- 1School of Computer Science and Technology, Changsha University of Science and Technology, Changsha, China
- 2School of Information Engineering, Changsha Medical University, Changsha, China
With the rapid development of information technology, the demand for ensuring data security and privacy protection has become increasingly urgent. The purpose of this study is to address the limitations of existing image encryption methods and develop a more secure and efficient image encryption scheme. To achieve this, we adopt a research method that involves constructing a new type of discrete memristor hyperchaotic map by coupling an upgraded cosine discrete memristor with the Cubic map, and then conducting in-depth analysis of the system’s dynamic characteristics using phase diagrams, Lyapunov exponential spectra, and bifurcation diagrams to confirm its ability to reach a hyperchaotic state. Based on this hyperchaotic map, we propose a new image encryption scheme, generating high-quality chaotic sequences through its excellent chaotic characteristics to effectively scramble and diffuse image data, and also introducing a novel forward and reverse diffusion strategy in the diffusion process to enhance encryption efficiency. Through experiments on various images, we verify the algorithm’s effectiveness in improving encryption strength, reducing information leakage risks, and ensuring data security. Finally, the results of keyspace analysis, histogram analysis, correlation analysis, and information entropy demonstrate that the scheme has high security and practicability, along with good application prospects and practical value.
1 Introduction
Chaos is a non-linear kinematic system widely used in the biological and social sciences of nature [1–5]. The application of chaotic systems due to their randomness, unpredictability, and initial state sensitivity brings many advantages [6–10], and hyperchaotic systems further extend this complexity [11–14]. Hyperchaotic systems are oscillators with two positive Lyapunov exponents, but chaotic systems have only one, so hyperchaotic systems have more complex dynamical behaviors than general chaotic systems [15–18]. In a continuous system, at least four dimensions or more are required to produce hyperchaos, while in discrete systems, it is possible to produce a hyperchaotic state in two dimensions and have abundant dynamic behaviors [19, 20]. Mostafaee et al. proposed a novel exponential hyperchaotic system with complex dynamics and analyzed the dynamic behaviors of chaotic attractors, bifurcation graphs, and equilibrium points [21].
Based on the principle of symmetry and completeness of circuit variables, Chua proposed a mathematical model to describe the relationship between charge and magnetic flux, namely, a memristor [22]. As a non-linear resistive element, memristor can adjust the resistance or conductance value through charge or magnetic flux due to its small size and low power consumption [23, 24], and its unique non-linear electrical transport characteristics similar to neural synapses have attracted much attention in many fields [25–28]. In addition, memristors are widely used in chaotic systems to improve nonlinear dynamic behavior [4, 29–31]. It should be noted that most of the research on memristive chaotic systems is limited to the continuous-time domain [32–36], but the common application of continuous memristors will lead to problems such as high computational cost and poor controllability, so the concept of discrete memristors is introduced. In addition, discrete maps have simpler iterative equations and higher computational efficiency than continuous systems [37–41].
Discrete memristor-fusion chaos mapping can generate rich dynamic behaviors such as hyperhybrid and coexisting attractors [42–45], and can also enhance sequence complexity and chaos range [46–48]. Pan et al. [49] proposed a discrete memristor model based on difference theory, describing in detail the process of constructing a discrete memristor by difference theory. Peng et al. [50] established a Simulink model of discrete memristor chaos mapping and verified the feasibility of discrete memristors. Liu et al. [38] reported a discrete two-dimensional memristive map and observed the coexistence of its hidden attractors. Bao et al. [51] reported a new two-dimensional discrete memristive hyperchaotic map.
With the continuous advancement of image encryption technology, researchers have found that it is difficult to improve image encryption with a single chaotic system [52, 53]. In order to ensure people’s privacy, Banu S et al. studied traditional encryption algorithms such as AES, RSA, and DES [54], but this algorithm is more suitable for text message encryption. Therefore, it is necessary to develop an efficient encryption scheme to solve the security problem of image encryption [55]. Researchers have investigated a variety of image encryption schemes, such as the application of chaos theory [56], optical methods [57], and compressive sensing [58] to image encryption algorithms. Among them, the characteristics of chaos theory are extremely consistent with the requirements of image encryption schemes, which also promotes the development of chaotic digital image encryption. An image encryption scheme based on double chaotic cyclic shift and Joseph’s problem uses the complexity and unpredictability of chaotic systems to enhance the encryption effect. Xu et al. proposed a fast image encryption algorithm based on compressed sensing and hyperchaotic map [59], which uses the sparse representation of compressed sensing and the randomness of chaotic map to realize image encryption and decryption. Chen et al. proposed an optical multiimage encryption method based on multiplane phase retrieval and interference [60], which significantly enhances encryption security and robustness of encryption through the complexity and unpredictability of optical components. However, when applied to image encryption, the image encryption algorithm is inefficient due to weaknesses such as discontinuous chaotic regions and narrow chaotic ranges of the chaotic map [61, 62]. In short, the structural defects of the image encryption algorithms and the low performance of chaos theory will lead to the inefficiency of the encryption algorithms, and it is difficult to resist ordinary security attacks.
With the rapid development of information technology, data security and privacy protection are confronted with unprecedented challenges. Traditional image encryption technologies are gradually showing their limitations when dealing with complex and changeable security threats, and there is an urgent need to explore more efficient and secure encryption solutions. In this context, this paper conducts in-depth research and achieves a series of innovative results. Firstly, a new two-dimensional hyperchaotic map is proposed. By skillfully combining the classical cubic map with the improved cosine discrete memristor, a new discrete memristive map is constructed, which provides new ideas for the research of chaotic systems. Secondly, the encryption method is innovated. The chaotic sequence generated by the new chaotic map is integrated into the encryption algorithm. Through operations such as index scrambling and forward and reverse diffusion of images, the image encryption process is optimized. Thirdly, the characteristics of the system are analyzed in multiple dimensions. By studying the parameter-dependent phase diagram, Lyapunov exponential spectrum, bifurcation diagram, and coexisting attractors, and verifying the pseudo-randomness, the chaotic characteristics of the system suitable for image encryption are revealed. Through simulation and analysis of the dynamic characteristics of the chaotic system, it is verified that the system is highly sensitive to parameters, thus providing a new approach for image encryption. Moreover, the chaotic sequence is incorporated into the encryption algorithm. Through operations like index scrambling and diffusion on images and security analysis, it is confirmed that the proposed scheme has extremely high security and anti-interference capabilities, indicating that the chaotic characteristics of the system possess great application value in the field of image encryption.
The general structure of this paper is as follows. Section 2 mainly introduces the Cubic map and the proposed discrete memristor, and then constructs the proposed discrete memristor hyperchaotic map and analyzes its performance; Section 3 shows the rich dynamics of a new discrete memristive hyperchaotic map; Section 4 details the image encryption algorithm; Section 5 summarizes the work of this paper and illustrates the prospects for future research directions.
2 Design of a new discrete hyperchaotic map model
2.1 Mathematical model of discrete hyperchaotic map
Discrete hyperchaotic map is a unique dynamic system, and the key point is to improve the complexity and security of the system with the help of high-dimensional chaos characteristics. Based on the Cubic map, a new discrete hyperchaotic map model can be constructed. Memristors, as the fourth fundamental circuit element, relate charge to magnetic flux and possess unique memory characteristics. In this paper, a cosine-type discrete memristor is proposed, in which the relationship between current and voltage and the relationship between internal charge variables is described as Equation 1:
where
Adding the power supply
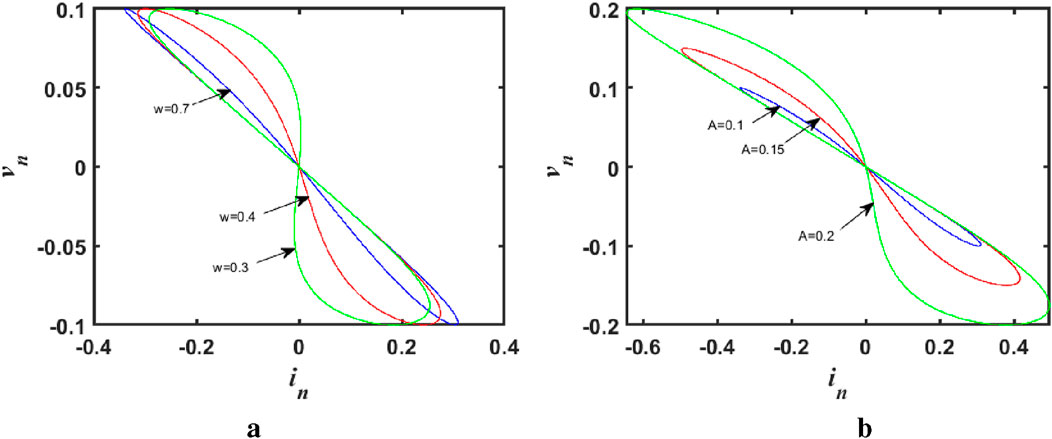
Figure 1. Properties of discrete memristors when
Through the analysis of numerical simulation, the trajectory distribution and dynamic behavior characteristics of the model can be clearly observed under different initial conditions. It can be seen that the discrete hyperchaotic map not only opens up a new perspective for the research of chaos theory, but also lays a solid theoretical foundation for practical application in related fields.
