data and requires two parameters that define the density of the points in the clusters: (1) εnb (radius of the neighborhood of a point), (2) mpts (minimum number of points in εnb-neighborhood of a point). In general, attackers can split into formations with varied range of densities making the choice of the parameters εnb and mpts challenging. There are variants of the DBSCAN algorithm, such as OPTICS (Ankerst et al., 1999), which can find clusters of varying density; however, they are more time consuming. Therefore, to keep the computational demands low, we use the DBSCAN algorithm with fixed parameters εnb and mpts, which quickly yields useful clustering information about the attackers satisfying a specified connectivity constraints.
The neighborhood of an attacker is defined using weighted distance between two attackers: , where and M is a weighing matrix defined as M = diag([1, 1, φ, φ]), where φ weights relative velocity against relative position. We choose φ < 1 because relative position is more important in a spatial cluster than the velocity alignment at a given time instance. The εnb-neighborhood of an attacker is then defined as the set of points such that d(xai, x) < εnb.
The largest circle inscribed in the largest Closed-StringNet formation formed by the 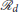 (Na) defenders has radius
(Na) defenders has radius 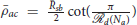 . Maximum radius of any cluster with Na points identified by DBSCAN algorithm with parameters εnb and mpts is . If all of the attackers were to be a single swarm enclosed inside the region with radius , then we would require εnb to be greater than in order to identify them as a single cluster. So we choose , and since we want to identify clusters with as low as 3 agents, we need to choose mpts = 3. With these parameters for DBSCAN algorithm, we have:
. Maximum radius of any cluster with Na points identified by DBSCAN algorithm with parameters εnb and mpts is . If all of the attackers were to be a single swarm enclosed inside the region with radius , then we would require εnb to be greater than in order to identify them as a single cluster. So we choose , and since we want to identify clusters with as low as 3 agents, we need to choose mpts = 3. With these parameters for DBSCAN algorithm, we have:
Lemma 1. Let be the clusters identified by DBSCAN algorithm with at time t, where Nac(t) is the total number of clusters at time t. If and Na = Nd, then the radius ρack(t) of the cluster satisfies 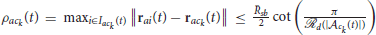 , for all k ∈ Iac(t) = {1, 2, …, Nac(t)}.
, for all k ∈ Iac(t) = {1, 2, …, Nac(t)}.
As the number of attackers increases, the computational cost for DBSCAN becomes higher and looses its practical usefulness. Furthermore, the knowledge of the clusters is only required by the defenders when a swarm of attackers does not satisfy the assumed constraint on its connectivity radius so the defenders can be reconfigured and reassigned. So we continuously track the radii of the clusters and run the DBSCAN algorithm only when at some instant t = tse the connectivity constraint is violated by the swarms of attackers for some k ∈ Iac(tse) i.e., when the radius ρack(tse) of the swarm of attackers exceeds the value 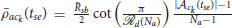 . The connectivity constraint violation is termed as split in this paper. The split event is defined as:
. The connectivity constraint violation is termed as split in this paper. The split event is defined as:
Definition 4 (Split event). An instant tse when for any swarm , k ∈ Iac(tse), the radius of the swarm of attackers defined as exceeds the value .
We also make the following assumption regarding the splitting behavior of the attackers.
Assumption 2. Once a swarm of attackers splits, its member attackers never rejoin each other, i.e., for all i ∈ Ia, if ∃ t > 0 such that for any k ∈ Iac(t) then for all t ≤ t′.
4.2. Defender Assignment to the Swarms of Attackers
The initially single-one swarm of attackers splits into smaller swarms that are being identified by the defenders. After then, the defenders must distribute themselves into smaller groups, and assign these groups to the attackers' swarms (clusters), so that subsequently they enclose the attackers' clusters and herd them to the closest safe area. Let be a set of swarms of the attackers after a split event has happened at time tse.
We assume that none of the swarms in is a singular one, i.e., a swarm with less than three agents, for all k ∈ Iac(t), t ≥ 0. We formally define the defender to attackers' swarm assignment as:
Definition 5 (Defender-to-AttackSwarm Assignment). A set β(t) = {β1(t, ·), β2(t, ·), …βNac(t, ·)} of mappings βk(t, ·):{1, 2, …, 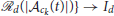 , where βk(t, ·) gives the indices of the defenders assigned to the swarm at time t for all k ∈ Iac(t).
, where βk(t, ·) gives the indices of the defenders assigned to the swarm at time t for all k ∈ Iac(t).
We want to find an assignment that minimizes the sum of distances of the defenders from the centers of the assigned attackers' swarms. This ensures that the collective effort needed by all the defenders is minimized when enclosing the swarms of the attackers. For successful enclosing of the newly formed attacking swarms, it is required that all the defenders that are assigned to an attackers' cluster are neighbors of each other, are already connected to each other via string barriers, and the underlying graph is an Open-StringNet.
Let be a set of swarms of the defenders, where denotes the instant immediately before t = tse. Each of these swarms is already connected via a StringNet and was assigned to herd some cluster of attackers an instant before a split event happened at time tse. Now that a split event has happened and new smaller clusters have been formed by the attackers, we seek to reassign the defenders to herd the newly formed clusters of the attackers.
