- 1Department of Information Engineering, Ningxia Communications Technical College, Yinchuan, China
- 2School of Computer, Central China Normal University, Wuhan, China
As an important component of the smart grid, Vehicle-to-Grid (V2G) can achieve bidirectional exchange of data and power flow between electric vehicles and smart grid, and is an effective promoter for grid storage and decarbonization. However, when electric vehicles are connected to the grid, the V2G network involves a large amount of privacy data exchange and sensitive charging and discharging transactions. Once these data are leaked, the privacy and security of users will be threatened. The existing authentication protocols in V2G network lack sufficient protection for vehicle user identity privacy and cannot provide user identity anonymity. Therefore, this article proposes an anonymous and privacy-preserving authentication protocol tailored for V2G environments, aiming to protect user identity privacy. The protocol integrates Elliptic Curve Cryptography (ECC) and Physical Unclonable Function (PUF) to achieve mutual authentication between EVs and the grid. It ensures the anonymity of participants through the use of temporary identity values and secures the session key.T he security and efficiency of the protocol are verified through Scyther simulation and heuristic analysis. Compared with other protocols, the protocol proposed in this article not only meets the security requirements in smart grid environment, but also reduces costs, demonstrating significant security and overhead advantages. This work contributes to building a more trustworthy, scalable and privacy-conscious V2G network, thereby supporting sustainable energy development and smart grid security.
1 Introduction
As human society continues to advance rapidly, the significance of energy and environmental challenges has grown increasingly pronounced. To address these issues, the smart grid has emerged as a focal point of global research. This new generation of power grid aims to establish an energy system that is green, low-carbon, safe, and reliable, thereby mitigating the impact of energy consumption on the environment [1–3]. Unlike traditional power grids, smart grid has advantages such as safety, flexibility and cleanliness. They can achieve bidirectional communication of power flow and information flow between the grid and users, improve the traditional one-way power service mode, and provide people with better quality services. At the same time, smart grid has fully implemented an intelligent and lean power grid operation and maintenance mode. This greatly enhances the ability of the power grid to respond to sudden events and emergency failures and optimizes resource allocation capabilities. In addition, the combination of smart grid and emerging energy storage technologies enables the grid connected operation of renewable energy, making renewable energy a more suitable energy supply mode for human social development [4–7]. However, the integration of renewable energy into power generation can introduce instability and volatility, potentially affecting grid reliability [8]. To mitigate these fluctuations, auxiliary systems are necessary. Electric vehicle (EV), serving as capable energy storage units, offer a solution to stabilize the incorporation of clean energy into the grid. To facilitate mutual benefits between EV and the grid, energy exchange and communication must occur through a dedicated network. Consequently, the concept of the Vehicle-to-Grid (V2G) network has been proposed [9–11].
V2G integrates EV as mobile energy storage devices with smart grid to achieve a more sustainable, efficient and safe energy system. The significance of V2G technology lies in its ability to achieve bidirectional flow and management of energy. On the one hand, when the load on the power grid is low, the grid can use the excess electricity to charge the batteries of electric vehicles, avoiding resource waste. On the other hand, when the load on the power grid is high, electric vehicles transfer the energy stored in the battery to the grid, helping to alleviate the load pressure on the grid and improve its flexibility and stability [12]. Meanwhile, users can use electric vehicles as reliable energy storage devices through V2G technology to generate revenue. This new source of income can encourage more people to purchase electric vehicles, thereby promoting the popularization of EV. Therefore, V2G presents enormous practical efficiency and has broad application prospects.
V2G plays a crucial role in the development of smart grid by facilitating data and power exchange. However, bidirectional communication and power flow in V2G environments involve a large amount of private data, which is vulnerable to malicious attacks and can cause property damage [13]. And due to the high-speed mobility of EV, privacy breaches in V2G are more severe than in other parts of smart grid. Overall, the following security threats still exist in V2G environments [14]. Firstly, unauthorized adversaries may attempt to disguise themselves as the vehicle owner in order to gain access to the vehicle and engage in charging/discharging activities without the owner’s knowledge, resulting in wastage of resources. Secondly, the V2G environment involves the exchange of user personal information and vehicle data, such as energy transmission, driving routes, charging/discharging habits, etc. When adversaries steal this information, they will make guesses about users’ consumption levels, company locations, home addresses, lifestyle habits, and other private information, posing a great threat to users. In addition, in V2G environments, users frequently perform charging/discharging transactions, so it is necessary to ensure the data integrity. Finally, due to the V2G environment being exposed to public environments, the entire communication process will also be subjected to more and more complex attacks, such as replay attacks, physical attacks, etc. Identity authentication is a security mechanism used to confirm the legitimacy and authenticity of an entity’s identity [15–17]. In theV2G environment, the importance of identity authentication is particularly prominent. Through identity authentication, unauthorized access and tampering can be prevented, ensuring the security of information and systems. Existing V2G authentication protocols continue to suffer from notable limitations, particularly in terms of privacy and security. Many lack robust mechanisms to ensure user identity anonymity, leaving vehicles vulnerable to tracking through identifiable information or communication behavior. Additionally, inadequate privacy protection measures expose users to the risk of having their locations and movement patterns analyzed by adversaries. Moreover, these protocols often fail to provide comprehensive defenses against a range of security threats, such as replay attacks, man-in-the-middle attacks, and identity forgery, reflecting an incomplete set of security guarantees. To address these issues, this paper proposes a lightweight anonymous authentication protocol that combines Elliptic Curve Cryptography (ECC) and Physically Unclonable Functions (PUFs). The proposed scheme not only enables mutual authentication and session key agreement between electric vehicles and charging stations, but also significantly enhances both security properties and performance. By leveraging PUF technology, storage and computational costs are reduced, and the use of ECC decreases key length and computational complexity, thereby greatly minimizing communication and computational overhead—making the scheme suitable for resource-constrained V2G devices. The main contributions of this article are as follows:
(1) Based on elliptic curve cryptography and physically unclonable function technology, this paper designs an anonymous authentication protocol. This protocol enables electric vehicles and charging stations to verify their identities and successfully establish session keys for future communication. The protocol ensures the security of session keys by combining temporary secret values with long-term secret values. In order to protect the anonymity of participants, entities send temporary identity values for transmission to prevent attackers from locating them.
