- 1Shandong Key Laboratory of Optical Communication Science and Technology, School of Physics Science and Information Technology, Liaocheng University, Liaocheng, China
- 2Key Laboratory of Broadband Wireless Communication and Sensor Network Technology, Nanjing University of Posts and Telecommunications, Nanjing, China
- 3Shanghai Key Laboratory of Trustworthy Computing, East China Normal University, Shanghai, China
In this article, the secrecy performance of a hybrid radio frequency (RF)/visible light communication (VLC) system is studied. In this hybrid system, the source node (i.e., Alice) transmits information to the relay node via the outdoor RF link. Nakagami-m fading and path loss are considered for the RF link. The relay node includes an outdoor component and an indoor component, which are connected by using a wired medium. The outdoor component receives and recovers information by using the decode-and-forward (DF) relaying scheme and then transmits it to the indoor component. The indoor component then converts the received electrical signal into an optical signal by using a light-emitting diode. A legitimate receiver (i.e., Bob) deployed on the floor receives the optical signal. An eavesdropper (i.e., Eve) deployed in the RF or VLC link wiretaps the confidential information. In this study, we use the secrecy outage probability (SOP) and the probability of strictly positive secrecy capacity (SPSC) to evaluate the system performance. We then obtain the closed-form expression for a lower bound on the SOP and an exact closed-form expression for the probability of SPSC when the RF and VLC links are wiretapped, respectively. Numerical results are presented to validate the accuracy of our derivations. We further discuss the effects of the noise standard deviation, the equivalent threshold of the signal-to-noise ratio, and the floor radius on the system secrecy performance when the VLC link is eavesdropped upon. For the case when the RF link is eavesdropped upon, the impacts of the distance between Alice and the relay, the path loss exponent, the fading factor, and the distance between Alice and Eve on secrecy performance are also provided.
1 Introduction
In the past ten years, the research on conventional radio frequency (RF) wireless communication has intensified [1]. With the rapid development of solid-state lighting, the visible light communication (VLC) technology has emerged as a promising technology in recent years [2]. VLC has a wider modulation bandwidth, less susceptibility to electromagnetic interference, and a larger capacity than RF communications. In VLC, both illumination and communication are simultaneously implemented [3]. The performance of VLC, however, heavily depends on the line-of-sight (LoS) connection, and it also has a limited coverage area. Therefore, the performance of VLC suffers severe degradation in the absence of the LoS link. Moreover, the light emitted by a light-emitting diode (LED) in VLC is easily blocked by obstacles [4]. In contrast, RF communication has higher transmission reliability even in the absence of the LoS link [5–10]. To address the issues mentioned above, hybrid VLC/RF technology is proposed to tackle the aforementioned problems. The VLC technology can overcome the shortcomings of RF spectrum shortage and large power consumption, while the RF technology compensates for the dependence of VLC on LoS to improve the communication coverage and also reduces the power consumption. Besides, VLC and RF signals do not interfere with each other [7].
There are several studies on hybrid wireless systems combining RF and VLC technologies. In reference [3], a random geometric framework for the coexistence of VLC and RF networks was proposed, and its coverage and achievable rate analysis for typical users were studied. In reference [5], the power and bandwidth allocation problem for the energy efficiency maximization of the VLC/RF hybrid system was solved, and the impact of the system parameters on the energy efficiency of the mixed system was investigated. The research in reference [7] showed that compared with the network that only uses RF or VLC, a hybrid RF/VLC network can reduce the probability of interruption by reducing the area power consumption. An effective beamforming design was also discussed in reference [8].
Since the physical layer security (PLS) utilizes the randomness of the wireless channel and noise, it is often considered to be a viable solution to ensure secure communication and prevent eavesdropping and jamming attacks [11]. In reference [9], PLS characteristics of the hybrid RF/VLC system were studied, the problem of minimizing the power consumption was also studied, and a zero-forcing beamforming strategy and a minimum power allocation algorithm were proposed. The PLS of indoor heterogeneous VLC/RF networks based on known and unknown channel state information (CSI) was further analyzed in reference [12]. In reference [13], the PLS transmission for VLC with simultaneous lightwave information and power transfer was investigated.
