Abstract
The rapid growth of e-commerce has been significantly driving the logistics industry’s development, while the speed of information technology transformation has laid a solid foundation for this progress. The Internet of Things (IoT), recognized as a representative of next-generation information technology, has injected new vitality into intelligent logistics management through its powerful data collection and transmission capabilities. The importance of user access control mechanisms has become increasingly evident in logistics management systems. Therefore, this paper proposes a signature-based authenticated scheme for logistics management systems. In this scheme, the user’s password, biometrics and smart card are used as the three authentication factors. During the login and authentication phase, registered users and devices in the logistics management system can securely and efficiently complete mutual authentication and key agreement. To verify the security performance of the proposed scheme, an simulation analysis is performed using the Scyther tool. Furthermore, performance evaluation demonstrates that the proposed scheme not only significantly enhances the security of the logistics management system but also maintains low costs.
1 Introduction
The continuous advancement of the socio-economic landscape has made the logistics industry a crucial pillar of the economic system, profoundly influencing people’s daily lives. Driven by the rapid advancements in information technology, Internet of Things (IoT) and artificial intelligence, the logistics industry is steadily advancing toward a new phase of intelligent transformation. By leveraging IoT technology, the logistics management supply chain has been constructed and optimized, establishing an integrated supply channel for goods circulation. This has not only significantly contributed to the prosperity of production and sales industries but also effectively addressed various challenges in traditional logistics, greatly enhancing distribution efficiency and service quality. The core of logistics management systems under IoT is to enable seamless interaction and sharing of diverse information, thereby effectively reducing transportation costs, improving efficiency, and driving the intelligence of logistics decision-making and execution. Through intelligent management models, high-quality logistics services can be provided at reduced costs. The essence of IoT-based logistics management systems lies in relying on real-time and comprehensive information to emulate human intelligence, make optimal decisions, create greater value for customers, and deliver a superior service experience. Traditional logistics models have often relied on experience-based decision-making due to delayed and insufficient information. In contrast, IoT-based logistics management systems have achieved revolutionary innovation over traditional logistics, having profound impacts on the industry’s structure, operating models, business models, ecological systems, and development paradigms. With the widespread application of big data technology, IoT-based logistics management systems leverage big data to process logistics information, further integrating characteristics such as informatization, digitization, networking, and visualization.
With the deep integration of IoT technology into logistics management systems, sensors, as an indispensable component of these systems, play a pivotal role [
1]. They serve not only as direct perceivers of logistics environment information but also as key enablers for the intelligent and precise control of logistics processes. Sensors can accurately collect and monitor in real time various physical and chemical parameters in logistics environments, such as temperature, humidity, and pressure, providing abundant and accurate data support for logistics decision-making. These real-time data not only enhance the transparency of logistics processes but also enable managers to promptly identify and address anomalies that could affect cargo safety and quality, thereby ensuring the efficiency and security of logistics operations. In IoT-based logistics management systems, mutual authentication between sensor devices and users is important for ensuring the security and efficiency of logistics. It effectively prevents unauthorized access and operations in complex logistics environments, safeguarding the integrity and security of logistics information. Although IoT-based logistics management systems have made significant progress compared to traditional models, existing authentication schemes still have key limitations. Most current schemes rely on two-factor authentication, which is vulnerable to offline brute force attacks, device theft, and session hijacking threats in untrusted networks. Additionally, traditional schemes often overlook the computational limitations of edge devices, resulting in unacceptable delays during large-scale deployment. Based on the above discussion, the main contributions of this paper are as follows:
(1) This paper proposes a signature-based authenticated scheme for logistics management systems. The proposed scheme enables legitimate registered users to access data or tasks from devices. During the user login phase, passwords, personal biometrics and smart card are used to verify user identity. In the authentication phase, mutual authentication between the user and device is performed, and a secure session key is established to ensure the security of subsequent communications between the user and the device.
(2) Formal security analysis using Scyther has been conducted to ensure the security of the proposed scheme. Furthermore, heuristic analysis indicates that the proposed scheme can resist common attacks while maintaining user-friendliness. Experimental results show that the scheme performs excellently in terms of security strength, communication efficiency, and scalability, providing a practical and feasible security authentication framework for large-scale intelligent logistics systems.
In Section 2 and Section 3, a brief review of the relevant literature and knowledge is presented. The proposed scheme is detailed in Section 4. The security of the proposed scheme is evaluated in Section 5. Subsequently, performance analysis is conducted in Section 6. Finally, we conclude this paper.
