- 1School of Business and Tourism Management, Yunnan University, Kunming, China
- 2Management College, Ocean University of China, Qingdao, China
- 3School of Economics and Management, Beijing Normal University, Beijing, China
Information-sharing behavior is affected by identity recognition perception. The current study aims to delve into the impact of familiarity and anonymity on information-sharing behavior, and the mediating role of intrinsic motivations on WeChat Moments. We hypothesized a mediator role of intrinsic motivations in the relationship between an individual’s perceptions and information sharing. Based on the self-determination theory, a model was created and tested using a sample of 531 frequent users. In this study, these users were asked to use WeChat Moments, the most popular mobile private social networking site in China. The results demonstrate the significance of familiarity and identifiability in an interpersonal relationship, when using social networking sites. Moreover, the influence of perceived anonymity on information-sharing behavior, which is entirely mediated by intrinsic motivation has been validated from an empirical perspective. Our findings extend previous studies by showing the totally mediated effect of perceived anonymity on information-sharing behavior on WeChat Moments and the influential mechanism of intrinsic motivation. The results will inform researchers about the importance of incorporating the interpersonal structural features and intrinsic motivation of social networking sites into future studies on online information-sharing behavior. Important ways to promote attention and share information involve building a familiar relationship with communities and equipping oneself with off-line relations. Final indications for future developments are provided, with a special emphasis on the development of these findings in various social networking sites contexts.
Introduction
With social networking sites becoming more and more critical, individuals all over the world have integrated these sites into their daily practices (Lee and Ma, 2012; Cheung et al., 2015). Social networking sites, abbreviated SNSs, mainly has three functions: To improve the innovation ability of individuals and groups, to explore social behavior change, and to cultivate collective intelligence (Cachia et al., 2007), improving people’s lives, users with low self-esteem and life satisfaction benefit most from the use of SNS (Błachnio et al., 2016), which is positively related to friendship quality (Wang et al., 2014), and personal characteristics, attitudes, motivations, privacy concerns, and self-efficacy may predict the use of SNSs (Wang D. et al., 2015; Wang J.L. et al., 2015; Dienlin and Metzger, 2016; Chua and Chua, 2017).
A long line studies have explored factors that may influence one’s information disclosure on SNSs (Krasnova et al., 2012; Cheung et al., 2015; Shibchurn and Yan, 2015; Zhang and Ling, 2015; Chen et al., 2016; Dienlin and Metzger, 2016; Levontin and Yom-Tov, 2017; Lin and Utz, 2017). On different SNSs, users use different identity construction strategies to find a balance between the exposure and concealment of their real identity (Cunningham, 2013; Chen et al., 2016). Indeed, 81% of Internet users used strategies to protect their real identity, and the average anonymity seeker used between 3 and 4 of these strategies each time (Rainie et al., 2013). The more open the information sharing, the more a social networking site contributes to participatory social capital (Park et al., 2012). However, there is a gap in the research relating to the influence of the concealment of users’ identities on self-disclosure or information-sharing behavior on different SNSs.
According to the different boundaries associated with information presentation, social networking sites can be classified as public and private. According to global social media research released in 2016, Facebook was an open social media platform and the world’s largest SNS. WhatsApp was the world’s second largest SNS and the world’s largest private SNS, which is a kind of acquaintance social networking site, only friends of the user can see his/her moments (Lin et al., 2017). WeChat was ranked as the fifth largest SNS in the world and the second largest private SNS in the world (Chaffey, 2016), becoming one of the world’s most popular social media platforms (Montag et al., 2018). In China, WeChat is the most widely used social networking site, more than 90% of mobile phones have installed WeChat (Wang, 2017), and by the end of 2019, WeChat had over 1 billion active users around the world.
Internet users around the world spend an average of 2 h and 22 min a day on social networking sites, and have an average of 8.5 social media accounts and tend to use each platform for different purposes (Bayindir and Kavanagh, 2018). Users of SNSs of different functions manifested different behavioral characteristics (Montag et al., 2015; Montag et al., 2018). Facebook is still the largest social network site with respect to user numbers, but it falls behind YouTube in terms of its weekly visiting rate; YouTube leads in the visiting rate by 7% over other SNS, although it has fewer users (Bayindir and Kavanagh, 2018). According to the “2018 Annual Data Report of WeChat,” published by Tencent, 45 billion WeChat messages are sent every day. However, the average sojourn time of a single visit is obviously shorter than that of “Headline,” an SNS for sharing news and content. Most WeChat friends have a realistic basis, and individuals prefer to use WeChat to satisfy their need for society and affection (Gan, 2017, 2018). WeChat Moments is a function that allows users to share their life and posts on the WeChat application. The main users of WeChat are Chinese, yet there are more than 200 million WeChat users from other countries. Although cultural factor of trusting beliefs plays a role in the self-disclosure decisions of users from various cultures (Krasnova et al., 2012), the need for social communication and the motivations for using social media applications are consistent throughout the world. Therefore, the current study could be generalized to a large extent.
A friend may know a person through the information shared on his or her WeChat Moments, so WeChat Moments is also used to promote users’ real social identities. Users of WeChat Moments mainly share mood notes, as well as notes related to learning and working, daily chores, cuisines, travel, etc. The posting patterns that are available to users include text and picture, as well as text and photos or short videos, which may enhance communication effects. Through WeChat Moments, on the one hand, users find emotional support via interpersonal communication with friends; on the other hand, they shape their own images through shared information. As a smartphone-based social networking site, its rich and diverse features further highlight the fragmentation in information sharing and acquisition. At the same time, WeChat Moments also helps friends overcome the limits of time and space in socialization.
Before social networking sites had gained widespread popularity, studies on computer-mediated communication (CMC) suggested that anonymity in cyberspace, with an absence of reality, could promote expression (Joinson, 2001, 2007; Butler et al., 2009). However, an anonymous identity may have different impacts on users’ disclosures behaviors (Chen et al., 2016). Information sharing in various online contexts has been used as a way to enhance users’ real-world relationships (Subrahmanyam et al., 2008). With its deep integration of networks and real societies, the cyberspace of real societies is equipped with a network communication space based on realistic relationships, and it plays an increasingly important and extensive role in providing a convenient communication platform for people’s work and life (Ibrahim, 2010). The most representative example of such a cyberspace in China is WeChat.
Communication online always comes with more or less different levels of anonymity (Joinson, 2007) Anonymity has been considered in studies concerning free speech online (Akdeniz, 2002). Researchers have gradually put emphasis on the information to which users are exposed as a consequence of users posting about their own lives (Utz, 2015). However, there have not been many studies focusing on how anonymity influences user behavior (Hite et al., 2014), especially in the SNS context. Unlike previous studies (Jessup et al., 1990; Joinson, 2001; Reinig and Mejias, 2004; Lapidot-Lefler and Barak, 2012; Yoon and Rolland, 2012; Hsieh and Luarn, 2014), the current study focuses on the application scenario of WeChat and, in particular, answers the following research questions concerning private SNS:
RQ1. How does perceived anonymity influence users’ intrinsic motivations and information-sharing behaviors on private SNS?
RQ2. Do intrinsic motivations mediate the relationship between perceptions and information sharing on private SNS?
Based on the self-determination theory, we synthesized the existing literature to build a theoretical model, which posits that familiarity exerts negative effects on anonymity perception and positive effects on the intrinsic motivation of information sharing, while perceived anonymity exerts negative effects, and intrinsic motivations mediates the effects among familiarity, perceived anonymity, and information sharing. The current study makes two principal contributions to the literature: first, it scrutinized the negative effect of perceived anonymity on information sharing – an effect that is totally mediated by intrinsic motivation on private SNS. Second, a theoretical model was constructed with which to study both the impact of intrinsic motivation on information sharing and the influence of the basic psychological needs of familiarity and perceived anonymity.
This article consists of the following sections: section “Theoretical Background” reviews the theoretical foundation, section “Research Model and Hypotheses” proposes the research model and hypotheses, section “Methodology” explains the methodology, section “Data Analysis and Results” presents the results and related analysis, section “Discussion” discusses the influences of this article on future research and practice, limitations and potential avenues for future research, and section “Conclusion” concludes the article.
Theoretical Background
Anonymity in Computer-Mediated Communication
Computer-mediated communication1, has two significant features: anonymity and social context cue deficiency (Hsieh and Luarn, 2014). The communication on SNS is also a kind of CMC, promoting the accumulation of social relations (Neves, 2013). These SNSs are useful for users, who are opposed to meeting new people, because they allow them to enhance their relationships in the real world and maintain contact with their friends, families and other connections (Ellison et al., 2007). Offline social capital also impacts SNS use (Yoon, 2014). In China, WeChat has been deeply integrated into users’ work, learning, and everyday lives (Lien et al., 2017; Gan, 2018). However, users still face the challenge of balancing interpersonal relationships and potential privacy concerns (Lowry et al., 2011; Hallam and Zanella, 2017). Verifying the applicability of relevant theories will require an additional examination of how anonymity influences SNS behavior.
Anonymity is when a person’s real identity is unknown due to a lack of identity and information identification in the social interaction (Marx, 1999). Anonymity online means that one cannot find out another’s identity or one cannot be identified by others (Christopherson, 2007), which provides a suitable approach to the study of SNS, because this concept is closely related to human relations research on communication on the Internet (Scott and Orlikowski, 2014). Identity anonymity and visual anonymity have impacts on human behavior on SNS (Lapidot-Lefler and Barak, 2012; Rainie et al., 2013). People may be more willing to share content and messages with an anonymous online identity, without worries about the consequences of their actions (Joinson, 2007; Levmore and Nussbaum, 2010; Jardine, 2015).
The emerging online communication has resulted in intense debates on the pros and cons of anonymity. There are substantial studies that discuss the positive or negative effects of anonymity on SNS (Christopherson, 2007; Lapidot-Lefler and Barak, 2012; Scott and Orlikowski, 2014; Fox et al., 2015; Jardine, 2015; Chen et al., 2016, 2019). Some studies have suggested that anonymity on SNS is a significant way to protect private information (Brazier et al., 2004; Rainie et al., 2013) and build a personal image (Lin et al., 2017), and it has been suggested that people use anonymous online forums as platforms for self-disclosing actions that they feel guilty about (Levontin and Yom-Tov, 2017). However, in the contemporary Internet environment, with a significant use of smart mobile phones, the influence of anonymity on behavior requires further in-depth exploration, as there is no absolute anonymity in the current online environment (Bodle, 2013). Indeed, the data produced by mobile phone networks can identify most people from only pieces of information from their social media use or from the location from which they make calls (De Montjoye et al., 2013).
