- Los Alamos National Laboratory, Information Systems and Modeling, Los Alamos, NM, United States
This study considers the hypothetical quantum network case where Alice wishes to transmit one qubit of information (specifically a pure quantum state) to
1 Introduction
Unknown quantum information cannot, in general, be cloned; this is a fundamental property of quantum mechanics (Wootters and Zurek, 1982; DGBJ, 1982). However, approximate quantum cloning is possible (Buž ek and Hillery, 1996). This study proposes that universal, symmetric, optimal quantum cloning machines can be used in a repeater-type quantum network in order to transmit single qubits to a large number (
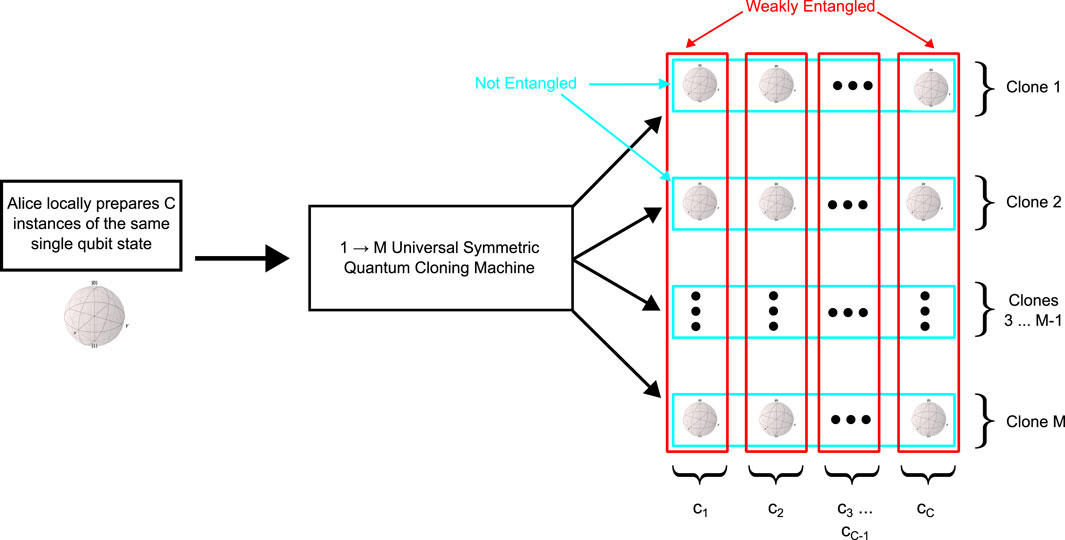
Figure 1. Qubit cloning network diagram, where the
Since the initial
Whereas typically in quantum networks, one of the central goals is to share entanglement using entanglement swapping (Shchukin and van Loock, 2022; Xu et al., 2017; Goebel et al., 2008; Bruschi et al., 2014; Zhao et al., 2010; Sangouard et al., 2008), there are a number of proposed algorithms that encode information into individual qubits, usually in the context of quantum machine learning (Pérez-Salinas, 2020; Thumwanit, 2021; Ambainis, 2009; Tapia et al., 2023). Therefore, it is conceivable that in a hypothetical future large-scale quantum network, one may wish to transmit a single qubit state to a large number of remote parties. We can imagine two potential cases where the proposed method could be used. The first is where the preparation of the single qubit state requires a non-insignificant amount of computing time, and therefore Alice wishes to reduce the total number of preparations (particularly to offload the computing time onto the quantum cloning process). The second is where a quantum cloning machine already has a direct networked connection to the intended recipients, and therefore it is easier for Alice to send qubits through the quantum cloning node in order to distribute the quantum information.