Besides, dual-hop relay technology has been considered to be another efficient technology that can be used to increase the capacity and expand the coverage of low-power wireless networks [14]. In such systems, the signal propagates from the source node to the destination node through a relay node, so that the connection can be realized in the case of high path loss and deep attenuation in the traditional direct transmission between the source node and the destination node. In references [4, 10], the dual-hop hybrid systems with energy harvesting relays were investigated. Specifically, the authors of reference [4] optimized the VLC/RF hybrid system from the perspective of maximizing the data rate, while the authors of reference [10] investigated the data packet transmission performance of the VLC/RF hybrid system. Furthermore, in reference [14], the performance of hybrid free-space optical (FSO) communication and RF dual-hop systems based on amplify-and-forward relaying and CSI-assisted relaying were analyzed, and the closed-form expressions for the outage probability and the average bit error rate were derived in the high signal-to-noise ratio (SNR) regime. In reference [15], the expressions of the outage probability, bit error rate, and average capacity of the hybrid RF/FSO system were derived for the first time. For amplify-and-forward relay, the outage probability and bit error probability of the hybrid RF/FSO system were also obtained in reference [16]. There are many studies on the PLS of the dual-hop system. It is noteworthy that the authors of references [17–20] considered the mixed RF/FSO transmission systems. The lower bound of the secrecy outage probability (SOP) and the closed-form expression of the probability of strictly positive secrecy capacity (SPSC) when an eavesdropper is eavesdropping on the FSO link were derived in reference [17]. Furthermore, for a mixed RF/FSO downlink simultaneous wireless information and power transfer system, reference [18] derived the exact and asymptotic expressions of the SOP. The closed-form expressions for the lower bound of the SOP and the exact average secrecy capacity of mixed RF/FSO systems were also derived in reference [19], where an eavesdropper node eavesdrops on the FSO hop. In reference [20], the secrecy outage performance of a mixed RF/FSO system with imperfect CSI was analyzed. To the best of the authors’ knowledge, in the aforementioned works, Shannon’s capacity is often employed to evaluate the performance of the VLC link [11, 12]. However, in the actual VLC environment, the visible-light signal is an optical intensity signal, which means that the signal amplitude of the VLC system is non-negative. Furthermore, in the VLC system, it is necessary to consider illumination while transmitting data; therefore, the average optical intensity should be a fixed value according to the users’ dimming requirement [21]. Therefore, Shannon’s capacity is not suitable for VLC. Based on the considerations above, it is necessary to analyze the secrecy performance of the hybrid RF/VLC dual-hop relaying systems.
In this study, we analyze the PLS performance of a hybrid RF/VLC system. The main contributions are summarized as follows:
• Based on the system model, when the VLC link is eavesdropped upon, the probability density functions (PDFs) of the channel gain for the RF and VLC channels are derived, respectively. Using those PDFs, we then derive the closed-form expressions for the lower bound of the SOP and the probability of SPSC. It is also shown that the performance gap between theoretical results and simulation results is small, which verifies the accuracy of the derived expression. Moreover, the SOP increases with the noise standard deviation of Bob and decreases with the noise standard deviation of Eve. The SNR threshold degrades the system secrecy performance. The performance of the probability of SPSC mainly depends on the VLC, which deteriorates with Bob’s noise standard deviation and improves with Eve’s noise standard deviation or the radius of the floor.
• For the case when the RF link is eavesdropped upon, the PDFs and cumulative distribution functions (CDFs) of the instantaneous SNR at the relay node and the Eve node have been derived. Based on these statistic distributions, we also derive the closed-form expressions for the lower bound of the SOP and the probability of SPSC. The results further show that the performance gap between theoretical results and simulation results is also small, which verifies the accuracy of the derived expressions. In this case, the performance of the probability of SPSC mainly depends on the RF link, and all theoretical results of the probability of SPSC match the simulation results very well. Numerical results further confirm that the system secrecy performance is degraded with the distance between the Alice and relay nodes and the channel fading factor and improved by increasing the path loss exponent.
This article is arranged as follows. In Section 2, the system model of the hybrid VLC/RF system is presented. In Section 3, we derive the lower bound of the SOP and the exact expression of the probability of SPSC when the VLC link is eavesdropped upon. The secrecy performance analysis when the RF link is eavesdropped upon is presented in Section 4. Section 5 presents some numerical results. Finally, the conclusion of this article is given in Section 6.
2 System Model
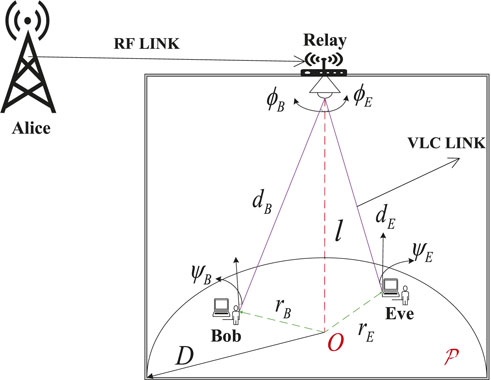
As shown in Figure 1, we consider a dual-hop hybrid RF/VLC network, which includes an outdoor RF link and an indoor VLC link. The hybrid network is composed of a source node (Alice), a relay node, an eavesdropper (Eve), and a legitimate receiver (Bob). The relay node includes an outdoor component and an indoor component, which are connected by using a wired medium. In this study, we assume that the outdoor component receives and recovers information by using the DF relaying scheme and then transmits it to the indoor component. The indoor component converts the received electrical signal to an optical signal by using an LED. There is no direct communication between Alice and Bob; information must be transmitted through the relay node. The communication arranges two transmission time slots. In the first time slot, Alice transmits confidential information x to the outdoor component of the relay over the RF channel. In the second time slot, the indoor component of the relay forwards the optical signal X to Bob through the indoor VLC channel. Both Bob and Eve deploy photodiodes to receive information and perform photoelectric conversion. When Alice transmits to Bob, Eve attempts to intercept the secret information.