The influence of CMC anonymity on behavior has been extensively studied by researchers, which has led to theories that illustrate anonymous behavior (Christopherson, 2007). The social identity model of the deindividuation (SIDE) effect asserts that, in the context of anonymous identities, people show a behavioral tendency to obey a group norm due to the prominence of an individual identity (Vilanova et al., 2017). Anonymity in computer-mediated communication may not necessarily lead to antisocial behavior (Christopherson, 2007). Instead, anonymity could enhance social processes related to group identity in online communication (Spears, 2017). While anonymity may benefit information sharing, there is an argument that it may negatively affect sharing behavior (Yoon and Rolland, 2012). The negative effects of online anonymity are reflected in the effects of personalization, misconduct, and false information, which are related to the dark side of the Internet (Fox and Moreland, 2015). In Internet-based interpersonal communication, such as social networking sites, anonymity can also play a negative role in information exchanges (Yoon and Rolland, 2012; Chen et al., 2016, 2019). Research on Twitter also showed that anonymous participants expressed greater hostile sexism through tweeting than non-anonymous participants (Fox et al., 2015).
The hype personal model emphasizes people’s tendency to strategically construct their self-image using Internet technology, making use of online messages to enhance their relationships (Walther, 2007). SNS provides real-time feedback for the construction process of users’ personal images and enhances the ability of users to build their own image and influence others (Li et al., 2018). The hype person is a more perfect version of oneself than reality, and WeChat users take advantage of the impression management technology and relationship maintenance functions, as a mediated interface that WeChat strategically permits to achieve their goals and needs (Zhang et al., 2017).
Motivation and Self-Determination Theory
The self-determination theory explains the determination process of behavior, where individuals make decisions only by their own desires, without being influenced by any other external factors (Deci and Ryan, 1985). It is a theory of self-motivation, delving into human motivation and individual personality with conventional empirical methods, which puts emphasis on how psychology impacts people’s personalities and the way they evaluate their own behaviors (Ryan and Deci, 2017). Three basic human psychological needs have been defined (Ryan and Deci, 2017): autonomy, with which one feels self-motivated when behaving; competence, indicating an individual’s need to feel competent, while engaging in activities; and relatedness, one’s desire to maintain relationships with friends, family, etc. Based on the theory of self-determination, social contexts can enhance individuals’ self-motivation by internalizing their external motivations and maintaining good behavior by satisfying their needs of autonomy, competence, and relatedness. These three critical psychological needs are closely related to users’ behavior (Ryan and Deci, 2017).
Some studies have confirmed the influence of intrinsic motivation on different types of information sharing on SNSs. The influence of intrinsic motivations on the sharing of knowledge related to intentions and behaviors in firms has been confirmed (Welschen et al., 2012; Lai and Chen, 2014; Rode, 2016; Safa and Von Solms, 2016), as well as actual travel experience sharing on social media (Kang and Schuett, 2013), m-coupon sharing (Tang et al., 2016), and sharing information about products and services (Cho et al., 2015). The crowding-out effect was found when examining users’ motives to share commercial content on social networking sites: in self-reports, intrinsic motives for sharing dominated, while in the experiment, extrinsic incentives induced a greater willingness to share (Vilnai-Yavetz and Levina, 2018). The specific factors that influence the intrinsic motivation of information-sharing behavior have been refined (Welschen et al., 2012; Lai and Chen, 2014).
While some studies have explored the role of other factors in promoting intrinsic motivation, such as system support and information feedback (de Almeida et al., 2016). There is a gap in the literature relating to the influence of psychological perception factors on intrinsic motivation. Furthermore, Research examines the motivation of sharing behaviors on SNS using the theory of planned behavior (Cho et al., 2015; Shibchurn and Yan, 2015; Chen et al., 2018). However, there is a lack of research on the influence of intrinsic motivation on information-sharing behavior on SNS from the perspective of self-determinism.
Information-sharing behaviors in the WeChat Moments function are forms of self-expression that are determined by individual competence levels (Wang et al., 2016). Social relatedness, based on private social networking and convenient communication, is an important component of WeChat usage (Gan and Wang, 2015; Gan, 2017). WeChat use intensity can significantly predict users’ motivations, and intrinsic use motivation was the mediator between the use intensity and subjective well-being of users (Wen et al., 2016). SNSs are perfect for users to express themselves, since they relate to the gratification of self-efficacy (Cheung et al., 2015; Vogel and Rose, 2016). On SNSs, information sharing is a self-motivated behavior. Thus, we hypothesize that the satisfaction of basic needs will impact users’ information-sharing behavior on WeChat.
Research Model and Hypotheses
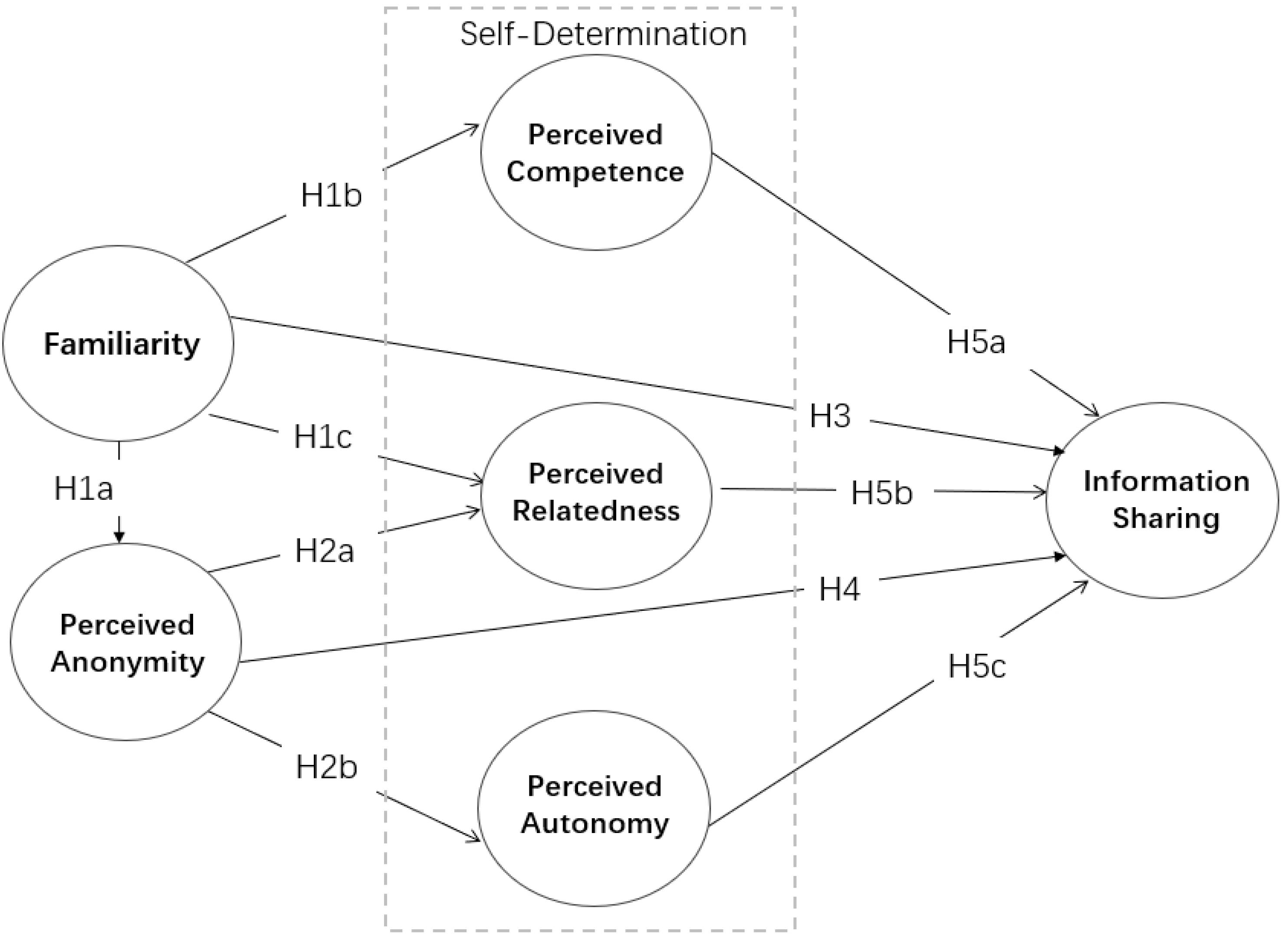
The current study constructs a model based on the self-determination theory, which is informed by the most popular SNS, WeChat Moments, in China. We examine how the factors of familiarity and perceived anonymity affect the motivation to share information on WeChat. In addition, this study also pays attention to the mediating influence of self-determination on familiarity, perceived anonymity, and information-sharing behavior. The research model is depicted in Figure 1.
Familiarity and Anonymity on Social Networking Sites
Familiarity and anonymity are two interrelated but different psychological perceptions that have an influence on users’ behavior. Familiarity refers to an understanding of a thing, contact, or interaction experience that forms a relatively stable cognitive structure and carries the expectation of possible situations and results in subsequent contact with someone or the use of something (Kaptein et al., 2013). Social networking sites provide major platforms for exhibitionism, and users can share information at their own will (Munar, 2010). Besides, they can also adjust the words and pictures of their posts to present themselves (Moon et al., 2016). SNSs allow users to present themselves and connect with friends in different ways. Thus, they serve as venues for significant signals of identity, which enables users to perform properly in the virtual world and articulate friendship links (Ellison et al., 2011). The familiarity of the platform reflects the integration of WeChat contactors with users’ real social relations. Thus, we hypothesize that:
H1a: Users’ familiarity will have a positive impact on their perception of their anonymity on WeChat Moments.
Familiarity is a concept referring to one’s previous associations, connections and knowledge, which is closely related to trust (Komiak and Benbasat, 2006). Familiarity influences how individuals understand others’ behavior and actions on SNSs (Sánchez-Franco and Roldán, 2015). Users’ previous experiences with computers directly enhance their self-efficacy. They believe that computers are user-friendly and useful (John, 2013). Their sense of familiarity with the Internet and expectations of its outcomes has a positive relation with how users perceive their self-efficacy in using SNSs (Eastin and LaRose, 2000; Kenny et al., 2012). Some perceptions related to identifiability, such as the degree of familiarity, perceived similarity with previous experiences, and trust have a positive relation with users’ participation in online communities (Zhao et al., 2012). Thus, we hypothesize that:
H1b. Users’ familiarity will have a positive impact on their perception of their competence on WeChat Moments.
Familiarity may reduce uncertainty, such that people can feel closely related to each other and supported by the people around them (Lin and Utz, 2017). With respect to acquaintances, users have a higher mutual trust and closer ties, and increasing trust is a necessary requirement for online self-disclosure (Taddei and Contena, 2013). WeChat is an acquaintance social platform with a reality-based form as its foundation (Wang and Gu, 2016). Thus, the degree of familiarity therein will affect people’s awareness of their relationships (Finkel et al., 2015). With familiarity, uncertainty will be lowered (Gefen, 2000), enabling people to feel that they are capable of adequately using this platform to make contact with others and feel support from others. Thus, we hypothesize that:
H1c. Users’ familiarity will have a positive impact on their perception of relatedness on WeChat Moments.