Accurately measuring which quantum state has been prepared, particularly on hardware experiments, is of considerable interest for quantum information processing. In particular, quantum state tomography of a single qubit (Roman, 2016) is the simplest of these types of tasks since there is not an exponential overhead that comes with larger system sizes. Therefore, this study strictly considers the case in which recipients measure the state of single qubits using quantum-state tomography. There are many methods for performing full quantum-state tomography, but in this case we use Pauli basis state tomography in all simulations. Geometrically, the factor by which the Bloch vector of an input message state in the Bloch sphere representation is shrunk when copied by an optimal universal symmetric quantum cloning process is given by
(Scarani et al., 2005; Bruss et al., 1998; Bruß et al., 1998) (for a qubit, e.g.,
For universal symmetric quantum cloning machines, there is a known optimal bound on the best quantum state fidelity that can be achieved for single-qubit clones. This bound is shown in Equation 1. The primary motivation of this proposed single-qubit distribution methodology is that
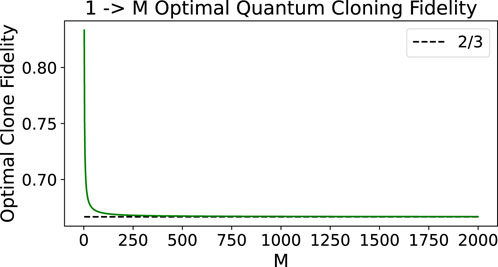
Figure 2. Ideal quantum clone fidelity (Equation 1) for
Iqbal (2022) and Iqbal et al. (2023) studied similar concepts of using quantum cloning for qubit transmission but limited the number of clones to four; they did not use single-qubit quantum state tomography (QST) or geometric extrapolation to determine the intended pure quantum state. Wang and Cai (2018); Wang and Cai (2019) similarly studied using many qubit copies to transmit information but only examined making repeated quantum copies of classical bits; they did not extend the number of clones to large
2 Methods
In order to quantify how close the post-processed quantum clones are to the original pure quantum state, we measure the distance along the surface of the Bloch sphere between the extrapolated single qubit clone vector (since universal quantum cloning only shrinks the Bloch vector by a factor given in Equation 2, and does not change the angle of the vector) and the pure quantum state vector at the point at which they intersect the surface of the Bloch sphere. This error measure thus quantifies the geodesic distance along the Bloch sphere between two Bloch vectors. This measure is 0 when the two states are exactly the same and is a maximum of
The extrapolation procedure we employ is to compute the coordinates of the mixed-state density matrix within the Bloch sphere and then compute the intersection of that Bloch vector with the surface of the Bloch sphere. The extrapolated Bloch vector intersection point with the Bloch sphere can be computed by solving the positive value of
The density matrix reconstruction was performed using a slightly modified version of Qiskit Ignis (Contributors, 2023), with the least squares parameter optimization performed using the Python 3 package “cvxopt” (Diamond and Boyd, 2016; Agra et al., 2018) which uses convex optimization (Agrawal et al., 2019; Agrawal and Boyd, 2020a; Agrawal, 2019; Agrawal and Boyd, 2020b) to perform maximum likelihood estimation (Smolin et al., 2012). Conversion formulas between density matrix representations and Bloch sphere coordinates are given in Supplementary Appendix S1. All simulations in this study assume no de-coherence of any of the quantum states during transmission (or any other part of the protocol) and assume in general ideal conditions—for example, we assume no qubit loss during transmission either. The only noise considered is shot noise (e.g., finite sampling effect).
Quantum fidelity is a standard quantum state overlap measure and therefore is most likely to be interpretable. However, the distance along the surface of the Bloch sphere provides a geometrical intuition which is very compatible with the notion of single-qubit quantum cloning, and therefore we report both error measures in this study.
2.1 Clone emulation
Single qubit clones of universal, symmetric, quantum cloning machines have well defined properties—namely, that the clones of quantum state correspond geometrically to the vector of the original state being shrunk by factor
This means that for the purposes of analyzing unentangled sequences of single-qubit clones (e.g., the unentangled sequences described in Figure 1), the relevant quantum cloning procedure can be emulated by constructing a density matrix that describes the mixed state of the original pure quantum state, shrunk by
In this study,
For all numerical simulations, a single qubit state is used since the cloning process is universal (state-independent). For the clone emulation procedure, 10,000 instances (for each number of shots) are executed instead of all
In order to verify that the clone emulation worked as expected, we performed simulations that compared classical simulations of quantum cloning circuits with the single qubit emulation. This comparison was made using parallel single-qubit quantum state tomography run using full statevector simulations of quantum cloning circuits in order to compute (ground-truth) clone quality. The quantum cloning circuits used to simulate this protocol are a variant of quantum cloning known as “quantum telecloning”; they are universal, symmetric, and optimal. The construction of these telecloning circuits is described in Pelofske (2024), Pelofske (2022), and Pelofske et al. (2022). Supplementary Appendix S1 shows an example of one of these circuits, described in the form of an explicit compiled quantum circuit diagram.
