- 1Information Security Center, State Key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, Beijing, China
- 2Information Security Center, School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing, China
Semi-quantum secret sharing is an important research issue in quantum cryptography. In this paper, we propose a (t, n) threshold semi-quantum secret sharing protocol, which combines the practicality of semi-quantum secret sharing protocols and the flexibility of (t, n) threshold quantum secret sharing protocols. Participants prepare and transmit single particles in a circular way, and then any t out of n participants can recover the secret according to Shamir’s secret sharing scheme. As quantum resources, single particles are easy to prepare. Furthermore, classical participants only need to possess the capability to prepare and insert particles. The security analysis shows our protocol has security against most attacks. Except decoy particles, all particles are useful to carry the secret message, so the efficiency of the proposed protocol can achieve 100%.
1 Introduction
Secret sharing is an important branch of modern cryptography. The concept of secret sharing is that the secret holder divides his secret into several pieces and each participant can obtain a piece from the holder. The threshold number of participants can recover the secret in collaboration with others.
The first classical secret sharing (CSS) protocol [1] was proposed by Shamir in 1979. However, if an eavesdropper, Eve, controls the communication channel, she can easily obtain the secret holder’s, Alice’s, secret [2]. Unfortunately, the physical properties of quantum mechanics mean that eavesdropping can be detected easily because eavesdropping may disturb quantum information, which induces errors. Therefore, quantum secret sharing (QSS) emerged based on security additional requirements. In 1999, Hillery et al. proposed the first QSS protocol [3]. Authors employed the three-particle and four-particle entangled Greenberger-Horne-Zeilinger (GHZ) state to share a secret message in their protocol. In 2003, Guo et al. proposed a more efficient QSS protocol [4] that only used product states. In 2008, Wang et al. put forward a QSS protocol [5] with higher efficiency and security based on single photons. After that, a huge number of QSS protocols [6–15] were proposed.
The above QSS protocols require all participants to possess full quantum capabilities, but not all participants are equipped with complete quantum devices. Fortunately, the concept of semi-quantum secret sharing (SQSS) was proposed. In a semi-quantum environment, some participants have limited quantum capabilities. They can cooperate with the participants with full quantum capabilities to complete tasks of secret distribution and reconstruction in SQSS protocols. In 2010, Li et al. proposed the first semi-quantum secret sharing protocol [16]. In the protocol, they used entangled GHZ-type states to share a secret message. In 2015, Xie et al. presented an efficient SQSS protocol [17] that can share a specific secret. In 2018, an SQSS protocol with limited resources was designed by Li et al. [18], which was more efficient compared with previous protocols. In 2021, Yin et al. proposed an SQSS protocol [19] based on GHZ-type states. The protocol adopted identity authentication to verify the identification of participants in communication. In recent years, more SQSS protocols [20, 21–27] were proposed.
However, all the above SQSS protocols are (n, n) threshold protocols. That is to say, the secret sharing tasks cannot be completed when there is someone unable to participate. So, we propose a (t, n) threshold SQSS protocol based on Shamir’s secret sharing scheme, in which any t out of n participants with limited quantum capabilities can recover the secret. All participants only use single particles, which are easier to prepare than other quantum resources. In our protocol, the initial particles prepared by Alice are sent to the first participant. Every participant inserts his particles and sends the new sequence to the next one until Alice receives the final sequence from the last participant. The sequence composed of particles is transmitted in a circular way. Due to the circular transmission mode, participants play the different roles. Furthermore, classical participants in our protocol are released from many quantum operations and they are only required to possess the capability to prepare and insert particles. Moreover, the qubit efficiency of our protocol can achieve 100% because all particles are used to carry the secret message except for decoy particles. As mentioned above, a flexible and efficient SQSS protocol is proposed in this paper. In addition, the security of our protocol can be proved under intercept-resend attack, measure-resend attack, entangle-measure attack, and collusion attack.
The rest of this paper is organized as follows. In Section 2, we present some preliminaries about the setting of SQSS and Shamir’s secret sharing. Then, in Section 3, we describe a (t, n) threshold SQSS protocol. An example of the proposed (t, n) threshold SQSS protocol is given in Section 4. In Section 5, we analyze the security of our protocol and give a comparison with some SQSS protocols. Finally, a conclusion is provided in Section 6.
2 Preliminaries
Here, to make our protocol easier to understand, we will briefly introduce some preliminaries about the setting of SQSS and Shamir’s secret sharing.