Perception of anonymity refers to a low level of identifiability and results in users’ self-perception that they are untraceable in their virtual interactions (Kang et al., 2013). Under anonymous conditions, social bonds are less strong, and social norms are more often aggressive (Wright, 2014). When in group discussion, it was revealed that users who feel anonymous are more likely to embellish others’ opinions, compared with those who are identifiable (Jessup et al., 1990). On social networking sites, anonymous participants reported more post-task sexism than identifiable participants (Fox et al., 2015). The anonymous behavior indicated the consequence that interpersonal connections are weakened in the virtual world. Not being identified means that there is no familiar social connection. Thus, we hypothesize that:
H2a. Users’ perception of anonymity will have a negative impact on their perception of relatedness on WeChat Moments.
Perception of anonymity introduces security awareness into interpersonal interactions (Bodle, 2013). Researchers have posited that the context of communication influences receiver attempts to identify sources, as well as their perceptions of senders (Rains and Scott, 2007). The anonymity of in-group members has been shown to cognitively enhance the perceived unity or entitativity of groups (Sassenberg and Postmes, 2002), which results from reductions in psychological perceptions of individual self-mastery. Users are strategic about using social networking sites to improve their images in social relations (Vogel and Rose, 2016). When users perceive themselves as highly anonymous, they may think about others’ reactions to their sharing, and these thoughts may reduce individuals’ perceived autonomy (Yoon and Rolland, 2012). Thus, we hypothesize that:
H2b. Users’ perception of anonymity will have a negative impact on their perception of autonomy on WeChat Moments.
Familiarity means a close relation, cultural identification, and trust (Gefen, 2000). Concepts related to familiarity, such as interface and habitualness, have been shown to play a critical role in information sharing (Yu et al., 2010; Kim, 2016). The development of an ongoing, trusting relationship, with an understanding of people’s needs, concerns, and shared responsibility, has a positive influence on information-sharing behaviors (Yang and Maxwell, 2011). In addition, familiarity may reduce the perception of risk in communication, mediating the impact of changes in policies’ monetization options on whether people would like to reveal information (Gerlach et al., 2015). The online interrelation built upon personal reputation is crucial for encouraging successful knowledge sharing (Hung et al., 2011). In addition, the role of social capital and a directed social network in users’ information sharing on SNSs has been highlighted (Liu et al., 2016). Thus, we hypothesize that:
H3. Users’ familiarity will have a positive impact on their information-sharing behavior on WeChat Moments.
The concept of perceived anonymity refers to how much personal identity information users believe has been revealed (Hite et al., 2014). Anonymity promotes some negative online behavior (Barlett et al., 2016). Research also suggests that a higher level of perceived anonymity on SNSs means less tendency toward self-disclosure (Chen et al., 2016). There are supportive results proving the negative relationship between anonymity and knowledge-sharing behavior in virtual communities (Yoon and Rolland, 2012), as well as a significant relationship between privacy concerns and self-disclosure on Facebook (Faisal and Alsumait, 2011). On WeChat, users interact and keep in touch with one another to gain attention and a sense of existence and connection by sharing information (Lien et al., 2017). Identifiability is important for users to maintain relationships with their acquaintances, so unidentifiability may reduce the tendency of users to share information. Thus, we hypothesize that:
H4. Users’ perception of anonymity will have a positive impact on their information-sharing behavior on WeChat Moments.
Self-Determination Factors of Information Sharing on Social Networking Sites
The relationship between intrinsic motivation and behavior in humans is supported by studies on online communities (Yoon and Rolland, 2012; Wang and Hou, 2015). We assume that satisfaction, based on the intrinsic needs of the self, affects users’ information-sharing behavior in maintaining relationships and building their image.
The level of task performance has been shown to be greatly influenced by how competent individuals believe they are. Self-perceived competence has emerged as a significant predictor of willingness to communicate (Donovan and MacIntyre, 2004). Self-efficacy has various positive impacts and has hence become a significant variable in social psychological research (Gecas, 1989). It has emerged as a highly effective predictor of motivation, learning, and performance (Chen et al., 1998) and has also been shown to have an effect on behaviors associated with sharing knowledge on online platforms (Hsu et al., 2007), as well as product information sharing on SNS (Cho et al., 2015; Hajli and Lin, 2016). Thus, we believe that competence has become a driving force behind users’ information sharing on SNSs. Thus, we hypothesize that:
H5a. Users’ perception of their competence will have a positive impact on their information-sharing behavior on WeChat Moments.
Perceived relatedness defines how connected they feel with the people around them (Yoon and Rolland, 2012). SNSs provide fundamental platforms, where people can build connections on the Internet (Lin and Lu, 2011). With the spread of SNSs, users feel closely connected with more people, such that they can accumulate social capital and obtain more information (Boyd and Ellison, 2007; Ellison et al., 2011; Zhao et al., 2012; Yoon, 2014). In addition, the social interaction ties of trust, rules of reciprocity, and identification influence how people share with others on online platforms (Chiu et al., 2006), and the effect of relationship building through SNS on an individual’s intention to share information has been confirmed (Kim, 2012). Thus, we hypothesize that:
H5b. Users’ perception of relatedness will have a positive impact on their information-sharing behavior on WeChat Moments.
Perceived autonomy is a concept that shows how much control a person thinks he/she has over his/her own actions. When individuals are in a virtual world, their level of self-presence and autonomy are two critical factors (Jung, 2011). Users’ can adjust their behaviors strategically, such that they can enhance their relationships. The more autonomy they believe they have in maintaining their friendships, the more satisfied they are (Demir et al., 2011). Sharing behavior may depend on people’s own self-expressive needs (Constant et al., 1994), of which the logical premise is the user’s independent control of the information expressed. A user’s personal status is also significant for the information diffusion on social networking sites (Stieglitz and Dang-Xuan, 2013). Users who were driven by the potential satisfaction of their information seeking were more likely to share on social networking sites (Lee and Ma, 2012). Positive attitudes toward sharing were found to lead to positive intentions and, ultimately, to actual sharing behaviors (Bock and Kim, 2001). SNS users’ structural autonomy has been confirmed as an antecedent of relational inertia in information sharing (Cheon et al., 2015). Thus, we hypothesize that:
H5c. Users’ perception of their autonomy has a positive impact on their information-sharing behavior on WeChat Moments.
The Mediating Effect of Self-Determination Factors
Human motivation is a complicated, multidimensional internal process (Deci and Ryan, 1985; Chen and Jang, 2010). Several studies have confirmed that self-motivation has direct relations with psychology and behaviors (Charbonneau et al., 2001; Prabhu et al., 2008; Zapata-Phelan et al., 2009; Fernet et al., 2013). According to the theory of self-determination, self-motivation is correlated with three basic needs: whether people feel competent, the degree of relatedness, and whether there is self-autonomy (Deci et al., 1989). While there are many studies investigating these three factors, their mediating roles in an online context, especially on social networking sites, have rarely been empirically tested. In computer and human interactions, perceptions of users’ competence mediate their use behavior (Canary and Spitzberg, 1989; Davis and Wiedenbeck, 2001). In addition, the mediating effect of some self-determination factors has been confirmed in some SNS contexts (Li et al., 2013, 2014; Wong et al., 2015). Thus, we hypothesize that:
H6. Perceived competency and relatedness have a mediating effect on familiarity and information-sharing behavior on WeChat Moments.
H7. Perceived relatedness and perceived autonomy have a mediating effect on anonymity and information-sharing behavior on WeChat Moments.
Methodology
This study puts emphasis on WeChat Moments users’ information-sharing behaviors. WeChat Moments provides users with virtual spaces to share information with their existing friends, which is an ideal platform for the current research on information sharing.
In addition, WeChat was chosen due to the surge in its popularity since its introduction. WeChat is now the most popular acquaintance-based social networking site, having around 1 billion unique active users, of which more than 200 million users are from countries other than China (Tencent, 2018). WeChat has the typical features of an acquaintance social platform, and more than 70% of Chinese people maintain numerous social relations on WeChat (Wang and Gu, 2016). We collected our data from frequent users, which are believed to constitute an appropriate and representative sample of acquaintance-based social networking sites.
Data Collection
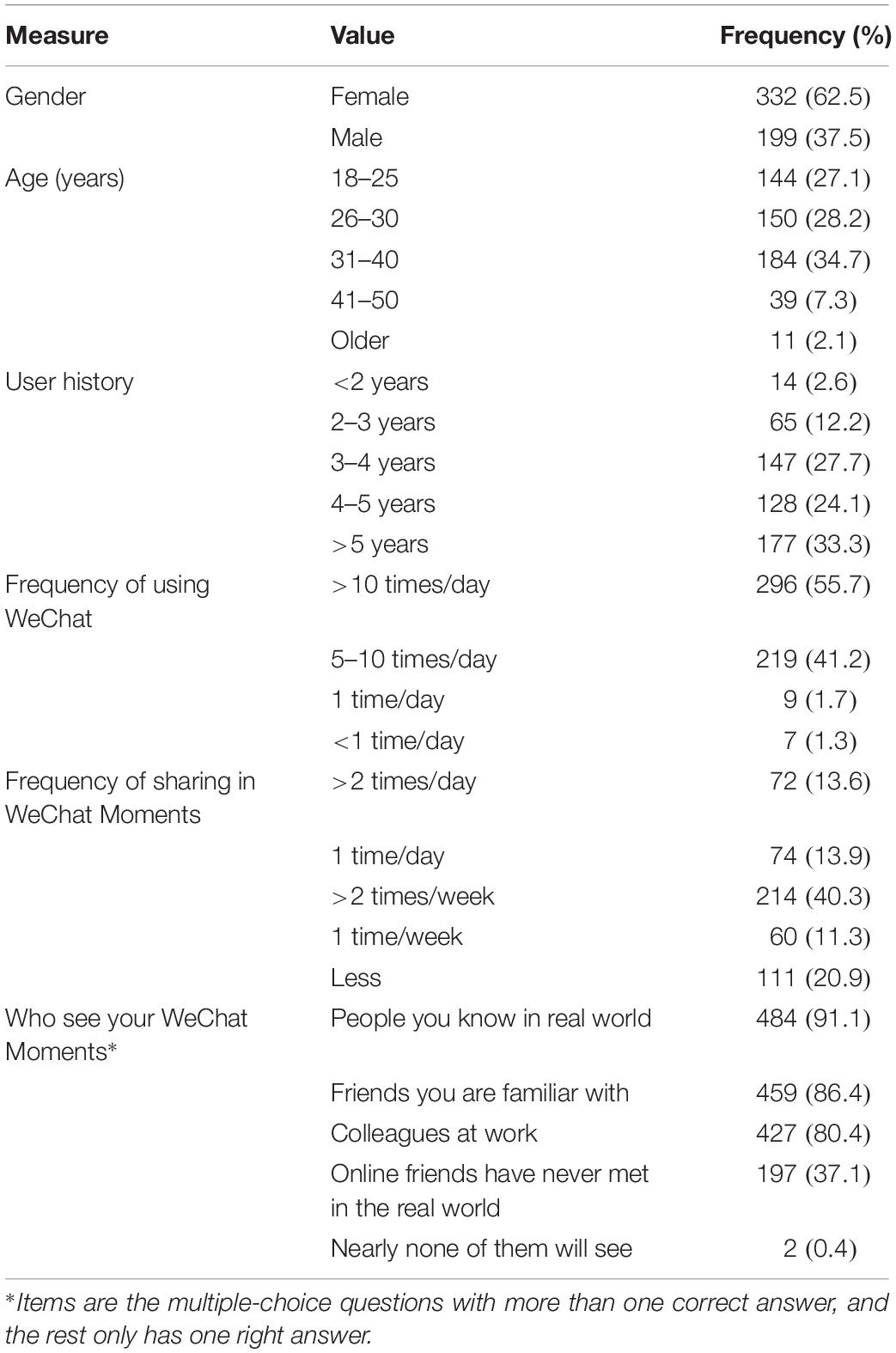
In the preliminary stages, this study tested the research model through an investigation of WeChat users from China. The data were collected based on an online questionnaire using the online survey platform, www.sojump.com. The purposive sampling method was applied in this survey. Participants were enrolled through a representative sample service, where they were asked to fill in a questionnaire online. After they finished the questionnaire, they received a coupon and had the chance to win something through a lucky draw. Screening questions were included as a filter in order to identify frequent WeChat Moment users for the study, which yielded a total of 531 valid questionnaires out of 601 responses (Supplementary Table S1). Table 1 below shows the results of the survey concerning the participants’ characteristics.