2 Literature review
Authentication serves as the first line of defense in logistics management systems. For sensor devices, mutual authentication with users is conducted to validate the legitimacy of user identities while also verifying whether the devices themselves are authorized to read or write specific information. This bidirectional authentication mechanism significantly enhances system security and mitigates the risks of data breaches or damages caused by malicious attacks or operational errors.
In industrial scenarios or smart logistics contexts, numerous authentication key agreement protocols have been proposed by researchers [2–5]. Chang et al. [6] discovered that Kalra et al.'s scheme [5] failed to achieve the claimed mutual authentication and session key agreement. An improved protocol was proposed. However, Wang et al. [7] demonstrated that Chang et al.'s [6] scheme remained insecure. Subsequently, the protocol was improved, and its security was formally proven. Later, Pham et al. [8] optimized Wang et al.'s [7] protocol to support mutual authentication between devices. Despite its advantages in security and efficiency, the scheme lacked privacy protection mechanisms for devices due to identity exposure during authentication. Pham et al. [9] further improved the aforementioned protocol, and a privacy-preserving authentication protocol was proposed to support secure communication between devices in distributed network architectures. Amin et al. [10] propose a scheme that incurs significant computational overhead. Li et al. [11] proposed a scheme based on ECC, but it involves sunstantial. Wazid et al. [12] proposed an identity authentication scheme vulnerable to forgery threats, while Li et al. [13] introduced a privacy-preserving data aggregation protocol susceptible to impersonation threats. To reduce overhead, Sodorov et al. [14] proposed an RFID-based ultra-lightweight identity verification key exchange for intelligent supply chains. Later, Sergi et al. [15] introduced a secure authentication algorithm for smart logistics and IoT systems. In recent years, to address the growing demand for secure communications in industrial IoT, researchers have conducted extensive studies on authentication and key management. Zhou et al. [16] proposed a two-factor authentication mechanism utilizing hash functions and XOR operations, which emphasized lightweight properties. However, subsequent studies revealed its susceptibility to replay attacks and key leakage issues. To address these shortcomings, Ali et al. [17] introduced a three-factor authentication approach incorporating hash functions, XOR operations, and AES encryption. Despite these enhancements, the scheme failed to counter man-in-the-middle (MITM) attacks and did not achieve the expected level of secure authentication, as noted in related research [18]. In practice, approaches relying solely on lightweight operations often face challenges in maintaining robust security. To mitigate this, public key cryptography [5] has been employed to strengthen protocol security. Das et al. [19] proposed a certificate-based device access control mechanism known as LACKA-IoT. Nevertheless, its significant computational and communication overhead restricts its effectiveness in resource-constrained industrial settings. Meanwhile, Chatterjee et al. [20] designed a protocol that leverages identity-based encryption alongside hash functions, but it fell short in ensuring sufficient forward secrecy.
Identity-Based Cryptography (IBC) eliminates the need for extensive digital certificate exchanges in secure applications, making it more lightweight and easier to deploy. Under an IBC framework, a device’s private key is generated based on its unique identifier, removing the requirement for PKI-provided certificate support. This significantly broadens the application scope of public key cryptography while substantially reducing the costs associated with certificate maintenance. Over time, identity-based key algorithms have undergone numerous advancements [21–24]. Li et al. introduced a decentralized multi-signature protocol [25] that integrates identity-based signatures with the Schnorr scheme under the elliptic curve discrete logarithm problem. This protocol addresses the challenges of security and efficiency in IoT identification within centralized signature schemes. Fang et al. utilized IBS to prevent data alteration and reduce the overhead of third-party authentication [26]. Heo et al. [27] designed an identity-based mutual authentication scheme for power line communication, effectively simplifying the deployment and management of authentication credentials by eliminating the need for public key certificates. Li et al. [28] proposed a cloud-based identity authentication scheme designed for asymmetric mutual authentication between cloud servers and device users. Jin et al. [29] focused on data security and privacy in wireless body area networks by designing a privacy-preserving scheme based on biometric identities. In this scheme, user identities are constructed from biometric traits. Based on this, the authors developed an access control scheme. Subsequently, many researchers [30–32] have proposed identity-based authentication schemes in Vehicular Ad hoc Networks (VANET) to improve the communication efficiency of VANET. Existing research has made significant progress in the design of authentication protocols for logistics and industrial scenarios, but limitations remain. Most schemes struggle to balance security and lightweight requirements. Lightweight protocols are often vulnerable to replay attacks or key leakage risks due to simplified computations, while schemes that introduce public-key cryptography improve security but incur high overhead due to certificate management or complex computations, making them difficult to adapt to resource-constrained industrial environments.