This assignment problem is closely related to generalized assignment problem (GAP) (Öncan, 2007), in which n objects are to be filled in m knapsacks (n ≥ m). This problem is modeled as a GAP with additional constraints on the objects (defenders) that are assigned to a given knapsack (attackers' swarm). The additional constraint on the defenders is to ensure their connectivity to each other within a newly formed swarm of defenders. So, we call this constrained assignment problem as connectivity constrained generalized assignment problem (C2GAP), and provide a mixed integer quadratically constrained program (MIQCP) to find the optimal assignment centrally as:
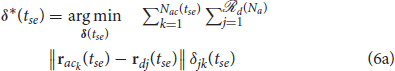
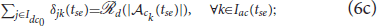
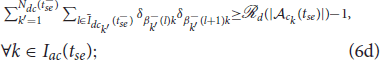
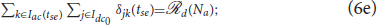
where Idc0 = {1, 2, …, 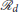 (Na)}; , where is the k′th swarm before the reassignment;
(Na)}; , where is the k′th swarm before the reassignment; 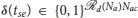 is the binary decision vector defined as δ(tse) = {δjk(tse)|j ∈ Idc0, k ∈ Iac(tse)}, where δjk(tse) is a decision variable which is equal to 1 when the defender is assigned to the swarm and 0 otherwise; and is the assignment of the defenders to a cluster prior to the split event. The constraints (6b) ensure that each defender is assigned to exactly one swarm of the attackers. The capacity constraints (6c) ensure that for all k ∈ Iac(tse) swarm has exactly
is the binary decision vector defined as δ(tse) = {δjk(tse)|j ∈ Idc0, k ∈ Iac(tse)}, where δjk(tse) is a decision variable which is equal to 1 when the defender is assigned to the swarm and 0 otherwise; and is the assignment of the defenders to a cluster prior to the split event. The constraints (6b) ensure that each defender is assigned to exactly one swarm of the attackers. The capacity constraints (6c) ensure that for all k ∈ Iac(tse) swarm has exactly 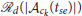 defenders assigned to it. The quadratic constraints (6d) ensure that all the defenders assigned to swarm are connected together with an underlying Open-StringNet for all k ∈ Iac(tse). Consider any sub-group of
defenders assigned to it. The quadratic constraints (6d) ensure that all the defenders assigned to swarm are connected together with an underlying Open-StringNet for all k ∈ Iac(tse). Consider any sub-group of 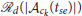 defenders out of the defenders that are already connected via Open-StringNet at the time of assignment. The intuition behind the constraints (6d) is that, for these
defenders out of the defenders that are already connected via Open-StringNet at the time of assignment. The intuition behind the constraints (6d) is that, for these 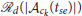 defenders, to be connected to each other via an Open-StringNet, each defender needs to be connected to its immediate neighbors and the total number of such connections should be equal
defenders, to be connected to each other via an Open-StringNet, each defender needs to be connected to its immediate neighbors and the total number of such connections should be equal 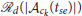 − 1. If the total number of connections is less than
− 1. If the total number of connections is less than 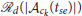 − 1 then it is evident that there are at least two disconnected components in the given subgroup of defenders and they do not form a single Open-StringNet, which is not desired in our case. For example, in the scenario shown in Figure 3, if we were to assign 5 defenders to a cluster of attackers then the only choices under this quadratic constraint would be to choose the defenders at for l ∈ {1, 2, …, 5} or the defenders at for l ∈ {6, 7, …, 10} and not the defenders at for l ∈ {1, 2, 7, 8, 9} or any such combination of defenders that violates the Open-StringNet connectivity. The constraint (6e) ensures that all the
− 1 then it is evident that there are at least two disconnected components in the given subgroup of defenders and they do not form a single Open-StringNet, which is not desired in our case. For example, in the scenario shown in Figure 3, if we were to assign 5 defenders to a cluster of attackers then the only choices under this quadratic constraint would be to choose the defenders at for l ∈ {1, 2, …, 5} or the defenders at for l ∈ {6, 7, …, 10} and not the defenders at for l ∈ {1, 2, 7, 8, 9} or any such combination of defenders that violates the Open-StringNet connectivity. The constraint (6e) ensures that all the 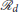 (Na) defenders are assigned to the attackers' swarms.
(Na) defenders are assigned to the attackers' swarms.
The aforementioned MIQCP can be solved using a MIP solver Gurobi (Gurobi Optimization, 2018). After solving (6), one can find the mapping βk(t, ·), for all k ∈ Iac(t), as follows:
where and l0 is the smallest integer for which ; tcomp is the computation time to solve (6); and is an unknown future time at which a split happens. In other words, the assignment obtained using the states at tse continues to be a valid assignment until the next split event happens at some unknown time in the future. As shown in an instance of the defender-swarm assignment in Figure 3, the defenders at for l ∈ {1, 2, …, 5} are assigned to swarm and those at for l ∈ {6, 7, …, 10} are assigned to swarm .
4.3. Decentralized Algorithm for Defender to AttackSwarm Assignment
The MIQCP in (6) is solved centrally, i.e., a single agent has access to the information pertaining to all the agents and the MIQCP is solved by a single agent or computer and the assignment result is communicated to other agents. To make the proposed assignment approach robust toward failure, we provide a decentralized algorithm to solve the assignment problem.
When a swarm of attackers splits into smaller swarms at t = tse. The newly identified swarms of the attackers by the DBSCAN algorithm are assigned new indices. Namely, one of the swarm is assigned the index k, i.e., the index of the parent swarm and the rest swarms are assigned integers greater than Nac(tse) as their indices. Let denote the indices of the clusters of the attackers that are newly formed out of the parent cluster , when the cluster splits at t = tse, as identified by the DBSCAN algorithm. Then, we can assign the defenders in only to the clusters , for all , and not consider other clusters of attackers, that did not split, or the other defenders during the reassignment process. We do so by solving the following modified MIQCP, which is solved only for the defenders in and the attackers in the cluster .
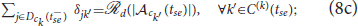
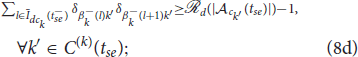
where defined as , is the set of indices of the defenders in prior to the reassignment. As one can see, the dimension of the decision vector is going to be smaller than that of the decision vector in (6) and hence (8) can be solved relatively quicker than (6).
Although the clustering information is acquired and tracked centrally, the problem in (8) is solved and the assignment solution is communicated to other teammates by the lead defender in , where the lead defender is identified to be the one in the middle of the Open-StringNet formation, i.e., the defender where , for all k for which the have split.
This helps the defenders find the Defender-to-AttackSwarm assignment quickly, and without having to consider all the agents in the assignment formulation, i.e., in a decentralized way.
If only one swarm of the attackers splits at a given time instant tse then indeed the optimal cost obtained in (6) and (8) are same. For other cases, the cost obtained by the decentralized algorithm would be suboptimal. A detailed analysis of performance of the centralized and the decentralized algorithms will be studied in our future work.