The distribution of sample demographic information is relatively reasonable. Although bias differences exist in the gender distribution of the research, the factors discussed in this study have some similarity with the researched population. Gender differences do not affect the researches on general sharing behaviors online, which are confirmed by some related studies on similar gender distribution differences (Yoon and Rolland, 2012; Cheung et al., 2015; Yan et al., 2016). The respondents’ WeChat Moments views are characteristic of users of acquaintance SNSs. The respondents are familiar with the use of WeChat and often share information on WeChat Moments.
An ethics approval was not required, according to the relevant institutional and national guidelines and regulations, and the informed consent of the participants was implied in their completion of the survey. First, the data collection of the current study needs no fuzzing processing, as no privacy or sensitive issue is involved. Second, the data collection of the current study does not involve implication, drug or mental manipulation, as the subjects are only required to report their experience and behavior tendency according to the use conditions of the online platform. Thus, no issue with respect to safety, health or right and interest protection is involved. Third, the data extraction of the current study only withholds users’ IP addresses, as there is no need to record private information concerning, for example, the names and identities of the subjects. Fourth, the questionnaire for collecting the data for the current study includes an informed consent statement, and the subjects are only requested to answer questions according to their use conditions. The data are only used for scientific research, and no influence is generated on the privacy, reputation, living conditions or health of the participants. Fifth, the current study does not store or use the private information of the participants, and any information that may lead to identity risks (only the IP Address) is removed during the analysis and submission for scientific review.
Measures
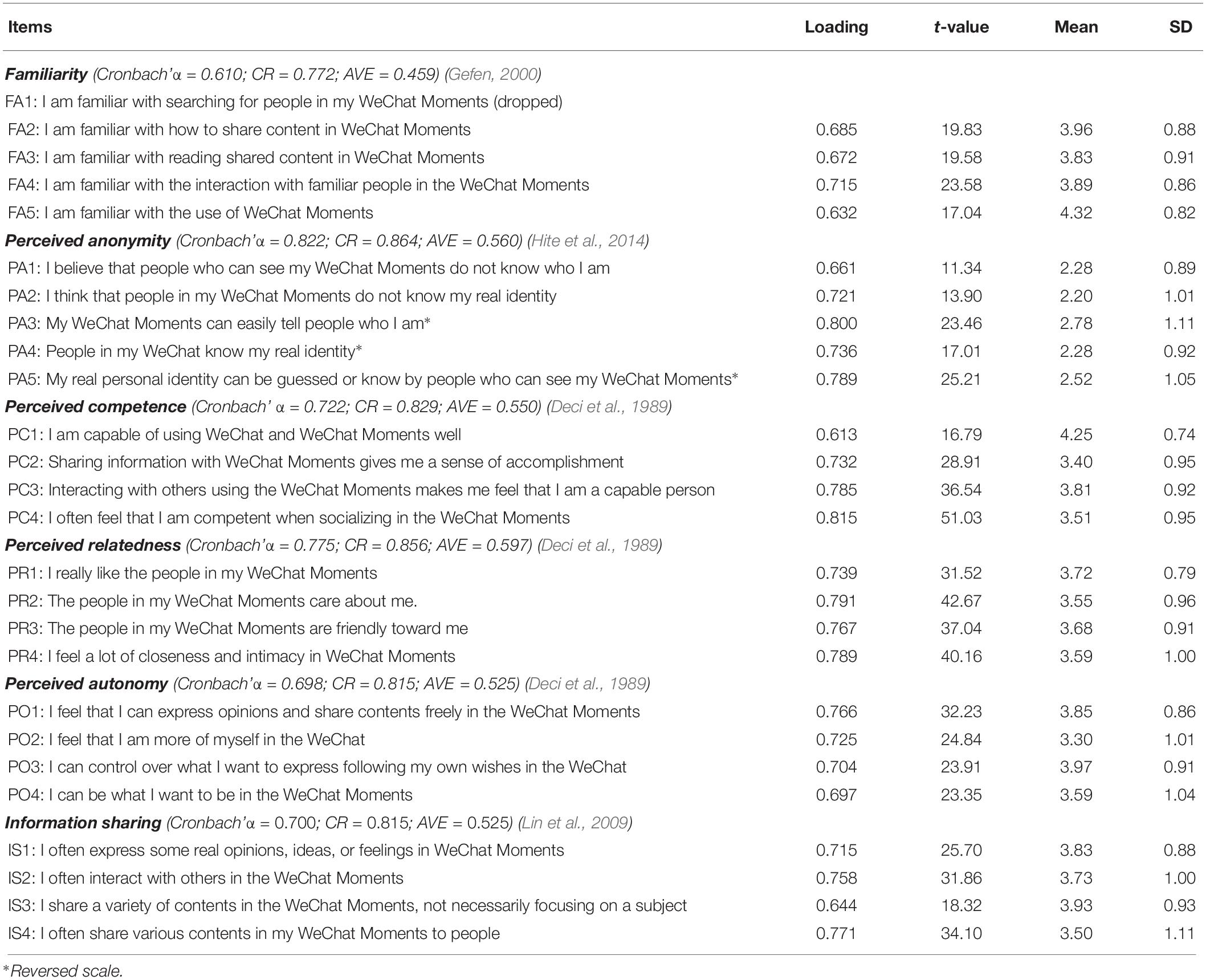
All applied measures of this study were drawn from the relevant existing literature. We translated the scale into Chinese and then translated it back into English, based on the research needs. We asked two researchers with a Ph.D. to verify the consistency of the expressions in the scale in order to ensure that the translation was consistent with the original scale. Multi-item measures were applied to make sure the study is valid and reliable. All measures used five-point Likert scales (1 = strongly disagree to 5 = strongly agree). Table 2 lists the constructs and measures applied in this paper.
Data Analysis and Results
The structural equation model is used to verify the research model. We performed statistical analysis using the partial least squares method (PLS). Smart PLS version 3 (Ringle et al., 2014) has been used to test the research model and is an analytical technique widely used in behavioral and business research because it provides a flexible method, which is widely used by researchers studying human behavior, with coherent explanations for complex relationships (Henseler et al., 2014). PLS is very suitable for predictive exploratory modeling and research (Henseler et al., 2014). According to the two-step analysis method (Hair et al., 2014), we first tested the validity of the measured values and then evaluated the structural model.
With the application of the two-step analytical approach, we were able to confidently draw the conclusion that a structural relationship could be drawn from a series of measurement instruments with desirable psychometric properties.
Reliability and Validity of the Measurement Items
In order to validate the measurement model, we tested the convergence and discriminant validity of the data. The following general criteria are used to evaluate the convergence effectiveness of the structure: all project loads should be greater than 0.60; the composite reliability (CR) should be at least 0.70; and the average variance extraction (AVE) should be at least 0.50 (Fornell and Larcker, 1981). The results of this study, shown in Table 2, satisfy all three convergence validity conditions, except that the AVE of familiarity is less than, but very close to 0.5, which is acceptable for empirical research. The factor loadings of all items surpassed 0.60, and a single item’s loading lower than 0.60 was excluded.
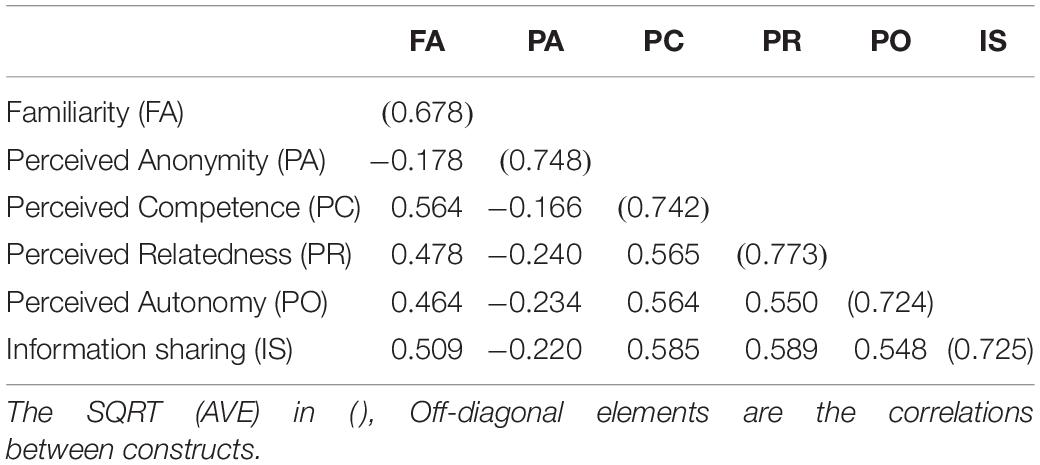
Discriminative validity refers to the degree to which the measurement of one variable does not reflect other variables. The low correlation between interest measures and other structural measures indicates the validity of the discrimination (Fornell and Larcker, 1981). If the AVE square root of each construct is greater than its correlation with all other constructs, it is proved to be discriminant. As shown in Table 3, the AVE square root of each construct is greater than the correlation of them and all of the other constructs. The results show that all of the measured values have sufficient discriminant validity. In the current study, the evidence proves that our data analysis results have enough higher convergent validity and discriminant validity.
Structural Model
Based on the hypothetical research model, we analyze the structural model by examining the significance of the path coefficients and the (R2) variance for the dependent constructs. Figure 2 reveals the path and its importance for the structural model, as well as the coefficients of each related structure, their T values on the structural model and the deterministic coefficients (R2). From the statistical data, anonymity perception has no direct significant impact on users’ information sharing, while other structures have significant impacts. With the exception of H4, all other hypotheses have been confirmed. We also conducted a half-way data analysis test on the samples, and the results were completely consistent.
The results indicate that the independent variable explains a relatively high proportion of the variance of the dependent variable. In this model, 31.8% of the variance of self-competence perception was explained, and 25.3% of the variance of correlation perception and 48.6% of the variance of information sharing were also explained. The model can moderately predict information-sharing behavior, perceived competence, and perceived relatedness. The predictive effectiveness for perceived autonomy was quite low (R2 = 0.055), as well as that for perceived anonymity (R2 = 0.032). The R2 statistic may be small, yet the coefficient p-values can still be statistically significant. Such a relationship between the predictors and response is also very important, even though it may not explain a large amount of variation in the response (Chin, 1998).