3 Preliminaries
3.1 System model
In IoT-based logistics management systems, sensors capture detailed information about objects, including location, temperature, orientation, and other parameters. Any authenticated user can access the status of these objects. The system model proposed is illustrated in Figure 1, with the following participants:
FIGURE 1

System model.
3.1.1 Registration center (RC)
RC is responsible for initializing the system and handling the registration of users and service providers. RC distributes secret information associated with each registrant. Notably, in this scheme, the RC is not involved during the mutual authentication phase.
3.1.2 User ()
Users can directly access sensory data collected by devices, allowing them to obtain real-time information about the environment, devices, or target objects. This sensory data can include various types of information such as light intensity, location, and motion status, depending on the type of sensor and the application scenario. By accessing this data, users or applications can accurately track specific target objects, such as the current location and condition of a package during logistics transportation.
3.1.3 Device ()
Sensor devices deployed in warehouses and on vehicles efficiently read item-related information, including identity, status, and other relevant parameters. This may involve unique identifiers, transportation conditions, and location records for the goods being tracked.
3.2 Elliptic curve cryptography
Definition 1Elliptic Curve Discrete Logarithm Problem (ECDLP): is an elliptic curve group over the prime field . P is a generator of . Computing is relatively easy for given and . However, given , , to find an integer such that is computational hard.
Definition 2Elliptic Curve Diffie- Hellman Problem (ECDHP):Let , and are points over an elliptic curve. It is computational infeasible to solve without knowledge of and .
3.3 Adversary model
In our proposed scheme, we adopt the widely recognized Dolev-Yao threat model (DY model) to assess potential security risks. The DY model assumes a powerful adversary with full control over the communication channel, capable of eavesdropping, tampering with, injecting, or replaying any transmitted message [
33–
35]. We assume the following capabilities for an adversary (denoted as A):
(1) It is assumed that can intercept, block, and alter messages transmitted over public channels.
(2) It is assumed that numerate all possible identity-password pairs within the dictionary space.
(3) In three-factor authentication system, it is assumed that could potentially compromise any two of the authentication factors.
4 Proposed protocol
We propose a signature-based authenticated scheme for logistics management systems. It comprises three types of participants: the registration center (RC), sensor devices (), and users (). Table 1 shows the symbols.
TABLE 1
| Notations | Definitions |
|---|---|
| Registration Center | |
| Identity for user | |
| Identity for Device | |
| session key | |
| Current Timestamp | |
| Hash function | |
| Nonequivalence Operation | |
| k | System Private Key |
Symbols.
4.1 System setup
E is an elliptic curve defined over , and the RC selects a cyclic additive group G on with an order of q, where q is a prime number. The generator of G is P. RC randomly selects as the system’s master key, and the system’s public key is . RC chooses a secure hash function (). RC securely stores the master key k and publishes parameters .
4.2 Registration phase
4.2.1 Device registration
(1) sends its identity value to RC.
(2) Upon receiving the identity value of , RC calculates and . The RC then sends to via a credible channel.
(3) stores securely and publicly shares .The registration process is as illustrated in Figure 2.
FIGURE 2

Device registration process.
4.2.2 User registration
(1) chooses its identity , a password , and inputs biometric . Then, generates a random number and computes . Finally, sends to RC.
(2) Upon receiving , RC checks whether exists in its authentication list. If it does, the user is considered a duplicate registrant, and the server rejects the request. If does not exist, the RC stores in its authentication list. Then, RC selects a random number , and computes , , , , . Finally, RC stores in smart card and issues to via reliable channel.
(3) Upon receiving , computes , replaces with , and stores and in .
The user registration process is as illustrated in Figure 3.
FIGURE 3

User registration process.
4.3 User login
enters 、 and imprints . Next the smart card performs the following calculations: , , , , and verifies whether . If , the session terminates. If , the smart card proceeds to the next step.
4.4 Mutual authentication
shows the mutual authentication process between the device and the user, where the user completes the signing process and the device verifies the signature. The process uses a signature scheme that signs messages with pre-generated private keys.