3 Results
Figure 3 verifies that the clone emulation procedure produces identical results, up to shot noise, compared with the full parallel single-qubit state tomography procedure. The full parallel single-qubit state tomography procedure was performed using the quantum telecloning circuits from Pelofske (2024), Pelofske (2022), and Pelofske et al. (2022).
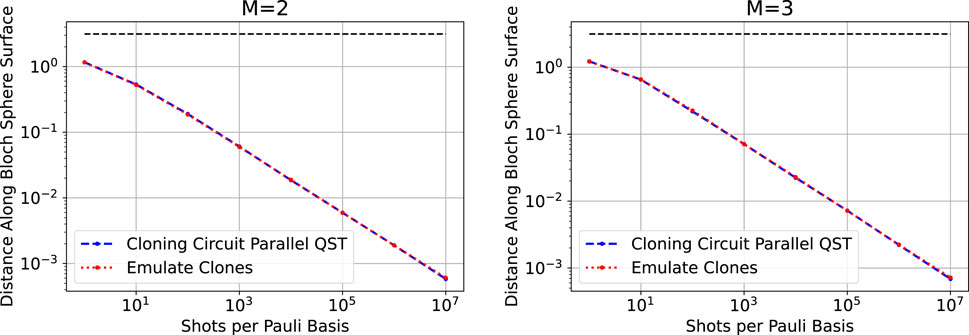
Figure 3. Comparison of single-qubit clone emulation against full quantum circuit parallel single-qubit state tomography for
Figure 4 compares direct single-qubit state tomography and extrapolated quantum state reconstruction from the approximate quantum clones. “Direct QST” refers to the procedure where Alice transmits the qubit to each of the
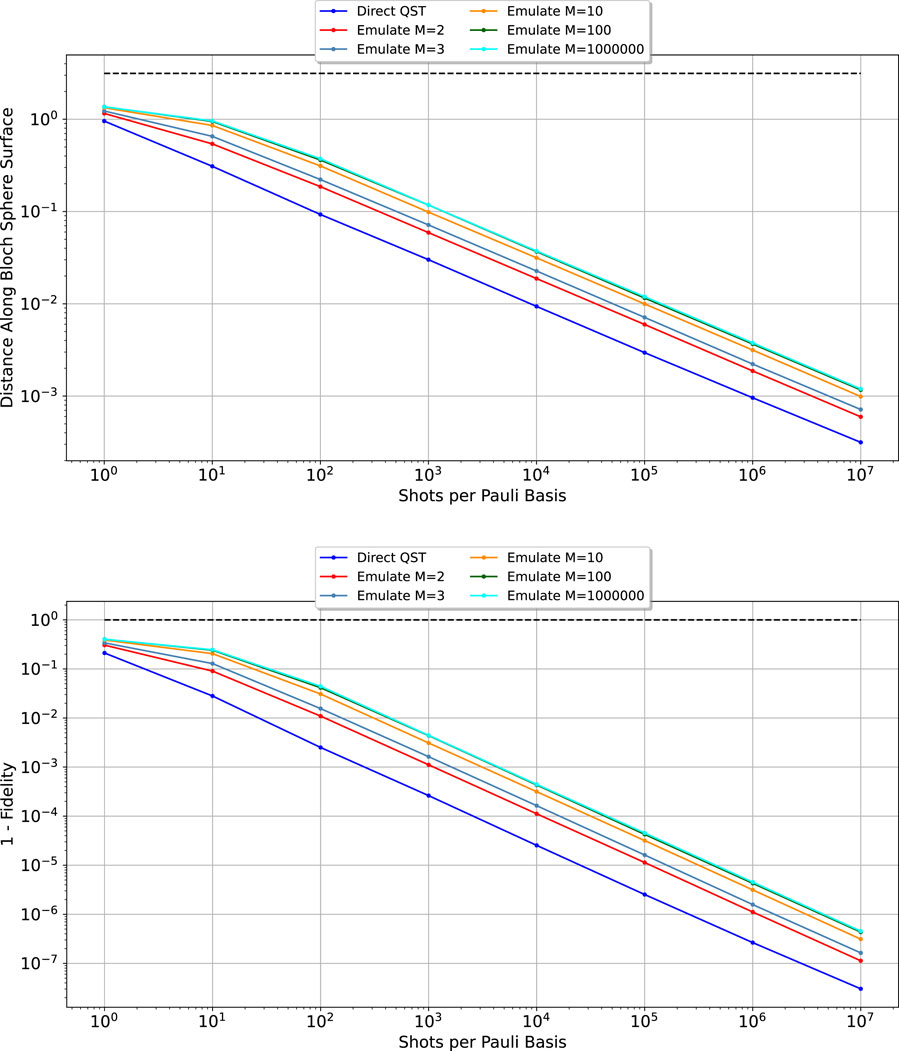
Figure 4. Comparison of direct quantum state tomography and quantum state tomography on single-qubit emulated clones, using the metric of mean distance along the Bloch sphere surface (top) and mean infidelity, which is 1 minus the standard-state overlap quantum fidelity measure (bottom). Both metrics quantify the error of the transmission protocol, when recipients measure using quantum state tomography; therefore, both error rate measures closer to 0 correspond to a lower error rate. Due to the convergence of the state overlap between the single qubit clones and the original state (Equation 1), for example, the error rates of
Figure 4 shows that the proposed protocol (Figure 1) provides a significant improvement over direct single-qubit transmission when
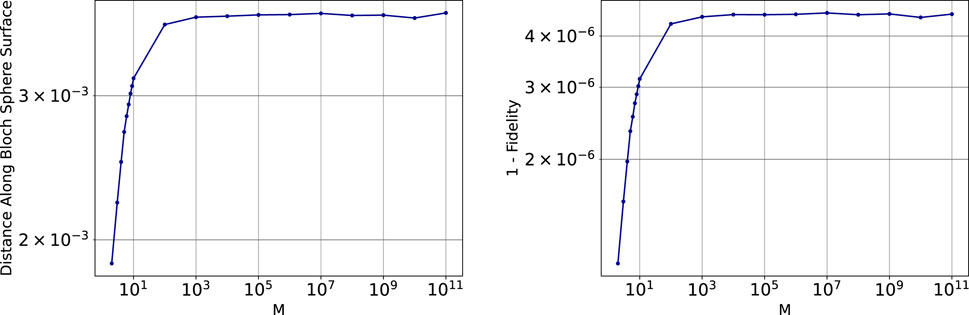
Figure 5. Average error rate (y-axis) as a function of
The breakeven point is defined as the point where the two methods (the direct single qubit transmission and the proposed quantum cloning protocol) require the same number of message qubits to be prepared by Alice in order for the receiver error rate (for all
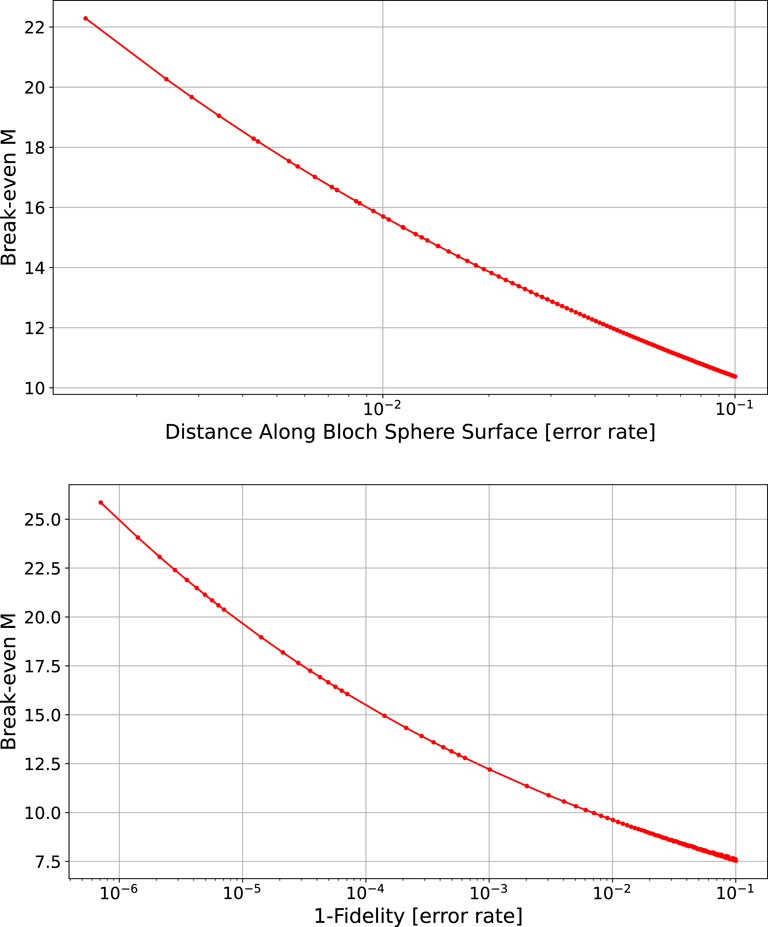
Figure 6. Average breakeven point in terms of
For a desired error rate, if