(2) This article uses two security analysis methods to analyze the design protocol. By using Scyther tool to simulate the protocol process, it has been proven that the protocol can achieve bidirectional authentication and ensure the security of session keys. The heuristic analysis results indicate that the protocol can have good forward security and anonymity, and is not easily susceptible to replay attacks, etc.
(3) Compared with other protocols, the security comparison results show that the protocol can meet all security requirements in smart grid environments, while other protocols have security vulnerabilities. The performance analysis results indicate that the protocol reduces costs while achieving the same level of security. From this, it can be concluded that the protocol has advantages in terms of security and overhead.
The organization of this paper is as follows: In Section 2, we review pertinent literature. Section 3 presents the models. Section 4 provides detailed information on the design. Section 5 conducts a security analysis. Section 6 reports the performance and Section 7 concludes the paper.
2 Related work
V2G refers to the technology of bidirectional interaction, allowing electric vehicles to not only serve as terminal devices for consuming electrical energy, but also as energy storage and injection devices, providing support for the power grid. However, V2G security and privacy issues have also attracted widespread attention from scholars [13,14]. In order to ensure the reliability and security of V2G, effective security and privacy protection measures need to be taken. In the communication process, authentication protocols are a key component to ensure secure communication.
[18] used an anonymous mechanism to protect the privacy. In this protocol, the central aggregator issues licenses to vehicles using partially blind signatures, establishes communication sessions with the local aggregator using licenses and pseudo-random identities, and regularly sends status reports. The privacy of electric vehicles is guaranteed, but if any car cheats, the central aggregator will disclose its true identity. [19] designed an efficient Privacy Aware Authentication (PAA) scheme and demonstrated its ability to resist various attacks. [20] pointed out that [19] cannot resist forgery attacks from service providers. They proposed a novel PAA scheme based on [19], which uses identity-based signature technology to resist server forgery attacks and protect user identity privacy. [21] designed a lightweight V2G scheme that is secure and protects user privacy. Meanwhile, the protocol generates static pseudonyms through private credentials for electric vehicles, suitable for vehicles with limited resources. However, as the protocol does not provide a password update phase, it cannot achieve perfect forward security and resist asynchronous attacks. [22] proposed a privacy protected blockchain power auction scheme. This protocol uses smart contracts to automatically auction protocols to facilitate transactions, utilizes group signatures to protect the privacy of electric vehicles and charging stations, and trusted institutions can query real identity information in emergency situations. However, due to the use of bilinear pairing to construct random signatures, it imposes an additional computational burden on vehicles. [23] proposed a lightweight authentication framework for V2G (Vehicle-to-Grid) networks. The framework uses PUF responses to establish authentication among electric vehicles, charging stations, and the grid server. However, electric vehicles and charging stations share their real identities over insecure channels, making it impossible for them to remain anonymous within the network. [24] proposed another authentication and key generation protocol for V2G networks using Elliptic Curve Cryptography (ECC), XoR operations, and one-way hash functions. However, the scheme fails to ensure the security of the session key and does not provide user anonymity for electric vehicles and charging stations. [25] designed a lightweight authentication. [26] designed a secure communication protocol. This protocol considers the traceability of EV, but does not take into account forward security. [27] pointed out that the security issues need to be considered when EV play different roles, and proposed an authentication scheme to achieve secure communication. However, this scheme ignores issues such as tracking, revoking, and forward security for malicious EV. [25] introduced a privacy-preserving authentication protocol for V2G networks that employs elliptic curve cryptography and one-way hash functions to achieve mutual authentication among participants. Despite its strengths, the scheme lacks non-traceability and is vulnerable to user impersonation attacks. [13] presented a session key generation and authentication mechanism for a cloud-based V2G environment, utilizing ECC, one-way hashing, and XoR operations. However, their approach falls short in securing the session key when faced with ephemeral secret leakage attacks. [28] proposed an authentication mechanism b, which also requires assigning pseudonyms to EV. [29] proposed a protocol for V2G. Although this scheme can resist various security attacks, EV in this scheme also requires TA to generate pseudonyms for it. [30] designed a new license generation scheme. But the security assumption for LAG is too high. [23] proposed a secure user key exchange identity authentication protocol from the perspective of physical security. During the authentication process, there is no need to store any secret information in the EV and aggregator, but the security assumption for physical devices in the scheme is too high. [31] designed a key negotiation scheme based on elliptic curve cryptography technology. The scheme realizes secure communication between multiple layers of architecture in the smart grid environment. However, this scheme lacks a comprehensive security model and formal security analysis. [27] considered that electric vehicles may interact with the grid as different roles in V2G environments, and designed a scheme based on this requirement. [32] proposed a privacy protection protocol for V2G, which achieves mutual authentication without exposing the user’s true identity, and achieves self-synchronization by updating pseudonyms in the session. [33] pointed out that [32] cannot resist simulated attacks and offline password guessing attacks, and cannot achieve session key security. [34] proposed a privacy protection authentication scheme for V2G communication based on Energy Internet (EI). A new communication model based on EI enables electric vehicles to seamlessly charge or discharge batteries at different charging stations. [35] pointed out that [34] may suffer from desynchronization attacks during the user login phase, and adversaries can select legitimate information on open channels to conduct replay attacks on vehicles. Therefore, they combined fuzzy extractor technology to propose a lightweight security model based on EI communication architecture, allowing vehicles to communicate or charge/discharge at desired service stations and resist various attacks. [36] introduced fog servers to achieve parallel management based on V2G network environment. However, the entire protocol incurs significant computational overhead. Some representative works are shown in Table 1.