2.1 RF Link
In the first time slot, the received signal at the relay can be written as follows:
where
The instantaneous SNR
In the RF link,
where
where
Furthermore,
where λ denotes the path loss exponent,
Therefore, the PDF of
By using (8.351.1) in reference [23], the cumulative distribution function (CDF) of
where
2.2 VLC Link
In the second time slot, we consider an indoor VLC link. To facilitate the analysis, it is assumed that the receiving area
where U represents the position of Bob and W represents the position of Eve.
In the second time slot, the received signals at Bob and Eve can be expressed as follows:
where X represents the input optical intensity,
Because the information is modulated as the instantaneous optical intensity, X must meet the non-negative constraint as follows [21]:
Although the optical intensity can be adjusted according to the dimming requirements, the average optical intensity cannot change with time. Therefore, the dimmable average optical intensity constraint is given by the following [21]:
where ξ indicates the dimming target, and P indicates the nominal optical intensity of the LED. Because the user can adjust the optical intensity at will, the dimming target must satisfy the following [21]:
Without loss of generality, we assume that both Bob and Eve can be illuminated by the LED, and thus, the illumination angle
where
where
According to Eqs. 8 and 9, the CDF of
Furthermore, the PDF of
where
The PDF of the channel gain
where
Substituting Eq. 15 and Eq. 17 into Eq. 18, we can obtain the PDF of
where
3 Secrecy Performance Analysis When VLC Link Is Eavesdropped Upon
3.1 SOP Analysis
In this subsection, we analyze the SOP of the hybrid RF/VLC system. Because there are no eavesdroppers in the RF link, the instantaneous SC of the first hop is its instantaneous channel capacity, that is,
In the VLC link, we need to consider the average and non-negative constraints simultaneously. Therefore, Shannon’s capacity is not applicable to the VLC link [25]. For VLC with constraints as in Eqs 11, 12, a lower bound on the instantaneous SC is given by the following [26]:
Furthermore, according to Eq. 19,
where
As is known, the hybrid system is equivalent to a series network, so the capacity of the system is determined by the worse channel [27]. Therefore, the instantaneous SC of the entire hybrid system is the minimum of
The SOP is an important performance metric to evaluate the PLS of a wireless communication system. It is defined as the probability that the instantaneous SC is lower than the target capacity