Figure 6 contains three key observations. The first is that the scaling of the breakeven point as a function of
4 Discussion and conclusion
This study proposes a hypothetical use for a large scale universal symmetric quantum cloning machine in the context of transmitting a single qubit from a local sender Alice to a large number of remote receivers
1. Single-qubit clones retain the same Bloch angle as the parent clone in the Bloch sphere representation; the loss of fidelity corresponds to a shrinking of the Bloch vector, making the clone a mixed quantum state when the original quantum state was pure. This means that given a sufficient number of samples of an approximate quantum clone generated from the same input quantum state, the original quantum state can be extrapolated by extending the computed mixed state Bloch vector to the surface of the Bloch sphere.
2. The state overlap (e.g., fidelity) of the clones generated by
The primary logical next question is the extent to which more general (universal, symmetric)
The emphasis of this study is to show proof-of-principle for a specific type of quantum networking protocol. Importantly, this type of protocol is far from currently feasible on real quantum computers or quantum networks; this study does not examine real world aspects that would certainly be relevant, such as timing. Quantifying how real world decoherence error rates, both for the transmission and for the preparation of the quantum cloning circuit, impact the reconstruction error is another important future question. Noise, particularly de-coherence, could both shrink the length of the Bloch vector as well as bias its angle. Nevertheless, the implementation shown here uses the real-world characterization protocol of quantum state tomography, thus showing that this could be algorithmically implemented if there was hardware that could perform these operations. It would need to be possible to obtain good low error rate state reconstruction despite very large numbers of clones being generated in total.