3 Preliminaries
3.1 System model
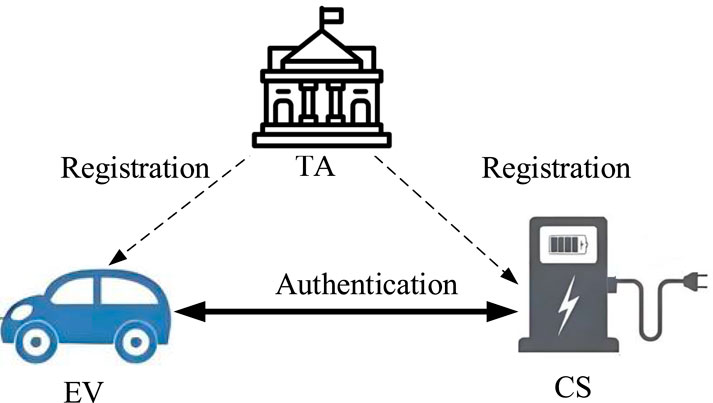
This protocol mainly considers the privacy, security, and anonymity issues of the interaction layer between vehicles and smart grids in V2G networks [13,20–32]. As shown in Figure 1, the system model mainly consists of three components, namely, trusted authority (TA), electric vehicle (EV) and charging station (CS). The specific descriptions of each part are as follows:
(1) Trusted Authority (TA): TA plays a crucial role as a trusted third-party organization, typically analogous to official entities such as power regulatory agencies. Its core responsibilities include the comprehensive initialization of the V2G network system, ensuring the legal registration of all participating entities, and being responsible for publishing and maintaining the security parameter system of the entire system. This step is crucial for building a safe and reliable V2G interaction environment.
(2) Electric Vehicle (EV): Each EV is equipped with a Tamper Resistant Device (TRD) specifically designed to securely store sensitive information and secret keys of the vehicle. During the initialization phase of V2G, EV must register through TA, which verifies their identity information and hardware integrity. EV that has not been registered with TA will be denied access by the system and will not be able to enjoy the various services provided by the V2G, effectively preventing unauthorized access and potential security risks.
(3) Charging Station (CS): As a key component of the smart grid, CS not only undertakes the task of providing electrical energy supply to EVs, but also is responsible for efficient and safe two-way exchange of information and electrical energy with EV. To ensure the legality and security of interactions between entities, CS also needs to complete the registration process with TA during the initialization phase.
3.2 Threat model
The threat model is used to identify potential threats in proposed protocols in order to reduce the security risks of the protocol [13,25–36]. The protocol in this article will be able to achieve the claimed security under the Dolev Yao model. In this model, the capabilities possessed by attackers are defined as follows:
(1) Attackers can eavesdrop on messages in V2G public channels;
(2) Attackers are able to maintain existing states, record communication information, and store commonly used values in communication message processes.
(3) Attackers can forge and send tampered messages after hijacking them;
(4) Attackers can impersonate legitimate users to participate in the operation of the protocol.
3.3 Security requirement
In this article, a secure and efficient authentication key protocol is designed [13,20–36,41]. This protocol can meet the following design objectives:
(1) Privacy protection: In V2G environment, CS and EV will achieve mutual authentication and exchange important information. However, users’ privacy information may be obtained by adversaries, who will analyze this sensitive data and infer users’ lifestyle habits and social activities. Therefore, the design of the protocol needs to implement privacy protection and ensure the anonymity of users during the authentication process.
(2) Session key security: Session keys are mainly used for encrypting and decrypting communication content, so it is necessary to ensure the security of session keys. In V2G environment, after completing authentication, the vehicle will share a session key with the aggregator for subsequent transmission of confidential data. If this key is stolen by an adversary, the entire communication process will no longer be secure. Therefore, the designed protocol needs to ensure the security of session keys.
(3) Resist impersonation attacks: Adversaries may disguise themselves as EVs or CSs and illegally access authorized data and privacy information. This may lead to the leakage of user identity privacy and data privacy. Therefore, the protocol needs to be able to resist impersonation attacks.
(4) Resist physical attacks: EVs are usually parked in easily accessible areas for adversaries and left unattended. This means that adversaries can easily capture devices on vehicles and launch various attacks on the keys stored in the device’s memory to steal sensitive data. Therefore, it is very important for the protocol to ensure that V2G entities are protected from physical attacks.
(5) Resist replay attacks: In this type of attack, the adversary will impersonate a legitimate entity by sending information from the previous session or a message from the current session. The entities in the entire communication session should be able to detect the freshness of messages and reject stale messages.