2.1 The setting of SQSS
In SQSS protocols, there are participants restricted to using only the quantum states in the fixed computational basis
2.2 Shamir’s secret sharing
Shamir [1] proposed a (t, n) threshold scheme based on polynomial interpolation in 1979. According to the property of polynomial interpolation, this technique enables the construction of secret sharing schemes that can function even when fewer than n participants want to reconstruct the secret. Therefore, Shamir’s scheme has been widely used in the field of quantum cryptography, such as quantum secret sharing [28–30] and quantum key distribution [31].
Given that there is a secret holder Alice and n participants
In the secret sharing phase, the secret holder Alice selects a polynomial of t–1 degree:
Here, S is Alice’s secret, t is the lower limit of the number of participants who can reconstruct Alice’s secret S, and
In secret reconstruction phase, t participants use the Lagrange interpolation formula and their shares to reconstruct the secret. The Lagrange interpolation formula is as follows:
Participants can calculate the polynomial under the condition that
3 A (t, n) threshold SQSS protocol
In this section, we propose a (t, n) threshold SQSS protocol. Assume that the secret holder Alice wants to share her secret among n participants
Step 1. Alice picks a random polynomial:
where S is Alice’s secret and
Step 2. Alice randomly chooses an integer xi and computes
Step 3. Alice randomly prepares N particles in one of the states
Step 4. After receiving
Step 5.
Step 6. Alice and
Step 7. After the eavesdropping checks, Alice measures the remaining particles with Z basis. According to the measurement results, Alice can obtain the private key
Step 8. Because all participants announce where they insert their particles in Step 6,
4 An example
To give a clear explanation of our protocol, we will take a (3, 4) threshold protocol as an example in the following. Suppose the secret holder Alice wants to share her secret 00001 with the participants. Obviously,
4.1 Alice’s preparation
Alice picks a polynomial
Alice randomly prepares 5 decoy particles in one of the states
4.2 Secret sharing
Alice sends
For eavesdropping detection, participants announce where they insert their particles. Alice can obtain the positions of her particles. She measures these particles with proper measurement basis and checks the error rate. For example, if Alice prepares
After eavesdropping detection, Alice measures the remaining particles with Z basis. Subsequently, she obtains
All participants declare where they insert their particles in Step 6, so
Finally,
4.3 Secret recovery
Suppose three participants,
In this way, they complete a (3,4) threshold SQSS protocol and recover the secret shared by Alice.
5 Security analysis and comparison
In this section, we will analyze the security of our protocol and further compare our protocol with some SQSS protocols. An inside participant has a more powerful ability to eavesdrop on an SQSS protocol than an outside attacker. If a protocol can resist the attack from an inside participant, it is also secure for an outside attacker. Thus, in the following security analysis, we focus on the attack from an inside participant. The dishonest participant will try to steal Alice’s secret by using the following attack strategies.
5.1 Measure-resend attack
Suppose that
5.2 Intercept-resend attack
To obtain Alice’s shared integers, the malicious participant
5.3 Entangle-measure attack
Suppose that
Here,
We can infer
Here, 0 denotes a column zero vector.
Then, the deduced results are as follows:
From Eq. 12, we can create Eq. 13:
In this way, the final results can be deduced as the following, Eq. 14:
So,
5.4 Collusion attack
Two or more dishonest participants may try to steal other participants’ secret shadows by stealing their private keys. First, we assume that
Subsequently, we will discuss the situation where
In this section, we prove that the proposed protocol is secure enough to resist measure-resend attack, intercept-resend attack, entangle-measure attack, and collusion attack.
5.5 Comparison
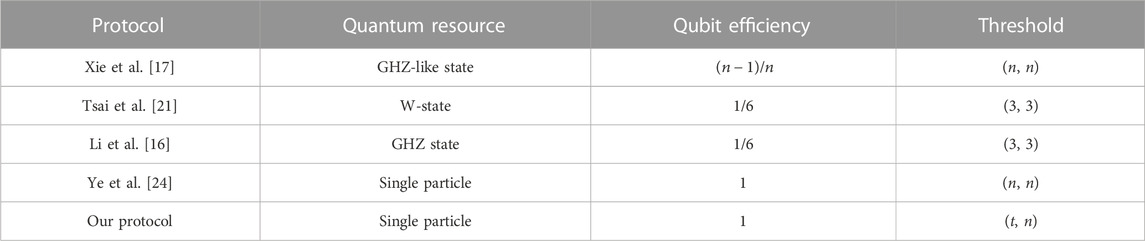
Here, we will give a comparison with some SQSS protocols. The comparison results are displayed in Table 1. The qubit efficiency is defined as
In terms of the threshold structure, our protocol is (t, n) threshold protocol. That is, the proposed protocol is more flexible than the (n, n) threshold protocols in Refs. [17, 21, 16, 24]. For quantum resources, all participants in our protocol use single particles, which are easier to prepare than entangled states used in the protocols in Refs. [17, 21, 16]. Furthermore, in our protocol, except for the decoy particles, all particles prepared are used to carry the secret shadows in principle. Thus, the qubit efficiency of our protocol can achieve 100%. Therefore, our protocol has better qubit efficiency than the protocols in Refs. [17, 21, 16]. In summary, our protocol is efficient, and it is more flexible than these protocols.