Although not investigated here, this proposed protocol could certainly also be applied to message qubits which are mixed states. However, this would cause the cloning fidelity to be even lower than it is when the message qubit is a pure quantum state, thus necessitating more copies to passed through the quantum cloning machine in order to achieve reasonably low error rate single-qubit state tomography for the receivers.
Data availability statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Author contributions
EP: Methodology, Funding acquisition, Formal Analysis, Visualization, Software, Writing – review and editing, Data curation, Project administration, Validation, Conceptualization, Writing – original draft, Resources, Supervision, Investigation.
Funding
The author(s) declare that financial support was received for the research and/or publication of this article. This work was supported by the U.S. Department of Energy through the Los Alamos National Laboratory. Los Alamos National Laboratory is operated by Triad National Security, LLC, for the National Nuclear Security Administration of U.S. Department of Energy (Contract No. 89233218CNA000001). Research presented in this article was supported by the NNSA’s Advanced Simulation and Computing Beyond Moore’s Law Program at Los Alamos National Laboratory.
Acknowledgments
This research used resources provided by the Darwin testbed at Los Alamos National Laboratory (LANL) which is funded by the Computational Systems and Software Environments subprogram of LANL’s Advanced Simulation and Computing program (NNSA/DOE). LANL report number LA-UR-23-31,425.
Conflict of interest
The author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Generative AI statement
The author(s) declare that no Generative AI was used in the creation of this manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Supplementary material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/frqst.2025.1598893/full#supplementary-material
References
Agrawal, A. (2019). “Differentiable convex optimization layers,” in Advances in neural information processing systems, 9558–9570.