3.4 Elliptical curve cryptography
Elliptical Curve Cryptography (ECC) is a public key cryptography system constructed based on the characteristics of elliptic curves over finite fields [37].
For the additive cyclic subgroup G of elliptic curves with order q, we have:
1. Given P,
2. Given P,
3.5 Physical unclonable function
Physical unclonable function (PUF) is a random function that extracts the unique randomness of each integrated circuit from the changes in its physical and electrical characteristics, mapping the basic properties of hardware entities into a stream of bit information [38]. This mode is called challenge response pair (CRP). The PUF with challenge C as input and response R as output can be represented as: R = PUF(C). A secure PUF needs to meet the following properties: 1) No two challenges can produce the same response; 2) PUF should satisfy uniqueness, that is, it is not allowed for two PUF devices to be the same, because in the manufacturing process of PUF devices, some processing is required to maintain the uniqueness of PUF; 3) PUF should also meet unpredictability; 4) PUF should also meet reliability characteristics.
Due to the above characteristics of PUFs, even if attackers can capture nodes equipped with PUF and detect the internal circuit structure of non-volatile memory (NVM) in the chip, attempting to modify the internal organization to obtain key secret data stored therein, these operations will affect the internal structure of PUF and their response to challenges, rendering them useless. Therefore, using PUF can ensure the security of keys without occupying storage space, reduce the computational overhead of encryption algorithms, and alleviate hardware costs. This makes PUF more suitable for resource constrained IoT environments.
4 Protocol
Table 2 shows the definitions of notation.
4.1 Generation of system parameters
In the V2G network system, trusted authority TA is responsible for the establishment and initialization of the entire system, as well as selecting safety parameters for the system.
Step 1: Let E be an elliptic curve defined on the finite field F, and TA select a group G of order q with a large prime number on E.
Step 2: TA randomly selects
Step 3: TA selects a secure hash function H. In addition, EV and CS are equipped with their own physically unclonable functions
4.2 Registration
4.2.1
4.2.2
R1:
R2:
R3:
R4:
R5:
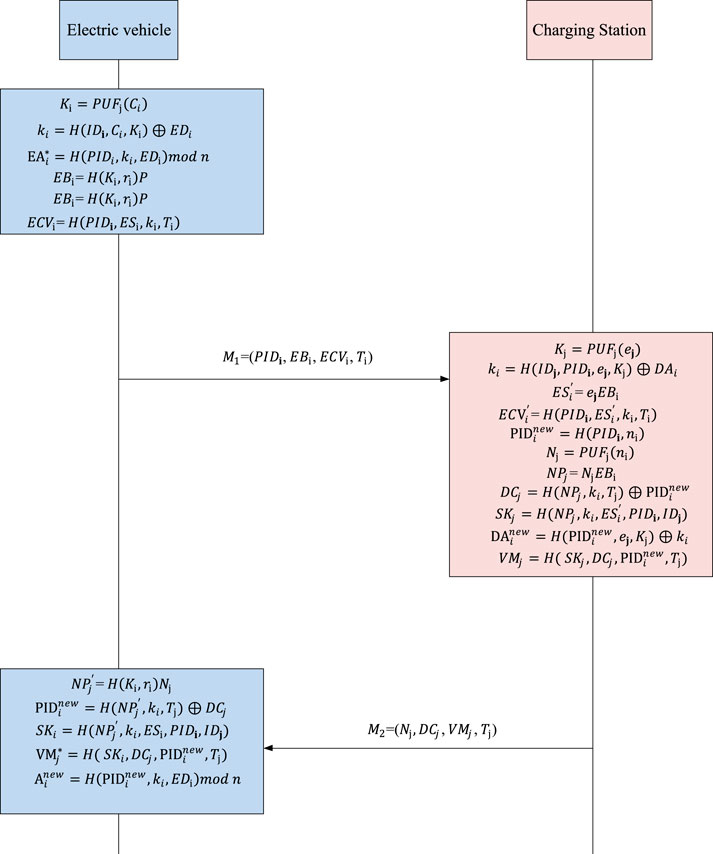
4.3 Authentication phase
The specific process is shown in Figure 2.
The specific steps are as follows:
A1.
A2.
A3.
A4. If
A5.
A6.
A7. If
5 Security analysis of the protocol
5.1 Simulation security analysis based on Scyther
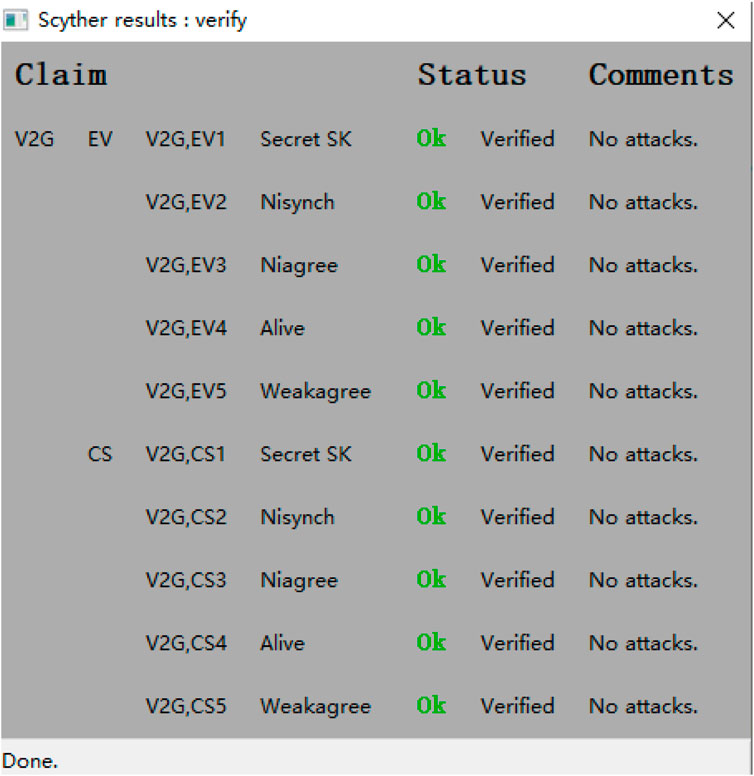
Scyther is a tool for formal analysis of protocol security, widely used to verify the security of protocols [38]. Scyther uses Secure Protocol Description Language (SPDL) for protocol description. SPDL simulates the message transmission process based on the participating roles, verifying the security of messages in the protocol from a formal security perspective, and whether they can resist security issues such as message tampering and forgery, replay attacks, and desynchronization attacks. If there is an attack, Scyther can present a graphical interface related to the attack for users to analyze. In Scyther, in addition to the Dolev Yao model, various types of adversarial models are also provided to verify the protocol’s resistance to newly introduced attacks.