Substituting Eq. 26 into Eq. 27, the SOP is rewritten as follows:
where
and
where
From Eqs 28, 29, and 31, the SOP is lower-bounded by the following:
In Eq. 25,
where
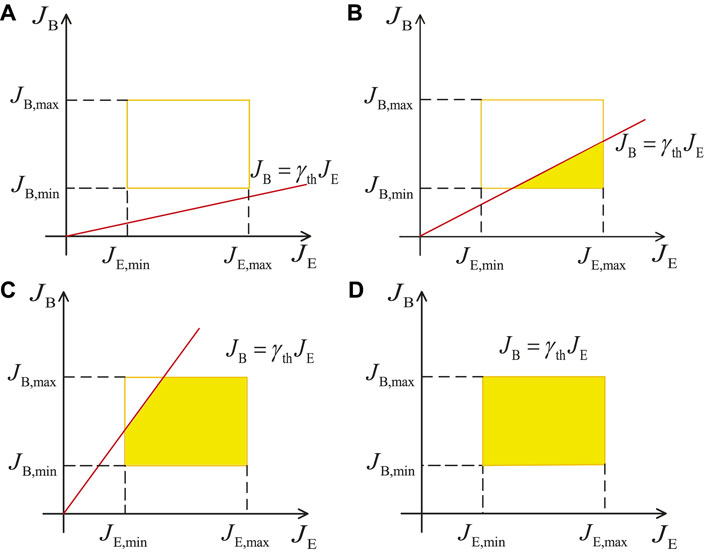
FIGURE 2. Four cases of the integral of
and
where
The lower bound of the SOP can be further derived as follows:
Substituting Eq. 34 and Eq. 35 into Eq. 36, the expression for the lower bound of the SOP can be obtained as Eq. 37, as shown below:
Remark 1.According toEq. 33, with the increase in
Remark 2.With the increase in
3.2 Probability of SPSC Analysis
In secure communications, the probability of SPSC is a fundamental benchmark that is employed to emphasize the existence of SC [17]. In this subsection, we derive the probability of SPSC of the hybrid RF/VLC system. The probability of SPSC is defined as follows:
According to Eq. 23,
and
Remark 3.Since
It should be noted that the value of Eq. 40 also depends on the integral region. Figure 3 shows four cases of the integral region in Eq. 40. Based on the four cases, the probability of SPSC in Eq. 40 can be written as follows:
Since
and
Finally, the closed-from expression of the probability of SPSC can be expressed as follows:
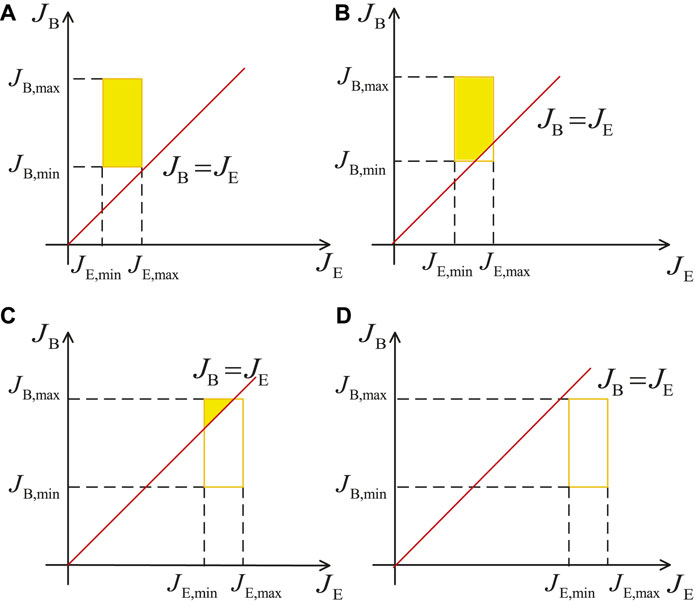
FIGURE 3. Four cases of the integral of
Remark 4.Opposite to Remark 1, with the increase in
Remark 5.As the radius D increases, the probability of Eve being placed far away from Bob increases and the probability of Eve eavesdropping on confidential information decreases. Therefore, the channel gain
4 Secrecy Performance Analysis When RF Link Is Eavesdropped Upon
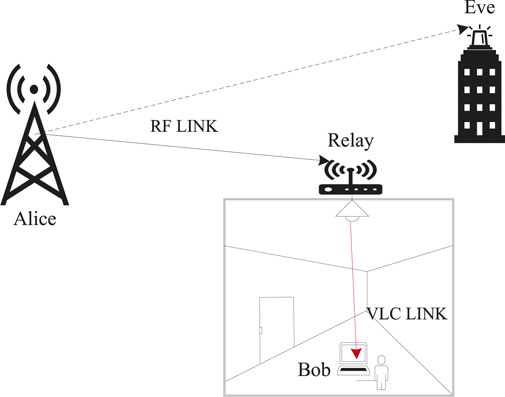
In Section 3, the SOP and the probability of the SPSC have been analyzed when the VLC link is eavesdropped upon. However, in practice, the RF link is more vulnerable to unauthorized users, so it is necessary to analyze the secrecy performance of the hybrid RF/VLC system when the RF link is eavesdropped upon. The system model is shown in Figure 4.
4.1 SOP Analysis
In this subsection, we analyze the SOP of a hybrid RF/VLC system when the RF link is eavesdropped upon. The instantaneous SC of the first hop is given by the following:
where
Similarly, the
where the PDF of
where
where
Because there are no eavesdroppers in the VLC link, the instantaneous SC of the first hop is its instantaneous channel capacity, that is, a lower bound on the instantaneous SC of the second hop is written by using the following [21]:
Similarly, the instantaneous SC of the entire hybrid system is the minimum of