2.2 Application of discrete memristor in hyperchaotic map
Compared with traditional chaotic maps, discrete hyperchaotic maps exhibit richer dynamic characteristics in parameter space, including irregular periodicity and extreme sensitivity to initial conditions [46]. In the hyperchaotic mapping system, the memristor interacts with other maps. The nonlinear characteristics of the memristor will be coupled with the characteristics of other components, thus generating more complex nonlinear dynamic behaviors, so as to improve the complexity and robustness of their chaotic behavior.
The cubic map is a discrete chaotic map with a simple structure. Its iterative equation is shown in Equation 3:
By introducing the memristor model (Equation 2) into the Cubic map, a new two-dimensional discrete memristive chaotic system can be obtained:
When the parameters are
where
3 Construction and dynamic analysis of a new discrete hyperchaotic map
3.1 Fixed point
In the study of chaotic systems, an immobile point is one of the important features of a dynamical system, denoting a state that remains unchanged during the evolution of the system. For a new type of discrete hyperchaotic map, it is of great theoretical and practical significance to determine the location and properties of its fixed points. The fixed point of 2D-DMC is the solution to Equation 5.
From Equation 5, it follows that 2D-DMC has infinite fixed points, which can be expressed as
It can be seen that the eigenvalue
The properties of these fixed points determine the complexity of hyperchaotic maps and their potential applications in image encryption. Further studies show that appropriate initial values and parameters can make fixed points exhibit rich dynamic behaviors, thus enhancing the security of chaotic systems.
In general, the study of fixed points provides an important theoretical basis for the application of new discrete hyperchaotic maps. Through in-depth analysis of the properties of fixed points, we can understand the behavior characteristics of chaotic systems and provide valuable guidance for the design and implementation of image encryption algorithms.
3.2 Parametric bifurcation graphs and lyapunov exponents
In the dynamic analysis, the chaotic characteristics of the model can be evaluated by using tools such as the Lyapunov exponent and the bifurcation diagram. In order to explore the sensitivity of the system to different parameters, the dynamic behavior of the system is analyzed in detail by a bifurcation diagram and the Lyapunov exponential spectrum.