Agrawal, A., and Boyd, S. (2020b). Differentiating through log-log convex programs. arXiv, 12553. Available online at: https://arxiv.org/abs/2004.12553
Agrawal, A., Diamond, S., and Boyd, S. (2019). Disciplined geometric programming. Optim. Lett. 13.5, 961–976. doi:10.1007/s11590-019-01422-z
Agrawal, A., Verschueren, R., Diamond, S., and Boyd, S. (2018). A rewriting system for convex optimization problems. J. Control Decis. 5.1, 42–60. doi:10.1080/23307706.2017.1397554
Bae, J., and Acín, A. (2006). Asymptotic quantum cloning is state estimation. Phys. Rev. Lett. 97 (3), 030402. doi:10.1103/PhysRevLett.97.030402
Bennett, C. H., and Brassard, G. (2014). Quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 7–11. doi:10.1016/j.tcs.2014.05.025
Bouchard, F., Fickler, R., Boyd, R. W., and Karimi, E. (2017). High-dimensional quantum cloning and applications to quantum hacking. Sci. Adv. 3.2, e1601915. doi:10.1126/sciadv.1601915
Bruschi, D. E., Barlow, T. M., Razavi, M., and Beige, A. (2014). Repeat-until-success quantum repeaters. Phys. Rev. A 90 (3), 032306. doi:10.1103/PhysRevA.90.032306
Bruss, D., Ekert, A., and Macchiavello, C. (1998). Optimal universal quantum cloning and state estimation. Phys. Rev. Lett. 81 (12 1998), 2598–2601. doi:10.1103/PhysRevLett.81.2598
Bruß, D., Cinchetti, M., Mauro D’Ariano, G., and Macchiavello, C. (2000). Phase-covariant quantum cloning. Phys. Rev. A 62 (1), 012302. doi:10.1103/PhysRevA.62.012302
Bruß, D., DiVincenzo, D. P., Ekert, A., Fuchs, C. A., Macchiavello, C., and Smolin, J. A. (1998). Optimal universal and state-dependent quantum cloning. Phys. Rev. A 57 (4), 2368–2378. doi:10.1103/PhysRevA.57.2368
Buž ek, V., and Hillery, M. (1996). Quantum copying: beyond the no-cloning theorem. Phys. Rev. A 54 (3), 1844–1852. doi:10.1103/physreva.54.1844
Buzek, V., and Hillery, M. (1998). Universal optimal cloning of qubits and quantum registers. doi:10.1103/PhysRevLett.81.5003
Chefles, A., and Barnett, S. M. (1999). Strategies and networks for state-dependent quantum cloning. Phys. Rev. A 60 (1), 136–144. doi:10.1103/PhysRevA.60.136
Chen, H., Lu, D., Chong, B., Qin, G., Zhou, X., Peng, X., et al. (2011). Experimental demonstration of probabilistic quantum cloning. Phys. Rev. Lett. 106 (18), 180404. doi:10.1103/PhysRevLett.106.180404
Christandl, M., Renner, R., and Ekert, A. (2004). A generic security proof for quantum key distribution. Available online at: https://arxiv.org/abs/quant-ph/0402131.
Contributors, Q. (2023). Qiskit: an open-source framework for quantum computing. doi:10.5281/zenodo.2573505
Cummins, H. K., Jones, C., Furze, A., Soffe, N. F., Mosca, M., Peach, J. M., et al. (2002). Approximate quantum cloning with nuclear magnetic resonance. Phys. Rev. Lett. 88 (18), 187901. doi:10.1103/PhysRevLett.88.187901
Dgbj, D. (1982). Communication by EPR devices. Phys. Lett. A 92 (6), 271–272. doi:10.1016/0375-9601(82)90084-6
Diamond, S., and Boyd, S. (2016). CVXPY: a Python-embedded modeling language for convex optimization. J. Mach. Learn. Res. 17.83, 83–85.