We have known that SOP can be given by
where
and
Substituting Eqs 54 and 55 into Eq. 53, we have the following:
It is mathematically difficult to obtain the exact close-form expression for SOP as shown in Eq. 56. Therefore, we alternatively evaluate the lower bound of SOP. We assume that
where
Remark 6.With the increase in
Remark 7.According toEqs 2, 46, and 54, it is seen that by increasing λ, the value of the
Remark 8.By increasing
4.2 Probability of SPSC Analysis
Similarly, the probability of SPSC of the hybrid RF/VLC system when an eavesdropper eavesdrops on the RF link can be written as follows:
According to Eq. 45,
and
Based on Eqs 60 and 61, the closed-from expression of the probability of SPSC in Eq. 59 can be written as follows:
Remark 9.Similar to Remark 6, the probability of the SPSC decreases by increasing
Remark 10.Since the value of the
5 Numerical Results
In this section, we present the numerical results of hybrid RF/VLC systems. Here, the theoretical results of the derived lower bound of the SOP and the probability of SPSC are verified by using Monte-Carlo simulation, which is performed by generating
5.1 Results When VLC Link Is Eavesdropped Upon
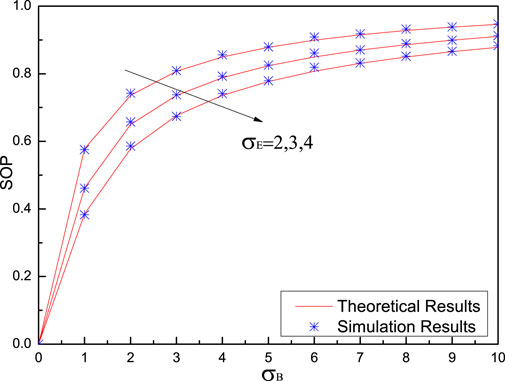
Figure 5 shows the SOP versus Bob’s noise standard deviation
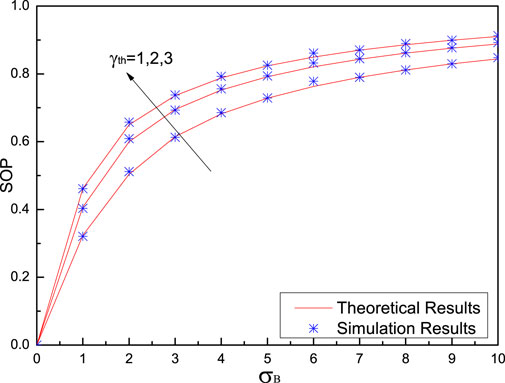
Figure 6 shows the SOP versus Bob’s noise standard deviation
From Figure 5 and Figure 6, it can be clearly observed that simulation results are in close agreement with the theoretical results, which validates our theoretical analysis of SOP as correct.
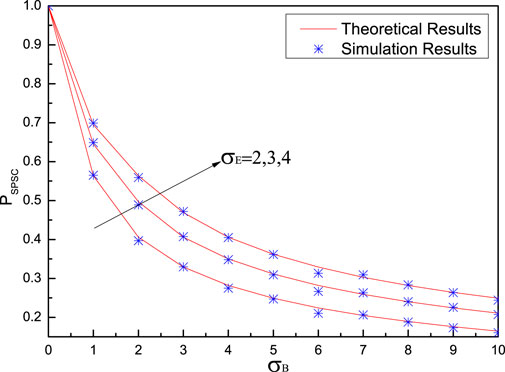
Figure 7 shows the probability of SPSC versus Bob’s noise standard deviation
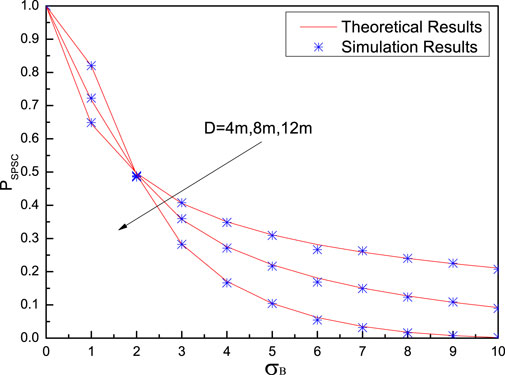
Figure 8 shows the probability of SPSC versus Bob’s noise standard deviation
Moreover, it can be found from Figure 7 and Figure 8 that all theoretical results match simulation results very well, which indicates the correctness of the theoretical analysis.
5.2 Results When RF Link Is Eavesdropped Upon
Figure 9 shows SOP versus the distance between nodes Alice and relay
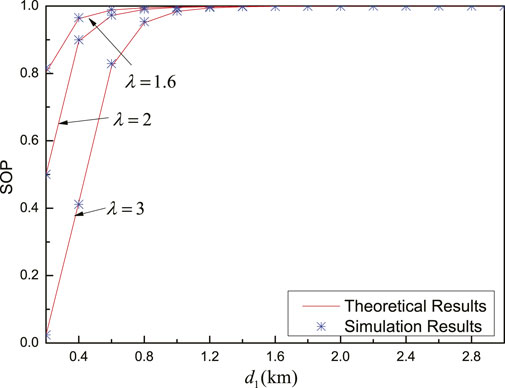
FIGURE 9. SOP versus
Figure 10 shows the SOP versus the distance between nodes Alice and relay
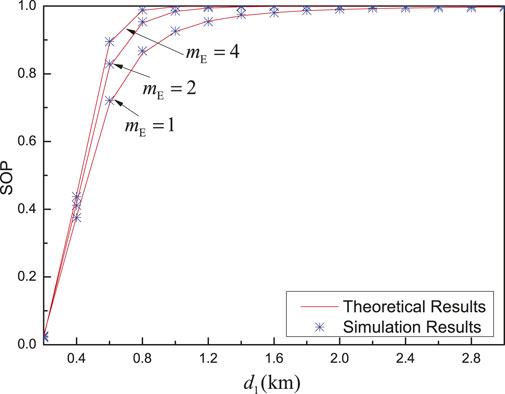
FIGURE 10. SOP versus
From Figure 9 and Figure 10, it should be emphasized that the performance gap between theoretical results and simulation results is small, which verifies the accuracy of the derived expression, which indicates that the scaling for the lower bound of SOP is reasonable.