(1) The influence of the parameter
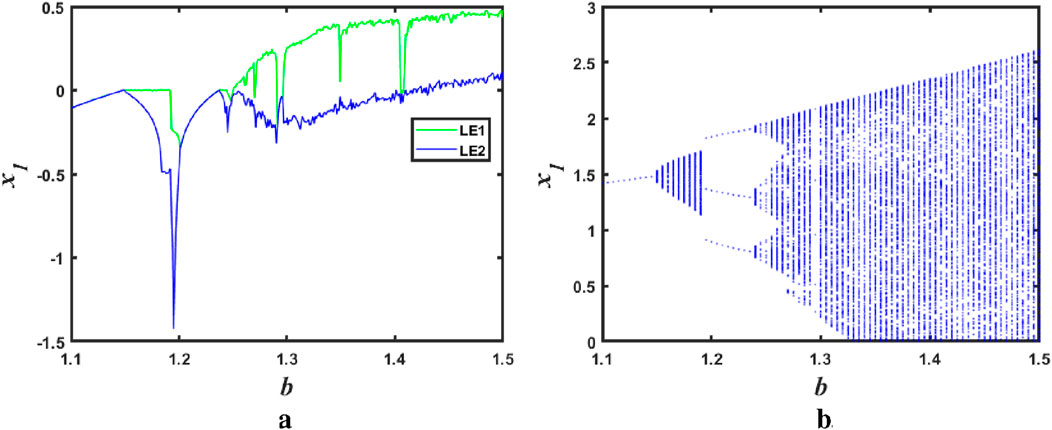
Figure 3. The Lyapunov exponent spectrum and bifurcation diagram of
As can be seen in the figure, when the parameter
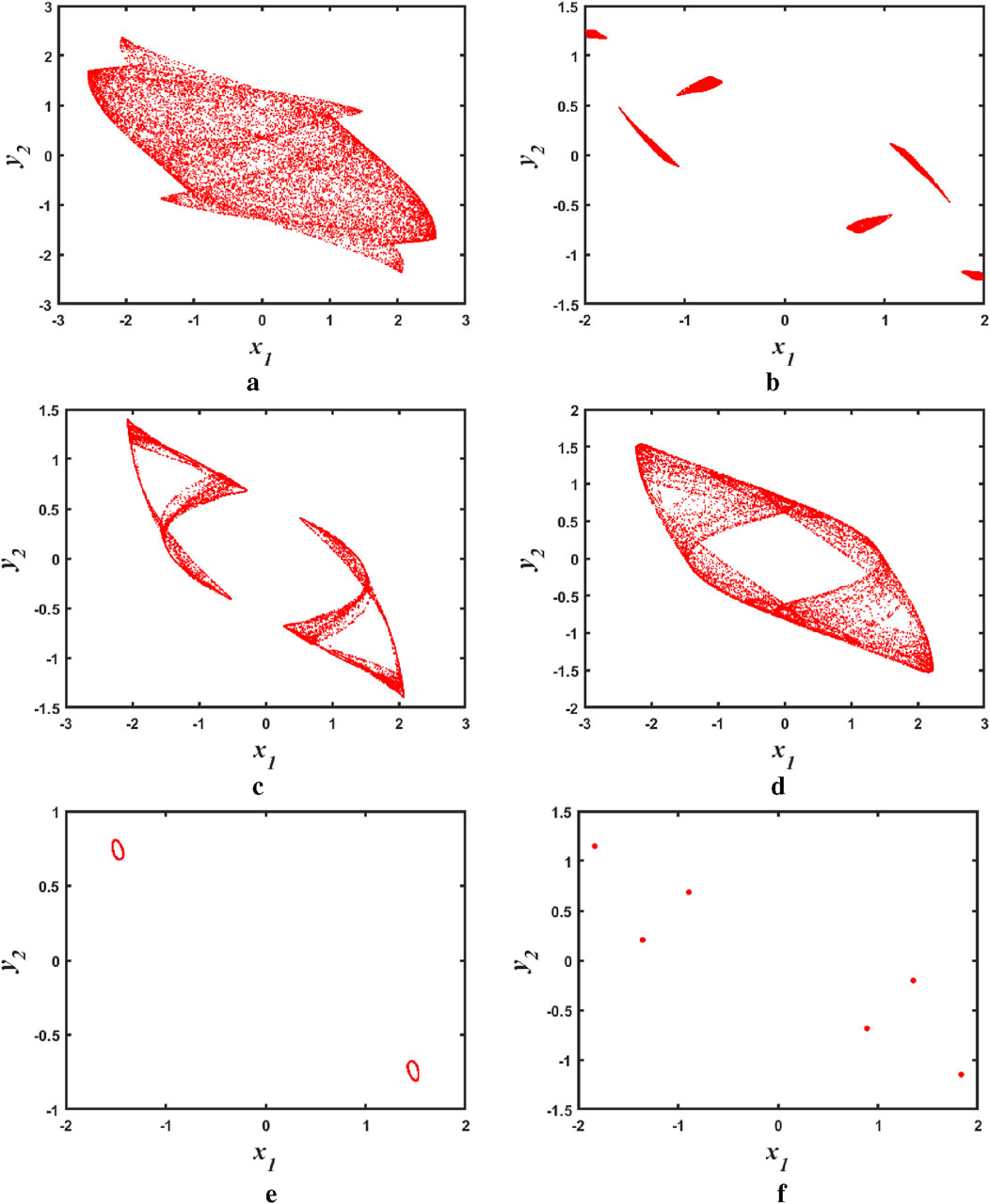
Figure 4. Phase diagram of a discrete memristive chaotic system as a function of parameter
(2) Impact of the parameter
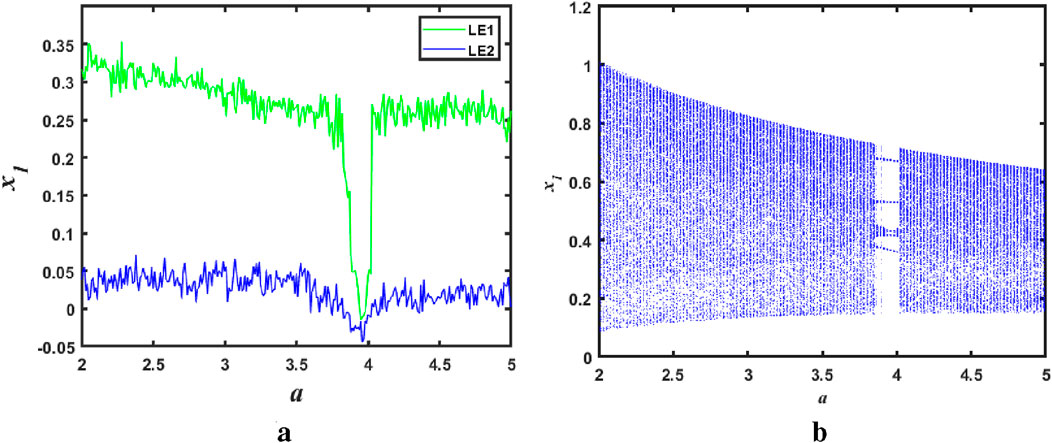
Figure 5. The Lyapunov exponent spectrum and bifurcation diagram of
As can be seen in Figure 5, when
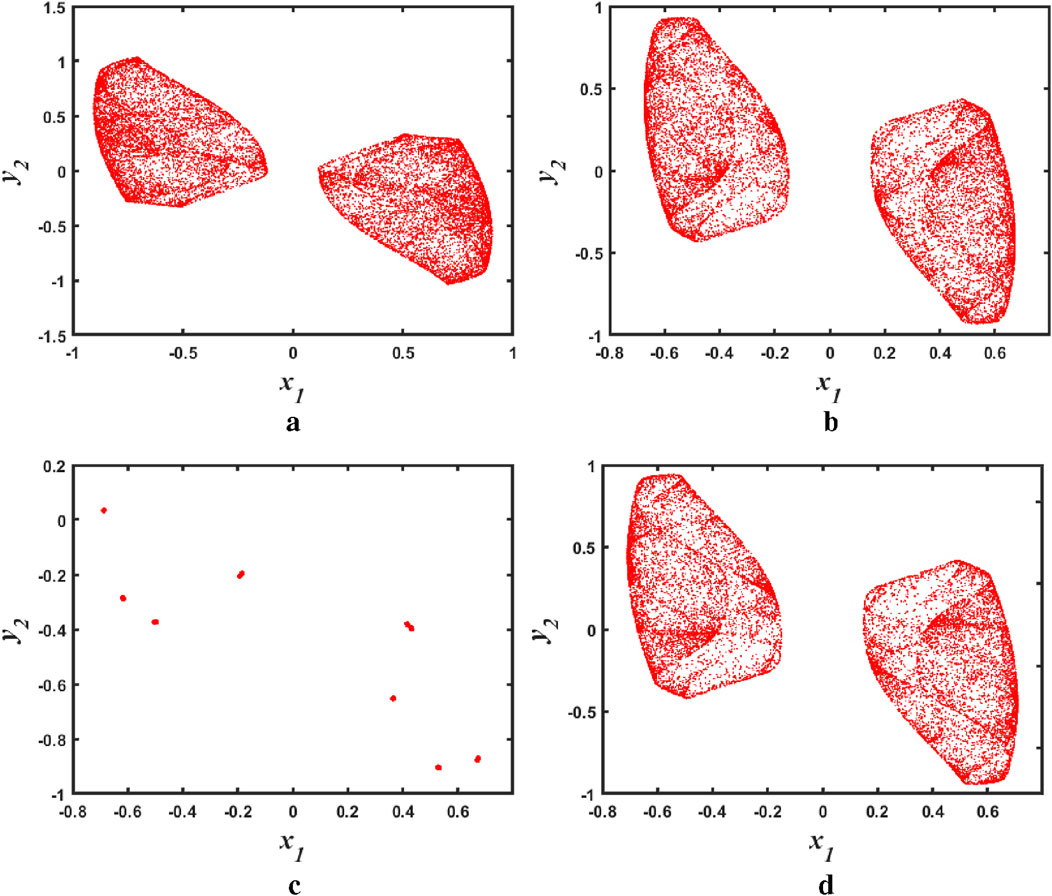
Figure 6. Phase diagram of a discrete memristive chaotic system as a function of parameter
(3) The influence of the parameter
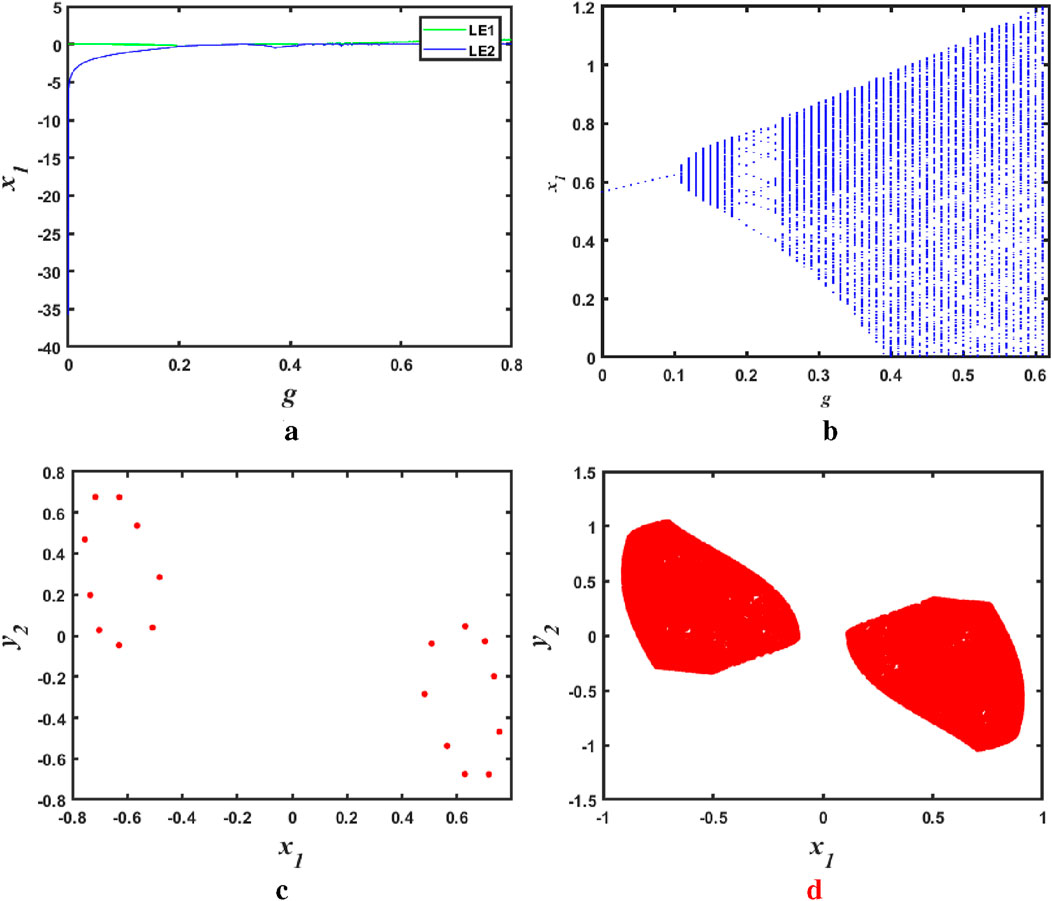
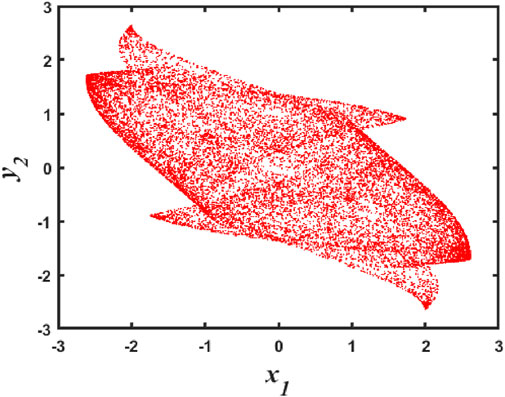
Figure 7. The Lyapunov exponent spectrum, bifurcation diagram and phase diagram of
When parameters
The discrete memristive chaotic attractors corresponding to the different parameter values
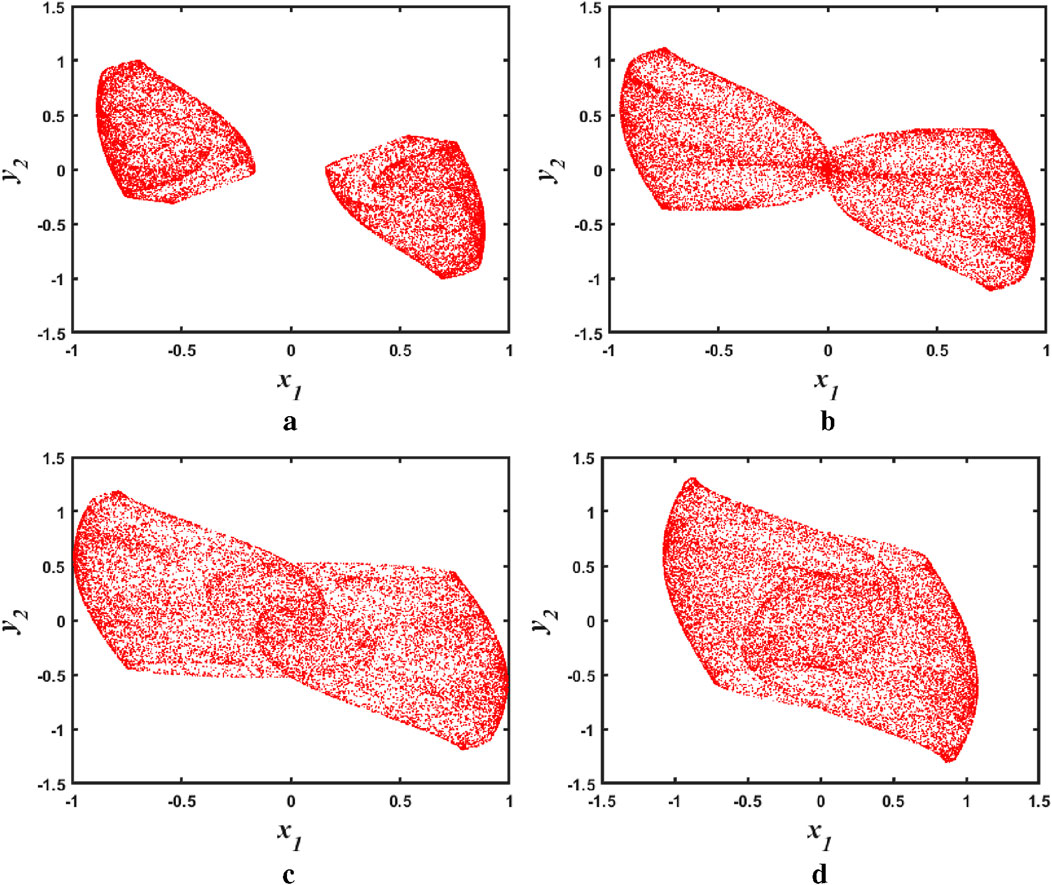
Figure 8. Phase diagram of
3.3 Random analysis
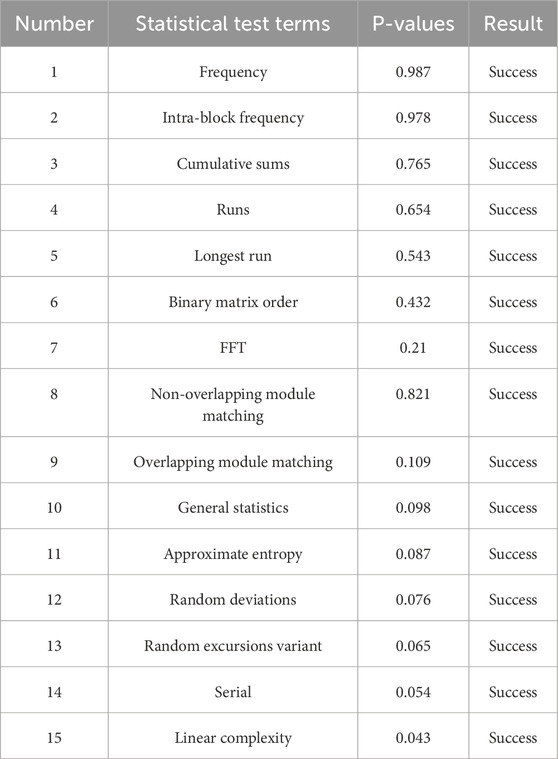
Discrete memristive hyperchaoticmap has been widely used to improve the credibility of data analysis, random number generation, and encrypted communication. In these areas, randomness is a critical requirement, as the resulting chaotic sequences that do not have sufficient randomness can easily be cracked or predicted, compromising the security of the application. Through the randomness test, the randomness and safety of chaotic sequences generated by the discrete memristive hyperchaotic map can be evaluated. To test the randomness of chaotic sequences, we performed two statistical tests, NIST and 0-1. NIST tests are a series of standardized tests that are used to evaluate and verify the security of random number generators and cryptographic algorithms to check whether the generated data are random. The test results are shown in Table 1, from which it can be found that all P values are greater than 0.01, indicating that the key system has successfully passed the test and the generated data have sufficient security and randomness.
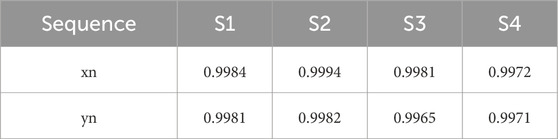