According to Hair et al. (2016), the use of PLS-SEM for theory testing and confirmation is limited since it does not have an adequate global goodness-of-fit measure. Researchers using PLS-SEM may not draw on a global goodness-of-fit measure to evaluate the overall model fit, as PLS-SEM focuses on prediction (Hair et al., 2014).
Mediating Effect Test of Self-Determination
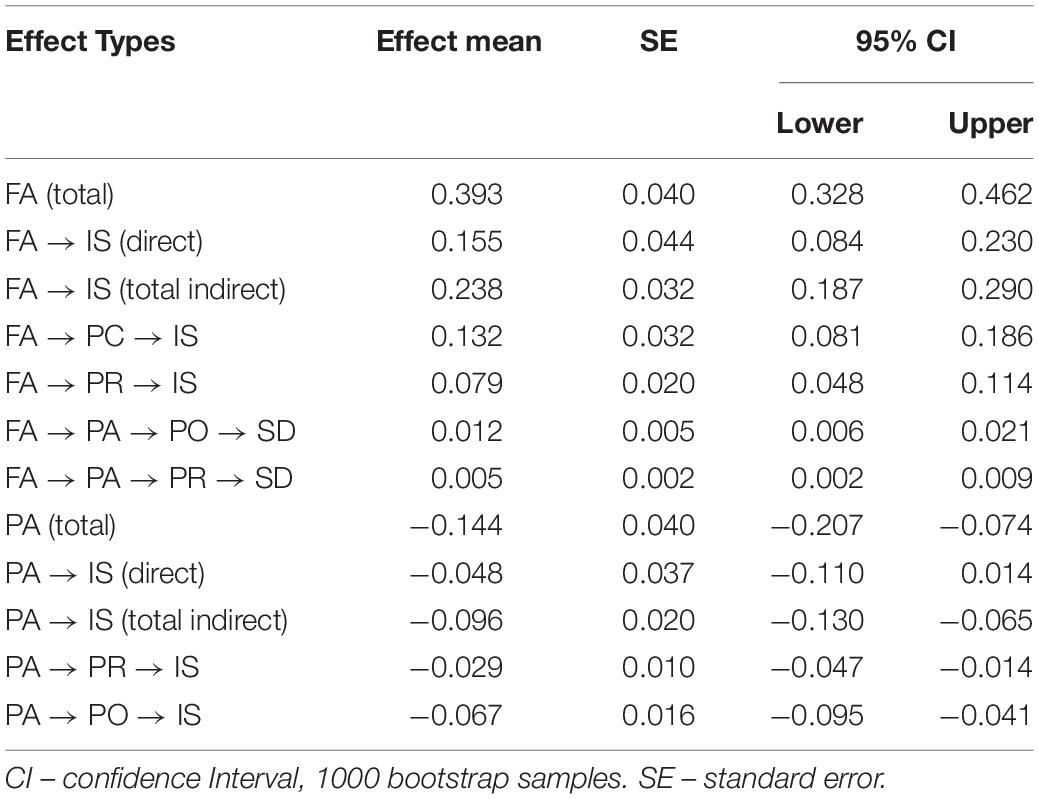
Preacher and Hayes (2004) proposed that the bootstrapping method can effectively and reasonably verify the non-direct impact. In this study, we used this method to verify the mediating effect. As shown in Table 4, the mediating effect of self-determination has been confirmed.
Perceived competence and relatedness have crucial and positive mediating influences on familiarity, with respect to the total mediating effect of the perceived competence and perceived relatedness combination. The mediating effect of perceived competence accounted for 33.6% of the total effect, occupying 55.5% of the total intermediary effect. The mediating effect of perceived relatedness accounted for 20.1% of the total effect and 33.2% of the total intermediary effect. The combined effect of perceived anonymity, perceived competence, perceived autonomy, and perceived relatedness comprised 60.6% of the total effect. Familiarity accounted for about 40% of the direct effect on information sharing.
The negative mediating effects of perceived autonomy and perceived relatedness on perceived anonymity and information sharing were significant. This was also evidenced by the total mediating effect on perceived anonymity and information sharing. The intermediary effect of perceived autonomy accounted for 69.8% of the total intermediary effect. The mediating effect of perceived relatedness accounted for 30.2% of the total intermediary effect. In the case when the direct effect of perceived anonymity and information sharing was weakened, perceived autonomy and perceived relatedness had a complete mediating role. As a result, the negative effect of perceived anonymity on information sharing – an effect that is totally mediated by intrinsic motivation – has been confirmed.
Discussion
The results of current study showed that familiarity has a deep positive influence on perceptions of competence and relatedness and information sharing. The current study also revealed the negative effect of perceived anonymity on users’ motivations in information sharing on WeChat Moments. It showed that the higher the level of anonymity perceived by the users, the less relatedness and autonomy they feel. Motivation had a partly mediating impact on familiarity and information sharing and a total mediating impact on anonymity and information sharing. We also found that self-motivation, perceived competence, perceived relatedness, and perceived autonomy significantly affect information-sharing behavior.
The direct connections between perceived anonymity and information-sharing behaviors on acquaintance SNSs are not significant. This might be explained by the fact that the effect of perceived anonymity is intermediated by perceived relatedness and perceived autonomy. Many scholars have studied the correlations in how anonymity affects behavior in many different contexts (Hite et al., 2014). Indeed, CMC research has confirmed that anonymity influences behavior (Reinig and Mejias, 2004). Anonymous online settings are also related to a tendency to provide socially desirable responses (Muhlenfeld, 2005). However, the influence of different types of anonymities, especially perceived anonymity, on behavior still needs to be examined in different online contexts. The current study showed that the negative effect of perceived anonymity on information sharing is totally mediated by intrinsic motivation.
Theoretical Implications
The current study presents implications to facilitate future explanation of the behavior of the users of social networking sites, particularly WeChat Moments. Whetten (1989) argues that when existing models are applied to a new context, they lose their academic significance, unless they are modified. An important way to promote the development of a theory is to study relevant problems from the perspective of other fields, so as to further explain the mechanism of the relationship between different variables. The current study makes theoretical contributions in the following ways.
First, these findings supplement previous studies on the information-sharing behavior on WeChat Moments. The results showed that familiarity has an important positive effect on information sharing on WeChat Moments. The findings of the study have important implications for understanding social networking sites based on the acquaintance relationship.
Second, this study further examined the online anonymous behavioral theory. Anonymity has generated obvious differences in the influential mechanism of self-expression behavior between people in acquaintance relationships on WeChat and in other relationships in cyberspace, such as public forums (Yoon and Rolland, 2012; Gan and Wang, 2015). To some extent, the environment of WeChat Moments highlights users’ real social identities and leads to the sharing of positive content (Chen et al., 2016), while perceived anonymity reduces users’ willingness to share information. From the perspective of technological applications, interactions based on social networking sites strengthen the effect of hyper personal communication. A close connection between the subjects of sharing behavior helps to cultivate the construction of hyper-personal impressions. The current study lays the foundation for the further verification and extension of the hyper-personal communication theory in relation to WeChat Moments.
Third, the effectiveness of the self-determination theory in explaining WeChat Moments was validated. In addition, the influence of the basic psychological requirements of familiarity and anonymity was validated. The partial intermediary effect of intrinsic motivation on familiarity and information sharing, as well as the total intermediary effect of intrinsic motivation on anonymity and information sharing, was confirmed. These variables could be applied to studies on the self-determination theory in other contexts. The research model is applicable to more online scenarios and is capable of considering other psychological or cultural factors.
Practical Implications
The findings of this study also have some practical utility, especially for policymakers, service providers, and users of social networking sites. It is shown that familiarity has an important effect on perceived competence, perceived relatedness, and information sharing on WeChat Moments. For service providers, SNSs should put more emphasis on the design of the human–computer interaction interface to meet users’ preferences, facilitate the investment in and bonding of user relationships, and increase the means of user interactions to promote feelings of familiarity. They should also encourage users to invite other people with which users have real-world social relationships in order to introduce more acquaintances into social networking sites. The improvement of user activation and connection will further increase the value of WeChat Moments for individual users.
The current study suggests that perceived anonymity has a negative influence on perceived relatedness and autonomy, and the two intrinsic motives totally mediate the negative influence of perceived anonymity on information sharing. Service providers should include more information concerning user identity on WeChat Moments to decrease perceived anonymity. In this way, they could improve the degree of individual identity, enhance self-awareness and generate the use of acquaintances to advance public self-awareness; both qualities are connected with low deindividuation and aggression (Prenticedunn and Rogers, 1982). How to improve the supervision of net users’ real identity should not be the only focus of regulators. It is also critical to consider the influence of real identity on perceived anonymity and include it in the user identity regulation system. That perceived anonymity has different effects on user behavior in different online spaces should be taken into consideration.
Limitations and Future Directions
This study has the following limitations. First, the research scenario and participants of the survey have been restricted to WeChat Moments. As information sharing is considered a dynamic process and is affected by individual and contextual factors (Hsu et al., 2007), additional research is needed to examine how and to what extent contextual differences affect users’ information-sharing behavior. The research model is applicable to more online scenarios and is capable of considering other psychological or cultural factors. Second, the current study provides no support for the H5 hypothesis, which suggests that perceived anonymity has no direct effect on information sharing, and the two intrinsic motives totally mediate the negative influence of perceived anonymity. Familiarity, a positive psychological perception, directly affects information sharing, while anonymity, a negative psychological perception, can only affect information sharing through motivation. We have repeatedly verified this phenomenon, although its causes need further verification. Third, differences exist in the age and sex distribution of the research sample and the whole netizen group. Future studies should enhance the representativeness and universality of the research sample and consider more variables in future study. Finally, this study did not differentiate the impacts of different types of information. Individuals have different preferences for different information types, which may influence their sharing and acquisition behavior. Future studies should therefore consider the characteristics of information, as well as different types of social networking sites.
Conclusion
The current study applied the theory of self-determination and constructed a research model to explore the influence of two psychological factors, familiarity and perceived anonymity. We looked into how these two factors impact the self-motivation of users in information sharing on WeChat Moments. It has been proved that this measurement model has high validity in terms of both its convergent and discriminant aspects. The basic elements of intrinsic motivation displayed a critical intermediary effect. With the prevalence of smartphones, mobile Internet-based social networking services have become an important medium for communication. Social networking sites for acquaintances are playing an increasingly crucial role in social reality. The current study contributes to the literature by allowing for an understanding of familiarity, anonymity, intrinsic motivation, and information sharing in relation to WeChat Moments. It is hoped that the current study will inspire future researchers to explore human behavior, as it is manifested on WeChat Moments.
Data Availability Statement
All datasets generated for this study are included in the article/Supplementary Material.
Author Contributions
XC performed the theory analysis and design, and contributed to drafting the manuscript. MS analyzed the data and improved the empirical analysis. DW analyzed the data and improved the writing. XS improved the writing and conclusions.