4.4. Heuristic to Find Defender-To-AttackSwarm Assignment
Finding the optimal defender-swarm assignment by solving the MIQCPs discussed above may not be real-time implementable for a large number of agents (>100). In this section, we develop a computationally-efficient heuristic, called hierarchical approach, to find defender-swarm assignment. A large dimensional assignment problem is split into smaller, lower-dimensional assignment problems that can be solved optimally and quickly using the MIQCP formulation discussed earlier. Algorithm 1 provides the steps to reduce the problem of size Nac to smaller problems of size smaller than or equal Nac(≤ Nac). In Algorithm 1,  is a data structure, at the time of assignment t = tse, with fields that store the information of: (i) centers of the attackers' swarms , (ii) numbers of the attackers in each newly formed swarm , (iii) total number of attackers . Similarly,
is a data structure, at the time of assignment t = tse, with fields that store the information of: (i) centers of the attackers' swarms , (ii) numbers of the attackers in each newly formed swarm , (iii) total number of attackers . Similarly,  is a data structure that stores the information of: (i) defenders' positions , and (ii) the goal assignment . splitApproxEqual function splits the attackers into two groups
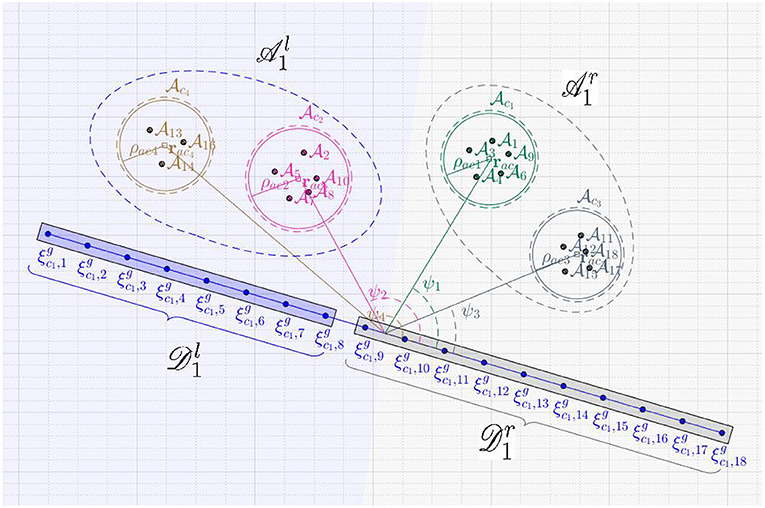
is a data structure that stores the information of: (i) defenders' positions , and (ii) the goal assignment . splitApproxEqual function splits the attackers into two groups 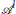 and
and 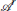 of roughly equal number of attackers, and the defenders into two groups
of roughly equal number of attackers, and the defenders into two groups 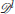 and
and 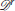 . The split is performed based on the angles made by relative vectors , for all , with the vector where is the center of as shown in Figure 5.
. The split is performed based on the angles made by relative vectors , for all , with the vector where is the center of as shown in Figure 5.
We first arrange these angles in descending order. The first few clusters in the arranged list with roughly half the total number of attackers become the left group 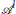 and the rest become the right group
and the rest become the right group 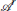 . Similarly, the left group
. Similarly, the left group 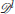 is formed by the first
is formed by the first 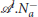 defenders as per the assignment β− and the rest defenders form the right group
defenders as per the assignment β− and the rest defenders form the right group 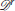 . For example, as shown in Figure 5, after the very first split event, the clusters become part of
. For example, as shown in Figure 5, after the very first split event, the clusters become part of 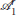 and are a part of
and are a part of 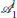 . Similarly, the defenders at for j ∈ {1, 2, …, 8} become part of
. Similarly, the defenders at for j ∈ {1, 2, …, 8} become part of 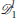 while the defenders at for j ∈ {9, 10, …, 18} become part of
while the defenders at for j ∈ {9, 10, …, 18} become part of 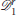 . We assign the defenders in
. We assign the defenders in 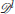 only to the swarms in
only to the swarms in 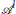 and those in
and those in 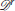 only to the swarms in
only to the swarms in 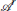 . By doing so we may or may not obtain an assignment that minimizes the cost in (6a) but we reduce the computation time significantly and obtain a reasonably good assignment quickly. As in Algorithm 1, the process of splitting is done recursively until the number of attackers' swarms is smaller than a pre-specified number Nac. The function assignMIQCP finds the defender-swarm assignment by solving (6).
. By doing so we may or may not obtain an assignment that minimizes the cost in (6a) but we reduce the computation time significantly and obtain a reasonably good assignment quickly. As in Algorithm 1, the process of splitting is done recursively until the number of attackers' swarms is smaller than a pre-specified number Nac. The function assignMIQCP finds the defender-swarm assignment by solving (6).
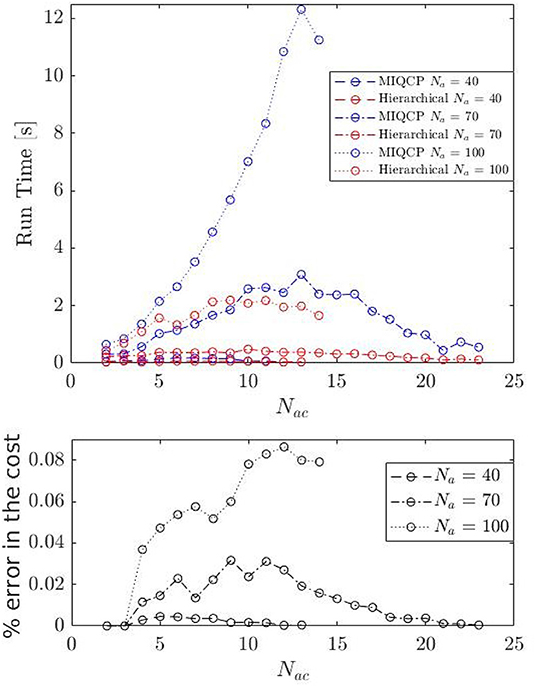
In Figure 6, we show the average computation time for a number of cluster configurations and random initial conditions. The computation cost first increases with the number of clusters, reaches a maximum point, and then decreases. This is because the computation cost is proportional to the number of choices available, i.e., number of ways Nac groups of given sizes can be formed out of N players (). More importantly, as shown in Figure 6, the average computation time for the hierarchical approach (heuristic) to assignment is significantly smaller than that of the MIQCP formulation. We also compare the cost of MIQCP and the heuristic. Figure 6 shows the percentage error between the cost from heuristic and the optimal cost from MIQCP, defined as , where costMIQCP and costHeuristic are the costs obtained by the MIQCP and the Heuristic, respectively. The cost of the hierarchical algorithm is very close to the optimal cost (MIQCP), see Figure 6. In summary, the hierarchical heuristic exploits the geometry to provide a reasonable assignment solution within a fraction of time that the optimal MIQCP formulation could have taken to find.
5. Dominance Region for the Defenders
In this and the following section, we provide conditions under which the defenders can successfully herd the attackers. The defenders succeed in herding the attackers if they manage to achieve the open-StringNet with line formation 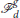 centered at a gathering center on the expected path of the attackers, well before the attackers reach the gathering center. If the successful gathering is possible by the defenders, then they could proceed to use the proposed StringNet herding approach to herd the attackers to safe areas, otherwise, the defenders would have to use some other approach to defense, such as direct physical capturing of the attackers.
centered at a gathering center on the expected path of the attackers, well before the attackers reach the gathering center. If the successful gathering is possible by the defenders, then they could proceed to use the proposed StringNet herding approach to herd the attackers to safe areas, otherwise, the defenders would have to use some other approach to defense, such as direct physical capturing of the attackers.