The “0-1 test” generally refers to a statistical test performed on a random number or chaotic sequence, mainly to evaluate whether the resulting sequence is sufficiently random to meet specific statistical requirements and application needs. Firstly, a chaotic sequence with a duration of more than 2000 was randomly selected, and the values were selected at a certain step interval for testing, and the test results are shown in Table 2. As you can see from the results in the table, the test result value is close to 1. This indicates that the discrete memristive hyperchaotic map exhibits a high degree of randomness.
Based on the results shown in Tables 1, 2, it can be concluded that the key system derived from the discrete memristive hyperchaos map has excellent randomness. Chaotic randomness testing is of great significance in application security, data analysis, and simulation, which can ensure the security of the application and meet the security and reliability requirements required for image encryption.
4 Design and implementation of image encryption algorithm
4.1 An image encryption scheme based on hyperchaotic map
In this section, a novel image encryption scheme based on a two-dimensional hyperchaotic map based on cyclic shift, forward and reverse diffusion, and global displacement is introduced. By combining key steps such as pixel diffusion and displacement, hyperchaotic sequences are used to reorder the pixel positions of the original image and disrupt the overall structure of the image. On the one hand, the displacement process ensures randomness, while diffusion further enhances the complexity of image encryption. The processed chaotic sequence and pixel value are used to perform XOR operations to further improve the encryption strength and reduce the risk of information leakage. The steps are as follows:
1. Select the original image and perform channel separation, and select a grayscale image of
2. Generate m
3. Based on the chaotic characteristics of the hyperchaotic sequences
The image encryption algorithm of the new discrete memristive chaotic system provides a secure and powerful encryption scheme for grayscale image encryption. In the encryption stage, the plaintext image undergoes cyclic shift, forward and reverse diffusion, and global substitution operations, combined with the dynamic key generated by the chaotic system, and finally generates an irreversible ciphertext image,as shown in Figure 9a. During decryption, global substitution, forward and reverse diffusion, and cyclic shift are performed in reverse, and the original pixel value and position are restored by the same chaos key to achieve lossless decryption,as shown in Figure 9b.