Funding
This work was supported by the China National Social Science Fund Project, named “Research on Network Anonymity and Network Society Governance” (Grant Number: 15CSH017), Program for Excellent Young Talents, Yunnan University, and the Dong Lu youth scholar training project of Yunnan University (No. C176220200).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Acknowledgments
We are grateful for the comments from the editor GV and the reviewers JC, XS, and YN. We are also grateful for the comments and suggestions from Tianguang Meng, Hailong Liu, and Hongzhong Zhang. All remaining errors are strictly the responsibility of the authors.
Supplementary Material
The Supplementary Material for this article can be found online at: https://www.frontiersin.org/articles/10.3389/fpsyg.2019.02540/full#supplementary-material
TABLE S1 | Questionnaire results.
Footnotes
- ^ Computer-mediated communication refers to communication using devices such as computers and smartphones as media. Most online communications are considered CMC.
References
Barlett, C. P., Gentile, D. A., and Chew, C. (2016). Predicting cyberbullying from anonymity. Psychol. Pop. Media Cult. 5, 171–183.
Bayindir, N., and Kavanagh, D. (2018). GWI Social Summary: GlobalWebIndex’s Report on the Latest Trends in Social Networking [Flagship Report 2018]. London: GlobalWebIndex.
Błachnio, A., Przepiorka, A., and Pantic, I. (2016). Association between facebook addiction, self-esteem and life satisfaction: a cross-sectional study. Comput. Human Behav. 55, 701–705. doi: 10.1016/j.chb.2015.10.026
Bock, G. W., and Kim, Y. G. (2001). Breaking the myths of rewards: an exploratory study of attitudes about knowledge sharing. PACIS 2001 Proceedings 78, 1112–1125.
Bodle, R. (2013). The ethics of online anonymity or Zuckerberg vs. Moot. ACM SIGCAS Comput. Soc. 43, 22–35. doi: 10.1145/2505414.2505417
Boyd, D. M., and Ellison, N. B. (2007). Social network sites: definition, history, and scholarship. J. Comput. Mediat. Commun. 13, 210–230. doi: 10.1111/j.1083-6101.2007.00393.x
Brazier, F., Oskamp, A., Prins, C., Schellekens, M., and Wijngaards, N. (2004). Anonymity and software agents: an interdisciplinary challenge. Artif. Intell. Law 12, 137–157. doi: 10.1007/s10506-004-6488-5
Butler, S. F., Villapiano, A., and Malinow, A. (2009). The effect of computer-mediated administration on self-disclosure of problems on the addiction severity index. J. Addict. Med. 3, 194–203. doi: 10.1097/ADM.0b013e3181902844
Cachia, R., Compañó, R., and Da Costa, O. (2007). Grasping the potential of online social networks for foresight. Technol. Forecast. Soc. Change 74, 1179–1203. doi: 10.1016/j.techfore.2007.05.006
Canary, D. J., and Spitzberg, B. H. (1989). A model of the perceived competence of conflict strategies. Hum. Commun. Res. 15, 630–649. doi: 10.1111/j.1468-2958.1989.tb00202.x
Chaffey, D. (2016). Global Social Media Research Summary 2016. Smart Insights. Social Media Marketing. Available at: http://www.smartinsights.com/social-media-marketing/social-mediastrategy/new-global-social-media-research/ (accessed Oct 3, 2016).
Charbonneau, D., Barling, J., and Kelloway, E. K. (2001). Transformational leadership and sports performance: the mediating role of intrinsic motivation. J. Appl. Soc. Psychol. 31, 1521–1534. doi: 10.1111/j.1559-1816.2001.tb02686.x
Chen, C. C., Greene, P. G., and Crick, A. (1998). Does entrepreneurial self-efficacy distinguish entrepreneurs from managers? J. Bus. Ventur. 13, 295–316. doi: 10.1016/s0883-9026(97)00029-3
Chen, K. C., and Jang, S. J. (2010). Motivation in online learning: testing a model of self-determination theory. Comput. Human Behav. 26, 741–752. doi: 10.1016/j.chb.2010.01.011
Chen, X., Fang, S., Li, Y., and Wang, H. (2019). Does identification influence continuous E-commerce consumption? The mediating role of intrinsic motivations. Sustainability 11:1944. doi: 10.3390/su11071944
Chen, X., Li, G., Hu, Y., and Li, Y. (2016). How anonymity influence self-disclosure tendency on sina weibo: an empirical study. Anthropologist 26, 217–226. doi: 10.1080/09720073.2016.11892151
Chen, Y., Liang, C., and Cai, D. (2018). Understanding WeChat users’ behavior of sharing social crisis information. Int. J. Hum. Comput. Interact. 34, 356–366. doi: 10.1080/10447318.2018.1427826
Cheon, Y. J., Choi, S. K., Kim, J., and Kwak, K. T. (2015). Antecedents of relational inertia and information sharing in SNS usage: the moderating role of structural autonomy. Technol. Forecast. Soc. Change 95, 32–47. doi: 10.1016/j.techfore.2014.05.002
Cheung, C., Lee, Z. W., and Chan, T. K. (2015). Self-disclosure in social networking sites: the role of perceived cost, perceived benefits and social influence. Int. Res. 25, 279–299. doi: 10.1108/intr-09-2013-0192
Chin, W. W. (1998). The partial least squares approach to structural equation modeling. Modern Methods Bus. Res. 295, 295–336.
Chiu, C. M., Hsu, M. H., and Wang, E. T. (2006). Understanding knowledge sharing in virtual communities: an integration of social capital and social cognitive theories. Decis. Support Syst. 42, 1872–1888. doi: 10.1016/j.dss.2006.04.001
Cho, I., Park, H., and Kim, J. K. (2015). The relationship between motivation and information sharing about products and services on facebook. Behav. Inf. Technol. 34, 858–868. doi: 10.1080/0144929x.2014.988177
Christopherson, K. M. (2007). The positive and negative implications of anonymity in Internet social interactions:“On the internet, nobody knows you’re a dog”. Comput. Human Behav. 23, 3038–3056. doi: 10.1016/j.chb.2006.09.001
Chua, Y. P., and Chua, Y. P. (2017). Do computer-mediated communication skill, knowledge and motivation mediate the relationships between personality traits and attitude toward facebook? Comput. Human Behav. 70, 51–59. doi: 10.1016/j.chb.2016.12.034
Constant, D., Kiesler, S., and Sproull, L. (1994). What’s mine is ours, or is it? A study of attitudes about information sharing. Inform. Syst. Res. 5, 400–421. doi: 10.1287/isre.5.4.400
Cunningham, C. (ed.) (2013). Social Networking, and. (Impression)Management: Self-Presentation in the Digital Age. Lanham, MD: Rowman & Littlefield.
Davis, S., and Wiedenbeck, S. (2001). The mediating effects of intrinsic motivation, ease of use and usefulness perceptions on performance in first-time and subsequent computer users. Interact. Comput. 13, 549–580. doi: 10.1016/s0953-5438(01)00034-0
de Almeida, F. C., Lesca, H., and Canton, A. W. (2016). Intrinsic motivation for knowledge sharing–competitive intelligence process in a telecom company. J. Knowl. Manag. 20, 1282–1301. doi: 10.1108/jkm-02-2016-0083
De Montjoye, Y. A., Hidalgo, C. A., Verleysen, M., and Blondel, V. D. (2013). Unique in the crowd: the privacy bounds of human mobility. Sci. Rep. 3, 1376. doi: 10.1038/srep01376
Deci, E. L., Connell, J. P., and Ryan, R. M. (1989). Self-determination in a work organization. J. Appl. Psychol. 74, 580–590. doi: 10.1037/0021-9010.74.4.580
Deci, E. L., and Ryan, R. M. (1985). Intrinsic Motivation and Self-Determination in Human Behavior. New York, NY: Plenum.
Demir, M., Özdemir, M., and Marum, K. P. (2011). Perceived autonomy support, friendship maintenance, and happiness. J. Psychol. 145, 537–571. doi: 10.1080/00223980.2011.607866
Dienlin, T., and Metzger, M. J. (2016). An extended privacy calculus model for SNSs: analyzing self-disclosure and self-withdrawal in a representative US sample. J. Comput. Mediat. Commun. 21, 368–383. doi: 10.1111/jcc4.12163
Donovan, L. A., and MacIntyre, P. D. (2004). Age and sex differences in willingness to communicate, communication apprehension, and self-perceived competence. Commun. Res. Rep. 21, 420–427. doi: 10.1080/08824090409360006
Eastin, M. S., and LaRose, R. (2000). Internet self-efficacy and the psychology of the digital divide. J. Comput. Mediat. Commun. 6, 1–13. doi: 10.2196/mental.8311
Ellison, N. B., Steinfield, C., and Lampe, C. (2007). The benefits of facebook “friends:” social capital and college students’ use of online social network sites. J. Comput. Mediat. Commun. 12, 1143–1168. doi: 10.1111/j.1083-6101.2007.00367.x
Ellison, N. B., Steinfield, C., and Lampe, C. (2011). Connection strategies: social capital implications of facebook-enabled communication practices. New Media Soc. 13, 873–892. doi: 10.1071/AH18198
Faisal, M., and Alsumait, A. (2011). “Social network privacy and trust concerns,” in Proceedings of the 13th International Conference on Information Integration and Web-based Applications and Services, (New York, NY: ACM), 416–419.
Fernet, C., Austin, S., Trépanier, S. G., and Dussault, M. (2013). How do job characteristics contribute to burnout? Exploring the distinct mediating roles of perceived autonomy, competence, and relatedness. Eur. J. Work Organ. Psychol. 22, 123–137. doi: 10.1080/1359432x.2011.632161
Finkel, E. J., Norton, M. I., Reis, H. T., Ariely, D., Caprariello, P. A., Eastwick, P. W., et al. (2015). When does familiarity promote versus undermine interpersonal attraction? A proposed integrative model from erstwhile adversaries. Perspect. Psychol. Sci. 10, 3–19. doi: 10.1177/1745691614561682
Fornell, C., and Larcker, D. F. (1981). Evaluating structural equation models with unobservable variables and measurement error. J. Mark. Res. 18, 39–50. doi: 10.2307/3151312
Fox, J., Cruz, C., and Lee, J. Y. (2015). Perpetuating online sexism offline: anonymity, interactivity, and the effects of sexist hashtags on social media. Comput. Human Behav. 52, 436–442. doi: 10.1016/j.chb.2015.06.024
Fox, J., and Moreland, J. J. (2015). The dark side of social networking sites: an exploration of the relational and psychological stressors associated with Facebook use and affordances. Comput. Human Behav. 45, 168–176. doi: 10.1016/j.chb.2014.11.083
Gan, C. (2017). Understanding WeChat users’ liking behavior: an empirical study in China. Comput. Human Behav. 68, 30–39. doi: 10.1016/j.chb.2016.11.002
Gan, C. (2018). Gratifications for using social media: a comparative analysis of Sina Weibo and WeChat in China. Inf. Dev. 34, 139–147. doi: 10.1177/0266666916679717
Gan, C., and Wang, W. (2015). Uses and gratifications of social media: a comparison of microblog and WeChat. J. Syst. Inf. Technol. 17, 351–363. doi: 10.1108/jsit-06-2015-0052
Gefen, D. (2000). E-commerce: the role of familiarity and trust. Omega 28, 725–737. doi: 10.1016/s0305-0483(00)00021-9
Gerlach, J., Widjaja, T., and Buxmann, P. (2015). Handle with care: how online social network providers’ privacy policies impact users’ information sharing behavior. J. Strateg. Inf. Syst. 24, 33–43. doi: 10.1016/j.jsis.2014.09.001
Hair, F., Marko, J. S., Lucas, H., and Volker, G. K. (2014). Partial least squares structural equation modeling (PLS-SEM) An emerging tool in business research. Eur. Bus. Rev. 26, 106–121. doi: 10.1108/ebr-10-2013-0128
Hair, J. F. Jr., Hult, G. T. M., Ringle, C., and Sarstedt, M. (2016). A Primer on Partial Least Squares Structural Equation Modeling (PLS-SEM). Thousand Oaks, CA: Sage publications.