Figure 5is verification algorithm. The detailed steps are as follows:
(1) forms current timestamp . The user generates a signature: according to the signing algorithm shown in Figure 6. Finally, the user sends: {} to over a public channel.
(2) Upon receiving {}, verifies the freshness of the timestamp . If the check holds, executes the signature verification algorithm to check its validity. If successful, selects a random number , computes ) and sends {} to the user, which is current timestamp.
(3) Upon receiving {}, the smart card checks the freshness of the timestamp . If the check holds, the smart card computes , (). The smart card verifies whether . If they match, mutual authentication is successfully completed, and the session key is established.
FIGURE 4

Login and mutual authentication process.
FIGURE 5
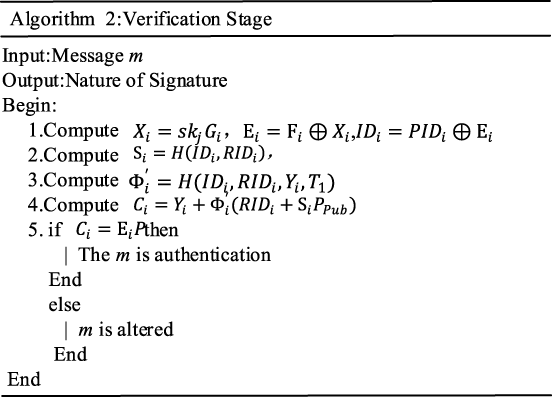
Verification algorithm.
FIGURE 6

Signing algorithm.
4.5 Password and biometric update
User
can update their password and biometric data offline by following these steps:
(1) inputs 、 , and imprints , then performs the following calculations: . The smart card verifies whether If , the smart card rejects the request. Otherwise, is prompted to input a new password and new biometric data .
(2) inputs and , and then the smart card performs the following calculations: , , , .
(3) The smart card updates with .
5 Security evaluation
5.1 Informal security analysis
Here, we conducted a comprehensive evaluation of potential security risks through heuristic analysis. By simulating real-world attack scenarios, we validated the scheme’s ability to defend against informal attacks [36–42].
5.1.1 Mutual authentication
Devices authenticate users by verifying . User generates the signature using . Only users with can compute a valid signature. Additionally, the user authenticates devices based on . During the signing process, the user encrypts using . Only devices with the key can compute and recover , ensuring that equals , and successfully establish the session key.
5.1.2 Session key agreement
User and device generate . The session key consists of and , where is derived from the elliptic curve Diffie-Hellman key exchange. , generated using , ensures resistance against attacks targeting session-specific temporary information.
5.1.3 Perfect forward secrecy
Assume obtains the user’s and device’s long-term secrets and intercepts information. attempts to recover SK, but SK is protected by random numbers and , where () is generated using the Diffie-Hellman key exchange. Even if the attacker gains long-term secrets, they cannot retrieve from and .
5.1.4 User impersonation attack
attempting to impersonate needs to create a legitimate login request by generating and . These values require the , , , and the information stored in . Only with all these elements can an attacker successfully generate a legitimate login request.
5.1.5 Device impersonation attack
attempting to impersonate needs to create a valid response message by computing : , = . Since attacker lacks knowledge of , they cannot compute . Additionally, . To derive , the attacker would also need the user’s . Thus, cannot produce a valid response message.
5.1.6 User-friendliness
During the authentication phase, the registration center remains offline, allowing users to directly access devices without RC. The proposed scheme supports password and biometric updates, which can be completed without further communication with the RC. Therefore, the proposed scheme demonstrates excellent user-friendliness.
5.1.7 Resistance to insider attack
In insider attacks, privileged users such as system administrators may attempt to access legitimate users’ accounts. However, in this scheme, the user’s and biometric are concatenated, and the concatenation is processed using hash function H, XORed with the parameter . Neither insiders nor the registration center can retrieve the original password.
5.1.8 Stolen smart card attack
In the proposed scheme, if steals a smart card, they may attempt to impersonate a legitimate user. However, cannot log into system because they must also provide the user’s , password , and biometric . While the smart card is tamper-resistant, could extract all stored information. Nevertheless, cannot derive the user’s password or biometric data.
5.1.9 Temporary secret leakage attack
If the random numbers and are accidentally or maliciously exposed to an attacker , they can compute . However, still cannot derive . This is because cannot retrieve without access to the user’s private key or the device’s private key.