This article uses Scyther security tool to simulate and analyze this protocol. In the proposed protocol, there are two roles: EV and CS. This article uses SPDL to model the proposed protocol roles and conducts security analysis of the protocol through security declarations. The Secret declaration can test the confidentiality of keys or other secret parameters. To describe different levels of security attributes, this article also uses the following statements: Alive and Weakage statements can test the protocol’s ability to resist man in the middle attacks. Niagree declares that it can control modules to confirm that they have received instructions from the controller, while Nisynch declares that it can synchronize operations between multiple modules in an attack.
The running results of Scyther security tool simulation analysis are shown in Figure 3. According to the analysis results, this protocol can meet the security requirements mentioned. The session key of this agreement is secure and cannot be cracked temporarily within a limited state space. Overall, the protocol proposed in this article is provably secure.
5.2 Security analysis using ROM
In this section, the tool employed for protocol security verification is the random oracle model. The security model, query model, and detailed security proofs used in the security analysis are described as follows.
Security Model:In this protocol, the primary participants are denoted as
Query Model:The adversary
• Execute (
• Send (
• Reveal (
• Corrupt
• Test
Theorem 1. The advantage of adversary
Where
Proof: We prove this theorem by defining a sequence of games
Game 1: In this game, adversary
Game 2: Based on the birthday paradox principle, the collision probability of the hash function output is bounded by
Game 3: Adversary
Game 4: In Game 4, adversary
All random oracles are simulated, and adversary
Finally, we obtain:
Through the above analysis, we can prove the security of the scheme under the ROM model.
5.3 Informal security analysis
5.3.1 Forward security
The session keys for
5.3.2 User anonymity and untraceability
During the registration phase,
5.3.3 Man in the middle attack
Assuming that attackers can eavesdrop on the messages transmitted during the authentication process through public channels. However, the attacker cannot obtain the identity identifier
5.3.4 User forgery attack
Attackers cannot forge
5.3.5 Mutual authentication
In this protocol,
5.3.6 Replay attack
The protocol in this article uses timestamps and random numbers in its design, both of which can resist replay attacks. Firstly, using timestamps
5.3.7 Session key security
In the authentication protocol,
5.3.8 Brief secret leakage attack
In the proposed protocol,
5.4 Security attribute
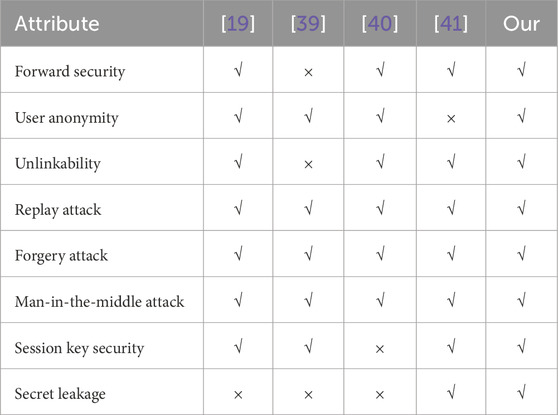
This article compares the security properties implemented by the protocol with those of other authentication protocols such as Tsai [19], Lwamo [39], Zhao [40] and Wang [41]. Tsai [19] and Lwamo [39] have implemented many security attributes, but there are still some attributes that have not been fully satisfied. In addition, although Zhao [40] achieves various security attributes well, it didn't analyze the session key security and secret leakage. At the same time, this protocol implements all security attributes, as shown in Table 3. Therefore, compared with the comparison protocol, this protocol implements all security attributes.