Hajli, N., and Lin, X. (2016). Exploring the security of information sharing on social networking sites: the role of perceived control of information. J. Bus. Ethics 133, 111–123. doi: 10.1007/s10551-014-2346-x
Hallam, C., and Zanella, G. (2017). Online self-disclosure: the privacy paradox explained as a temporally discounted balance between concerns and rewards. Comput. Human Behav. 68, 217–227. doi: 10.1016/j.chb.2016.11.033
Henseler, J., Dijkstra, T. K., Sarstedt, M., Ringle, C. M., Diamantopoulos, A., Straub, D. W., et al. (2014). Common beliefs and reality about PLS: comments on Rönkkö and Evermann (2013). Organ. Res. Methods 17, 182–209. doi: 10.1177/1094428114526928
Hite, D. M., Voelker, T., and Robertson, A. (2014). Measuring perceived anonymity: the development of a context independent instrument. J. Methods Meas. Soc. Sci. 5, 22–39.
Hsieh, A. Y., and Luarn, P. (2014). Speech or silence: the effect of user anonymity and member familiarity on the willingness to express opinions in virtual communities. Online Inf. Rev. 38, 881–895. doi: 10.1108/oir-03-2014-0076
Hsu, M. H., Ju, T. L., Yen, C. H., and Chang, C. M. (2007). Knowledge sharing behavior in virtual communities: the relationship between trust, self-efficacy, and outcome expectations. Int. J. Hum. Comput. Stud. 65, 153–169. doi: 10.1016/j.ijhcs.2006.09.003
Hung, S. Y., Durcikova, A., Lai, H. M., and Lin, W. M. (2011). The influence of intrinsic and extrinsic motivation on individuals’ knowledge sharing behavior. Int. J. Hum. Comput. Stud. 69, 415–427. doi: 10.1016/j.ijhcs.2011.02.004
Ibrahim, Y. (2010). “Social networking sites (SNS) and the ‘narcissistic turn’: the politics of self-exposure,” in Social Computing: Concepts, Methodologies, Tools, and Applications, (Pennsylvania, PA: IGI Global), 1855–1868. doi: 10.4018/978-1-60566-984-7.ch122
Jardine, E. (2015). The Dark Web Dilemma: Tor, Anonymity and Online Policing. Global Commission on Internet Governance Paper Series, (21). Available at: https://ssrn.com/abstract=2667711 (accessed on September 30, 2015).
Jessup, L. M., Connolly, T., and Galegher, J. (1990). The effects of anonymity on GDSS group process with an idea-generating task. MIS Q. 14, 313–321.
John, S. P. (2013). Influence of computer self-efficacy on information technology adoption. Int. J. Inf. Technol. 19, 1–13.
Joinson, A. N. (2001). Self-disclosure in computer-mediated communication: the role of self-awareness and visual anonymity. Eur. J. Soc. Psychol. 31, 177–192. doi: 10.1002/ejsp.36
Joinson, A. N., Woodley, A., and Reips, U. D. (2007). Personalization, authentication and self-disclosure in self-administered internet surveys. Comput. Human Behav. 23, 275–285. doi: 10.1016/j.chb.2004.10.012
Jung, Y. (2011). Understanding the role of sense of presence and perceived autonomy in users’ continued use of social virtual worlds. J. Comput. Mediat. Commun. 16, 492–510. doi: 10.1111/j.1083-6101.2011.01540.x
Kang, M., and Schuett, M. A. (2013). Determinants of sharing travel experiences in social media. J. Travel Tour. Mark. 30, 93–107. doi: 10.1080/10548408.2013.751237
Kang, R., Brown, S., and Kiesler, S. (2013). “Why do people seek anonymity on the internet? informing policy and design,” in Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, (New York, NY: ACM), 2657–2666.
Kaptein, M., Nass, C., Parvinen, P., and Markopoulos, P. (2013). “Nice to know you: familiarity and influence in social networks,” in Proceedings of the 2013 46th Hawaii International Conference on System Sciences, (Washington, DC: IEEE), 2745–2752.
Kenny, R. F., Van Neste-Kenny, J. M., Burton, P. A., Park, C. L., and Qayyum, A. (2012). Using self-efficacy to assess the readiness of nursing educators and students for mobile learning. Int. Rev. Res. Open Distrib. Learn. 13, 277–296.
Kim, H. S. (2016). What drives you to check in on facebook? Motivations, privacy concerns, and mobile phone involvement for location-based information sharing. Comput. Human Behav. 54, 397–406. doi: 10.1016/j.chb.2015.08.016
Kim, J. (2012). The effect of relationship building through SNS on an individual’s intention to share information. Inform. Pol. 19, 57–84.
Komiak, S. Y., and Benbasat, I. (2006). The effects of personalization and familiarity on trust and adoption of recommendation agents. MIS Q. 30, 941–960.
Krasnova, H., Veltri, N. F., and Günther, O. (2012). Self-disclosure and privacy calculus on social networking sites: the role of culture. Bus. Inform. Syst. Eng. 4, 127–135. doi: 10.1007/s12599-012-0216-6
Lai, H. M., and Chen, T. T. (2014). Knowledge sharing in interest online communities: a comparison of posters and lurkers. Comput. Human Behav. 35, 295–306. doi: 10.1016/j.chb.2014.02.004
Lapidot-Lefler, N., and Barak, A. (2012). Effects of anonymity, invisibility, and lack of eye-contact on toxic online disinhibition. Comput. Human Behav. 28, 434–443. doi: 10.1016/j.chb.2011.10.014
Lee, C. S., and Ma, L. (2012). News sharing in social media: the effect of gratifications and prior experience. Comput. Human Behav. 28, 331–339. doi: 10.1016/j.chb.2011.10.002
Levmore, S., and Nussbaum, M. C. (eds) (2010). The Offensive Internet. Cambridge, MA: Harvard University Press.
Levontin, L., and Yom-Tov, E. (2017). Negative self-disclosure on the web: the role of guilt relief. Front. Psychol. 8:1068. doi: 10.3389/fpsyg.2017.01068
Li, C., Shi, X., and Dang, J. (2014). Online communication and subjective well-being in Chinese college students: the mediating role of shyness and social self-efficacy. Comput. Human Behav. 34, 89–95. doi: 10.1016/j.chb.2014.01.032
Li, G., Jung, J. R., and Park, S. T. (2018). Factors enhancing mobile social networking friendship maintenance: a study of alumni community on Wechat. Cluster Comput. 21, 1127–1138. doi: 10.1007/s10586-017-0851-2
Li, X., Li, D., and Newman, J. (2013). Parental behavioral and psychological control and problematic internet use among Chinese adolescents: the mediating role of self-control. Cyberpsychol. Behav. Soc. Netw. 16, 442–447. doi: 10.1089/cyber.2012.0293
Lien, C. H., Cao, Y., and Zhou, X. (2017). Service quality, satisfaction, stickiness, and usage intentions: an exploratory evaluation in the context of WeChat services. Comput. Human Behav. 68, 403–410. doi: 10.1016/j.chb.2016.11.061
Lin, C., Fang, W., and Jin, J. (2017). You are what you post in “circle of friends” of WeChat: self-presentation and identity production from a personality perspective. Glob. Media China 2, 138–152. doi: 10.1177/2059436417728855
Lin, K. Y., and Lu, H. P. (2011). Why people use social networking sites: an empirical study integrating network externalities and motivation theory. Comput. Human Behav. 27, 1152–1161. doi: 10.1016/j.chb.2010.12.009
Lin, M. J. J., Hung, S. W., and Chen, C. J. (2009). Fostering the determinants of knowledge sharing in professional virtual communities. Comput. Hum. Behav. 25, 929–939. doi: 10.1016/j.chb.2009.03.008
Lin, R., and Utz, S. (2017). Self-disclosure on SNS: do disclosure intimacy and narrativity influence interpersonal closeness and social attraction? Comput. Human Behav. 70, 426–436. doi: 10.1016/j.chb.2017.01.012
Liu, L., Cheung, C. M., and Lee, M. K. (2016). An empirical investigation of information sharing behavior on social commerce sites. Int. J. Inform. Manag. 36, 686–699. doi: 10.1016/j.ijinfomgt.2016.03.013
Lowry, P. B., Cao, J., and Everard, A. (2011). Privacy concerns versus desire for interpersonal awareness in driving the use of self-disclosure technologies: the case of instant messaging in two cultures. J. Manag. Inform. Syst. 27, 163–200. doi: 10.2753/mis0742-1222270406
Marx, G. T. (1999). What’s in a name? Some reflections on the sociology of anonymity. Inform. Soc. 15, 99–112. doi: 10.1080/019722499128565
Montag, C., Becker, B., and Gan, C. (2018). The multipurpose application WeChat: a review on recent research. Front. Psychol. 9:2247. doi: 10.3389/fpsyg.2018.02247
Montag, C., Błaszkiewicz, K., Sariyska, R., Lachmann, B., Andone, I., Trendafilov, B., et al. (2015). Smartphone usage in the 21st century: who is active on WhatsApp? BMC Res. Notes 8:331. doi: 10.1186/s13104-015-1280-z
Moon, J. H., Lee, E., Lee, J. A., Choi, T. R., and Sung, Y. (2016). The role of narcissism in self-promotion on Instagram. Pers. Individ. Dif. 101, 22–25. doi: 10.1016/j.paid.2016.05.042
Muhlenfeld, H. (2005). Differences between ‘talking about’ and ‘admitting’ sensitive behavior in anonymous and non-anonymous we-based interviews. Comput. Human Behav. 21, 993–1003. doi: 10.1016/j.chb.2004.02.023
Munar, A. M. (2010). Digital exhibitionism: the age of exposure. Cult. Unbound 2, 401–422. doi: 10.3384/cu.2000.1525.10223401
Neves, B. B. (2013). Social capital and Internet use: the irrelevant, the bad, and the good. Sociol. Compass 7, 599–611. doi: 10.1111/soc4.12059
Park, S., Choi, Y., Hwang, D., and Paek, M. (2012). “Do different types of SNS have different impacts on participatory social capital?,” in Proceedings of the International Conference on Electronic Government and the Information Systems Perspective, (Berlin: Springer), 231–241. doi: 10.1007/978-3-642-32701-8_20
Prabhu, V., Sutton, C., and Sauser, W. (2008). Creativity and certain personality traits: understanding the mediating effect of intrinsic motivation. Creat. Res. J. 20, 53–66. doi: 10.1080/10400410701841955
Preacher, K. J., and Hayes, A. F. (2004). SPSS and SAS procedures for estimating indirect effects in simple mediation models. Behav. Res. Methods Instrum. Comput. 36, 717–731. doi: 10.3758/bf03206553
Prenticedunn, S., and Rogers, R. W. (1982). Effects of public and private self-awareness on deindividuation and aggression. J. Pers. Soc. Psychol. 43, 503–513. doi: 10.1037//0022-3514.43.3.503
Rainie, L., Kiesler, S., Kang, R., Madden, M., Duggan, M., Brown, S., et al. (2013). Anonymity, privacy, and security online. Pew Res. Center 5, 1–35.