5.1.10 Man-in-the-middle attack
forges valid user authentication and responses messages to convince participants that the information is legitimate. To do so, would need to compute relevant parameters. However, cannot access the user’s and device’s private keys, password , or biometric . As a result, cannot forge valid authentication and response messages.
5.1.11 Replay attack
According to the proposed scheme, the user and the device generate new random numbers and during the authentication phase, and the information recipient verifies the timestamp. Therefore, the proposed new protocol can effectively defend against replay attacks.
5.2 Scyther verification
The proposed scheme was subjected to an in-depth security analysis using Scyther, with the results presented in Figure 7. During the verification process, multiple security properties of the protocol were evaluated, including key confidentiality (Secret SK), liveness (Alive), weak agreement (Weakagree), non-interactive agreement (Niagree), and synchronization (Nisynch). All verification results were marked as “Ok,” with a status of “Verified” and no attacks detected, indicating that no potential vulnerabilities were identified under the current verification conditions.
FIGURE 7

Scyther results.
6 Performance analysis
This section will provide a comparative performance analysis, including comparisons of computational and communication overhead. This section focuses on the performance comparison during the login and authentication phases. The performance comparison in this section focuses solely on elliptic curve addition, point multiplication, and hash operations. XOR operations are considered negligible in terms of computational time, and thus bitwise XOR operations are excluded from the time analysis.
6.1 Security comparison
A detailed comparison between the proposed scheme and other related schemes has been carried out. The outcomes of this evaluation are summarized in Table 2. In the table, ✓ signifies the presence of a specific feature or functionality, whereas ⨯ denotes its absence.
TABLE 2
| Feature | [35] | [36] | [37] | [38] | Our |
|---|---|---|---|---|---|
| Mutual authentication | |||||
| Key Agreement | |||||
| Forward Security | |||||
| User Friendliness | |||||
| Replay Attack | |||||
| Impersonation Attack | |||||
| Man-in-the-Middle Attack | |||||
| Temporary Secret Leakage Attack | |||||
| Stolen Smart Card Attack | |||||
| Privileged Insider Attack | |||||
| Three-factor authentication |
Security comparison.
6.2 Computation overhead comparison
The computational overhead of the proposed protocol is compared with the protocols presented in Refs. [35–38], as shown in Table 3. The symbols , , and represent the time required to execute a single hash function, elliptic curve addition, and elliptic curve point multiplication, respectively. The following times (in milliseconds) for cryptographic operations are used [40, 41]: , , .
During the user login phase, 4 hash operations are performed, along with 3 elliptic curve point multiplications and 1 hash operation for the signature algorithm. Additionally, when the device receives a message, 1 elliptic curve point multiplication and 2 hash operations are performed. During the authentication phase, the device verifies the signature algorithm, requiring 4 elliptic curve point multiplications, 1 elliptic curve addition, and 2 hash operations, along with 2 more hash operations and 2 elliptic curve point multiplications. Therefore, the total computational cost of the proposed scheme is .
As shown in Table 3 and Figure 8, the proposed scheme demonstrates significant optimization in computational cost and execution time compared to other protocols. The total execution time of the proposed scheme is 134.747 ms, which is significantly lower than the protocols in [36, 37]. Compared to the protocol in [38], the execution time of the proposed scheme is reduced by approximately 17.4%. Additionally, the scheme reduces the number of hash operations and minimizes the computationally expensive elliptic curve point multiplication operations. This indicates that the proposed scheme strikes a better balance between performance optimization and computational complexity, showcasing superior efficiency.
TABLE 3
Computation overhead.
FIGURE 8

Computation overhead.
6.3 Communication overhead comparison
To evaluate the communication cost, it is assumed that the user identity, random number, timestamp, hash output, and elliptic curve point ) require 160 bits, 160 bits, 32 bits, 160 bits, and 320 bits, respectively, where and are the x- and y-coordinates of the elliptic curve point P.
In the proposed protocol, the total length of the exchanged information during the login and authentication phases is calculated as . The communication costs of other protocols are summarized in Table 4. From the comparison, it is evident that the proposed scheme incurs a lower communication overhead. Additionally, the amount of information transmitted during the authentication phase is relatively small. This demonstrates that the proposed scheme achieves higher security and functionality while minimizing communication costs.