For given initial conditions of all the agents, the defenders require to solve the problem of finding the best gathering center and the corresponding defender-goal assignment βo using the iterative MIQP formulation discussed in Algorithm 1 in Chipade and Panagou (2020b). One needs to check if this problem is feasible for given initial conditions to conclude whether defenders can succeed in gathering. This formulation, however, becomes computationally demanding as the number of agents becomes larger. In order to quickly decide if the successful gathering is feasible or not, we provide the following approximate problem formulation that can be solved relatively quickly.
Let Ta(ra, r, ρa) be the minimum time required by an attacker at ra to reach within ρa distance from the point r ∈ ℝ2. Let Rd = [rd1, rd2, …, rdNd] denote the positions of the defenders for all j ∈ Id. Let 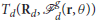 be the maximum time required by all the defenders to achieve the gathering formation
be the maximum time required by all the defenders to achieve the gathering formation 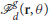 centered at r with orientation vector making an angle θ with x-axis.
centered at r with orientation vector making an angle θ with x-axis.
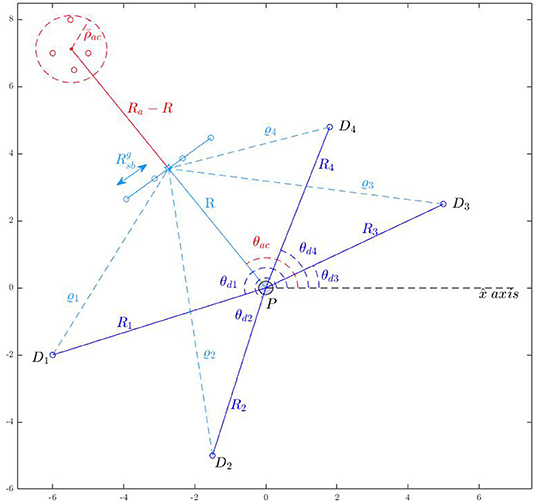
Consider Nd defenders and Na attackers located at given positions as shown in Figure 7. Consider the protected area located at the origin (). Let the largest radius of the attackers' formation be . Let the position vector of the center of mass of the attackers make an angle θac with x-axis. Let the center of the desired formation be located at a distance R from the protected area along the direction θac. The distance of the defender from the center of the desired formation is:
for all j ∈ Id. The maximum value among ϱj, for all j ∈ Id, can be bounded as: (Stipanović et al., 2012). For which we also have.
The maximum distance any defender would have to travel in the best defender-goal assignment can be upper bounded by . The maximum time for any defender to reach the gathering location assigned to it as per the best defender-goal assignment under time-optimal control (Chipade and Panagou, 2020a) can be bounded from above by:
where , , . Similarly, the minimum time that the attackers require to reach the gathering location is when the attackers move toward the protected with the maximum possible speed. Then, the difference between the time needed for the attackers to reach the gathering location and the time required by the defenders to reach there can be bounded from below by:
where Rac is the distance of the center of mass of the attackers from the center of the protected area and is the maximum radius of the attackers' formation under consideration. Defenders want to be able to gather well before the attackers reach the gathering center. Here is a user-defined time to account for the size of the attackers' swarm and the time required by the defenders to get connected by string barriers once arrived at the desired gathering formation. Given initial states of the attackers, one can find ΔT using (11) to assess, at least conservatively, whether the defenders can gather in the attackers' path before the attackers, without solving the actual, computationally heavy iterative MIQP formulation (Chipade and Panagou, 2020b).
Furthermore, using the above approximate analysis, for given initial conditions of the defenders, we characterize sufficient conditions on the initial positions of the attackers for which the defenders successfully gather on the shortest path of the attackers to the protected area, before the attackers can reach there. We call this set of initial conditions of the attackers as the dominance region for the given initial positions of the defenders. The dominance region is formally defined as:
Definition 6 (Defenders' Dominance Region). such that 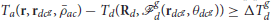 .
.
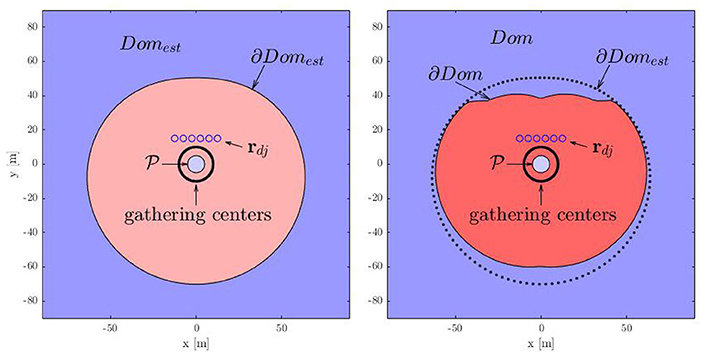
We use (11) to find an estimate Domest of the dominance region Dom that is completely contained inside Dom. We are interested in the limiting condition when , that corresponds to the boundary of Domest, for which we have:
We want to find the smallest value Rac(> ρp) of Rac for which , i.e.,
Lemma 2. Given that no two defenders are co-located, i.e., for all , f(R) as given in Equation (12) is a locally convex function of R.
Proof: The proof is provided in the Appendix.□
One can find Rac by solving the convex optimization (13) with R = R*, the minimizer of , as an initial guess to a gradient descent algorithm with sufficiently small step size. For different directions from which the attackers can approach the protected area, we solve the convex optimization (13) to find the corresponding point on the boundary Domest. Figure 8 shows the boundaries ∂Domest and ∂Dom of the estimate Domest and the dominance region Dom, respectively. Here ∂Dom is obtained by numerically evaluating the iterative MIQP for each direction. The regions outside of the closed boundaries ∂Domest and ∂Dom are, respectively, Domest and Dom, computed for the case where the defenders are at given locations (blue circles). On the other hand, the set inside the boundaries ∂Domest and ∂Dom are the complement sets and Domc = ℝ2\Dom, respectively. The set Domc is essentially the dominance region of the attackers, i.e., the attackers can reach the protected area before the defenders can gather on their path if the attackers start inside Domc. Note that the estimate Domest is completely contained in the dominance region Dom. The region Dom is larger on the side where the density of the defenders is larger. This is intuitive because many defenders have to travel less when the attackers approach from this side and hence allow defenders to gather on the expected path of the attackers in time even if the attackers start more closer to the protected area on this side. We have the following result based on the above analysis.