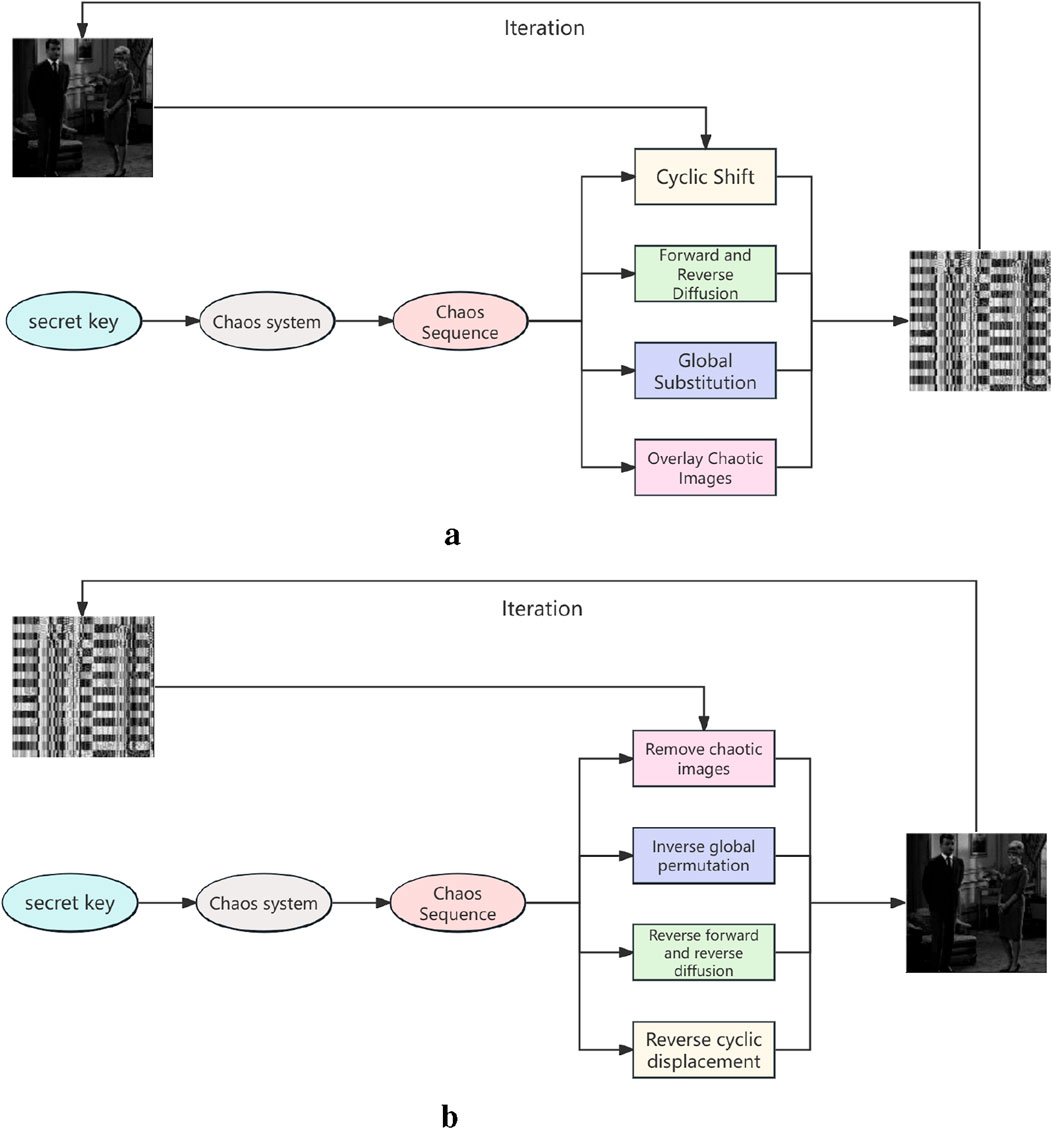
Figure 9. Encryption and decryption process diagram. (a) Encryption Flow Diagram. (b) Decryption Process Diagram.
4.2 Performance analysis of encryption algorithms
In image encryption algorithms, the size of the key space directly determines the security of the encryption. To verify the feasibility and effectiveness of the proposed algorithm, simulation tests were performed using Matlab 2023b, with the key set as

Figure 10. Encryption and decryption effects of images. (a) Plaintext image. (b) Encryption-image. (c) Decryption-image. (d) Plaintext image. (e) Encryption-image. (f) Decryption-image. (g) Plaintext image. (h) Encryption-image. (i) Decryption-image.
4.2.1 Key space analysis
In image encryption algorithms, the size of the key space directly determines the security of the encryption. Studies have shown that the larger the key space, the more difficult it is for attackers to crack. It is generally accepted that the size of the key space should be greater than 2,128 [45] to ensure security. The keys of IES-CTG are
where
Brute-force attack refers to the situation where an attacker tries all possible key combinations until the correct key for decrypting the information is found. The size of the key space determines the number of possible key combinations. The larger the key space, the more difficult it is for the attacker to find the correct key through brute-force attempts. The key space designed for the novel discrete hyperchaotic map is
4.2.2 Histogram analysis
In image encryption, histogram analysis is an important method to evaluate the encryption effect [63]. Figures 11a, c, e are the original images, and their corresponding image histograms are shown in Figures 11b, d, f, and their pixel value distribution can be visually seen. By comparing the encrypted histograms, as shown in Figures 11g, i, k, it can be observed that the encrypted image histograms should show more uniform distribution characteristics. The histogram of the decrypted image is obtained by the decryption algorithm as shown in Figures 11h, j, l. This balance indicates that confusing and dispersing the pixel information of the original image reduces its recognizability and improves security. That is, the attacker cannot obtain the histogram information of the plaintext image by statistically analyzing the histogram of the ciphertext image, indicating that the proposed algorithm has good diffusion and resistance to statistical attacks.
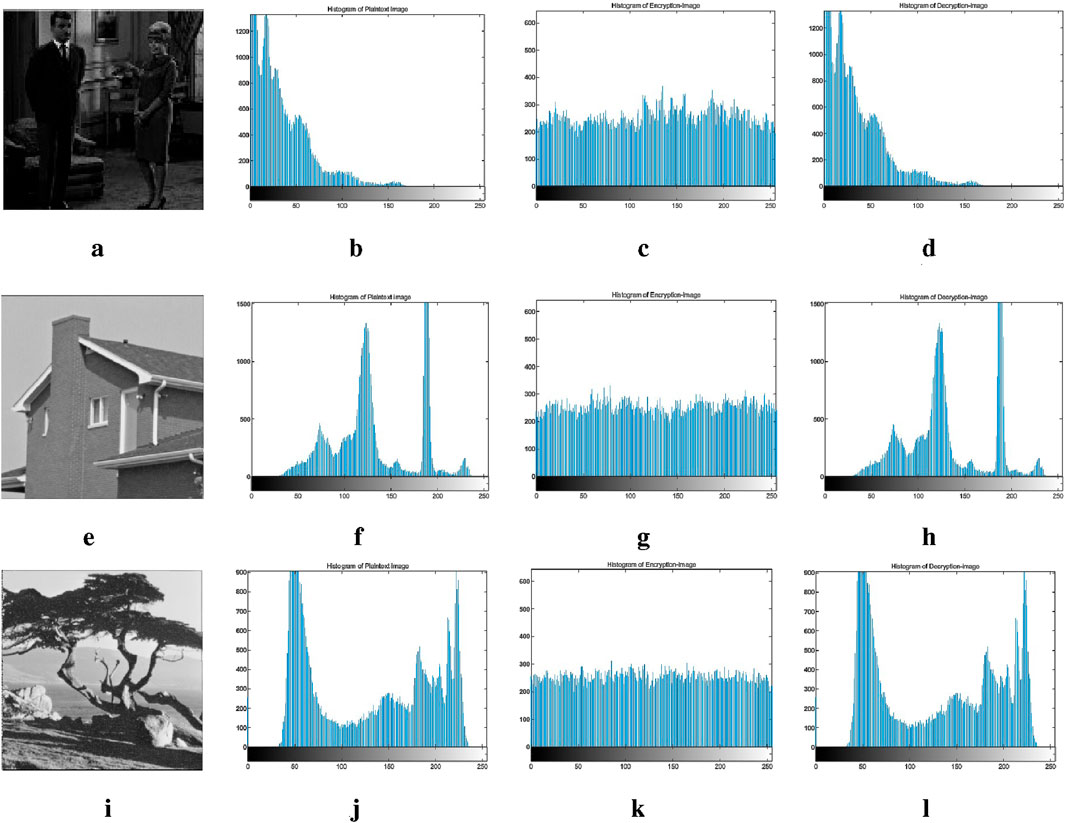
Figure 11. Histograms of plaintext and ciphertext images. (a) Plaintext-image. (b) Histogram of Plaintext-image. (c) Histogram of Encryption-image. (d) Histogram of Decryption-image. (e) Plaintext-image. (f) Histogram of Plaintext-image. (g) Histogram of Encryption-image. (h) Histogram of Decryption-image. (i) Plaintext image. (j) Histogram of Plaintext image. (k) Histogram of Encryption-image. (l) Histogram of Decryption-image.