6 Performance analysis
6.1 Computational overhead
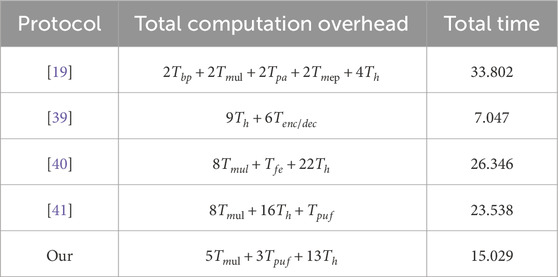
Here, we compare the computational cost of this protocol with Tsai [19], Lwamo [39] and Zhao [40]. In the experiment, this protocol used the JPBC library for experimental simulation. The hardware of the PC used is Intel Core i5 3.10 GHz CPU, 16GB RAM, programming language is Java, and the experimental code is executed on MyEclipse integrated development environment. By calculation, the time for hash operation, multiplication operation, pairing operation, PUF operation, fuzzy extractor and point addition operation are
As shown in Figure 4, compare the overall computational cost of this protocol with [19], [39] and [40]. In the authentication scenario, the computational costs of [19], [39] and [40] are 35.882 ms, 7.047 ms and 26.346 ms, respectively. The computational cost of this protocol is only 15.029 ms, which is the shortest compared to other protocols such as [19] and [40]. The cost of this protocol is higher than that of Lwamo [39]. But [39] did not allow for forward security, unlinkability and secret leakage. Therefore, compared to other protocols, this protocol achieves better computational overhead on a more comprehensive security basis.
6.2 Communication overhead
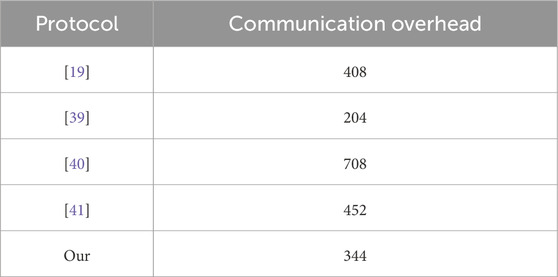
In this article, we will compare the communication overhead of our protocol with [19], [39] and [40]. In the comparison of communication overhead, the relevant group elements and variables are described as follows:
In Figure 5, further comparison of communication overhead among various protocols is shown. It can be seen that although the overall communication overhead of this protocol is slightly higher than [39], it is still lower than [19] and [40]. It should be explained that compared to [39], the communication overhead in this protocol is relatively high. In order to improve the security of the protocol, this paper sacrifices a small amount of communication overhead to achieve lower computational complexity and stronger security properties. Overall, in terms of communication overhead, this protocol is slightly weaker than [39], but better than [19] and [40]. However, in other aspects, compared to [19], [39] and Zhao [40], this protocol has more advantages.
7 Conclusion
This article focuses on the security challenges of V2G networks in smart grids and proposes an efficient and secure anonymous authentication protocol aimed at protecting user privacy and ensuring communication security. Through studying security threats in V2G environments, we have found that unauthorized access, user privacy breaches, and issues with transaction data integrity, as well as various forms of attacks during public communication, pose serious threats to the stable operation of V2G networks. In response to these challenges, we have designed an authentication protocol based on elliptic curve cryptography and physically unclonable function technology. This protocol not only achieves bidirectional authentication, ensuring the security of session keys, but also effectively protects the anonymity of participants by sending temporary identity values. Through simulation analysis and heuristic analysis using Scyther tool, we have verified the excellent performance of the protocol in terms of bidirectional authentication, session key security, forward security, and anonymity. At the same time, we have demonstrated that the protocol can resist various security threats. In addition, the performance comparison with other protocols shows that the proposed solution in this paper reduces costs while meeting the security requirements in the smart grid environment, demonstrating significant advantages in terms of security and overhead. In summary, the anonymity and privacy protection authentication protocol proposed in this article provides strong guarantees for the secure operation of V2G networks in smart grids. At the same time, the protocol is of great significance in promoting the popularization of electric vehicles, facilitating the two-way flow and management of energy and improving the flexibility and stability of the power grid.
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
ZS: Conceptualization, Data curation, Methodology, Supervision, Writing – original draft. YW: Formal Analysis, Methodology, Project administration, Supervision, Validation, Visualization, Writing – review and editing.
Funding
The author(s) declare that no financial support was received for the research and/or publication of this article.
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Generative AI statement
The author(s) declare that no Generative AI was used in the creation of this manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Khalid M. Smart grids and renewable energy systems: perspectives and grid integration challenges. Energy Strategy Rev (2024) 51:101299. doi:10.1016/j.esr.2024.101299
2. Zhang Y, Chen L, Battino M, Farag MA, Xiao J, Simal-Gandara J, et al. Blockchain: an emerging novel technology to upgrade the current fresh fruit supply chain. Trends Food Sci and Technology (2022) 124:1–12. doi:10.1016/j.tifs.2022.03.030
3. Faheem M, Kuusniemi H, Eltahawy B, Bhutta MS, Raza B. A lightweight smart contracts framework for blockchain-based secure communication in smart grid applications. IET Generation, Transm and Distribution (2024) 18(3):625–38. doi:10.1049/gtd2.13103
4. Zhang Z, Liu M, Sun M, Deng R, Cheng P, Niyato D, et al. Vulnerability of machine learning approaches applied in iot-based smart grid: a review. IEEE Internet Things J (2024) 11(11):18951–75. doi:10.1109/jiot.2024.3349381
5. Bai Z, Miao H, Miao J, Xiao N, Sun X. Artificial intelligence-driven cybersecurity applications and challenges. Innovative Appl AI (2025) 2(2):26–33. doi:10.70695/aa1202502a09
6. Jin Y, Liu J, Xu Z, Yuan S, Li P, Wang J. Development status and trend of agricultural robot technology. Int J Agric Biol Eng (2021) 14(4):1–19. doi:10.25165/j.ijabe.20211404.6821
7. Lu Y, Xu W, Leng J, Liu X, Xu H, Ding H, et al. Review and research prospects on additive manufacturing technology for agricultural manufacturing. Agriculture (2024) 14(8):1207. doi:10.3390/agriculture14081207
8. Udo WS, Kwakye JM, Ekechukwu DE, Ogundipe OB. Smart grid innovation: machine learning for real-time energy management and load balancing. Int J Smart Grid Appl (2024) 22(4):405–23. doi:10.51594/estj.v4i6.1395
9. İnci M, Savrun MM, Çelik Ö. Integrating electric vehicles as virtual power plants: a comprehensive review on vehicle-to-grid (V2G) concepts, interface topologies, marketing and future prospects. J Energy Storage (2022) 55:105579. doi:10.1016/j.est.2022.105579
10. Li J, Wu Z, Li M, Shang Z. Dynamic measurement method for steering Wheel Angle of Autonomous agricultural vehicles. Agric Basel (2024) 14(9):1602. doi:10.3390/agriculture14091602
11. Escoto M, Guerrero A, Ghorbani E, Juan AA. Optimization challenges in vehicle-to-grid (V2G) systems and artificial intelligence solving methods. Appl Sci (2024) 14(12):5211. doi:10.3390/app14125211
12. Naik N, Vyjayanthi C. Optimization of vehicle-to-grid (V2G) services for development of smart electric grid: a review[C]//2021 International Conference on smart generation computing, communication and networking (SMART GENCON). IEEE (2021). p. 1–6.