Theorem 3. Consider a group of defenders starting at given locations Rdc = [rd1, rd2, …, rdNd] and a swarm of Attackers with footprint of maximum radius . If the attackers start inside , then the defenders in are guaranteed to achieve a formation 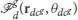 on the shortest path from the center of mass of the attackers in to the protected area before the attackers could reach there.
on the shortest path from the center of mass of the attackers in to the protected area before the attackers could reach there.
Proof: By construction, . The proof follows from the definition of the dominance region .□
In other words, Theorem 3 states that for the attackers starting in , the defenders are guaranteed to gather in their shortest path to the protected area in time. However, if the attackers do not start in nothing can be concretely said about the gathering of the defenders based on the above approximate analysis.
6. Results
Based on the DBSCAN clustering based assignment algorithm discussed earlier and the conditions on the initial states of the agents for successful gathering, we have the following result on the successful herding of the attackers.
Theorem 4. Consider a group of defenders 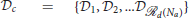 starting at given locations Rdc = [rd1, rd2, …, rd
starting at given locations Rdc = [rd1, rd2, …, rd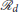 (Na)]. Let attackers' initial positions be such that , where , and that they belong to . Furthermore, suppose that for all times t > 0, each attacker belongs to one of the clusters , for some Nac, that are identified by DBSCAN algorithm with and mpts = 3 whenever a swarm splits into smaller swarms. Then,
(Na)]. Let attackers' initial positions be such that , where , and that they belong to . Furthermore, suppose that for all times t > 0, each attacker belongs to one of the clusters , for some Nac, that are identified by DBSCAN algorithm with and mpts = 3 whenever a swarm splits into smaller swarms. Then,
(i) the defenders in are guaranteed to enclose every attacker inside a StringNet; and
(ii) if a swarm of attackers has not reached the protected area by the time it is enclosed within a StringNet then the swarm is guaranteed to be herded to one of the safe areas.
Proof: (i) The attackers start inside , so as per Theorem 3 the defenders are able to gather and get connected by string barriers on the shortest path of the attackers to the protected area. Since each attacker belongs to one of the swarms of attackers that is identified by DBSCAN algorithm, we have from the Lemma 1 that each cluster satisfies 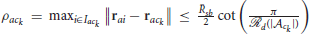 , as long as . This implies that a group of
, as long as . This implies that a group of 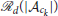 defenders connected via StringNet are capable of enclosing the attackers in for all k ∈ Iac. Under the control laws as described in section 3 (and in Chipade and Panagou (2020b)), it is proved in Theorem 5 and 6 in Chipade and Panagou (2020b) that the defenders in form a closed-StringNet around the attackers in , i.e., the defenders enclose the attackers, for all k ∈ Iac.
defenders connected via StringNet are capable of enclosing the attackers in for all k ∈ Iac. Under the control laws as described in section 3 (and in Chipade and Panagou (2020b)), it is proved in Theorem 5 and 6 in Chipade and Panagou (2020b) that the defenders in form a closed-StringNet around the attackers in , i.e., the defenders enclose the attackers, for all k ∈ Iac.
(ii) Once the attackers in a cluster are enclosed by the defenders in and it is true that the attackers have not reached the protected area, then the defenders in , under the control actions described in section 3.4 (and in Chipade and Panagou 2020b), herd the attackers in to one of the safe areas as proved in Theorem 7 in Chipade and Panagou (2020b), for all k ∈ Iac.□
Remark 1. We do provide strong guarantees on the completion of the gathering phase. We also proved in Chipade and Panagou (2020b) that the attackers' clusters will be enclosed within some finite time under the state-feedback control laws as discussed in Chipade and Panagou (2020b). However, finding upper bounds on this finite time with many agents and formation interacting with each other is not a trivial task and hence providing strong conditions under which seeking and enclosing phases are also completed well before attackers reach the protected areas for each cluster of attackers is left open for future research.
7. Simulations
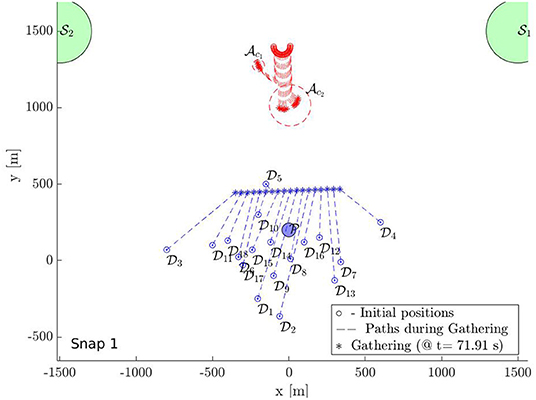
In this section, we provide a simulation of 18 defenders herding 18 attackers to with bounded control inputs. Figures 9–12 show the snapshots of the paths taken by all agents. The positions and paths of the defenders are shown in blue color, and that of the attackers in red. The string-barriers between the defenders are shown as wide solid blue lines with white dashes in them.
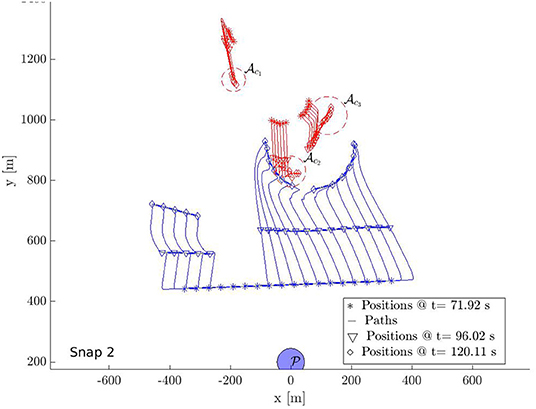
Snapshot 1 shows the paths during the gathering phase. As observed the defenders are able to gather at a location on the shortest path of the attackers to the protected area before the attacker reach there. Five attackers are already separated from the rest 13 in reaction to the incoming defenders in their path. The defenders have identified two swarms of the attackers and at the end of the gathering phase and assign two subgroups and of the defenders to and using Algorithm 1. As shown in snapshot 2, and seek and , but the attackers in swarm further start splitting and the defenders identify this newly formed and at time t = 120.11 s. The group is then split into two subgroups and of appropriate sizes and assigned to the new swarms and using Algorithm 1.