6 Conclusion
In this paper, we have proposed a (t, n) threshold SQSS protocol. Different from previous SQSS protocols, any t out of n classical participants can recover the secret in our protocol. Next, as quantum resources, single particles used in our protocol are easy to prepare. Moreover, except decoy particles, all particles are useful to transmit secret shadows, so the qubit efficiency of our protocol can achieve 100%. In addition, for classical participants, only the capability to prepare and insert single particles is required in our protocol. On the whole, the protocol proposed in this paper is flexible and efficient.
Data availability statement
The original contributions presented in the study are included in the article/Supplementary Material, further inquiries can be directed to the corresponding author.
Author contributions
All authors listed have made a substantial and intellectual contribution to this work and approved it for publication.
Funding
National Science Foundation of China (Grant No. 62272051) Foundation of Guizhou Provincial Key Laboratory of Public Big Data (Grant No. 2019BDKFJJ014). Project supported by the National Key R&D Program of China (Grant No. 2020YFB1805405), the 111 Project (Grant No. B21049), the National Science Foundation of China (Grant No. 62272051), the Foundation of Guizhou Provincial Key Laboratory of Public Big Data (Grant No. 2019BDKFJJ014), and the Fundamental Research Funds for the Central Universities, China (Grant Nos. 2020RC38, 2019XD-A02).
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
2. Yin A, Wang Z, Fu F. A novel semi-quantum secret sharing scheme based on Bell states. Mod Phys Lett B (2017) 31(13):1750150. doi:10.1142/S0217984917501500
3. Hillery M, Bužek M, Berthiaume A. Quantum secret sharing. Phys Rev A (1999) 59(3):1829–34. doi:10.1103/PhysRevA.59.1829
4. Guo GP, Guo GC. Quantum secret sharing without entanglement. Phys Lett A (2003) 310(4):247–51. doi:10.1016/S0375-9601(03)00074-4
5. Wang T, Wen Q, Chen X, Guo F, Zhu F. An efficient and secure multiparty quantum secret sharing scheme based on single photons. Opt Commun (2008) 281(24):6130–4. doi:10.1016/j.optcom.2008.09.026
6. Karimipour V, Bahraminasab A, Bagherinezhad S. Entanglement swapping of generalized cat states and secret sharing. Phys Rev A (2002) 65(4):042320. doi:10.1103/PhysRevA.65.042320
7. Chau HF. Practical scheme to share a secret key through a quantum channel with a 27.6% bit error rate. Phys Rev A (2002) 66(6):060302. doi:10.1103/PhysRevA.66.060302
8. Li Y, Zhang K, Peng K. Multiparty secret sharing of quantum information based on entanglement swapping. Phys Lett A (2004) 324(5-6):420–4. doi:10.1016/j.physleta.2004.03.034
9. Wang HF, Ji X, Zhang S. Improving the security of multiparty quantum secret splitting and quantum state sharing. Phys Lett A (2006) 358(1):11–4. doi:10.1016/j.physleta.2006.04.110
10. Lin S, Wen QY, Gao F, Zhu FC. Improving the security of multiparty quantum secret sharing based on the improved Boström–Felbinger protocol. Opt Commun (2008) 281(17):4553–4. doi:10.1016/j.optcom.2008.05.026
11. Gao G. Improvement of efficient multiparty quantum secret sharing based on bell states and continuous variable operations. Int J Theor Phys (2014) 53(7):2231–5. doi:10.1007/s10773-014-2023-y
12. Wang J, Zhang S, Zhang Q, Tang CJ. Semiquantum key distribution using entangled states. Chin Phys Lett (2011) 28(10):100301. doi:10.1088/0256-307X/28/10/100301
13. Gao G. Secure multiparty quantum secret sharing with the collective eavesdropping-check character. Quan Inf Process (2013) 12(1):55–68. doi:10.1007/s11128-011-0351-x