Figure 11 shows the probability of SPSC versus the distance between nodes Alice and relay
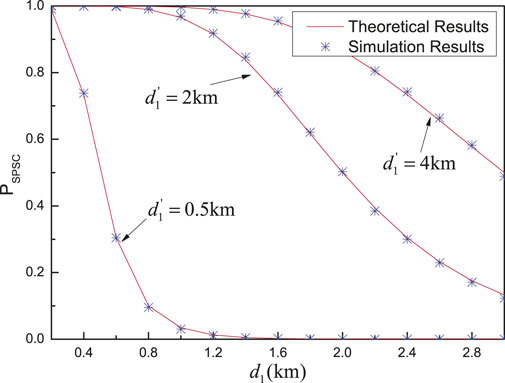
FIGURE 11.
Figure 12 shows the probability of SPSC versus the distance between nodes Alice and relay
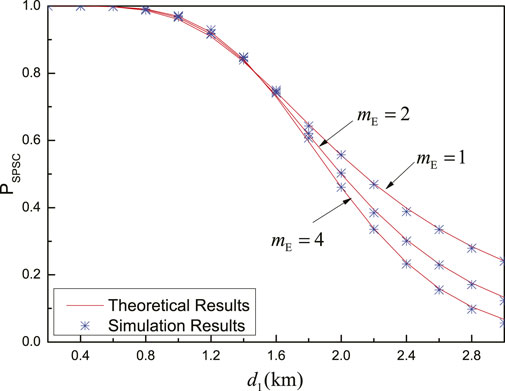
FIGURE 12.
From Figure 11 and Figure 12, all theoretical results of the probability of the SPSC match the simulation results very well, which verifies the accuracy of the derived theoretical expression of the probability of the SPSC. Therefore, the derived expression can be used directly to evaluate the system performance with time-intensive simulations.
5.3 Comparisons for Systems With and Without Eavesdroppers
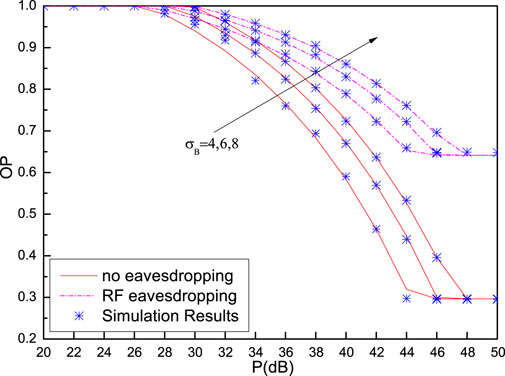
Figure 13 depicts OP performance for systems with and without an RF eavesdropper when ξ = 0.2 and
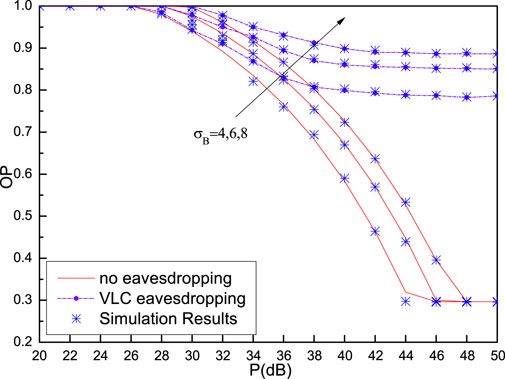
Figure 14 illustrates the OP performance for systems with and without a VLC eavesdropper when ξ = 0.2 and
6 Conclusion
In this article, we have studied the performance of a hybrid RF/VLC DF-based relaying network, in which two scenarios are taken into account: in one scenario, the VLC link is wiretapped, and in the other scenario, the RF link is wiretapped. The major conclusions of the study are given as follows:
1. We assume that the RF link experiences Nakagami-m fading and has path loss, and the non-negative and average optical intensity constraint in the VLC link is considered. The closed-form expressions of the lower bound of SOP and the probability of SPSC are derived, respectively. Numerical results show that theoretical results match simulation results well.
2. When the VLC link is eavesdropped upon, Bob’s (or Eve’s) noise standard deviation
3. If the RF link is eavesdropped upon, we can conclude that with the increase in
4. The derived theoretical expressions in this study will enable communication system designers to quickly and accurately evaluate PLS performance of the hybrid RF/VLC system without time-intensive and laborious Monte-Carlo simulations.