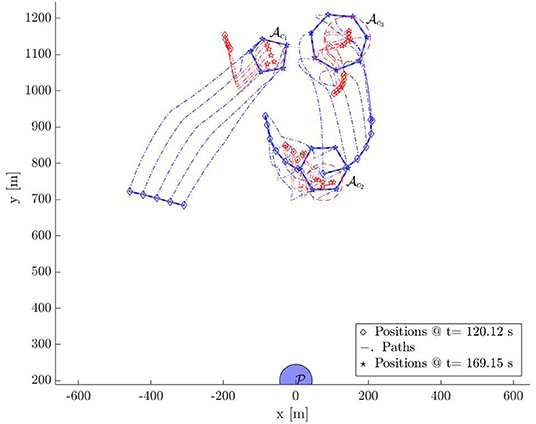
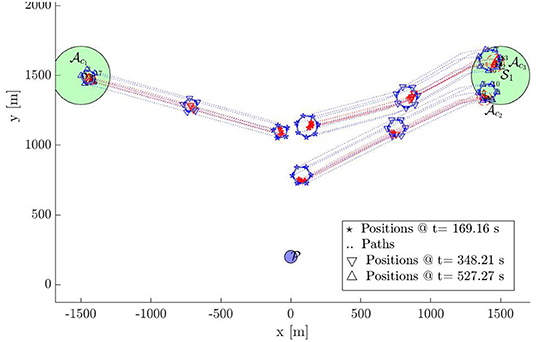
Snapshot 3 shows how the 3 subgroups of the defenders are able to enclose the identified 3 swarms of the attackers by forming Closed-StringNets around them. Snapshot 4 shows how all the three enclosed swarms of the attackers are taken to the respective closest safe areas while each defenders' group ensures collision avoidance from other defenders' groups. Additional simulations can be found at https://tinyurl.com/yypb2yv9.
8. Experimental Results
In this section, we provide hardware demonstrations of the herding approach. For this purpose, we use a fleet of in-house built 4 quadrotors each of which uses PixHawk cube 2.1 autopilot board for autonomous control. Each quadrotor is also fitted with Real-Time Kinetic (RTK) supported here+ GPS module and a ESP8266 Wi-Fi module. Figure 13 shows the overall experimental setup used for the demonstrations. The experimental setup consists of the fleet of quadrotors, a ground station computer, a wifi router, a RTK GPS base module. The ground station computer and the quadrotors are connected to a common wifi network created by the wifi router. The wifi modules on the quadrotors are used for the communication between the quadrotors and the ground station computer. The RTK GPS base module is used to provide corrections to the on-board GPS modules to provide centimeter level position accuracy. We use robot operating system (ROS) as an underlying framework to exchange and manipulate different signals used across the system. In particular, we use MAVROS package, based on MAVLink communication protocol, to exchange information between the ground station and the quadrotors.
Figure 13. Experimental setup, M-Air facility and the initial configuration (The dotted line in the figure on the left shows the safe region of operation inside M-Air facility).
As a proof of concept, we only demonstrate the “StringNet Herding” for single attacking swarm case in a centralized setting. In this setup, the ground station receives position and velocity commands from the vehicles and sends next reference commands, obtained through the MATLAB simulation running in the background based on the StringNet Herding formulation discussed earlier, to the quadrotors. The decentralized version for multi-swarm case can be tested similarly by having sufficient computational power available on the quadrotors.
We perform our experiments in an outdoor netted facility named M-Air at the University of Michigan. M-Air is a cuboid shaped netted facility as shown in Figure 13. We consider a scenario with 3 defenders and 1 attacker to demonstrate the proposed herding approach due to the limited space available in M-Air. The location of the protected area, the safe area and the initial locations of the quadrotors in M-Air are shown in Figure 13. We chose the protected area outside the M-Air so that we have large area available for quadrotors' motion. The safe area is chosen to be centered at one corner of M-Air with radius of 13 m so that the entire formation of the defenders after enclosing the attacker is able to reach inside the safe area.
Again due to limited space, we only demonstrate the enclosing and the herding phases of the StringNet Herding approach. During the experiment all the quadrotors are commanded to fly at an altitude of 2.5 m above the local ground. The paths traversed by the quadrotors starting at the initial positions as shown in Figure 13 during the experiment are shown in Figure 14. The visuals of the quadrotors at different time instances during the experiment are shown in Figure 15. In Figure 15, the defenders , , and are denoted by D1, D2, and D3, respectively, with blue oval drawn around them to highlight where they are located in the figure. Similarly, the attacker is denoted by A1 and a red oval is drawn around it to highlight it.
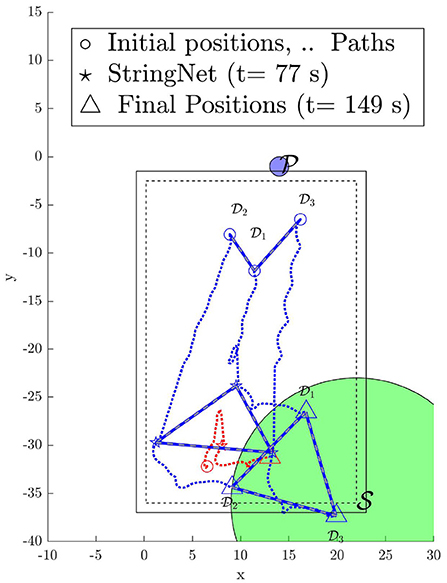
Figure 14. Paths traversed by the quadrotors during StringNet Herding (The dotted blue lines denote the paths of the defenders while the red denote that of the attackers. The solid blue lines with white dashes in them denote the string barrier assumed between the quadrotors).
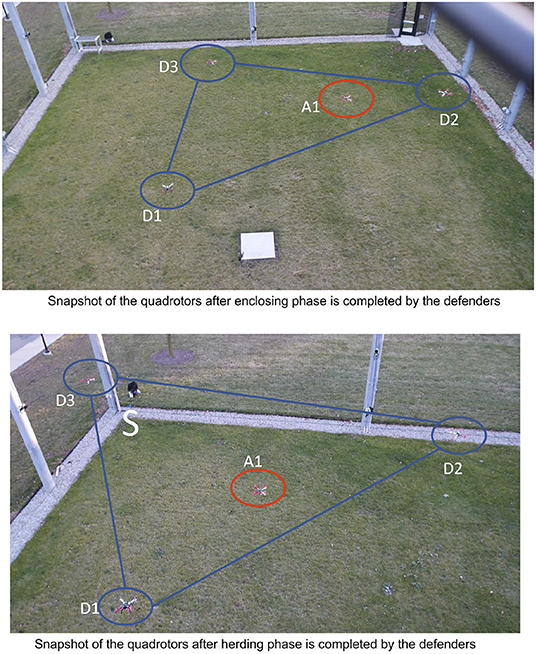
Figure 15. Snapshot of the quadrotors after enclosing and herding phases are completed by the defenders.