13. Sureshkumar V, Mugunthan S, Amin R. An enhanced mutually authenticated security protocol with key establishment for cloud enabled smart vehicle to grid network. Peer-to-Peer Networking Appl (2022) 15(5):2347–63. doi:10.1007/s12083-022-01350-3
14. Liang Y, Liu Y, Zhang X, Liu G. Physically secure and privacy-preserving charging authentication framework with data aggregation in vehicle-to-grid networks. IEEE Trans Intell Transportation Syst (2024) 25:18831–46. doi:10.1109/tits.2024.3443171
15. Prateek K, Maity S, Saxena N. Qska: a quantum secured privacy-preserving mutual authentication scheme for energy internet-based vehicle-to-grid communication. IEEE Trans Netw Serv Management (2024) 21:6810–26. doi:10.1109/tnsm.2024.3445972
16. Wei H, Miao J, Lv J, Chen CM, Kumari S, Amoon M. Secure and Trustworthy data management mechanism for Dance-Consumer Electronics in AIoT. IEEE Trans Consumer Electronics (2024) 71:1970–9. doi:10.1109/tce.2024.3471573
17. Miao J, Wang Z, Wang M, Feng X, Xiao N, Sun X. Security authentication protocol for massive machine type communication in 5G networks. Wireless Commun Mobile Comput (2023) 2023(1):1–10. doi:10.1155/2023/6086686
18. Yang Z, Yu S, Lou W, Liu C. P2: privacy-preserving communication and Precise Reward architecture for V2G networks in smart grid. IEEE Trans Smart Grid (2011) 2(4):697–706. doi:10.1109/tsg.2011.2140343
19. Tsai JL, Lo NW. A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst J (2015) 9(3):805–15. doi:10.1109/jsyst.2014.2322973
20. He D, Kumar N, Khan MK, Wang L, Shen J. Efficient privacy-aware authentication scheme for mobile cloud computing services. IEEE Syst J (2016) 12(2):1621–31. doi:10.1109/jsyst.2016.2633809
21. Abdallah A, Shen XS. Lightweight authentication and privacy-preserving scheme for V2GConnections. IEEE Trans Vehicular Technology (2016) 66(3):2615–29. doi:10.1109/tvt.2016.2577018
22. Zhang W, Yang W, Chen C, Li N, Bao Z, Luo M. Toward privacy-preserving blockchain-based electricity auction for V2G networks in the smart grid. Security Commun Networks (2022) 2022:1–12. doi:10.1155/2022/6911463
23. Bansal G, Naren N, Chamola V, Sikdar B, Kumar N, Guizani M. Lightweight mutual authentication protocol for V2G using physical unclonable function. IEEE Trans On Vehicular Technology (2020) 69:7234–46. doi:10.1109/tvt.2020.2976960
24. Khan A, Kumar V, Ahmad M, Jangirala S. A secure and energy efficient key agreement framework for vehicle-grid system. J Of Inf Security And Appl (2022) 68:103231. doi:10.1016/j.jisa.2022.103231
25. Su Y, Shen G, Zhang M. A novel privacy-preserving authentication scheme for V2G networks. IEEE Syst J (2019) 1–9. doi:10.1109/JSYST.2019.2932127
26. Mahmoud HE, Qi S, Angelos KM. Efficient, secure, and privacy-preserving PMIPv6 protocol for V2G networks. IEEE Trans Vehicular Technology (2019) 68(1):1–12. doi:10.1109/TVT.2018.2880834
27. Liu H, Ning H, Zhang Y, Xiong Q, Yang LT. Role-dependent privacy preservation for secure V2G networks in the smart grid. IEEE Trans Inf Forensics Security (2014) 9(2):208–20. doi:10.1109/tifs.2013.2295032
28. Saxena N, Choi BJ, Cho S. Lightweight privacy-preserving authentication scheme for V2G networks in the smart grid. In: IEEE Trustcom. IEEE (2015). p. 20–2.