The entropy of the histogram is also a key indicator to evaluate the effectiveness of image encryption. The higher the entropy value, the higher the complexity of the encrypted image information and the stronger the ability to resist various attacks, as shown in Figures 11d, h, i. In this study, the encrypted image generated by the new discrete hyperchaotic map has a high histogram entropy value, which shows the effectiveness and security of the encryption algorithm in practical applications.
4.2.3 Relevance analysis
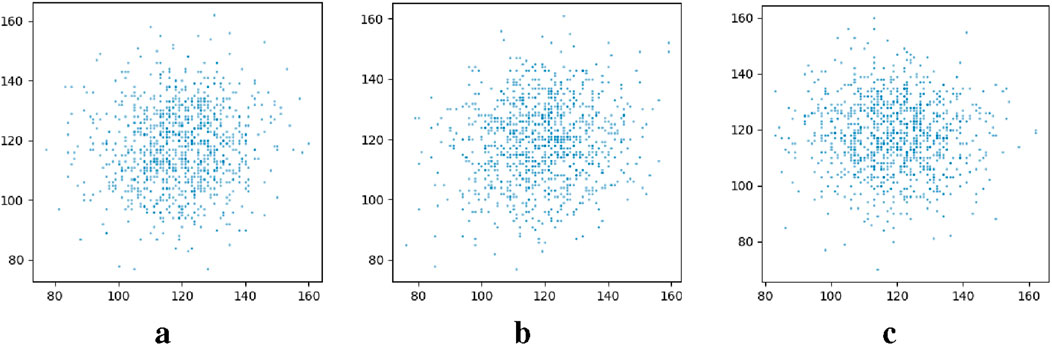
In the design and implementation of image encryption algorithms, correlation analysis is an important performance index. Low correlation means that there is almost no linear or non-linear relationship between the pixel values of the encrypted image, which effectively increases the difficulty of cracking. In order to evaluate the performance of the new discrete hyperchaotic map proposed in the process of image encryption, it is necessary to analyze the correlation of the images before and after encryption. Figures 12, 13 illustrate the correlation between the adjacent pixels of the plaintext image before image encryption and the ciphertext image after encryption, respectively.
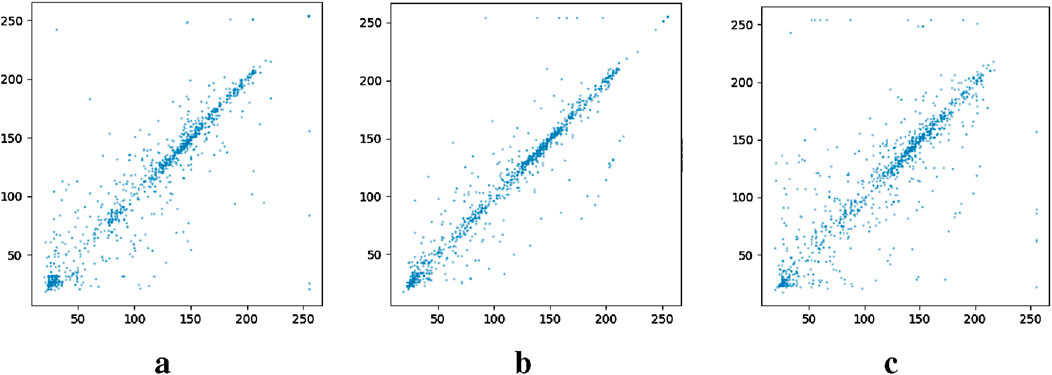
Figure 12. Correlation between adjacent pixels in a plaintext image. (a) Horizontal. (b) Vertical. (c) Diagonal.
The image is very strong, as shown in Figures 12a–c, and there is usually a correlation close to 1; However, the correlation between adjacent pixels in a ciphertext image is close to zero, as shown in Figures 13a–c. For different test images, different chaotic sequences are used for encryption, and the correlation difference between the encryption results can be observed, which further verifies the randomness of the new discrete hyperchaotic map, thus improving the security of the encrypted images.
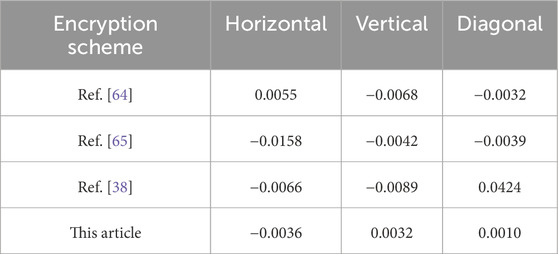
As can be seen from the correlation coefficient of the ciphertext image in Table 3, the correlation between adjacent pixels in the ciphertext image is close to 0, and they are almost uncorrelated. The experimental results show that the designed image encryption algorithm maintains a high encryption strength under the condition of low correlation. Compared with traditional chaotic encryption algorithms, this novel discrete hyperchaotic mapping effectively reduces the correlation between different pixels, thereby enhancing the security of the encrypted image. When compared with more advanced chaotic encryption algorithms, this algorithm also has obvious advantages in terms of processing speed. It can complete the encryption and decryption processes of images more rapidly. Moreover, when facing common attack methods such as differential attacks and statistical attacks, it demonstrates stronger attack resistance, providing a more reliable guarantee for the security of image data.
4.2.4 Information entropy analysis
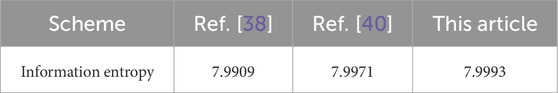
Information entropy is a basic concept of information theory. It is an important index for measuring the randomness and uncertainty of information. Generally, it is around 8.0, indicating that the encrypted image has good randomness in the pixel intensity distribution. In this study, a new encryption algorithm based on a discrete hyperchaotic map is used to compare the entropy of the original image and the encrypted image. It can be seen from Table 4 that after IES - CTG encryption processing, the information entropy of the ciphertext image is very close to the ideal value of 8, and compared to some existing schemes, it has certain advantages.
Furthermore, the variation law of the information entropy under different chaotic parameters is analyzed, and the information entropy performance of the encryption results is affected by adjusting the parameters of the chaotic system. Under the corresponding parameter settings, the increase in the entropy value shows significant sensitivity, which further verifies the effectiveness of chaos characteristics in enhancing the security of image encryption.
5 Conclusion
In this paper, we conduct in-depth research and discussion on a new type of discrete hyperchaotic map and its application in image encryption. By designing and analyzing a novel discrete hyperchaotic map model, we not only clarify its dynamic characteristics, but also reveal its advantages in generating high-quality chaotic sequences. Then, an image encryption algorithm based on a novel discrete hyperchaotic map design is implemented on the MATLAB platform. The key is used to scramble and diffuse the digital image to be encrypted at the pixel level to improve the security of the image. The experimental results show that the proposed encryption algorithm has significant performance advantages. By comparing images with different encryption effects, the security of encrypted images was evaluated using methods such as histogram analysis, information entropy calculation, and adjacent pixel correlation detection. The experimental results show that the encrypted image presents a good degree of visual chaos and the information entropy value is significantly improved, indicating that its security is better than that of traditional image encryption methods.
The new discrete hyperchaotic map and its application in image encryption have important theoretical value and practical significance. Future research can further explore the application potential of other chaos map models in different information security fields, to promote the progress and innovation of overall information encryption technology.
Data availability statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Author contributions
FY: Supervision, Writing – review and editing, Project administration, Resources, Writing – original draft. YW: Conceptualization, Data curation, Formal Analysis, Methodology, Software, Writing – original draft, Writing – review and editing. XW: Formal Analysis, Software, Validation, Writing – original draft. TH: Investigation, Supervision, Validation, Writing – original draft. SZ: Software, Supervision, Writing – original draft. JJ: Funding acquisition, Supervision, Writing – review and editing.