Du, J., Durt, T., Zou, P., Li, H., Kwek, L. C., Lai, C. H., et al. (2005). Experimental quantum cloning with prior partial information. Phys. Rev. Lett. 94 (4), 040505. doi:10.1103/PhysRevLett.94.040505
Durt, T., Fiurášek, J. r, and Cerf, N. J. (2005). Economical quantum cloning in any dimension. Phys. Rev. A 72, 5. doi:10.1103/physreva.72.052322
Fan, H., Imai, H., Matsumoto, K., and Wang, X. B. (2003). Phase-covariant quantum cloning of qudits. Phys. Rev. A 67 (2), 022317. doi:10.1103/PhysRevA.67.022317
Fan, H., Matsumoto, K., Wang, X. B., and Wadati, M. (2001). Quantum cloning machines for equatorial qubits. Phys. Rev. A 65 (1), 012304. doi:10.1103/PhysRevA.65.012304
Fan, H., Wang, Y. N., Jing, L., Yue, J. D., Shi, H. D., Zhang, Y. L., et al. (2014). Quantum cloning machines and the applications. Phys. Rep. 544.3, 241–322. doi:10.1016/j.physrep.2014.06.004
Fiurasek, J., Filip, R., and Cerf, N. J. (2005). Highly asymmetric quantum cloning in arbitrary dimension.
Fiurášek, J. R (2001). Optical implementation of continuous-variable quantum cloning machines. Phys. Rev. Lett. 86 (21), 4942–4945. doi:10.1103/physrevlett.86.4942
Gisin, N., and Massar, S. (1997). Optimal quantum cloning machines. Phys. Rev. Lett. 79 (11 1997), 2153–2156. doi:10.1103/PhysRevLett.79.2153
Goebel, A. M., Wagenknecht, C., Zhang, Q., Chen, Y. A., Chen, K., Schmiedmayer, J., et al. (2008). Multistage entanglement swapping. Phys. Rev. Lett. 101 (8), 080403. doi:10.1103/PhysRevLett.101.080403
Hardy, L., and Song, D. D. (1999). No signalling and probabilistic quantum cloning. Phys. Lett. A 259 (5), 331–333. doi:10.1016/s0375-9601(99)00448-x
Iblisdir, S., Acín, A., Cerf, N. J., Filip, R., Fiurášek, J., and Gisin, N. (2005). Multipartite asymmetric quantum cloning. Phys. Rev. A 72 (4), 042328. doi:10.1103/PhysRevA.72.042328
Iqbal, M. (2022). “Quantum bit retransmission using universal quantum copying machine,” in 2022 international conference on optical network design and modeling (ONDM), 1–3. doi:10.23919/ONDM54585.2022.9782866
Iqbal, M., Velasco, L., Costa, N., Napoli, A., Pedro, J., and Ruiz, M. (2023). Investigating imperfect cloning for extending quantum communication capabilities. Sensors 23, 7891. doi:10.3390/s23187891
Jozsa, R. (1994). Fidelity for mixed quantum states. J. Mod. Opt. 41.12, 2315–2323. doi:10.1080/09500349414552171
Karimipour, V., and Rezakhani, A. T. (2002). Generation of phase-covariant quantum cloning. Phys. Rev. A 66 (5), 052111. doi:10.1103/PhysRevA.66.052111
Liu, S., Lou, Y., Chen, Y., and Jing, J. (2021). All-optical optimal N-to-M quantum cloning of coherent states. Phys. Rev. Lett. 126 (6), 060503. doi:10.1103/PhysRevLett.126.060503
Meurer, A., Smith, C. P., Paprocki, M., Čertík, O., Kirpichev, S. B., Rocklin, M., et al. (2017). SymPy: symbolic computing in Python. PeerJ Comput. Sci. 3, e103–e5992. doi:10.7717/peerj-cs.103
Murao, M., Jonathan, D., Plenio, M. B., and Vedral, V. (1999). Quantum telecloning and multiparticle entanglement. Phys. Rev. A 59 (1), 156–161. doi:10.1103/PhysRevA.59.156
Nagali, E., Giovannini, D., Marrucci, L., Slussarenko, S., Santamato, E., and Sciarrino, F. (2010). Experimental optimal cloning of four-dimensional quantum states of photons. Phys. Rev. Lett. 105 (7), 073602. doi:10.1103/PhysRevLett.105.073602
Paris, M., and Rehacek, J. (2004). “Quantum state estimation,”, 649. Springer Science and Business Media.