Rains, S. A., and Scott, C. R. (2007). To identify or not to identify: a theoretical model of receiver responses to anonymous communication. Commun. Theory 17, 61–91. doi: 10.1111/j.1468-2885.2007.00288.x
Reinig, B. A., and Mejias, R. J. (2004). The efects of national culture and anonymity on flaming and criticalness in GSS-supported discussions. Small Group Res. 35, 698–723. doi: 10.1177/1046496404266773
Rode, H. (2016). To share or not to share: the effects of extrinsic and intrinsic motivations on knowledge-sharing in enterprise social media platforms. J. Inform. Technol. 31, 152–165. doi: 10.1057/jit.2016.8
Ryan, R. M., and Deci, E. L. (2017). Self-Determination Theory: Basic Psychological Needs in Motivation, Development, and Wellness. New York, NY: Guilford Publications.
Safa, N. S., and Von Solms, R. (2016). An information security knowledge sharing model in organizations. Comput. Human Behav. 57, 442–451. doi: 10.1016/j.chb.2015.12.037
Sánchez-Franco, M. J., and Roldán, J. L. (2015). The influence of familiarity, trust and norms of reciprocity on an experienced sense of community: an empirical analysis based on social online services. Behav. Inform. Technol. 34, 392–412. doi: 10.1080/0144929x.2014.959455
Sassenberg, K., and Postmes, T. (2002). Cognitive and strategic processes in small groups: effects of anonymity of the self and anonymity of the group on social influence. Br. J. Soc. Psychol. 41, 463–480. doi: 10.1348/014466602760344313
Scott, S. V., and Orlikowski, W. J. (2014). Entanglements in practice: performing anonymity through social media. MIS Q. 38, 873–893. doi: 10.25300/misq/2014/38.3.11
Shibchurn, J., and Yan, X. (2015). Information disclosure on social networking sites: an intrinsic–extrinsic motivation perspective. Comput. Human Behav. 44, 103–117. doi: 10.1016/j.chb.2014.10.059
Spears, R. (2017). Social Identity Model Of Deindividuation Effects. The International Encyclopedia of Media Effects. Hoboken, NJ: wiley-blackwell.
Stieglitz, S., and Dang-Xuan, L. (2013). Emotions and information diffusion in social media—sentiment of microblogs and sharing behavior. J. Manag. Inform. Syst. 29, 217–248. doi: 10.2753/mis0742-1222290408
Subrahmanyam, K., Reich, S. M., Waechter, N., and Espinoza, G. (2008). Online and offline social networks: use of social networking sites by emerging adults. J. Appl. Dev. Psychol. 29, 420–433. doi: 10.1016/j.appdev.2008.07.003
Taddei, S., and Contena, B. (2013). Privacy, trust and control: which relationships with online self-disclosure? Comput. Human Behav. 29, 821–826. doi: 10.1016/j.chb.2012.11.022
Tang, Q., Zhao, X., and Liu, S. (2016). The effect of intrinsic and extrinsic motivations on mobile coupon sharing in social network sites: the role of coupon proneness. Int. Res. 26, 101–119. doi: 10.1108/intr-05-2014-0136
Utz, S. (2015). The function of self-disclosure on social network sites: not only intimate, but also positive and entertaining self-disclosures increase the feeling of connection. Comput. Human Behav. 45, 1–10. doi: 10.1016/j.chb.2014.11.076
Vilanova, F., Beria, F. M., Costa, Â. B., and Koller, S. H. (2017). Deindividuation: from Le Bon to the social identity model of deindividuation effects. Cogent Psychol. 4:1308104.
Vilnai-Yavetz, I., and Levina, O. (2018). Motivating social sharing of e-business content: intrinsic motivation, extrinsic motivation, or crowding-out effect? Comput. Human Behav. 79, 181–191. doi: 10.1016/j.chb.2017.10.034
Vogel, E. A., and Rose, J. P. (2016). Self-reflection and interpersonal connection: making the most of self-presentation on social media. Transl. Issues Psychol. Sci. 2, 294–302. doi: 10.1037/tps0000076
Walther, J. B. (2007). Selective self-presentation in computer-mediated communication: hyperpersonal dimensions of technology, language, and cognition. Comput. Human Behav. 23, 2538–2557. doi: 10.1016/j.chb.2006.05.002
Wang, D. (2017). A study of the relationship between narcissism, extraversion, drive for entertainment, and narcissistic behavior on social networking sites. Comput. Human Behav. 66, 138–148. doi: 10.1016/j.chb.2016.09.036
Wang, D., Xu, L., and Chan, H. C. (2015). Understanding the continuance use of social network sites: a computer self-efficacy perspective. Behav. Inf. Technol. 34, 204–216. doi: 10.1080/0144929x.2014.952778
Wang, J. L., Jackson, L. A., Gaskin, J., and Wang, H. Z. (2014). The effects of social networking site (SNS) use on college students’ friendship and well-being. Comput. Human Behav. 37, 229–236. doi: 10.1016/j.chb.2014.04.051
Wang, J. L., Jackson, L. A., Wang, H. Z., and Gaskin, J. (2015). Predicting social networking site (SNS) use: personality, attitudes, motivation and internet self-efficacy. Pers. Individ. Dif. 80, 119–124. doi: 10.1016/j.paid.2015.02.016
Wang, W. T., and Hou, Y. P. (2015). Motivations of employees’ knowledge sharing behaviors: a self-determination perspective. Inform. Organ. 25, 1–26. doi: 10.1016/j.infoandorg.2014.11.001
Wang, X., Cao, R., Yang, M., and Chen, L. (2016). An empirical study of influence factors on WeChat user information sharing behavior: based on the perspective of information ecology. Library Inform. Serv. 60, 6–13.
Wang, X., and Gu, B. (2016). The communication design of WeChat: ideological as well as technical aspects of social media. Commun. Design Q. Rev. 4, 23–35. doi: 10.1145/2875501.2875503
Welschen, J., Todorova, N., and Mills, A. M. (2012). An investigation of the impact of intrinsic motivation on organizational knowledge sharing. Int. J. Knowl. Manag. 8, 23–42. doi: 10.4018/jkm.2012040102
Wen, Z., Geng, X., and Ye, Y. (2016). Does the use of WeChat lead to subjective well-being?: the effect of use intensity and motivations. Cyberpsychol. Behav. Soc. Netw. 19, 587–592. doi: 10.1089/cyber.2016.0154
Whetten, D. A. (1989). What constitutes a theoretical contribution? Acad. Manag. Rev. 14, 490–495. doi: 10.5465/amr.1989.4308371
Wong, T. Y., Yuen, K. S., and Li, W. O. (2015). A basic need theory approach to problematic Internet use and the mediating effect of psychological distress. Front. Psychol. 5:1562. doi: 10.3389/fpsyg.2014.01562
Wright, M. F. (2014). Predictors of anonymous cyber aggression: the role of adolescents’ beliefs about anonymity, aggression, and the permanency of digital content. Cyberpsychol. Behav. Soc. Netw. 17, 431–438. doi: 10.1089/cyber.2013.0457
Yan, Z., Wang, T., Chen, Y., and Zhang, H. (2016). Knowledge sharing in online health communities: a social exchange theory perspective. Inf. Manag. 53, 643–653. doi: 10.1016/j.im.2016.02.001
Yang, T. M., and Maxwell, T. A. (2011). Information-sharing in public organizations: a literature review of interpersonal, intra-organizational and inter-organizational success factors. Gov. Inf. Q. 28, 164–175. doi: 10.1016/j.giq.2010.06.008
Yoon, C., and Rolland, E. (2012). Knowledge-sharing in virtual communities: familiarity, anonymity and self-determination theory. Behav. Inf. Technol. 31, 1133–1143. doi: 10.1080/0144929x.2012.702355
Yoon, S. J. (2014). Does social capital affect SNS usage? A look at the roles of subjective well-being and social identity. Comput. Human Behav. 41, 295–303. doi: 10.1089/cyber.2014.0341
Yu, T. K., Lu, L. C., and Liu, T. F. (2010). Exploring factors that influence knowledge sharing behavior via weblogs. Comput. Human Behav. 26, 32–41. doi: 10.1016/j.chb.2009.08.002
Zapata-Phelan, C. P., Colquitt, J. A., Scott, B. A., and Livingston, B. (2009). Procedural justice, interactional justice, and task performance: the mediating role of intrinsic motivation. Organ. Behav. Hum. Decis. Process. 108, 93–105. doi: 10.1016/j.obhdp.2008.08.001
Zhang, C. B., Li, Y. N., Wu, B., and Li, D. J. (2017). How WeChat can retain users: roles of network externalities, social interaction ties, and perceived values in building continuance intention. Comput. Human Behav. 69, 284–293. doi: 10.1016/j.chb.2016.11.069
Zhang, Y., and Ling, Q. (2015). SNS as intimacy zone: social intimacy, loneliness, and self-disclosure on SNS. Glob. Media J. 13, 1–18. doi: 10.1016/j.chb.2017.01.012
Keywords: social networking sites, information sharing, perceived anonymity, intrinsic motivation, familiarity
Citation: Chen X, Sun M, Wu D and Song XY (2019) Information-Sharing Behavior on WeChat Moments: The Role of Anonymity, Familiarity, and Intrinsic Motivation. Front. Psychol. 10:2540. doi: 10.3389/fpsyg.2019.02540
Received: 02 June 2019; Accepted: 28 October 2019;
Published: 14 November 2019.
Edited by:
Gerrit C. Van Der Veer, University of Twente, NetherlandsReviewed by:
José Baptista Coelho, University of Lisbon, PortugalXiaoxun Sun, Australian Council for Educational Research, Australia
Yamikani Ndasauka, University of Malawi, Malawi
Copyright © 2019 Chen, Sun, Wu and Song. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Xi Chen, MTM2MTA0OTFAcXEuY29t
 Xi Chen
Xi Chen MingXue Sun
MingXue Sun Dong Wu
Dong Wu Xiao Yu Song
Xiao Yu Song