In this study, the secrecy performance of the hybrid RF/indoor VLC system is analyzed. In future work, we will establish the channel model for outdoor VLC and continue to study the secrecy performance of the hybrid RF/outdoor VLC system. Moreover, we will also explore some secrecy performance improvement schemes of the hybrid system.
Data Availability Statement
The original contributions presented in the study are included in the article/Supplementary Material; further inquiries can be directed to the corresponding authors.
Author Contributions
JW and QW designed the research. JW, QW, and JL contributed with data acquisition, analysis, and discussion of results. BZ contributed to the data analysis. JL wrote the manuscript with input from all other authors.
Funding
This work is supported by the National Nature Science Foundation of China (61701254 and 11604133), the Science and Technology Plan of Youth Innovation Team for Universities of Shandong Province (2019KJJ019), the Introduction and Cultivation Plan of Youth Innovation Talents for Universities of Shandong Province, the Fund of the Shandong Key Laboratory of Optical Communication Science and Technology in Liaocheng University (SDOC201901), and the Open Project of Shanghai Key Laboratory of Trustworthy Computing.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Footnotes
1Note that the instantaneous SC in reference [18] is defined as the difference of channel capacities between the Alice–relay–Bob channel and the Alice–relay–Eve channel. Different from reference [18], the instantaneous SC in our study is defined as the minimum SC of the two hops, which is similar to that in reference [17].
2The orange rectangle in Figure 2 is determined by JB and JE, and the red straight line represents
3Similarly to Figure 2, the orange rectangle in Figure 3 is also determined by JB and JE, and the red straight line represents JB = JE. The integral region is also the yellow enclosed area enclosed by the red straight line and the orange rectangle in Figure 3. The four cases in Figure 3 depend on the slope 1 of the line and the ratio of JB and JE. According to mathematical knowledge, the value of Pr {JB > JE} is actually equal to the double integral on the integral region, and the calculation of the double integral is realized by the repeated integral.
References
1. Yang Z, Chen M, Wong KK, Poor HV, Cui S. Federated Learning for 6G: Applications, Challenges, and Opportunities. arXiv preprint arXiv:2101.01338 (2021).
2. Wang J-Y, Yang Z, Wang Y, Chen M. On the Performance of Spatial Modulation Based Optical Wireless Communications. IEEE Photon Technol Lett (2016) 28:1. doi:10.1109/LPT.2016.2585502
3. Tabassum H, Hossain E. Coverage and Rate Analysis for Co-existing RF/VLC Downlink Cellular Networks. IEEE Trans Wireless Commun (2018) 17:2588–601. doi:10.1109/TWC.2018.2799204
4. Rakia T, Yang H-C, Gebali F, Alouini M-S. Optimal Design of Dual-Hop VLC/RF Communication System with Energy Harvesting. IEEE Commun Lett (2016) 20:1979–82. doi:10.1109/LCOMM.2016.2595561
5. Kashef M, Ismail M, Abdallah M, Qaraqe KA, Serpedin E. Energy Efficient Resource Allocation for Mixed RF/VLC Heterogeneous Wireless Networks. IEEE J Select Areas Commun (2016) 34:883–93. doi:10.1109/JSAC.2016.2544618
6. Hammouda M, Akin S, Vegni AM, Haas H, Peissig J. Link Selection in Hybrid RF/VLC Systems under Statistical Queueing Constraints. IEEE Trans Wireless Commun (2018) 17:2738–54. doi:10.1109/TWC.2018.2802937
7. Kong J, Ismail M, Serpedin E, Qaraqe KA. Energy Efficient Optimization of Base Station Intensities for Hybrid RF/VLC Networks. IEEE Trans Wireless Commun (2019) 18:4171–83. doi:10.1109/TWC.2019.2922611
8. Hsiao Y-C, Wu Y-C, Lin C. Energy-efficient Beamforming Design for MU-MISO Mixed RF/VLC Heterogeneous Wireless Networks. IEEE Trans Signal Process (2019) 67:3770–84. doi:10.1109/TSP.2019.2920612
9. Marzban MF, Kashef M, Abdallah M, Khairy M. Beamforming and Power Allocation for Physical-Layer Security in Hybrid RF/VLC Wireless Networks. In: 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC). Piscataway, New Jersey: IEEE (2017). p. 258–63.
10. Rakia T, Yang HC, Gebali F, Alouini MS. Dual-hop VLC/RF Transmission System with Energy Harvesting Relay under Delay Constraint. In: 2016 IEEE Globecom Workshops (GC Wkshps). Piscataway, New Jersey: IEEE (2016). p. 1–6.