As shown in Table 4 and Figure 9, the proposed scheme offers a significant advantage in terms of both communication cost and the amount of transmitted information compared to other protocols. In contrast to protocols, the proposed scheme requires only 2 messages to be transmitted, significantly fewer than the 3 to 5 messages needed by other protocols. This reduction in communication rounds enhances the efficiency of the protocol. In terms of communication cost, the proposed scheme has the lowest overhead at 1984 bits. This indicates that the proposed scheme effectively reduces information transmission costs through optimized communication, significantly improving the overall performance of the protocol, particularly in scenarios where high communication efficiency is required, ensuring the scalability of the protocol in large-scale scenarios.
TABLE 4
Communication overhead.
FIGURE 9

Communication overhead.
7 Conclusion
This paper proposes a signature-based authentication scheme designed to meet the security requirements of logistics management systems in the Internet of Things (IoT). The proposed scheme effectively reduces the complexity of elliptic curve operations and the number of communication exchanges, thus achieving a dual reduction in both computational cost and communication overhead. Additionally, the scheme incorporates a three-factor authentication mechanism to enhance system security. To comprehensively evaluate the effectiveness of the proposed protocol, it has been validated through heuristic evaluation, and testing with the Scyther tool. Compared to current mainstream protocols, the proposed scheme shows significant advantages in terms of communication efficiency and operational performance. It not only ensures the effectiveness of identity authentication and maintains data integrity but also provides robust protection against various attacks. The proposed scheme is suitable for various logistics scenarios, such as ensuring that only authorized personnel or devices can operate the system in large warehouses, preventing unauthorized operations or data tampering. Additionally, real-time identity verification is carried out using biometrics (such as fingerprints) and smart cards, ensuring that only designated personnel can unlock or access order information, reducing the risk of cargo theft during transportation. This scheme is particularly well-suited for logistics management scenarios requiring high security and efficiency, providing an efficient and reliable solution for secure communication in logistics.
Statements
Data availability statement
The original contributions presented in the study are included in the article/supplementary material, further inquiries can be directed to the corresponding author.
Author contributions
ZeZ: Conceptualization, Data curation, Formal Analysis, Investigation, Methodology, Project administration, Resources, Supervision, Visualization, Writing–original draft. XL: Data curation, Investigation, Methodology, Software, Supervision, Validation, Visualization, Writing–original draft. LG: Conceptualization, Methodology, Project administration, Validation, Writing–review and editing. ZaZ: Data curation, Investigation, Resources, Software, Validation, Writing–review and editing.
Funding
The author(s) declare that no financial support was received for the research and/or publication of this article.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Generative AI statement
The author(s) declare that no Generative AI was used in the creation of this manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1.
ChenJLiTZhangYYouTLuYTiwariPet alGlobal-and-Local attention-based reinforcement learning for cooperative behaviour control of multiple UAVs. IEEE Trans Vehicular Technology (2024) 73(3):4194–206. 10.1109/tvt.2023.3327571
2.
MiaoJWangZMiaoXXingL. A secure and efficient lightweight vehicle group authentication protocol in 5G networks. Wireless Commun Mobile Comput (2021) 2021:1–12. 10.1155/2021/4079092
3.
XiaoNWangZSunXMiaoJ. A novel blockchain-based digital forensics framework for preserving evidence and enabling investigation in industrial Internet of Things. Alexandria Eng J (2024) 86:631–43. 10.1016/j.aej.2023.12.021
4.
KhelloufiANingHNaouriASadaABQammarAKhalilAet alA multimodal latent-features-based service recommendation system for the social Internet of Things. IEEE Trans Comput Social Syst (2024) 11:5388–403. 10.1109/tcss.2024.3360518
5.
KalraSSoodSK. Secure authentication scheme for IoT and cloud servers. Pervasive Mobile Comput (2015) 24:210–23. 10.1016/j.pmcj.2015.08.001
6.
ChangCCWuHLSunCY. Notes on secure authentication scheme for IoT and cloud servers. Pervasive Mobile Comput (2017) 38:275–8. 10.1016/j.pmcj.2015.12.003
7.
WangKHChenCMFangWWuTY. A secure authentication scheme for internet of things. Pervasive Mobile Comput (2017) 42:15–26. 10.1016/j.pmcj.2017.09.004
8.
PhamDMCNguyenLPTDangTK. Resource-constrained IoT authentication protocol: an ECC-based hybrid scheme for device-to-server and device-to-device communications. In: Proceedings of the 6th international conference on future data and security engineering (FDSE 2019). Berlin: Springer (2019). p. 27–9.
9.