Funding
The author(s) declare that financial support was received for the research and/or publication of this article. This work was supported by National Natural Science Foundation of China under Grant 62273141, and by the Guiding Science and Technology Plan Project of Changsha City under Grant kzd2501129.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Generative AI statement
The authors declare that no Generative AI was used in the creation of this manuscript.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Deng Q, Wang C, Yang Q. Chaotic dynamics of memristor-coupled tabu learning neuronal network. International Journal of Bifurcation and Chaos (2025) 35:2550053. doi:10.1142/S0218127425500531
2. Yuan Y, Yu F, Tan B, Huang Y, Yao W, Cai S, et al. A class of n-d Hamiltonian conservative chaotic systems with three-terminal memristor: modeling, dynamical analysis, and fpga implementation. Chaos (2025) 35:013121. doi:10.1063/5.0238893
3. Gao S, Zhang Z, Iu HHC, Ding S, Mou J, Erkan U, et al. A parallel color image encryption algorithm based on a 2d logistic-rulkov neuron map. IEEE Internet Things J (2025) 1. doi:10.1109/JIOT.2025.3540097
4. Yu F, Wu C, Xu S, Yao W, Xu C, Cai S, Wang C. Color video encryption transmission in IoT based on memristive hopfield neural network. Signal, Image and Video Processing (2025) 19:77. doi:10.1007/s11760-024-03697-x
5. Jin J, Wu M, Ouyang A, Li K, Chen C. A novel dynamic hill cipher and its applications on medical iot. IEEE Internet Things J (2025) 12:14297–308. doi:10.1109/JIOT.2025.3525623
6. Yuan Z, Wu Y, Ou C, Zhong P, Zhao X, Ma M. Dynamical behavior of sw-sw neural networks. Chin J Phys (2025) 94:108–20. doi:10.1016/j.cjph.2024.12.031
7. Luo D, Wang C, Deng Q, Sun Y. Dynamics in a memristive neural network with three discrete heterogeneous neurons and its application. Nonlinear Dyn (2025) 113:5811–24. doi:10.1007/s11071-024-10513-1
8. Hua C, Cao X, Liao B. Real-time solutions for dynamic complex matrix inversion and chaotic control using ode-based neural computing methods. Comput Intelligence (2025) 41:e70042. doi:10.1111/coin.70042
9. Yu F, Zhang S, Su D, Wu Y, Gracia YM, Yin H. Dynamic analysis and implementation of fpga for a new 4d fractional-order memristive hopfield neural network. Fractal and Fractional (2025) 9:115. doi:10.3390/fractalfract9020115
10. Deng Q, Wang C, Sun Y, Yang G. Memristive multi-wing chaotic hopfield neural network for lidar data security. Nonlinear Dyn (2025) 113:17161–76. doi:10.1007/s11071-025-10982-y
11. Feng W, Zhang J, Chen Y, Qin Z, Zhang Y, Ahmad M, et al. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst Appl (2024) 246:123190. doi:10.1016/j.eswa.2024.123190
12. Lai Q, Yang L, Chen G. Design and performance analysis of discrete memristive hyperchaotic systems with stuffed cube attractors and ultraboosting behaviors. IEEE Trans Ind Electronics (2024) 71:7819–28. doi:10.1109/tie.2023.3299016
13. Liu X, Mou J, Zhang Y, Cao Y. A new hyperchaotic map based on discrete memristor and meminductor: dynamics analysis, encryption application, and dsp implementation. IEEE Trans Ind Electronics (2023) 71:5094–104. doi:10.1109/tie.2023.3281687
14. Yu F, Tan B, He T, He S, Huang Y, Cai S, et al. A wide-range adjustable conservative memristive hyperchaotic system with transient quasi-periodic characteristics and encryption application. Mathematics (2025) 13:726. doi:10.3390/math13050726
15. Chen L, Yu M, Luo J, Mi J, Shi K, Tang S. Dynamic analysis and fpga implementation of a new linear memristor-based hyperchaotic system with strong complexity. Mathematics (2024) 12:1891. doi:10.3390/math12121891
16. Ma X, Wang Z, Wang C. An image encryption algorithm based on tabu search and hyperchaos. Int J Bifurcation Chaos (2024) 34:2450170. doi:10.1142/s0218127424501700
17. Zhu S, Deng X, Zhang W, Zhu C. Construction of a new 2d hyperchaotic map with application in efficient pseudo-random number generator design and color image encryption. Mathematics (2023) 11:3171. doi:10.3390/math11143171
18. Yu F, Xu S, Xiao X, Yao W, Huang Y, Cai S, et al. Dynamics analysis, fpga realization and image encryption application of a 5d memristive exponential hyperchaotic system. Integration (2023) 90:58–70. doi:10.1016/j.vlsi.2023.01.006
19. Hua Z, Zhou Y, Bao B. Two-dimensional sine chaotification system with hardware implementation. IEEE Trans Ind Inform (2019) 16:887–97. doi:10.1109/tii.2019.2923553
20. Feng W, Wang Q, Liu H, Ren Y, Zhang J, Zhang S, et al. Exploiting newly designed fractional-order 3d lorenz chaotic system and 2d discrete polynomial hyper-chaotic map for high-performance multi-image encryption. Fractal and Fractional (2023) 7:887. doi:10.3390/fractalfract7120887
21. Mostafaee J, Mobayen S, Vaseghi B, Vahedi M, Fekih A. Complex dynamical behaviors of a novel exponential hyper–chaotic system and its application in fast synchronization and color image encryption. Sci Prog (2021) 104:00368504211003388. doi:10.1177/00368504211003388
22. Liu J, Li Z, Tang Y, Hu W, Wu J. 3d convolutional neural network based on memristor for video recognition. Pattern Recognition Lett (2020) 130:116–24. doi:10.1016/j.patrec.2018.12.005
23. Hong Q, Jiang H, Xiao P, Du S, Li T. A parallel computing scheme utilizing memristor crossbars for fast corner detection and rotation invariance in the orb algorithm. IEEE Trans Comput (2025) 74:996–1010. doi:10.1109/tc.2024.3504817
24. Yu F, He S, Yao W, Cai S, Xu Q. Bursting firings in memristive hopffeld neural network with image encryption and hardware implementation. IEEE Trans Computer-Aided Des Integrated Circuits Syst (2025) 1–13. doi:10.1109/TCAD.2025.3567878
25. Zhang S, Yao W, Xiong L, Wang Y, Tang L, Zhang X, et al. A hindmarsh–rose neuron model with electromagnetic radiation control for the mechanical optimization design. Chaos, Solitons and Fractals (2024) 187:115408. doi:10.1016/j.chaos.2024.115408
26. Sun J, Zhai Y, Liu P, Wang Y. Memristor-based neural network circuit of associative memory with overshadowing and emotion congruent effect. IEEE Trans Neural Networks Learn Syst (2024) 36:3618–30. doi:10.1109/TNNLS.2023.3348553
27. Xu Q, Fang Y, Feng C, Parastesh F, Chen M, Wang N. Firing activity in an n-type locally active memristor-based hodgkin–huxley circuit. Nonlinear Dyn (2024) 112:13451–64. doi:10.1007/s11071-024-09728-z
28. Peng Y, Li M, Li Z, Ma M, Wang M, He S. What is the impact of discrete memristor on the performance of neural network: a research on discrete memristor-based bp neural network. Neural Networks (2025) 185:107213. doi:10.1016/j.neunet.2025.107213
29. Yao W, Fang J, Yu F, Xiong L, Tang L, Zhang J, et al. Electromagnetic radiation control for nonlinear dynamics of hopfield neural networks. Chaos (2024) 34:073149. doi:10.1063/5.0194928
30. Deng W, Ma M. Analysis of the dynamical behavior of discrete memristor-coupled scale-free neural networks. Chin J Phys (2024) 91:966–76. doi:10.1016/j.cjph.2024.08.033
31. Xu Q, Ding X, Chen B, Parastesh F, Ho-Ching IH, Wang N. A universal configuration framework for mem-element-emulator-based bionic firing circuits. IEEE Trans Circuits Syst Regular Pap (2024) 71:4120–30. doi:10.1109/tcsi.2024.3428857
32. Lin H, Deng X, Yu F, Sun Y. Diversified butterfly attractors of memristive hnn with two memristive systems and application in iomt for privacy protection. IEEE Trans Computer-Aided Des Integrated Circuits Syst (2025) 44:304–16. doi:10.1109/tcad.2024.3429410