11. Al-Khori J, Nauryzbayev G, Abdallah MM, Hamdi M. Secrecy Performance of Decode-And-Forward Based Hybrid RF/VLC Relaying Systems. IEEE Access (2019) 7:10844–56. doi:10.1109/ACCESS.2019.2891678
12. Kumar A, Garg P, Gupta A. PLS Analysis in an Indoor Heterogeneous VLC/RF Network Based on Known and Unknown CSI. IEEE Syst J (2021) 15:68–76. doi:10.1109/JSYST.2020.2964033
13. Wang J-Y, Qiu Y, Lin S-H, Wang J-B, Wang Q, Zhang B. Performance Analysis and Improvement for Secure VLC with SLIPT and Random Terminals. IEEE Access (2020) 8:73645–58. doi:10.1109/ACCESS.2020.2988470
14. Zedini E, Soury H, Alouini M-S. On the Performance Analysis of Dual-Hop Mixed FSO/RF Systems. IEEE Trans Wireless Commun (2016) 15:3679–89. doi:10.1109/TWC.2016.2524685
15. Yang L, Hasna MO, Gao X. Performance of Mixed RF/FSO with Variable Gain over Generalized Atmospheric Turbulence Channels. IEEE J Select Areas Commun (2015) 33:1913–24. doi:10.1109/JSAC.2015.2432471
16. Soleimani-Nasab E, Uysal M. Generalized Performance Analysis of Mixed RF/FSO Cooperative Systems. IEEE Trans Wireless Commun (2016) 15:714–27. doi:10.1109/TWC.2015.2477400
17. Pan X, Ran H, Pan G, Xie Y, Zhang J. On Secrecy Analysis of DF Based Dual Hop Mixed RF-FSO Systems. IEEE Access (2019) 7:66725–30. doi:10.1109/ACCESS.2019.2914227
18. Lei H, Dai Z, Park K-H, Lei W, Pan G, Alouini M-S. Secrecy Outage Analysis of Mixed RF-FSO Downlink SWIPT Systems. IEEE Trans Commun (2018) 66:6384–95. doi:10.1109/TCOMM.2018.2865944
19. Lei H, Dai Z, Ansari IS, Park K-H, Pan G, Alouini M-S. On Secrecy Performance of Mixed RF-FSO Systems. IEEE Photon J. (2017) 9:1–14. doi:10.1109/JPHOT.2017.2723422
20. Lei H, Luo H, Park K-H, Ren Z, Pan G, Alouini M-S. Secrecy Outage Analysis of Mixed RF-FSO Systems with Channel Imperfection. IEEE Photon J. (2018) 10:1–13. doi:10.1109/JPHOT.2018.2835562
21. Wang J-B, Hu Q-S, Wang J, Chen M, Wang J-Y. Tight Bounds on Channel Capacity for Dimmable Visible Light Communications. J Lightwave Technol (2013) 31:3771–9. doi:10.1109/JLT.2013.2286088
22. Simon MK, Alouini MS. Digital Communication over Fading Channels. 2nd ed., Vol. 95. Hoboken, New Jersey: John Wiley & Sons (2005).
23. Jeffrey A, Zwillinger D. Table of Integrals, Series, and Products. Amsterdam, Netherlands: Elsevier (2007).
24. Komine T, Nakagawa M. Fundamental Analysis for Visible-Light Communication System Using LED Lights. IEEE Trans Consumer Electron (2004) 50:100–7. doi:10.1109/TCE.2004.1277847
25. Yin L, Haas H. Physical-layer Security in Multiuser Visible Light Communication Networks. IEEE J Select Areas Commun (2018) 36:162–74. doi:10.1109/JSAC.2017.2774429
26. Wang J-Y, Liu C, Wang J-B, Wu Y, Lin M, Cheng J. Physical-layer Security for Indoor Visible Light Communications: Secrecy Capacity Analysis. IEEE Trans Commun (2018) 66:6423–36. doi:10.1109/TCOMM.2018.2859943
Keywords: visible light communications, radio frequency communications, secrecy outage probability, probability of strictly positive secrecy capacity, hybrid RF/VLC systems
Citation: Liu J, Wang J, Zhang B and Wang Q (2021) Secrecy Performance Analysis of Hybrid RF/VLC Dual-Hop Relaying Systems. Front. Phys. 9:683479. doi: 10.3389/fphy.2021.683479
Received: 21 March 2021; Accepted: 28 June 2021;
Published: 30 July 2021.
Edited by:
Haohai Yu, Shandong University, ChinaReviewed by:
Qiong Wu, Jiangnan University, ChinaShuai Ma, China University of Mining and Technology, China
Zhaohui Yang, King’s College London, United Kingdom
Copyright © 2021 Liu, Wang, Zhang and Wang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Jinyuan Wang, anl3YW5nQG5qdXB0LmVkdS5jbg==; Qinglin Wang, d2FuZ3FpbmdsaW5AbGN1LmVkdS5jbg==
 Jiaoli Liu
Jiaoli Liu Jinyuan Wang
Jinyuan Wang Bingyuan Zhang1
Bingyuan Zhang1 Qinglin Wang
Qinglin Wang