Pelofske, E. (2022). “Quantum telecloning on NISQ computers,” in 2022 IEEE international conference on quantum computing and engineering (QCE) (IEEE). doi:10.1109/qce53715.2022.00083
Pelofske, E. (2024). Probing quantum telecloning on superconducting quantum processors. IEEE Trans. Quantum Eng. 5, 1–19. doi:10.1109/tqe.2024.3391654
Pelofske, E., Bärtschi, A., and Eidenbenz, S. (2022). “Optimized telecloning circuits: theory and practice of nine NISQ clones,” in 2022 IEEE international conference on rebooting computing (ICRC) (IEEE). doi:10.1109/icrc57508.2022.00009
Pérez-Salinas, A. (2020). “Data re-uploading for a universal quantum classifier,” in Quantum 4 (issn), 226, 2521–327X. doi:10.22331/q-2020-02-06-226
Renner, R., Gisin, N., and Kraus, B. (2005). Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72 (1), 012332. doi:10.1103/PhysRevA.72.012332
Roman, S. (2016). Quantum state tomography of a single qubit: comparison of methods. J. Mod. Opt. 63 (18), 1744–1758. doi:10.1080/09500340.2016.1142018
Sangouard, N., Simon, C., Zhao, B., Chen, Y. A., de Riedmatten, H., Pan, J. W., et al. (2008). Robust and efficient quantum repeaters with atomic ensembles and linear optics. Phys. Rev. A 77 (6), 062301. doi:10.1103/PhysRevA.77.062301
Scarani, V., Iblisdir, S., Gisin, N., and Acín, A. (2005). Quantum cloning. Rev. Mod. Phys. 77 (4), 1225–1256. doi:10.1103/revmodphys.77.1225
Shchukin, E., and van Loock, P. (2022). Optimal entanglement swapping in quantum repeaters. Phys. Rev. Lett. 128 (15), 150502. doi:10.1103/PhysRevLett.128.150502
Shor, P. W., and Preskill, J. (2000). Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85 (2), 441–444. doi:10.1103/physrevlett.85.441
Smolin, J. A., Gambetta, J. M., and Smith, G. (2012). Efficient method for computing the maximum-likelihood quantum state from measurements with additive Gaussian noise. Phys. Rev. Lett. 108, 070502. doi:10.1103/physrevlett.108.070502
Tapia, E. P. A, Scarpa, G., and Pozas-Kerstjens, A. (2023). A didactic approach to quantum machine learning with a single qubit. Phys. Scr. 98 (5), 054001. doi:10.1088/1402-4896/acc5b8
van Loock, P., and Braunstein, S. L. (2001). Telecloning of continuous quantum variables. Phys. Rev. Lett. 87 (24 2001), 247901. doi:10.1103/PhysRevLett.87.247901
Wang, M., and Cai, Q. (2018). Filling the gap between quantum no-cloning and classical duplication. arXiv 1803.05602.
Wang, M. H., and Cai, Q. (2019). Duplicating classical bits with universal quantum cloning machine. Sci. China Phys. Mech. and Astronomy 62, 30312–30315. doi:10.1007/s11433-018-9296-3
Wootters, W. K., and Zurek, W. H. (1982). A single quantum cannot be cloned. Nature 299, 802–803. doi:10.1038/299802a0
Xu, P., Yong, H. L., Chen, L. K., Liu, C., Xiang, T., Yao, X. C., et al. (2017). Two-hierarchy entanglement swapping for a linear optical quantum repeater. Phys. Rev. Lett. 119 (17), 170502. doi:10.1103/PhysRevLett.119.170502
Yang, Y., and Chiribella, G. (2013). ““Is Global Asymptotic Cloning State Estimation?” en,” in Schloss Dagstuhl – Leibniz-Zentrum für Informatik. doi:10.4230/LIPICS.TQC.2013.220
Keywords: quantum cloning, quantum cloning and quantum key distribution, quantum copying, single qubit, quantum state tomography, quantum network, quantum communication, quantum computing
Citation: Pelofske E (2025) Single-qubit multi-party transmission using universal symmetric quantum cloning. Front. Quantum Sci. Technol. 4:1598893. doi: 10.3389/frqst.2025.1598893
Received: 24 March 2025; Accepted: 04 June 2025;
Published: 04 July 2025.
Edited by:
Wei-Dong Li, Shenzhen Technology University, ChinaReviewed by:
Abdulbast A. Abushgra, Ashland University, United StatesUtpal Roy, Indian Institute of Technology Patna, India
Copyright © 2025 Pelofske. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Elijah Pelofske, ZXBlbG9mc2tlQGxhbmwuZ292
 Elijah Pelofske
Elijah Pelofske