As one can observe in Figure 14 the attacker starts moving toward the protected area in the beginning. Once it detects the defenders on its path, it starts to move away from them in order to protect itself. But, the defenders are able to enclose the attacker successfully at around t = 77 s despite attacker's initial attempt at escaping from them, see Figure 15 for the visual of the quadrotors at this instance. After the attacker is enclosed it is herded to the safe area located at the corner of M-Air at t = 149 s as shown in Figures 14, 15 and thus the protected area is protected from the attack by the attacker. The video of the experiment can be found at https://tinyurl.com/yyd3qfty.
9. Our Thoughts on Three Dimensional (3D) Case and Non-circular Geometries
The idea of StringNet can also be applied to 3D case. In our recent work Zhang et al. (2020), we extended the idea of “StringNet Herding” to the 3D case. The StringNet in 3D case, 3D-StringNet, is a single component, orientable triangle mesh with zero genus (holes) made of triangular net-like barrier faces. Similar to 2D-Stringnet herding, 3D-StringNet herding also consists of four phases: (1) gathering, (2) seeking, (3) enclosing and (4) herding. In Zhang et al. (2020), we design three 3D-StringNet formations of the defenders namely planar, hemispherical, spherical that are required to be achieved in the phases discussed above in order to effectively enclose the attackers and herd them to a safe area.
Although we assumed that the areas and the agents are circular, the proposed algorithm can be easily extended to non-circular geometries by considering appropriate distance metric in the algorithmic formulation.
10. Conclusions and Future Work
In this paper, we proposed a clustering-based, connectivity-constrained, assignment algorithm that distributes and assigns groups of defenders against swarms of the attackers, to herd them to the closest safe area using “StringNet Herding” approach. We provide two algorithms to solve this assignment problem: centralized and decentralized, and also a heuristic based on the optimal MIQCP that finds this assignment quickly. Furthermore, we provide conditions under which the defenders can successfully herd the attackers to safe areas.
Simulations show how this proposed multi-swarm herding method improves the original “StringNet Herding” method and enables the defenders herd all the attackers to safe areas even though the attackers start splitting into smaller swarms in reaction to the defenders. Hardware experiments demonstrate the success of the approach in real applications.
In our future work, we want to study a defense approach that combines herding and interception approach together in order to defend against wide range of attacks by the attackers.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Author Contributions
VC and DP contributed to the conception and design of the study. VC formulated and simulated the theoretical algorithms and simulation case studies. VC and VM contributed to the development of experimental platform and experimental demonstrations of the herding algorithm. VC wrote major sections of the manuscript. DP is the principal investigator associated with this project. All authors contributed to manuscript revision, read, and approved the submitted version.
Funding
This work has been funded by the Center for Unmanned Aircraft Systems (C-UAS), a National Science Foundation Industry/University Cooperative Research Center (I/UCRC) under NSF Award No. 1738714 along with significant contributions from C-UAS industry members.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Footnote
1. ^This is a better choice compared to a semicircular formation as chosen in Chipade and Panagou (2020b). Because, the semicircular formation, for a given length constraint on the string barrier (), creates smaller blockage to the attackers as compared to the line formation. Although, Completing a circular formation starting from a semicircular formation of the same radius is faster. It is a trade-off between effectiveness and speed.
References
Ankerst, M., Breunig, M. M., Kriegel, H.-P., and Sander, J. (1999). Optics: ordering points to identify the clustering structure. ACM Sigmod Rec. 28, 49–60. doi: 10.1145/304181.304187
Burkard, R., Dell'Amico, M., and Martello, S. (2012). Assignment Problems, Revised Reprint, Vol. 106. Philadelphia, PA: Siam.
Cai, N., Diao, C., and Khan, M. J. (2017). A novel clustering method based on quasi-consensus motions of dynamical multiagent systems. Complexity 2017:4978613. doi: 10.1155/2017/4978613
Chen, M., Zhou, Z., and Tomlin, C. J. (2017). Multiplayer reach-avoid games via pairwise outcomes. IEEE Trans. Autom. Control 62, 1451–1457. doi: 10.1109/TAC.2016.2577619
Chipade, V. S., and Panagou, D. (2019). “Herding an adversarial swarm in an obstacle environment,” in 2019 IEEE 58th Conference on Decision and Control (CDC) (Nice: IEEE), 3685–3690.
Chipade, V. S., and Panagou, D. (2020a). Approximate time-optimal trajectories for damped double integrator in 2d obstacle environments under bounded inputs. arXiv [Preprints] arXiv:2007.
Chipade, V. S., and Panagou, D. (2020b). Multi-agent planning and control for swarm herding in 2d obstacle environments under bounded inputs. IEEE Trans. Robot. Available online at: https://tinyurl.com/yy5k6943
Chipade, V. S., and Panagou, D. (2020c). “Multi-swarm herding: Protecting against adversarial swarms,” in 2020 59th IEEE Conference on Decision and Control (CDC) (IEEE), 5374–5379. doi: 10.1109/CDC42340.2020.9303837
Coon, M., and Panagou, D. (2017). “Control strategies for multiplayer target-attacker-defender differential games with double integrator dynamics,” in Conference on Decision and Control (Melbourne, VIC: IEEE), 1496–1502.
Dai, B., and Li, W. (2014). “Flocking of -agents with arbitrary shape obstacle,” in Proceedings of the 33rd Chinese Control Conference (Nanjing: IEEE), 1311–1316.
Deptula, P., Bell, Z. I., Zegers, F. M., Licitra, R. A., and Dixon, W. E. (2018). “Single agent indirect herding via approximate dynamic programming,” in 2018 IEEE Conference on Decision and Control (CDC) (Miami Beach, FL: IEEE), 7136–7141.
Ester, M., Kriegel, H.-P., Sander, J., and Xu, X. (1996). “A density-based algorithm for discovering clusters in large spatial databases with noise,” in Kdd (Portland, OR), Vol. 96-34, 226–231.
Goel, R., Lewis, J., Goodrich, M., and Sujit, P. (2019). “Leader and16 predator based swarm steering for multiple tasks,” in 2019 IEEE International Conference on Systems, Man and Cybernetics (SMC) (Bari: IEEE), 3791–3798.