29. Kaur K, Garg S, Kaddoum G, Gagnon F, Ahmad SH, Guizani M. A secure, lightweight, and privacy-preserving authentication scheme for V2G connections in smart grid. In: IEEE INFOCOM 2019 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). IEEE (2019). p. 541–6. doi:10.1109/INFCOMW.2019.8845140
30. Wang H, Qin B, Wu Q, Xu L, Domingo-Ferrer J. TPP: Traceable privacy-preserving communication and Precise Reward for vehicle-to-grid networks in smart grids. IEEE Trans Inf Forensics and Security (2015) 10(11):2340–51. doi:10.1109/tifs.2015.2455513
31. Nicanfar H, Leung VC. Multilayer Consensus ECC-based password authenticated key-exchange(MCEPAK) protocol for smart grid system. IEEE Trans Smart Grid (2013) 4(1):253–64. doi:10.1109/tsg.2012.2226252
32. Shen J, Zhou T, Wei F, Sun X, Xiang Y. Privacy-preserving and lightweight key agreement protocol for V2G in the social internet of things. IEEE Internet things J (2017) 5(4):2526–36. doi:10.1109/jiot.2017.2775248
33. Park K, Park Y, Das AK, Yu S, Lee J, Park Y. A dynamic privacy-preserving key management protocol for V2G in social internet of things. IEEE Access (2019) 7:76812–32. doi:10.1109/access.2019.2921399
34. Gope P, Sikdar B. An efficient privacy-preserving authentication scheme for energy internet-based vehicle-to-grid communication. IEEE Trans Smart Grid (2019) 10(6):6607–18. doi:10.1109/tsg.2019.2908698
35. Irshad A, Usman M, Chaudhry SA, Naqvi H, Shafiq M. A provably secure and efficient authenticated key agreement scheme for energy internet-based vehicle-to-grid technology framework. IEEE Trans Industry Appl (2020) 56(4):4425–35. doi:10.1109/TIA.2020.2966160
36. Sureshkumar V, Chinnaraj P, Saravanan P, Amin R, Rodrigues JJ. Authenticated key agreement protocol for secure communication establishment in vehicle-to-grid environment with FPGA Implementation. IEEE Trans Vehicular Technology (2022) 71(4):3470–9. doi:10.1109/tvt.2022.3146409
37. Miao J, Wang Z, Wang M, Garg S, Hossain MS, Rodrigues JJ. Secure and efficient communication approaches for industry 5.0 in edge computing. Computer Networks (2024) 242:110244. doi:10.1016/j.comnet.2024.110244
38. Nyangaresi VO, AlRababah AA, Yenurkar GK, Chinthaginjala R, Yasir M. Anonymous authentication scheme based on physically unclonable function and Biometrics for smart Cities. Eng Rep (2025) 7(1):e13079. doi:10.1002/eng2.13079
39. Lwamo NMR, Zhu L, Xu C, Sharif K, Liu X, Zhang C, et al. SUAA: a secure user authentication scheme with anonymity for the single and multi-server environments. Inf Sci (2019) 477:369–85. doi:10.1016/j.ins.2018.10.037
40. Zhao X, Li D, Li H. Practical three-factor authentication protocol based on elliptic curve cryp-tography for industrial internet of things. Sensors (2022) 22(19):7510. doi:10.3390/s22197510
Keywords: vehicle to grid, elliptic curve cryptography, anonymous, security, Scyther
Citation: Sun Z and Wang Y (2025) An anonymous authentication protocol for vehicle to grid based on elliptic curve cryptography. Front. Phys. 13:1589195. doi: 10.3389/fphy.2025.1589195
Received: 07 March 2025; Accepted: 31 July 2025;
Published: 26 August 2025.
Edited by:
Francisco Welington Lima, Federal University of Piauí, BrazilReviewed by:
Devishree Naidu, Shri Ramdeobaba College of Engineering and Management, IndiaTommaso Bianchi, University of Padua, Italy
Copyright © 2025 Sun and Wang. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Yan Wang, V2FuZ3lhbjEwMTZAbWFpbHMuY2NudS5lZHUuY24=
 Zeyu Sun1
Zeyu Sun1 Yan Wang
Yan Wang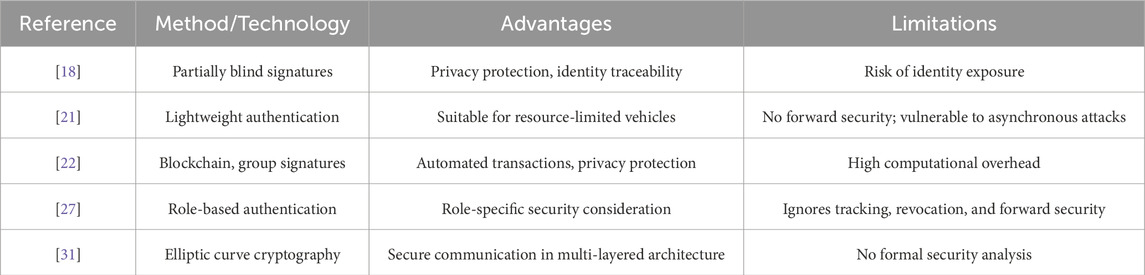
![Bar chart showing computation overhead across five categories: [44], [45], [46], [47], and](https://www.frontiersin.org/files/Articles/1589195/fphy-13-1589195-HTML-r1/image_m/fphy-13-1589195-g004.jpg)
![Bar chart showing communication overhead for five different methods. Method [44] has an orange bar at 408, [45] has a gray bar at 204, [46] has a yellow bar reaching 708, [47] has a blue bar at around 452, and](https://www.frontiersin.org/files/Articles/1589195/fphy-13-1589195-HTML-r1/image_m/fphy-13-1589195-g005.jpg)