14. Rahaman R, Parker MG. Quantum scheme for secret sharing based on local distinguishability. Phys Rev A (2015) 91(2):022330. doi:10.1103/PhysRevA.91.022330
15. Gao G, Wang Y, Wang D. Multiparty semiquantum secret sharing based on rearranging orders of qubits. Mod Phys Lett B (2016) 30(10):1650130. doi:10.1142/S021798491650130X
16. Li Q, Chan WH, Long DY. Semiquantum secret sharing using entangled states. Phys Rev A (2010) 82(2):022303. doi:10.1103/PhysRevA.82.022303
17. Xie C, Li L, Qiu D. A novel semi-quantum secret sharing scheme of specific bits. Int J Theor Phys (2015) 54(10):3819–24. doi:10.1007/s10773-015-2622-2
18. Li Z, Li Q, Liu C, Peng Y, Chan WH. Limited resource semiquantum secret sharing. Quan Inf Process (2018) 17(10):285–11. doi:10.1007/s11128-018-2058-8
19. Yin A, Chen T. Authenticated semi-quantum secret sharing based on GHZ-type states. Int J Theor Phys (2021) 60(1):265–73. doi:10.1007/s10773-020-04688-7
20. Hu WW, Zhou RG, Luo J. Semi-quantum secret sharing in high-dimensional quantum system using product states. Chin J Phys (2022) 77:1701–12. doi:10.1016/j.cjph.2022.03.031
21. Tsai CW, Yang CW, Lee NY. Semi-quantum secret sharing protocol using W-state. Mod Phys Lett A (2019) 34(27):1950213. doi:10.1142/S0217732319502134
22. Cao G, Chen C, Jiang M. A scalable and flexible multi-user semi-quantum secret sharing. In: Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering; November 2018; Beijing China (2018). p. 28–32. doi:10.1145/3291842.3291857
23. Yin AH, Tong Y. A novel semi-quantum secret sharing scheme using entangled states. Mod Phys Lett B (2018) 32(22):1850256. doi:10.1142/S0217984918502561
24. Ye CQ, Ye TY. Circular semi-quantum secret sharing using single particles. Commun Theor Phys (2018) 70(6):661. doi:10.1088/0253-6102/70/6/661
25. Li XY, Chang Y, Zhang SB. Multi-party semi-quantum secret sharing protocol based on Bell states. In: Proceedings of the International Conference on Artificial Intelligence and Security; November 2020; Cham (2020). p. 280–8. doi:10.1007/978-3-030-57881-7_25
26. Tian Y, Li J, Chen XB, Ye CQ, Li HJ. An efficient semi-quantum secret sharing protocol of specific bits. Quan Inf Process (2021) 20(6):217–1. doi:10.1007/s11128-021-03157-2
27. Tian Y, Li J, Yuan KG, Li HJ, Chen XB. An efficient semi-quantum key distribution protocol based on EPR and single-particle hybridization. QUANTUM INFORMATION COMPUTATION (2021) 21(7-8):563–76. doi:10.26421/QIC21.7-8-3
28. Yang YG, Wen QY. Threshold quantum secure direct communication without entanglement. Sci China Ser G: Phys Mech Astron (2008) 51(2):176–83. doi:10.1007/s11433-008-0028-3
29. Qin HW, Dai YW. An efficient (t, n) threshold quantum secret sharing without entanglement. Mod Phys Lett B (2016) 30(12):1650138. doi:10.1142/S0217984916501384
30. Lu CB, Miao FY, Meng KJ, Yu Y. Threshold quantum secret sharing based on single qubit. Quan Inf Process (2018) 17:64–13. doi:10.1007/s11128-017-1793-6
Keywords: semi-quantum secret sharing, (t, n) threshold, single particles, efficiency, circular transmission
Citation: Zhou Z, Wang Y, Dou Z, Li J, Chen X and Li L (2023) A (t, n) threshold protocol of semi-quantum secret sharing based on single particles. Front. Phys. 11:1225059. doi: 10.3389/fphy.2023.1225059
Received: 18 May 2023; Accepted: 03 July 2023;
Published: 21 July 2023.
Edited by:
Nanrun Zhou, Shanghai University of Engineering Sciences, ChinaReviewed by:
Qin Li, Xiangtan University, ChinaDan Li, Nanjing University of Aeronautics and Astronautics, China
Copyright © 2023 Zhou, Wang, Dou, Li, Chen and Li. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Zhao Dou, ZG91QGJ1cHQuZWR1LmNu
 Ziyi Zhou
Ziyi Zhou Yifei Wang1
Yifei Wang1 Zhao Dou
Zhao Dou Jian Li
Jian Li Lixiang Li
Lixiang Li