Haque, M. A., Rahmani, A. R., and Egerstedt, M. B. (2011). Biologically inspired confinement of multi-robot systems. Int. J. Bio Inspir. Comput. 3, 213–224. doi: 10.1504/IJBIC.2011.041145
Kline, A., Ahner, D., and Hill, R. (2019). The weapon-target assignment problem. Comput. Operat. Res. 105, 226–236. doi: 10.1016/j.cor.2018.10.015
Kuhn, H. W. (1955). The hungarian method for the assignment problem. Naval Res. Log. Q. 2, 83–97. doi: 10.1002/nav.3800020109
Licitra, R. A., Bell, Z. I., Doucette, E. A., and Dixon, W. E. (2018). Single agent indirect herding of multiple targets: a switched adaptive control approach. IEEE Control Syst. Lett. 2, 127–132. doi: 10.1109/LCSYS.2017.2763968
Licitra, R. A., Hutcheson, Z. D., Doucette, E. A., and Dixon, W. E. (2017). Single agent herding of n-agents: a switched systems approach. IFAC PapersOnLine 50, 14374–14379. doi: 10.1016/j.ifacol.2017.08.2020
MacQueen, J., Le Cam, L. M., and Neyman, J. (1967). “Some methods for classification and analysis of multivariate observations,” in Proceedings of the Fifth Berkeley Symposium on Mathematical Statistics and Probability, Vol. 1–14 (Oakland, CA), 281–297.
Mirjan, A., Federico, A., Raffaello, D., Fabio, G., and Matthias, K. (2016). “Building a bridge with flying robots,” in Robotic Fabrication in Architecture, Art and Design 2016 (Cham: Springer), 34–47.
Nardi, S., Mazzitelli, F., and Pallottino, L. (2018). A game theoretic robotic team coordination protocol for intruder herding. IEEE Robot. Autom. Lett. 3, 4124–4131. doi: 10.1109/LRA.2018.2857004
O'Callaghan, L., Mishra, N., Meyerson, A., Guha, S., and Motwani, R. (2002). “Streaming-data algorithms for high-quality clustering,” in Proceedings 18th International Conference on Data Engineering (San Jose, CA: IEEE), 685–694.
Öncan, T. (2007). A survey of the generalized assignment problem and its applications. Inform. Syst. Oper. Res. 45, 123–141. doi: 10.3138/infor.45.3.123
Paranjape, A. A., Chung, S.-J., Kim, K., and Shim, D. H. (2018). Robotic herding of a flock of birds using an unmanned aerial vehicle. IEEE Trans. Robot. 34, 901–915. doi: 10.1109/TRO.2018.2853610
Pierson, A., and Schwager, M. (2018). Controlling noncooperative herds with robotic herders. IEEE Trans. Robot. 34, 517–525. doi: 10.1109/TRO.2017.2776308
Raghuwaiya, K., Vanualailai, J., and Sharma, B. (2016). “Formation splitting and merging,” in International Conference on Swarm Intelligence (Bali: Springer), 461–469.
Rezende, M. D., De Lima, B. S. P., and Guimarães, S. (2018). A greedy ant colony system for defensive resource assignment problems. Appl. Artif. Intell. 32, 138–152. doi: 10.1080/08839514.2018.1451137
Sharan, R., and Shamir, R. (2000). Click: a clustering algorithm with applications to gene expression analysis. Proc. Int. Conf. Intell. Syst. Mol. Biol. 8, 307–316.
Shishika, D., Paulos, J., and Kumar, V. (2020). Cooperative team strategies for multi-player perimeter-defense games. IEEE Robot. Autom. Lett. 5, 2738–2745. doi: 10.1109/LRA.2020.2972818
Stipanović, D. M., Tomlin, C. J., and Leitmann, G. (2012). Monotone approximations of minimum and maximum functions and multi-objective problems. Appl. Math. Optimiz. 66, 455–473. doi: 10.1007/s00245-012-9179-8
Varava, A., Hang, K., Kragic, D., and Pokorny, F. T. (2017). “Herding by caging: a topological approach towards guiding moving agents via mobile robots,” in Proceedings of Robotics: Science and Systems (Cambridge, MA). doi: 10.15607/RSS.2017.XIII.074
Xu, D., and Tian, Y. (2015). A comprehensive survey of clustering algorithms. Ann. Data Sci. 2, 165–193. doi: 10.1007/s40745-015-0040-1
Yan, R., Shi, Z., and Zhong, Y. (2019). Task assignment for multiplayer reach–avoid games in convex domains via analytical barriers. IEEE Trans. Robot. 36, 107–124. doi: 10.1109/TRO.2019.2935345
Zhang, T., Ramakrishnan, R., and Livny, M. (1996). Birch: an efficient data clustering method for very large databases. ACM Sigmod Rec. 25, 103–114. doi: 10.1145/235968.233324
Zhang, W., Chipade, V. S., and Panagou, D. (2020). Herding an adversarial swarm in three-dimensional spaces. arXiv preprint arXiv:2007.04406.
11. Appendix
11.1. Proof of Lemma 2
Sum of two convex functions is always a convex function (Boyd and Vandenberghe, 2004), so it is sufficient to show that is a locally convex function to show that f(R) is a locally convex function. Let . The double derivative of g is:
We have
where Rθj = Rjcos(|θdj − θac|). Let R* be such that . We have that ϱj is a convex function of R which implies that its ℓδ-norm, , is also a convex function (Boyd and Vandenberghe, 2004). This means is the minimum value of , i.e., . Since not all defenders are co-located implying and λ > 1. From Equation (15d), we have . Then from Equation (14), we get . We know that ϱj is a twice continuously differentiable function of R for R > 0 and if we choose δ ≥ 2 then we can show that both and are continuous functions of R. From Equations (15a) and (15b), we have that and are continuous functions of R. This implies that is continuous at R = R*.
Combining the two results that is continuous and greater than 0 at R = R* implies that there exists ϵ > 0 such that for all R satisfying |R − R*| < ϵ, i.e., g(R) is locally convex in the neighborhood of R = R*. Hence f(R) is also a locally convex function in the neighborhood of R = R*.
Keywords: decision making, swarm defense, autonomous robots and drones, cooperative control feedback, multi-agent system
Citation: Chipade VS, Marella VSA and Panagou D (2021) Aerial Swarm Defense by StringNet Herding: Theory and Experiments. Front. Robot. AI 8:640446. doi: 10.3389/frobt.2021.640446
Received: 11 December 2020; Accepted: 08 March 2021;
Published: 20 April 2021.
Edited by:
George C. Karras, University of Thessaly, GreeceReviewed by:
Philip M. Dames, Temple University, United StatesAli Emre Turgut, Middle East Technical University, Turkey
Copyright © 2021 Chipade, Marella and Panagou. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Vishnu S. Chipade, dmlzaG51Y0B1bWljaC5lZHU=
 Vishnu S. Chipade
Vishnu S. Chipade Venkata Sai Aditya Marella
Venkata Sai Aditya Marella Dimitra Panagou
Dimitra Panagou