33. Hong Q, Xiao P, Fan R, Du S. Memristive neural network circuit design based on locally competitive algorithm for sparse coding application. Neurocomputing (2024) 578:127369. doi:10.1016/j.neucom.2024.127369
34. Gao S, Iu HHC, Erkan U, Simsek C, Toktas A, Cao Y, et al. A 3d memristive cubic map with dual discrete memristors: design, implementation, and application in image encryption. IEEE Trans Circuits Syst Video Technology (2025) 1. doi:10.1109/TCSVT.2025.3545868
35. Yu F, Su D, He S, Wu Y, Zhang S, Yin H. Resonant tunneling diode cellular neural network with memristor coupling and its application in police forensic digital image protection. Chin Phys B (2025) 34:050502. doi:10.1088/1674-1056/adb8bb
36. Wan Q, Yang Q, Liu T, Chen C, Shen K. Single direction, grid and spatial multi-scroll attractors in hopfield neural network with the variable number memristive self-connected synapses. Chaos, Solitons and Fractals (2024) 189:115584. doi:10.1016/j.chaos.2024.115584
37. Yu F, Xu S, Lin Y, Gracia YM, Yao W, Cai S. Dynamic analysis, image encryption application and fpga implementation of a discrete memristor-coupled neural network. Int J Bifurcation Chaos (2024) 34:2450068. doi:10.1142/s0218127424500688
38. Liu X, Sun K, Wang H, He S. A class of novel discrete memristive chaotic map. Chaos, Solitons and Fractals (2023) 174:113791. doi:10.1016/j.chaos.2023.113791
39. Tang Z, Zhang Y. Continuous and discrete gradient-zhang neuronet (gzn) with analyses for time-variant overdetermined linear equation system solving as well as mobile localization applications. Neurocomputing (2023) 561:126883. doi:10.1016/j.neucom.2023.126883
40. Demirtaş M. A novel multiple grayscale image encryption method based on 3d bit-scrambling and diffusion. Optik (2022) 266:169624. doi:10.1016/j.ijleo.2022.169624
41. Xiang Q, Gong H, Hua C. A new discrete-time denoising complex neurodynamics applied to dynamic complex generalized inverse matrices. The J Supercomputing (2025) 81:159–25. doi:10.1007/s11227-024-06601-z
42. Peng Y, He S, Sun K. A higher dimensional chaotic map with discrete memristor. AEU-International J Electronics Commun (2021) 129:153539. doi:10.1016/j.aeue.2020.153539
43. Liu X, Mou J, Yan H, Bi X. Memcapacitor-coupled Chebyshev hyperchaotic map. Int J Bifurcation Chaos (2022) 32:2250180. doi:10.1142/s0218127422501802
44. Wang C, Li Y, Deng Q. Discrete-time fractional-order local active memristor-based hopfield neural network and its fpga implementation. Chaos, Solitons and Fractals (2025) 193:116053. doi:10.1016/j.chaos.2025.116053
45. Di Marco M, Forti M, Pancioni L, Tesi A. New class of discrete-time memristor circuits: first integrals, coexisting attractors and bifurcations without parameters. Int J Bifurcation Chaos (2024) 34:2450001. doi:10.1142/s0218127424500019
46. Zhong H, Li G, Xu X. A generic voltage-controlled discrete memristor model and its application in chaotic map. Chaos, Solitons and Fractals (2022) 161:112389. doi:10.1016/j.chaos.2022.112389
47. Wang C, Luo D, Deng Q, Yang G. Dynamics analysis and fpga implementation of discrete memristive cellular neural network with heterogeneous activation functions. Chaos, Solitons and Fractals (2024) 187:115471. doi:10.1016/j.chaos.2024.115471
48. Hamadneh T, Abbes A, Al-Tarawneh H, Gharib GM, Salameh WMM, Al Soudi MS, et al. On chaos and complexity analysis for a new sine-based memristor map with commensurate and incommensurate fractional orders. Mathematics (2023) 11:4308. doi:10.3390/math11204308
49. Pan X. Research on discrete differential solution methods for derivatives of chaotic systems. AIMS Mathematics (2024) 9:33995–4012. doi:10.3934/math.20241621
50. Peng S, Shi H, Li R, Xiang Q, Dai S, Li Y. Simulink modeling and analysis of a three-dimensional discrete memristor map. Symmetry (2024) 16:990. doi:10.3390/sym16080990
51. Bao BC, Li H, Wu H, Zhang X, Chen M. Hyperchaos in a second-order discrete memristor-based map model. Electronics Lett (2020) 56:769–70. doi:10.1049/el.2020.1172
52. Zheng J, Luo Z, Tang Z. An image encryption algorithm based on multichaotic system and dna coding. Discrete Dyn Nat Soc (2020) 2020:1–16. doi:10.1155/2020/5982743
53. Lai Q, Lai C, Zhang H, Li C. Hidden coexisting hyperchaos of new memristive neuron model and its application in image encryption. Chaos, Solitons and Fractals (2022) 158:112017. doi:10.1016/j.chaos.2022.112017
54. Banu SA, Amirtharajan R. A robust medical image encryption in dual domain: chaos-dna-iwt combined approach. Med and Biol Eng and Comput (2020) 58:1445–58. doi:10.1007/s11517-020-02178-w
55. Li Y, You X, Lu J, Lou J. A joint image compression and encryption scheme based on a novel coupled map lattice system and dna operations. Front Inf Technology and Electron Eng (2023) 24:813–27.
56. Ahmad I, Shin S. A novel hybrid image encryption–compression scheme by combining chaos theory and number theory. Signal Processing: Image Commun (2021) 98:116418. doi:10.1016/j.image.2021.116418
57. Wei H, Wang X. Optical multiple-image authentication and encryption based on phase retrieval and interference with sparsity constraints. Opt and Laser Technology (2021) 142:107257. doi:10.1016/j.optlastec.2021.107257
58. Hua Z, Zhang K, Li Y, Zhou Y. Visually secure image encryption using adaptive-thresholding sparsification and parallel compressive sensing. Signal Process. (2021) 183:107998. doi:10.1016/j.sigpro.2021.107998
59. Xu Q, Sun K, Cao C, Zhu C. A fast image encryption algorithm based on compressive sensing and hyperchaotic map. Opt Lasers Eng (2019) 121:203–14. doi:10.1016/j.optlaseng.2019.04.011
60. Chen W, Chen X. Optical multiple-image encryption based on multiplane phase retrieval and interference. J Opt (2011) 13:115401. doi:10.1088/2040-8978/13/11/115401
61. Wei Z, Sixing X, Guilin W, Yonghong L, Qichang J. Multi-image optical encryption method of jtc system combining cgh and frequency shift. Infrared Laser Eng (2022) 51:20220175–1. doi:10.3788/irla20220175
62. Zhang B, Liu L. A novel fast image encryption algorithm based on coefficient independent coupled exponential chaotic map. Physica Scripta (2024) 99:025249. doi:10.1088/1402-4896/ad1fc3
63. Ning Y, Jin J, Li Z, Chen C, Ouyang A. A time-varying hill cipher for dynamic image cryptography. Tsinghua Sci Technology (2025). doi:10.26599/TST.2024.9010213
64. Wu X, Wang D, Kurths J, Kan H. A novel lossless color image encryption scheme using 2d dwt and 6d hyperchaotic system. Inf Sci (2016) 349:137–53. doi:10.1016/j.ins.2016.02.041
Keywords: discrete memristors, hyperchaotic map, dynamical analysis, image encryption, data security
Citation: Yu F, Wu Y, Wang X, He T, Zhang S and Jin J (2025) New discrete memristive hyperchaotic map: modeling, dynamic analysis, and application in image encryption. Front. Phys. 13:1617964. doi: 10.3389/fphy.2025.1617964
Received: 25 April 2025; Accepted: 12 May 2025;
Published: 05 June 2025.
Edited by:
Chunbiao Li, Nanjing University of Information Science and Technology, ChinaReviewed by:
Suo Gao, Harbin Institute of Technology, ChinaXinlei An, Lanzhou Jiaotong University, China
Copyright © 2025 Yu, Wu, Wang, He, Zhang and Jin. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Jie Jin, amo2NzEyM0BobnVzdC5lZHUuY24=
 Fei Yu
Fei Yu Yiya Wu1
Yiya Wu1 Jie Jin
Jie Jin