PhamCDDangTK. A lightweight authentication protocol for d2d-enabled IoT systems with privacy. Pervasive Mobile Comput (2021) 74:101399. 10.1016/j.pmcj.2021.101399
10.
AminRIslamSHBiswasiGPGiriDKhanMKKumarN. A more secure and privacy-aware anonymous user authentication scheme for distributed mobile cloud computing environments. Security Commun Networks (2016) 9(17):4650–66. 10.1002/sec.1655
11.
LiXNiuJBhuiyanMZAWuFKaruppiahMKumariS. A robust ECC-based provable secure authentication protocol with privacy protection for industrial internet of things. IEEE Transaction Ind Inf (2018) 14(8):3599–609. 10.1109/TII.2017.2773666
12.
WazidMDasAKOdeluVKumarNContiMJoM. Design of secure user authenticated key management protocol for generic IoT networks. IEEE Internet Things J (2018) 5(1):269–82. 10.1109/jiot.2017.2780232
13.
LiXLiuSWuFKumariSRodriguesJJPC. Privacy preserving data aggregation scheme for mobile edge computing assisted IoT applications. IEEE Internet Things J (2019) 6(3):4755–63. 10.1109/jiot.2018.2874473
14.
SidorovMOngMTSridharanRVNakamuraJOhmuraRKhorJH. Ultralightweight mutual authentication RFID protocol for blockchain enabled supply chains. IEEE Access (2019) 7:7273–85. 10.1109/access.2018.2890389
15.
SergiIMontanaroTBenvenutoFLPatronoL. A smart and secure logistics system based on IoT and cloud technologies. Sensors (2021) 21(6):2231. 10.3390/s21062231
16.
ZhouLLiXYehKSuCChiuW. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Generation Computer Syst (2019) 91:244–51. 10.1016/j.future.2018.08.038
17.
AliZHussainSRehmanRMunshiALiaqatMKumarNet alAn improved three-factor symmetric-key based secure AKA scheme for multi-server environments. IEEE Access (2020) 8:107993–8003. 10.1109/ACCESS.2020.3000716
18.
EsfahaniAMantasGMatischekRSaghezchiFBRodriguezJBicakuAet alA lightweight authentication mechanism for M2M communications in industrial IoT environment. IEEE Internet Things J (2019) 6(11):288–96. 10.1109/jiot.2017.2737630
19.
DasAWazidMYannamARodriguesJParkY. Provably secure ECC-based device access control and key agreement protocol for IoT environment. IEEE Access (2019) 7:55382–97. 10.1109/access.2019.2912998
20.
ChatterjeeUGovindanVSadhukhanRMukhopadhyayDChakrabortyRMahataDet alBuilding PUF based authentication and key exchange protocol for IoT without explicit CRPs in verifier database. IEEE Trans Dependable Secure Comput (2019) 16(3):424–37. 10.1109/tdsc.2018.2832201
21.
ShamirA. Identity-based cryptosystems and signature schemes. Lect.notes Comput (1985) 196(2):47–53. 10.1007/3-540-39568-7_5
22.
SakaiROhgishiKKasaharaM. Cryptosystems based on pairing. In: Proc. Of the 2000 symposium on cryptography and information security. Okinawa, Japan (2000).
23.
BonehDFranklinM. Identity-based encryption from the weil pairing (2003). p. 213–29.
24.
DeebakBDMemonFHKhowajaSADevKWangWQureshiNMF. In theDigital age of 5G networks:seamless privacy-PreservingAuthentication forCognitive-inspired internet of medical things. IEEE Trans IndustrialInformatics (2022) 18(12):8916–23. 10.1109/tii.2022.3172139
25.
LiuHHanDCuiMLiK -CSouriAIdenMultiSigMS. Ldentity-BasedDecentralized multi-signature in internet of things. J.EEE Trans onComputational Social Syst (2023) 10(4):1711–21. 10.1109/TCSS.2022.3232173
26.
FangLLiMLiuZLinCJiSZhouA. A secure and authenticated MobilePayment protocol against of-site attack strategy. lEEE Trans Dependableand Secure Comput (2022) 19(5):3564–78. 10.1109/TDSC.2021.3102099
27.
HeoJHongCSChoiMSJuSHLimYH. Identity-based mutual device authentication schemes for PLC system[C]//2008 IEEE international symposium on power line communications and its applications. IEEE (2008) 47–51. 10.1109/ISPLC.2008.4510397
28.
LiHDaiYTianLYangH. Identity-based authentication for cloud computing. In: 2009 IEEE international conference on cloud computing. IEEE (2009). p. 157–66.
29.
JinCHXuYLChenGHYuCHJinYShanJS. EBIAC: efficient biometric identity-based access control for wireless body area networks. J Syst Architecture (2021) 121:102317. 10.1016/j.sysarc.2021.102317
30.
BabuESDadiAKSinghKKNayakSRBhoiAKSinghA. A distributed identity-based authentication scheme for internet of things devices using permissioned blockchain system. Expert Syst – J Knowledge Eng (2022) 39(10). 10.1111/exsy.12941
31.
ShareedaMAAnbarMManickamSHasbullahIH. Towards identity-based conditional PrivacyPreserving authentication scheme for vehicular ad hoc networks. IEEE Access (2021) 9:113226–38. 10.1109/ACCESS.2021.3104148
32.
BansalUKarJIkramANaikK. ID-CEPPA: identity-based computationally efficient PrivacyPreserving authentication scheme for vehicle-to-vehicle communications. Jorunal Syst Architecture (2022) 123:102387. 10.1016/j.sysarc.2021.102387
33.
UllahIAminNUKhanMAKhattakHKumariS. An efficient and provable secure certificate-based combined signature, encryption and signcryption scheme for internet of things (IoT) in mobile health (M-Health) system. J Med Syst (2021) 45(1):4. 10.1007/s10916-020-01658-8
34.
MandalSBeraBSutralaAKDasAKChooKKRParkY. Certificateless-signcryption-based ThreeFactor user access control scheme for IoT environment. IEEE Internet Things J (2020) 7(4):3184–97. 10.1109/jiot.2020.2966242
35.
SaqibMJasraBMoonAH. A lightweight three factor authentication framework for IoT based critical applications. J King SaudUniversity-Computer Inf Sci (2022) 34(9):6925–37. 10.1016/j.jksuci.2021.07.023
36.
MaMHeDWangHKumarNChooKKR. An efficient and provably secure authenticatedkeyagreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet Things J (2019) 6(5):8065–75. 10.1109/jiot.2019.2902840
37.
LiFHanYJinC. Practical access control for sensor networks in the context of the Internet of Things. Comput Commun (2016) 89–90:154–64. 10.1016/j.comcom.2016.03.007
38.
SutralaAKObaidatMSSahaSDasAKAlazabMParkY. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyberphysical systems. IEEE Trans Intell Transportation Syst (2021) 23(3):2316–30. 10.1109/tits.2021.3056704
39.
MalaniSSrinivasJDasAKSrinathanKJoM. Certificatebased anonymous device access control scheme for IoT environment. IEEE Internet Things J (2019) 6(6):9762–73. 10.1109/JIOT.2019.2931372
40.
WuLWangJChooK-KRHeD. Secure key agreement and key protection for mobile device user authentication. IEEE Trans Inf Forensics Security (2019) 14(2):319–30. 10.1109/tifs.2018.2850299
41.
MiaoJWangZNingXShankarAMapleCRodriguesJJ. A UAV-assisted authentication protocol for internet of vehicles. IEEE Trans Intell Transportation Syst (2024) 25(8):10286–97. 10.1109/tits.2024.3360251
42.
KerracheCARatheeGLahbyMVegniAMBilalMFerragMA. A secure and transparent communication mechanism based on blockchain and fuzzy evaluation matrix in metaverse industry 4.0. Inf Security J A Glob Perspective (2024) 1–12. 10.1080/19393555.2024.2353067
Summary
Keywords
internet of things, security, signature-based, logistics management systems, authentication
Citation
Zhang Z, Liu X, Gong L and Zhuang Z (2025) A signature-based secure interaction scheme for logistics management systems in the internet of things. Front. Phys. 13:1540716. doi: 10.3389/fphy.2025.1540716
Received
06 December 2024
Accepted
20 March 2025
Published
23 April 2025
Volume
13 - 2025
Edited by
Gaogao Dong, Jiangsu University, China
Reviewed by
Chaker Abdelaziz Kerrache, University of Ghardaia, Algeria
Abdelkarim Ben Sada, University College Cork, Ireland
Updates
Copyright
© 2025 Zhang, Liu, Gong and Zhuang.
This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Zhenbo Zhang, zhenbozhang17@outlook.com
Disclaimer
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.